- Details
- Category: Security News
Cybersecurity , Data Breach , Risk Management
A Practical Approach to Digital Clinician and Patient Credentials- Details
- Category: Security News
A series of reports on the threats posed by Russian hackers and how to respond to them highlight the latest edition of the ISMG Security Report.
In this report, you'll hear:
ISMG Security and Technology Managing Editor Jeremy Kirk explain why the FBI is better positioned to attribute the source of the attacks that plague Democratic Party servers; Homeland Security Secretary Jeh Johnson address steps DHS can take to help local and state governments secure the electoral process; Internet Security Alliance Chief Executive Larry Clinton champion the creation of a new U.S. government department focused on cybersecurity; BankInfoSecurity Executive Editor Tracy Kitten analyze the breach of Oracle's point-of-sales business MICROS System.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Aug. 5 and Aug. 9 reports, which respectively analyze why the United States electoral system should be designated as critical infrastructure and the reopening of the encryption bypass debate. The next ISMG Security Report will be Tuesday, Aug. 16.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
Anti-Malware , Encryption , Technology
Ransomware Attackers Unleash Feline-Themed Assault New Hitler-Themed Malware Deletes Files, While Android Victims See Cats Photo: Kishjar (via Flickr/CC)
Photo: Kishjar (via Flickr/CC)Without a doubt, ransomware attackers have no scruples.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
That should have already been obvious from gangs of cybercriminals who show no remorse when it comes to encrypting everything from electronic health records at hospitals, to PCs used by law enforcement agencies, to consumers' precious digital snaps. Gangs have even been creating customer-service teams in an attempt to maximize their illicit profits.
But the latest ransomware attacks go to even further extremes, channeling everything from kittens to Hitler.
New self-described Hitler-themed "ransonware" (sic) was discovered by Jakub Kroustek, a malware analyst at security firm AVG Technologies. The Hitler ransomware's lock screen demands that victims buy a €25 ($28) virtual Vodafone gift card and send attackers the redemption code.
The ransomware appears to be a test version that's not yet ready for primetime, Kroustek says via Twitter. "I guess it is still under 'development,' and this one has leaked," he says.
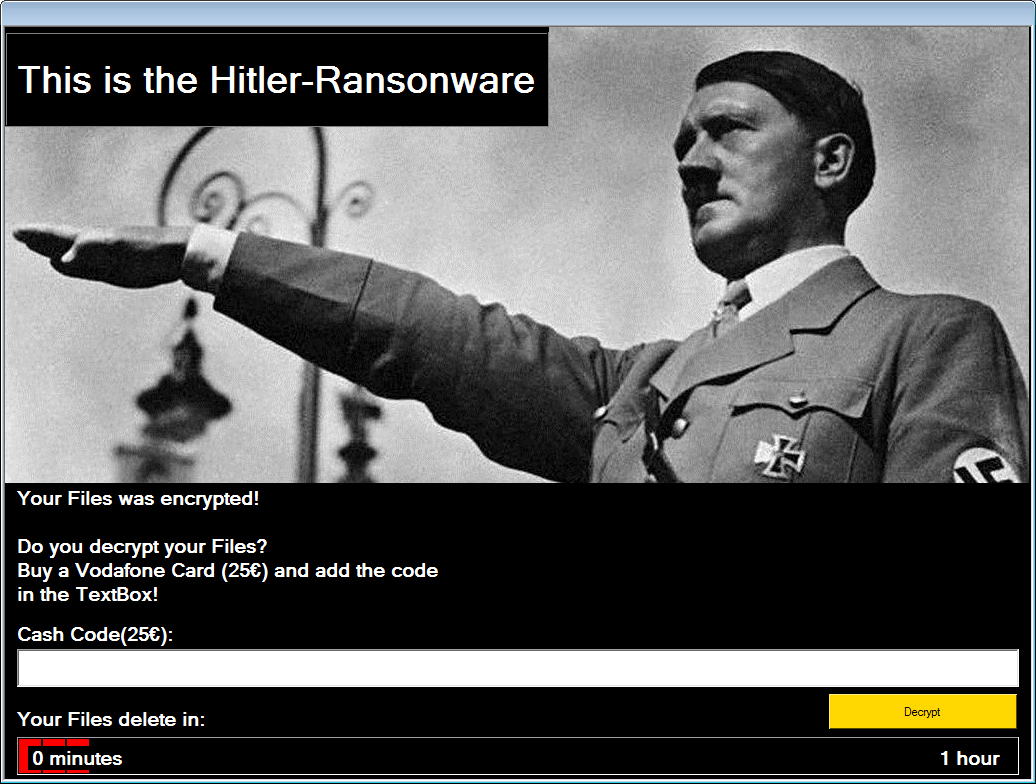 Hitler ransomware lock screen. Source: Bleeping Computer
Hitler ransomware lock screen. Source: Bleeping Computer
So far at least, the ransomware doesn't appear to have been designed to encrypt files. Instead it runs a batch file, which includes German-language comments from the apparent developer, that removes the extensions for certain file types stored in 11 different directories - ranging from a user's pictures and documents folders to their music and desktop directories - and then displays a lock screen with a one-hour countdown timer, according to a technical teardown published by anti-ransomware site Bleeping Computer. After the hour is up, it reports, the ransomware reboots the PC and runs an executable called "firefox32.exe" that deletes all of the files with excised filenames, while also terminating any processes - taskmgr, utilman, sethc, cmd - that a user might invoke to attempt to shut down the malicious file.
