- Details
- Category: Security News
Many organizations take months or years to discover they've been victimized by breaches because they lack experienced cybersecurity personnel, says employment researcher David Foote.
Enterprises are hiring cybersecurity specialists, but many of them are relatively young and lack the experience to help quickly detect that their organization has been hacked, says Foote, CEO and co-founder of the IT employment research firm Foote Partners. The solution to the cyber-skills shortage, he says, is "the maturing of the workforce."
"You learn some things in school [but] you have to go through a period of time when you're actually on the job, doing it live," Foote says in an interview with Information Security Media Group. "We just have to wait until the cybersecurity jobs mature and have enough people who have been out of school and have learned on the job how you determine whether you've been hacked ... what [are] the root causes and what's been stolen. I don't know if there is any other way. It's just a maturation process that takes time."
In the interview (click on player beneath above image to listen), Foote:
Discusses how organizations can immediately address the cybersecurity skills shortage as they bide time for the maturation process to work itself out; Explains how two types of risks - business risk and information security risk - are converging to help managers tackle the cybersecurity skills gap; Describes three types of CISOs now in demand.Before co-founding Foote Partners in 1997, Foote worked as an analyst at IT advisers Gartner and Meta Group.
- Details
- Category: Security News
Anti-Malware , Risk Management , Technology
Ransomware Gets Pokémon Go Treatment Crypto-Locking Ransomware Victims: Gotta Catch 'Em All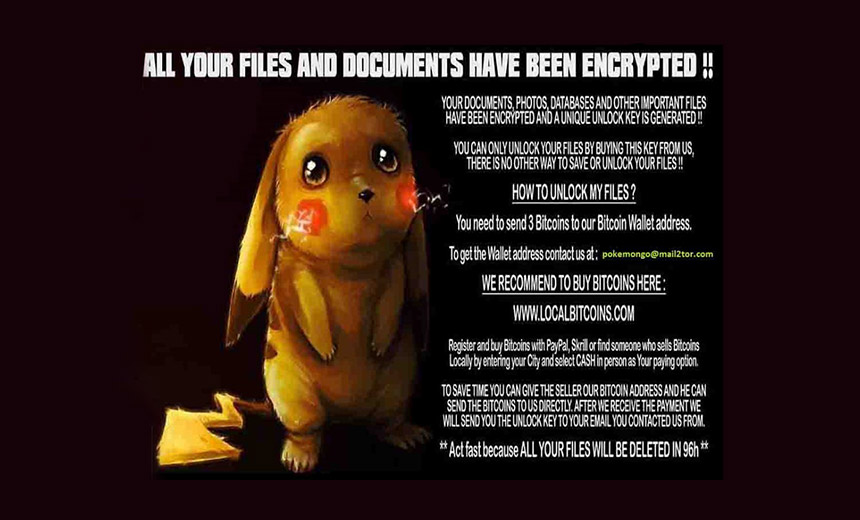 DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeam
DetoxCrypto PokemonGo variant's ransomware lock screen. Source: MalwareHunterTeamIn their attempts to compel victims to pay ransoms, cybercriminals have tested crypto-locking ransomware with themes ranging from horror movies to Hitler to cats.
See Also: Managing Identity, Security and Device Compliance in an IT World
Thus it's inevitable that recently spotted ransomware has opted to channel the hot new location-based augmented reality game Pokémon Go (see Pokémon Go Mayhem: Privacy, Muggings, Malware).
Two new versions of Pokémon Go ransomware have been discovered. One is a variant of DetoxCrypto, discovered by the MalwareHunterTeam group. Another variant of DetoxCrypto, meanwhile, looks like generic ransomware - there's no Pokémon theme - and was discovered by Marc Rivero López, a security researcher at Intel Security.
@malwrhunterteam @bleepincomputer @techhelplistcom @jameswt_mht @antelox @demonslay335 @nyxbone ransom note related pic.twitter.com/MV6moXZOve
The Calipso variant sends a screenshot of a user's system to the ransomware controller - potentially for blackmail purposes - and threatens to delete all encrypted files unless a user pays within 72 hours, according to anti-ransomware site Bleeping Computer.
Payload Security, an automated malware analysis service, reports that a related sample of the ransomware obtained by researchers is a 3.7 MB Windows executable file named "88547-pokemongo.exe."
