Cybersecurity , Data Breach , Governance
Network Intruders Exploit Your Vulnerabilities - Defend Yours. Attack Theirs.- Details
- Category: Security News

Do you have $100,000 burning a hole in your pocket and an abiding love of bitcoins? If so, then the U.S. Marshals Service has an offer you can't refuse.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
On August 8, the Marshals Service (part of the Department of Justice) announced that it's auctioning 2,719.32669068 bitcoins obtained by the U.S. government via forfeitures related to nine different cases - some federal, others civil or administrative. At current exchange rates, those bitcoins would be worth $1.6 million.
Now, the Marshals Service is planning to sell all of those bitcoins in a single block to the highest bidder, having been "granted authority to manage and sell these bitcoins through court orders" related to the nine cases.
Until 12pm ET on August 18, anyone of any nationality - provided they're not on the U.S. Treasury Department's Office of Foreign Assets Control list of "Specially Designated Nationals" - who wants to bid for the bitcoins can register with the Marshalls Service. Would-be bidders must provide some personal details, including a copy of a government-issued photo ID, their name, address, phone number, email address and taxpayer identification number. Any non-publicly traded entities or syndicates who want to register, meanwhile, must list personal details relating to anyone who's an officer of the company, owner, trustee or on its board of directors.
Would-be bidders must also send $100,000 - payable in U.S. dollars only - as a deposit to the Asset Forfeiture Fund at the Federal Reserve Bank of New York. The wire transfer must originate at a U.S. bank.
"The USMS will notify all bidders about their eligibility to participate in the auction by email no later than 5:00 PM EDT on Thursday, August 18, 2016," the auction notice reads. "If the USMS determines that you are not an eligible bidder, the deposit funds will be returned, and you will not be eligible to participate in the online auction."
Everyone else will get the heads-up that they're eligible to participate and then be allowed to submit a single, signed bid on Aug. 22, between 8:00 a.m. and 2:00 p.m. Eastern Time. "You will not have the opportunity to view other bids. You will not have the opportunity to change your bid once submitted," the auction notice states.
By 5 p.m. that day, the Marshals Service says that it will select and notify the highest bidder, who will then have until Aug. 23 at 2 p.m. to wire-transfer the funds in full from a U.S. bank. "Failure to provide the USMS with a copy of the wire transmittal receipt by the deadline will result in disqualification, forfeiture of the deposit, and award to another bidder," it says.
Dread Pirate Roberts' Treasure
This is the fifth bitcoin auction to be held by the Marshals Service. The most recent auction, in November 2015, involved 44,341 of the up to 144,000 bitcoins that were seized from Ross Ulbricht, a.k.a. Dread Pirate Roberts, which were mostly sold in auction blocks of 2,000 bitcoins each. Ulbricht was convicted of running the notorious darknet marketplace Silk Road and received a life sentence. Previous auctions have reportedly also sold bitcoins seized from Silk Road users.
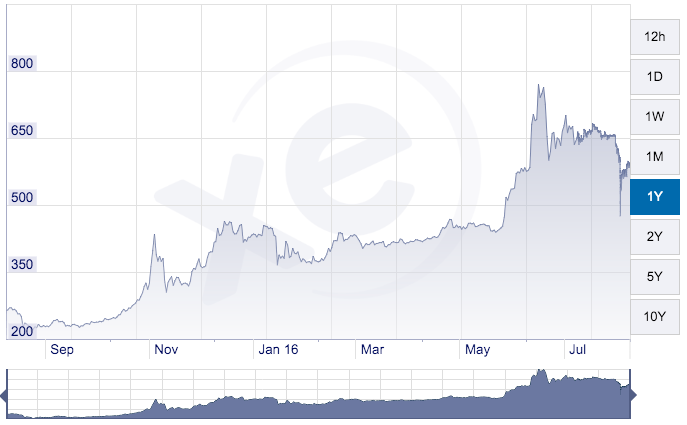 The value of a single bitcoin, in U.S. dollars, from August 2015 to August 2016. Source: XE Trade.
The value of a single bitcoin, in U.S. dollars, from August 2015 to August 2016. Source: XE Trade.
What makes this latest block of bitcoins special is that it includes not just bitcoins forfeited by Ulbricht, but also by Carl M. Force IV, formerly a special agent with the Drug Enforcement Administration who'd been assigned to a Silk Road task force. The 15-year DEA veteran pleaded guilty last year to stealing $820,000 worth of bitcoins while helping to run the U.S. government's investigation. In October 2015, he was sentenced to serve a 6.5-year prison sentence.
Anonymity Guaranteed
As with all things cryptocurrency, however, these bitcoins' provenance is no guarantee of their future value. Or as the Marshals Service says, "the USMS does not make any representations or warranties regarding bitcoin."
Appropriately for a pseudonymous cryptocurrency, however, the Marshals Service does promise anonymity. "The USMS will not release any information to the general public pertaining to the auction process or results, except for the number of registered bidders and the number of bids received."
Bitcoin fans: Start your bidding.
- Details
- Category: Security News

Did security researchers at financial solutions provider NCR unveil a security flaw with EMV - one that could allow hackers to steal card data from EMV chips and clone it on magnetic stripes?
See Also: The Inconvenient Truth About API Security
At the recent Black Hat USA conference in Las Vegas, point-of-sale security researchers at NCR (which sells, among other things, POS terminals, software and encryption solutions) reportedly demonstrated how fraudsters could fool POS terminals into thinking chip cards are actually chipless by altering mag-stripe data contained on those cards.