Such delete-everything behavior was seen earlier this year via a ransomware variant called Ranscam.
One potential defense against Hitler ransomware attacks, Bleeping Computer says, is to disable Windows automatically restarting after it crashes, which would give victims a chance to scrub their hard drive before the deletion routine starts.
Leave No Meme Behind
To date, ransomware attackers haven't paid too much attention to Android. That's no surprise: Cybercriminals often seem to prioritize attacks that generate maximum revenue for minimum effort, and thus most developers focus on coding Windows malware. With 10 percent of all PCs still running the outdated, insecure and often easy to hack Windows XP operating system, according to market researcher NetMarketShare, why bother creating cutting-edge malware designed to target the relatively small number of people - by comparison - who use Mac OS X, Linux, Android or iOS?
But some developers have been making forays into Android ransomware. One variant that first appeared last year, called FLocker - short for "frantic locker" - is now able to lock Android-powered mobile phones, tablets and smart TVs, demanding $200 worth of iTunes gift cards from victims to unlock infected devices, according to security firm Trend Micro.
Recently, another type of Android ransomware called "El Gato" - Spanish for cat - also debuted, Fernando Ruiz of Intel Security's McAfee Labs Mobile Malware Research Team says in a blog post.
El Gato packs typical malware tricks: it communicates with a command-and-control server to receive instructions, can disable any app that's running on the device as well as forward and delete any SMS messages stored on the device. But the malware can also send SMS messages to the victim, encrypt - or decrypt - all files stored on the device or on any inserted SD cards, as well as display a lock screen with a ransom demand that features a picture of a cat.
As with the Hitler ransomware, however, El Gato appears to be a work in progress, Ruiz says. For starters, the AES algorithm it uses to encrypt files features a hardcoded password, meaning that security researchers can use the app to decode anything that it's encrypted. More advanced forms of ransomware, by contrast, use a unique password for every different ransomware-infected system, making it much more difficult - if not impossible - for victims to decrypt files without paying the ransom (see Ransom Smackdown: Group Promises Decryption Tools).
Ruiz says the ransomware is likely under development and will likely be included in future exploit kits. Also known as cybercrime toolkits, developers sell these to cybercriminals, allowing them to automatically infect large numbers of PCs and - in this case - not only steal data but also attempt to extort victims into paying a ransom.
"This ransomware variant looks like a demo version," Ruiz says.
Lured by the promise of easy pickings, ransomware attacks are booming. As El Gato and the Hitler ransomware demonstrate, developers appear to be testing new ways to meet this ever-increasing demand.
- Details
- Category: Security News
Anti-Malware , Data Breach , Technology
MICROS Breach: What Happened? Potential Russian Cybercrime Gang Link Could Spell Big Trouble
The apparent breach of a system support portal used by Oracle to remotely access and service MICROS point-of-sale systems raised alarms earlier this week, after Oracle warned customers in a letter that it "has detected and addressed malicious code in certain legacy MICROS systems."
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
To date, however, Oracle has remained quiet about just how bad the breach might be. That's concerning, since MICROS Systems - acquired by Oracle in 2014 - builds point-of-sale software and hardware which it says gets used across 330,000 customer sites in 180 countries. Furthermore, security blogger Brian Krebs reports that the attack appears to be linked to the Russian crime ring behind Carbanak, which is banking malware that's been tied to numerous past attacks against retailers and banks.
The Carbanak connection, if true, is very concerning. Security firm Kaspersky Lab links the gang behind Carbanak to a diverse string of attacks against ATMs, money-transfer services and retail POS systems. From 2012 to 2014, the gang also stole an estimated $1 billion from as many as 100 banks in up to 30 countries, including the United States (see New Details About $1 Billion Crime Ring). And security and threat-intelligence firms Group-IB and Fox-IT, which refer to the gang as Anunak, say the group's core hackers appear to have been the developers behind the Carberp banking Trojan (see Russian Ring Blamed for Retail Breaches).