Both ransomware variants' lock screens play music. In the case of the PokemonGo version, it plays an audio file, "pok.wav," containing music from the Pokémon Gameboy game. The ransomware appears to be demanding 2 to 3 bitcoins ($1,160 to $1,700).
@BleepinComputer @demonslay335 @Seifreed @nyxbone @PolarToffee Targeted extensions and excluded folders: pic.twitter.com/lAPLk6DfOI
Hidden Tear: Pokémon Version
A separate piece of ransomware that sports a Pokémon Go theme was discovered by MalwareHunterTeam member Michael Gillespie, as Bleeping Computer first reported.
Independent malware analyst MlwrHpstr says in a blog post on the site of security firm Malwarebytes that the ransomware appears to be based on open source, proof-of-concept ransomware called Hidden Tear, which was published to code-sharing site GitHub by Turkish programmer Utku Sen in August 2015. Sen said his intentions were educational, and ever since then, attackers have been using it to school victims.
The ransomware includes some interesting tricks, including the ability to create an admin-level account named "Hack3r," as well as to locate removable drives and drop an autorun.inf file onto the devices, although this feature does not yet appear to be fully developed, MlwrHpstr says. But the attack technique could be used to spread the ransomware via USB drives or CDs and to have it automatically execute when they were connected to a new system.
"The purpose of dropping the autorun file is so the malware can be executed by the AutoRun and AutoPlay components of Microsoft Windows, which in turn means that the malware can be launched from a USB or CD upon being inserted into a new target system," MlwrHpstr says.
But that is just one of several features that don't appear to have been completed. "The current PokemonGo ransomware is not as sophisticated as Cerber, Petya, Mischa or Locky ransomware but appears to be under development," MlwrHpstr writes. "That being said ... PokemonGo could possibly be used in future social engineering attacks referencing Pokemon Go to entice new victims.
Ransomware Victims: Tough Choices
When it comes to being a ransomware victim, security researchers - working anonymously - recently found that in many cases, they were able to negotiate with attackers to lower their ransom demands (see Ransomware Gangs Take 'Customer Service' Approach). Of course, the prevailing recommendation is for PC users to always run anti-virus software; keep current, offline backups, so that infected systems can be wiped and restored; and if they do get infected, to avail themselves of free decryption tools, when available.
Authorities continue to urge individuals and organizations to never pay ransoms, because the funds directly support criminals' ongoing ransomware research and development.
This story has been updated to reflect that there are two separate and recently discovered types of ransomware with a Pokémon Go theme.
- Details
- Category: Security News
Data Breach , Fraud , Payments Fraud
Millennium and Noble House Learned of Breaches via Secret Service Millennium Broadway Hotel New York
Millennium Broadway Hotel New YorkTwo hotel chains are warning that they've suffered point-of-sale malware infections that compromised customers' payment card data. Both say they were alerted to related card fraud by the U.S. Secret Service and that they're now assisting law enforcement agencies' investigations.
See Also: The Inconvenient Truth About API Security
Millennium Hotels & Resorts North America, based in Denver, says that a malware infection that lasted more than three months resulted in a breach of card data from "food and beverage POS systems" at all 14 of its U.S. hotels. Separately, Noble House Hotels and Resorts, based in Kirkland, Wash., warned that systems at one of its properties were infected with POS malware for a two-month period.
In both cases, attackers may have compromised cardholders' names, payment card numbers, expiration dates and CVV numbers.
The timing of the two breach alerts, and fact that both hotel chains learned about the breaches via the Secret Service, suggests that the same cybercrime group may have been responsible. The Secret Service couldn't be immediately reached for comment on that possibility. But there's also strong evidence that the breach is tied to a recent alert from Oracle MICROS, warning that it had found malicious code in the software that runs POS devices that it provides to numerous businesses.
Millennium Breach: 14 U.S. Hotels Affected
Millennium says that after it was alerted to the breach at all of its 14 U.S. properties, it learned from its "third-party service provider - that supplies and services the affected point-of-sale systems - that it had detected and addressed malicious code in certain of its legacy point-of-sale systems, including those used by MHR," according to the hotel's breach notification. "MHR immediately adopted additional security measures as recommended by the third-party service provider."
The affected hotel properties are located in Anchorage, Alaska; Boston; Boulder, Colo.; Buffalo, N.Y.; Chicago; Cincinnati; Durham, N.C.; Los Angeles; Minneapolis; Nashville, Tenn; New York; and Scottsdale, Ariz.
Millennium says that hotel property management and booking systems are separated from its food and beverage POS systems, and that only the latter appear to have been infected. Millennium spokesman Peter Krijgsman tells Information Security Media Group that the company runs a number of systems on segmented networks - by region and hotel function - and that it changed all access passwords for affected POS systems following the breach. "We will continue to monitor for signs of intrusion, as we do as part of our standard security protocols," he says.
The company has not released details of how many customers may have been affected by the breach, which lasted from early March to mid-June. "We believe it involved less than 5,000 cards, and while the number of affected customers is not as large as the numbers reported by other, larger U.S. hotel operators, we take no comfort in that fact, as any breach is unacceptable," Krijgsman says, adding that Millennium's investigation remains ongoing. "If it reveals malware on our systems or if other types of personally identifiable information that can be used to commit identity theft have been potentially compromised, credit monitoring services likely will be provided."
The hotel chain declined to name its POS supplier, but said that "the third party is a significant supplier of POS systems to the hotel industry" and that "it is aware of these issues." The company also declined to name the outside incident response firm that it hired to investigate the breach.
Asked to clarify the hotel's reference to "legacy" POS systems, Krijgsman says that in this case it does not necessarily mean outdated. "While the affected POS systems are not the newest systems in the provider's portfolio, they are still supported by the supplier," he says. "Legacy systems can also signify systems provided by a company subsequently acquired by another."
A recent job listing offers a potential clue to the identity of its POS vendor. In the June 6 advertisement for a banquet manager, Millennium says that whoever gets the job must "utilize POS (Micros and Delphi) to accurately charge guests," apparently referring to Oracle MICROS, which provides POS systems to more than 330,000 locations, including hotels, across 180 countries. Oracle recently warned that it "has detected and addressed malicious code in certain legacy MICROS systems" (see Recent POS Attacks: Are They Linked?).
Breach at Ocean Key Resort & Spa
 Ocean Key Resort & Spa in Key West, Florida
Ocean Key Resort & Spa in Key West, Florida
Meanwhile, Noble House Hotels and Resorts says that its Ocean Key Resort & Spa in Key West, Fla., was infected by POS malware April 26 to June 8. Its breach alert says anyone who used a payment card at the hotel during that time - including at its restaurant and bars - may have had their card data compromised.
The Ocean Key breach follows a 2015 breach at The Commons, a Noble property in Minneapolis. Noble said that a POS malware infection at that hotel from January to August 2015 resulted in the suspected theft of 19,000 payment cards.
In the case of the Ocean Key breach, spokesman Simon Barker tells ISMG that the hotel chain hired FireEye's Mandiant incident response firm to investigate.
"At this time, it appears that 12,134 payment cards may have been affected by the incident at Ocean Key Resort," Barker tells ISMG. "We are in the process of sending notification letters to the guests for whom we have names and contact information. Legal notices have been placed in newspapers and a press release distributed nationally." The company says it's also working with payment card issuers to help them directly notify affected cardholders as well as institute heightened fraud monitoring.
The company has promised to reimburse any fraud that card issuers fail to cover. "If guests incurred costs that their financial institution declined to reimburse related to fraudulent charges on a payment card used at Ocean Key Resort & Spa, we will reimburse guests for any such reasonable, documented costs that their financial institutions decline to pay," he says. "We are not offering credit monitoring services as they do nothing to prevent fraudulent transactions on existing payment cards."
The hotel declined to discuss what security measures it had in place prior to the breach and what measures it plans to take. "We take the protection of payment card data security very seriously, but I'm afraid we are not prepared to discuss our specific security measures," Barker says.
These recent breaches at hotel chains follow a number of similar breaches in recent months that have affected Hilton, Hyatt, Starwood Hotels and Resorts, Omni and Trump Hotels, among others.
- Details
- Category: Security News
Anti-Malware , Endpoint Security , Forensics
Spyware Sold by Israel's NSO Group Linked to Attempted Attack
Apple has updated its mobile software to fix three zero-day software flaws used in an attempt to compromise a prominent United Arab Emirates-based dissident's iPhone. The attack code has been traced to an Israeli company that sells powerful hacking tools to governments - a business model that has been criticized for its potential for abuse.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
The code is the first publicly revealed that was capable of compromising Apple's latest iPhone software, enabling attackers to steal e-mails, SMS messages, iMessages, contact lists and application data. Security experts say these types of Apple software vulnerabilities that can provide attackers with such complete access to a target's device are highly sought after and can fetch upwards of $1 million from buyers.