Carbanak malware made a resurgence in the fall of 2015 (see Sophisticated Carbanak Banking Malware Returns, With Upgrades.
Details Scant
In theory, the revelation of an attack against MICROS would have resulted in Oracle releasing extensive details about the breach and its long-term impact. To date, however, no new details have been released.
In fact, things have been eerily quiet on the Oracle front, which raises more questions about what actually happened, when it happened, who was impacted, what data - if any - was comprised and who launched the attack.
Oracle Confirms Breach
Oracle's letter to MICROS customers notes that it "detected and addressed malicious code in certain legacy MICROS systems." The company adds that its corporate network and other service offerings, including its cloud services, were not affected, and that payment card data is encrypted "at rest and in transit in the MICROS-hosted environment."
Still, Oracle says it is requiring MICROS customers to change their passwords for all MICROS accounts, and "recommends" that passwords for any accounts used by MICROS representatives to remotely access POS systems also be changed.
"To prevent a recurrence, Oracle implemented additional security measures for the legacy MICROS systems," the letter adds.
Still Seeking Answers
But Oracle has left a lot of questions unanswered, such as:
When was the malware detected? When did the malware start infecting systems? How many MICROS customers were likely impacted? Is the attack linked to Carbanak?Oracle also makes no mention of a breach of its customer service portal, but alludes to it in its recommendation to change any passwords for accounts that get remotely accessed by MICROS representatives.
To date, Oracle has declined to comment further, beyond what it stated in its customer letter. But experts such as Gartner analyst Avivah Litan say the breach at MICROS could be to blame for a number of the retail breaches we've seen over the past two years. "This could explain a lot about the source of some of these retail and merchant point-of-sale hacks that nobody has been able to definitively tie to any one point-of-sale services provider," Litan tells Krebs. "I'd say there's a big chance that the hackers in this case found a way to get remote access," to MICROS customers' POS devices.
As noted, Oracle says MICROS POS systems used at more than 330,000 locations across 180 countries. "MICROS offers a range of software, hardware and related services along with rapidly growing cloud solutions to manage hotels, food and beverage facilities, and retailers," the company says.
Depending on how many of those customers use legacy systems, the impact of this breach could be far-reaching, says John Buzzard, a fraud specialist at CO-OP Financial Services, a credit union network that provides ATM, card payment and mobile services.
"I think it almost goes without saying, but this sort of complicated, layered attack is exactly why we tell everyone to vary their usernames and passwords across all systems," Buzzard says. "A ticketing system (like MICROS POS) is capturing a user ID and password that link to a professional persona that many of us are guilty of replicating over and over for ease of use. What gets you logged into one system may very well work in other systems, too."
Service Providers: A Growing Vulnerability
One big takeaway from the MICROS breach is that there are growing concerns over the risks that remote access poses to retailers and payments processors, says Al Pascual, head of fraud and security at Javelin.
"Over the past few years there has been an increased level of concern over risks inherent to third-party providers, which has led to action by various regulatory bodies," Pascual says. "PCI was inspired to release updated guidance by the compromise of terminal manufacturers and platforms that were cited in several large-scale, distributed breaches of smaller merchants. And the OCC [Office of the Comptroller of the Currency] began calling out these risks after large processors were breached, which subsequently led to action by the FFIEC [Federal Financial Institutions Examination Council]. At the end of the day, though, many of the breaches that inspired these regulatory responses were facilitated by remote access and the misuse of default or compromised credentials. It is a bit ridiculous that we keep having the same conversation around the need for strong authentication, especially in environments that protect payment data."
And Tom Kellermann, CEO of technology investment firm Strategic Cyber Ventures, says in an Aug. 9 blog post post that third-party service providers are increasingly being targeted by cybercriminals, because they have been "slow to adopt intrusion suppression technologies and, thus, have become the weak links."
Indeed, many of the retail breaches that come to light now appear to be tied to POS system vulnerabilities that can be exploited via remote access (see POS Remote Access: A Worry for Merchants).
That's why, in the coming weeks, Oracle needs to begin releasing more details about which of its customers were affected, and when, by the malicious code that it found in MICROS. Without a timeline, it's hard to know just how concerned any of us should be.
And while definitive attribution of this attack to the so-called Carbanak gang isn't likely, this gang's possible connection seems logical, and could spell big trouble for the state of POS attacks to come.