The findings were revealed Aug. 25 in joint report from Citizen Lab - a research group within the University of Toronto that has published detailed investigations into the use of software exploits by governments with questionable human rights records to monitor activists and dissidents - and mobile security software firm Lookout Mobile Security.
The two organizations unwound a complicated technical trail that lead to Ahmed Mansoor, an activist who has been highly critical of the UAE government, after Mansoor shared with Citizen Lab a suspicious SMS that he received on his iPhone 6 on Aug. 10.
Targeted for Exploitation
Mansoor has long been known to be careful with electronic devices. He was targeted in 2011 by the FinFisher software made by Gamma Group, a U.K.-based organization that sold spying tools to governments. The next year, he was targeted by tools developed by Hacking Team, an Italian company in the same line of business, according to a blog post from Citizen Lab.
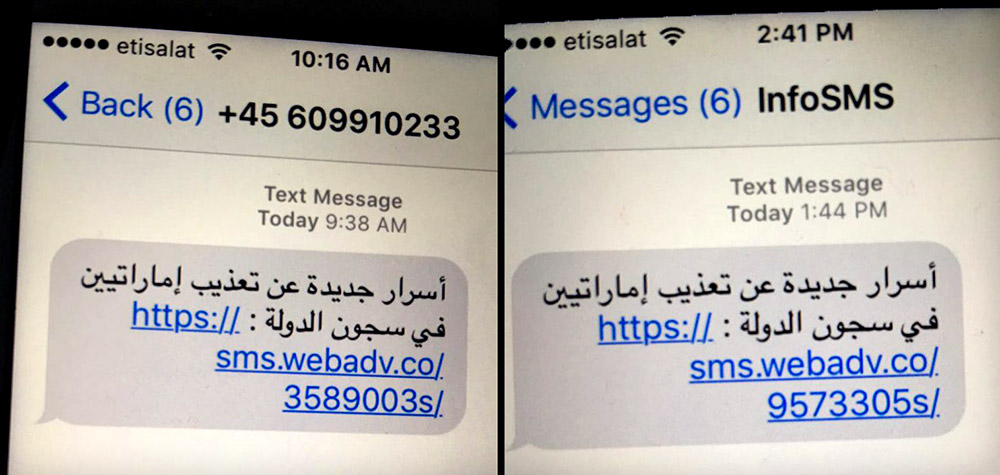 SMS text messages received by Mansoor (English: "New secrets about torture of Emiratis in state prisons"), via Citizen Lab. It says the sender's phone numbers were spoofed.
SMS text messages received by Mansoor (English: "New secrets about torture of Emiratis in state prisons"), via Citizen Lab. It says the sender's phone numbers were spoofed.
The day Mansoor received the text messages, he was running iOS 9.3.3 on an iPhone 6. Citizen Lab and Lookout found the malicious link successfully compromised an iPhone 5 running the same iOS version. They note that while the latest version of iOS at the time of the attack was 9.3.4, that is also vulnerable to the exploit.
Apple's strong security means attackers usually have to find and chain together several vulnerabilities in the mobile operating system before they can remotely compromise a device. The chain of exploits used in this attack, which researchers dubbed "Trident," starts with an exploit for a vulnerability in the browser engine WebKit, followed by exploiting two kernel-level flaws. Used together, the flaws allow for installation of an "implant," which is a euphemism for malware. The attack "happens invisibly and silently," Lookout says in a blog post.
Implant: Pegasus
The implant appears to come from NSO Group Technologies, which is based in Herzelia, Israel. In 2014, the private equity firm Francisco Partners bought a majority stake in the company for $120 million, according to Reuters.
"The implant installed by the Trident exploit chain would have turned Mansoor's iPhone into a digital spy in his pocket," Citizen Lab and Lookout say. "The spyware, which appears to be NSO's Pegasus spyware solution, was capable of employing his iPhone's camera and microphone to eavesdrop on activity in the vicinity of the device, recording his WhatsApp and Viber calls, logging messages sent in mobile chat apps, and tracking his movements."