- Details
- Category: Security News
Anti-Malware , Endpoint Security , Technology
Better Ransomware Detection: Follow the Shouting Unique Behavior Holds Key to Better Defenses, Researchers Say Northeastern University Professor Engin Kirda
Northeastern University Professor Engin KirdaIt's too soon to predict the decline of ransomware, the file-encrypting malware that poses a large and increasing risk to businesses and organizations. But it's the current obsession for the security industry. And while some computer security vendors claim their products can stop it, far too much ransomware is still bypassing defenses. As with any cybercriminal scam, though, the more attention it draws, the faster attackers' window of opportunity closes as defenses improve.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
At the 25th Usenix Security Symposium in Austin, Texas, this week, a team of researchers from Northeastern University in Boston presented a new method to detect ransomware, called Unveil, and they report that it's proved highly effective in testing.
Ransomware "is very simple attack that's simple to prevent if you have good backups," says Engin Kirda, a professor in the computer and information science department at Northeastern. "The reality is: People are bad at it. They don't have backups. They lose their data. Ransomware is exposing this big issue that we've always seen and known about, but now it's becoming more mainstream."
The Fakeout
To help, the research team's idea was to build a system that could be layered on top of technologies known as "sandboxing," which isolate executable code for analysis before passing clean code into an environment, Kirda says.
By design, Unveil appears to be a legitimate user environment, full of attractive files that ransomware code would target. That's a decoy technique being increasingly embraced by the security industry to lure hackers and study their movements in a system, without tipping them off that it's actually fake.
To try and block security researchers and law enforcement agencies, many ransomware developers code their malicious applications to detect when they've has been trapped in a sandbox, and if so to stop working. Kirda notes that many security firms continue to build new sandbox techniques that are designed to analyze malicious code, and attackers continue to bolster their defenses against these more advanced sandboxing environments.
But the Unveil researchers took a different approach, opting for a relatively unsophisticated sandbox, and found that they could find ransomware samples that more advanced sandboxing environments failed to detect.
Unveil's detection capabilities are centered on the unique ways that ransomware functions: it makes large-scale changes to file systems unlike other types of code. That same broad technique is similar to another academic project I wrote about called CryptoDrop (see Researchers Unleash Ransomware Annihilation).
If a process starts to make changes to a file's entropy - or randomness - it's a good clue that ransomware is at work. Accordingly, Unveil has direct access to data buffers that are involved in input and output requests, which allows it to monitor file system changes.
"I think the good thing about ransomware - people usually talk about the bad things - is that it has very distinct behaviors," Kirda says. "Ransomware actually shouts at you. It says, 'Hey, I just infected you.' These are behaviors that are in a way actually good for a defender because these are things that you can specifically look for."
A key difference between ransomware and other malware is it usually displays a prominent notification asking for payment. Unveil monitors the desktop, taking automatic screenshots of what it displays before and after a suspect executable is detected. It uses optical character recognition for changes, looking for keywords such as FBI, bitcoin and ransom.
"These are very suspicious words that a typical user will not always see," Kirda says.
No False Positives
Unveil was tested against 148,223 malware samples and correctly picked out 13,637 ransomware samples without any false positives, according to the group's research paper. It even picked out what was an unknown ransomware family, called SilentCrypt, that was able to bypass the sandboxing technology of a "well-known anti-malware company," the paper reads. Papers accepted for the Usenix go through a blind review by a program committee of vetted academics and experts.
Ransomware is able to fool many security products because attackers use compression and packing techniques to make what are essentially the same executable files appear different. Many anti-virus products rely on files that describe patterns of known malicious code - referred to as signatures - but repacked code can often evade those checks.
Unveil was developed by one of Kirda's students, Amin Kharraz, along with Sajjad Arshad, Collin Mulliner and William Robertson, all of Northeastern. Kirda is the founder of the computer security firm Lastline, but the research on Unveil is in the public domain. What the team developed is just a prototype, and other companies or organizations are free to take the ideas and develop it further. Kirda expects that Lastline also will implement some of the techniques in its products.
"The information is going to be out there," Kirda says. "It's online for everybody."
More Articles …
Page 3481 of 3546

 Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities."
Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
Different options to provide better patient and provider electronic authentication;
How superior identity management naturally leads to improved HIPAA and HITECH compliance;
How to implement remote ID verification;
How to secure end-to-end communications between patients and providers.
You might also be interested in …
Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities."
Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
Different options to provide better patient and provider electronic authentication;
How superior identity management naturally leads to improved HIPAA and HITECH compliance;
How to implement remote ID verification;
How to secure end-to-end communications between patients and providers.
You might also be interested in …