Lookout has published a detailed technical analysis of the Pegasus spyware.
Security experts say that all iOS users should update immediately. "iOS 9.3.5 fixes some serious vulnerabilities that are being actively exploited," says digital forensic scientist Jonathan Zdziarski, author of "iPhone Forensics," via Twitter. "Drop what you are doing and update." The flaws are reportedly also now fixed in beta versions of Apple's forthcoming iOS 10.
Backlash As Governments Target Activists
Citizen Lab has published an extensive series of reports about dissidents who have been targeted by offensive cyber weapons sold by private companies to governments.
Those vendors have traditionally defended their operations by maintaining they only sell lawful intercept tools to vetted clients. But once the sales are made, the companies have little control over how the tools are used. The backlash from human rights watchers has been especially pointed.
In 2015, more than 400 GB of internal company documents belonging to Hacking Team were stolen and published. Some of those documents suggested that the government of Sudan was a customer of the company, but Hacking Team has avoided responding to related questions. Other clients of the company apparently included the governments of Azerbaijan, Egypt, Ethiopia, Morocco, United Arab Emirates, Uzbekistan, Saudi Arabia and Sudan, which many civil rights monitoring organizations say regularly violate human rights (see Spyware Vendor Alert: Suspend Software).
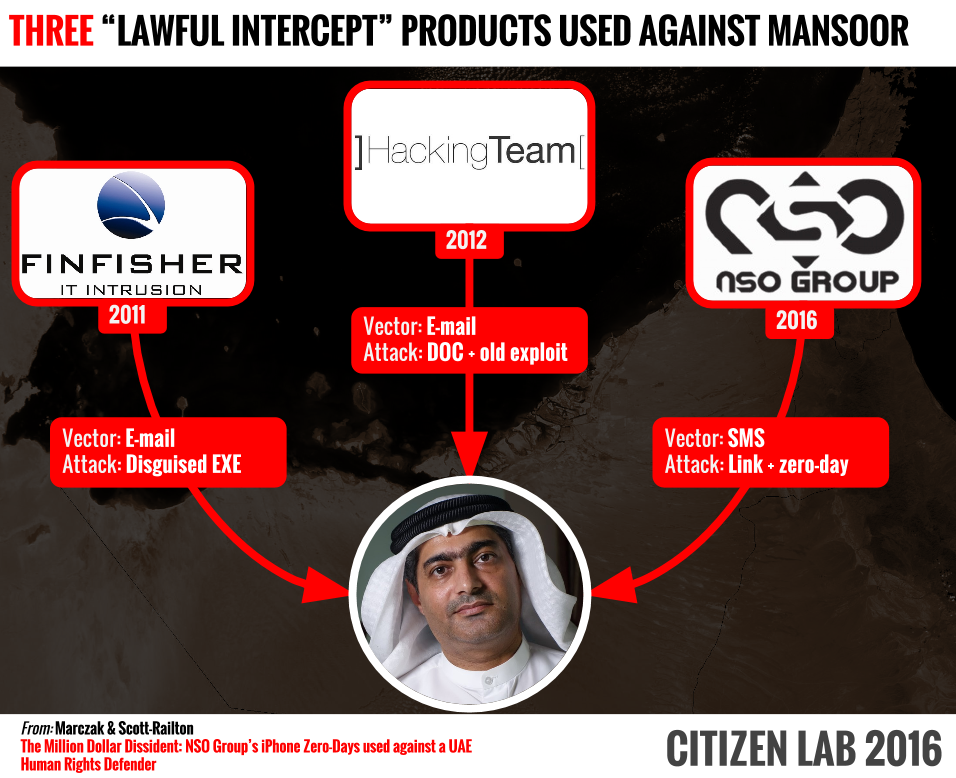 Ahmed Mansoor has been targeted multiple times using spyware sold to governments. Source: Citizen Lab
Ahmed Mansoor has been targeted multiple times using spyware sold to governments. Source: Citizen Lab
Ironically, those leaked documents provided more insights for Citizen Lab and Lookout into Pegasus, the spying software suite made by NSO Group linked to the attempted attack against Mansoor. "When we examined the Hacking Team emails leaked online after a 2015 breach, we found several instances of Hacking Team clients or resellers sharing what appeared to be NSO Group's product documentation and sales pitches," Citizen Lab says.
NSO Defends Its Sales Practices
But in a statement provided to Vice's Motherboard, NSO Group maintained that it only sells to "authorized government agencies" and complies with export control laws. The company sought to put itself at arm's length from its clients by adding it is strictly a technology company and does not operate any of its systems.
"NSO's mission is to help make the world a safer place by providing authorized governments with technology that helps them combat terror and crime," NSO Group says.
NSO Group's statement echoes a common defense of companies in its field, but one that falls flat with some security experts. "You really have to wonder what kind of human being says, 'This is how I want to make my money,'" wrote Matthew Green, a cryptography expert and associate professor at Johns Hopkins Information Security Institute, on Twitter.
Let me try this again. If some device you use a lot asks you to patch today, do it. Don't hit "later".
Citizen Lab's and Lookout's report maintains that the latest findings show that dangerous cyber weapons continue to be sold to countries that target human rights activists, despite existing export controls.
"If spyware companies are unwilling to recognize the role that their products play in undermining human rights, or address these urgent concerns, they will continue to strengthen the case for further intervention by governments and other stakeholders," the report says.
- Details
- Category: Security News
Anti-Malware , Network & Perimeter , Risk Management
Zero-Day Flaw Revealed via Equation Group Tool Dump
Cisco has begun releasing software updates for its Adaptive Security Appliance devices to patch a zero-day flaw that was revealed via leaked Equation Group attack tools. Cisco ASA devices provide anti-virus, firewall, intrusion prevention and virtual private network capabilities (see Equation Group Hacking Tool Dump: 5 Lessons).
See Also: How to Mitigate Credential Theft by Securing Active Directory
On Aug. 13, a group calling itself the Shadow Brokers published a 250 MB data dump that contained an assortment of Equation Group tools, including EGREGIOUSBLUNDER, targeting Fortinet-built Fortigate devices; BENIGNCERTAIN, targeting Cisco PIX devices; as well as other tools designed to exploit Juniper and Topsec equipment. The tools, which date from 2013, are widely believed to have been developed by the U.S. National Security Agency for use by its Tailored Access Operations group (see NSA Pwned Cisco VPNs for 11 Years).
So far, only one zero-day vulnerability has been found via the leaked tools, in the attack tool code-named EXTRABACON. "The EXTRABACON exploit targets a buffer overflow vulnerability in the SNMP code of the Cisco ASA, Cisco PIX and Cisco Firewall Services Module," according to Cisco's related security alert. "An attacker could exploit this vulnerability by sending crafted SNMP packets to an affected Cisco product." Successfully exploiting the vulnerability would then give the attacker full control over the system, including the ability to execute arbitrary code.
Cisco warned that all versions of ASA could be exploited.
Hold the EXTRABACON
On Aug. 24, however, Cisco began releasing patches for ASA devices to block the flaw exploited by EXTRABACON. "Cisco has updated the security advisory for the SNMP Remote Code Execution Vulnerability (CVE-2016-6366), which addresses the EXTRABACON exploit," writes Omar Santos, principal engineer in the Cisco Product Security Incident Response Team, in a blog post. "We have started publishing fixes for affected versions, and will continue to publish additional fixes for supported releases as they become available in the coming days."
Cisco says the following devices can likely be exploited via CVE-2016-6366:
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500-X Series Next-Generation Firewalls Cisco ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers Cisco ASA 1000V Cloud Firewall Cisco Adaptive Security Virtual Appliance (ASAv) Cisco Firepower 4100 Series Cisco Firepower 9300 ASA Security Module Cisco Firepower Threat Defense Software Cisco Firewall Services Module (FWSM) Cisco Industrial Security Appliance 3000 Cisco PIX FirewallsTo patch the vulnerability, Cisco's security advisory says users of ASA 7.x and 8.x should update to 9.1.7(9) or later, and users of 9.x should update to patched versions that it expects to release by Aug. 26.
No Fix for PIX Devices
That PIX devices are vulnerable to CVE-2016-6366 is concerning, because Cisco stopped supporting - and issuing updates - for the devices in 2013. Even so, security researcher Mustafa Al-Bassam last week found that at least 15,000 PIX servers are still in use and thus at risk from the flaws targeted by the Equation Group attack tools.
In its security advisory, Cisco says that it will not be patching PIX devices. "Cisco Firewall Service Modules and Cisco PIX Firewalls have passed the last day of software support milestone as stated in the published end of life documents," it says. "Further investigations into these devices will not be performed, and fixed software will not be made available."
Security Researchers First Detailed Risks
The danger posed by EXTRABACON was first revealed Aug. 16, when the Australia-based security researcher known as XORcat confirmed that EXTRABACON could be used to gain remote access to Cisco devices running firmware version 8.4, up to 8.4(4). "The requirements for the ExtraBacon exploit are that you have SNMP read access to the firewall, as well as access to either telnet or SSH," XORcat wrote. "Once the exploit is successful, the attacker will be able to SSH to or telnet to (depending on what protocol is setup on the [firewall]) without needing to enter credentials," unless an SNMP password was enabled for the device.
On Aug. 17, Cisco confirmed that ASA devices were vulnerable to the attack and released related IPS and Snort signatures to help block any attempts to exploit the flaw while it prepped related patches. It also said that related attacks could be blocked if the devices were set to use an SNMP password. This is known as the "SNMP community string," according to Craig Williams, senior technical leader of Cisco's security intelligence and research group Talos.
Cisco ASA SNMP Remote Code Execution vulnerability is a *new defect* - The SNMP community string needs to be known https://t.co/VepFS4X3RZ
But some security researchers have suggested that obtaining the SNMP password would be a trivial task for a sophisticated attacker.
I mean, that's true in a strictly literal sense, but discovering the required information is TRIVIAL. Sigh.
Researchers initially believed that EXTRABACON only worked against ASA devices running 8.x firmware, up to version 8.4.(4). But Hungary-based security consultancy SilentSignal on Aug. 23 reported that its researchers had successfully adapted EXTRABACON to target up to ASA version 9.2(4), which was released in July 2015.
We successfully ported EXTRABACON to ASA 9.2(4) #ShadowBrokers #Cisco pic.twitter.com/UPG6yq9Km2
The takeaway is that it would have been easy for the anyone - NSA or otherwise - in possession of the 2013-era tool set to update it and exploit the latest generation of ASA devices.
Intelligence Oversight Questions for Congress
One unanswered question - beyond the identity of the Shadow Brokers - is how they obtained the attack tools. On that front, Nicholas Weaver, a senior staff researcher focusing on computer security at the International Computer Science Institute in Berkeley, Calif., says it's time the U.S. Senate and House intelligence oversight committees begin asking NSA officials some pointed questions.
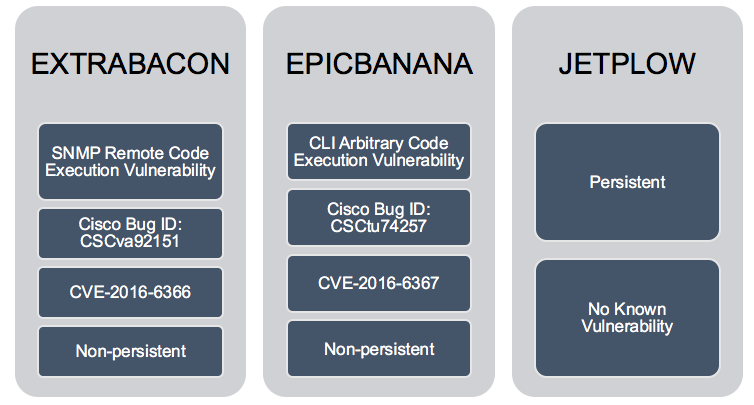 Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.
Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.For starters, when did the NSA know or suspect that one of its firewall attack toolkits had gone missing? "If the NSA knew of the breach of their tools and failed to notify Cisco and Fortinet, this would represent a serious dereliction of the NSA's Information Assurance [Directorate] mission because both of those products are used by the [U.S.] government and on [Department of Defense] systems which IAD is charged with protecting," Weaver writes on the Lawfare blog.
There are three leading theories as to how the tools came to be obtained by the individual or group calling themselves the Shadow Brokers: Hackers infiltrated a top secret system, an insider stole and leaked them, or a member of the NSA's Tailored Access Operations group loaded the tools onto an unclassified server while prepping an attack and accidentally left them there.
Many security experts suspect the third possibility to be most likely, and Weaver says that tools with difficult-to-use interfaces could easily be to blame.
More Articles …
Page 3489 of 3546