In a report about the alleged security flaw, CNN Money notes that NCR findings uncover a "glaring hole" in EMV, namely because when upgrading POS systems to accept EMV cards, retailers also need to deploy end-to-end encryption - which would render stolen card data useless.
But some security and payments experts balk at the research, saying the demo only proves what we already knew - that mag-stripe data remains vulnerable to attack, even if it exists on an EMV card. What's more, they argue that the demo's findings are self-serving and misleading, since end-to-end encryption, which demo researchers recommend as a solution, is a service NCR sells.
End-to-end encryption, experts say, would not prevent cloned mag-stripe data from being accepted at a POS device, though it could prevent card data from being compromised in transit, thus preventing mag-stripe data from being stolen in the first place.
That, however, would not prevent the type of attack demoed at Black Hat, says financial fraud expert and Gartner analyst Avivah Litan.
Fooling the System, Not Breaking the Tech
"Stealing the data is a different issue," she says. "The issue that's being talked about here is similar to what we saw in Brazil, when criminals stole mag-stripe cards and pushed them through as EMV transactions."
The vulnerability demoed by NCR basically hinges on the same concept, Litan adds. "It's a bit of a different twist, but along the same lines," she says. "The common theme here is that the criminals know the codes on the cards and in the POS systems, and they know how to manipulate them."
It's a huge problem - but not one that is new, Litan says.
"I heard about this a few months ago from the card companies," she says. "It's not really a technology flaw - it's a flaw in the technology process. In other words, there is a code on the mag-stripe that tells the card reader if the card is a chip or mag-stripe card. If the criminals change that mag-stripe's value on a chip card to say it's a mag-stripe card, they can use a counterfeit card, and the chip security features are not used."
Among issuers, this type of fraud is known as "fall-back" fraud, and it seems to be a growing problem.
In addition to Litan, I first heard about "fall-back" more than a month ago, when a respected banking leader told me about a new type of POS attack that was pushing fraud back on to issuers. He asked not to go on the record just yet, as more details about how the fraudulent transactions are actually fooling the POS are still being uncovered.
Based on what I know so far, this is the attack in a nutshell: Attackers are using counterfeit mag-stripe cards for accounts that the bank has already transitioned to EMV. The fraud "falls back" to the issuer, because the retailer says a mag-stripe was presented. See where the confusion comes in?
How Are Hackers Getting the Numbers?
In spite of EMV, what's likely perpetrating so-called fall-back fraud is the number of debit and credit cards that were breached before EMV was widely deployed. Fraudsters have all of these numbers and are still using them.
Use me as an example: Even though my bank has issued a chip card for me, the account number is the same as my old mag-stripe card. If my card was compromised at some point in the past, before I was issued an EMV card, then it's possible that fraudsters could create a cloned mag-stripe card with that old card data.
And even though today my account is associated with a chip, if a cloned account is presented at the POS, the system won't recognize a chip and will push the payment through as a mag-stripe transaction.
"The banks are getting hit with the fraud and blaming the retailers for not accepting those cards as chip cards," Litan says. "And the retailers have been telling the banks that the card was presented as a mag-stripe card."
The researchers who gave the demo at Black Hat could not be reached for comment.
Randy Vanderhoof, executive director of the EMV Migration Forum, a cross-industry body focused on supporting EMV chip implementation technology and processes in the U.S., says the fall-back fraud issue could be a legitimate one for banks. But the issue is not linked to a vulnerability in EMV.
"This is not an attack on EMV technology; it's an attack on the magnetic stripe," he says. "If the data on the magnetic stripe is altered, it might fool the terminal, but when the authorization request gets to the issuer, they can recognize it was altered because they know what information should be on the magnetic stripe, and will, therefore, reject the transaction. These kinds of risks with magnetic stripe cloning or altering is exactly the kind of problem that EMV is best at preventing."
The problem, as Litan points out, is that when the request gets to the issuer, there is a discrepancy. If fraudsters are successfully manipulating the code on the mag-stripe to fool the POS into thinking the card is a mag-stripe, not a chip, then what can be done to detect this kind of manipulation?
Should the card brands address this concern, or should it fall upon EMVCo, the global body that manages specifications and testing processes for the Europay, MasterCard, Visa standard?
What do you think?
- Details
- Category: Security News
In today's environment, federal and state regulators come at breached companies from all angles, with requests for investigative information, breach response plans and fines. Attorney Deborah Gersh, co-chair of the healthcare practice at law firm Ropes & Gray LLP, says it's easy for organizations to become overwhelmed when numerous regulators demand answers simultaneously in the wake of a breach. By having well-defined breach response plans in place before an incident, however, organizations can streamline their procedures to ensure compliance without damaging their reputations.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
"There have been quite a few developments recently, and I think it has to do with the fact that certain agencies think that another agency may not be doing their job as effectively as possible, or that they feel that they have a particular interest in a particular case that is unique to them," Gersh says in this video interview with Information Security Media Group. "For example, with the [Federal Trade Commission], they view themselves as the champions of consumer protection and consumer rights, and it may very well be that if the FTC does not feel that another agency, such as the OCR, Office of Civil Rights, is taking on a particular action, then they will step in to do so. It also has to do with advocating for their particular consumers, and it also has to do with the fact that, I think, they're looking to expand their jurisdiction."
In this interview recorded at ISMG's recent New York Fraud and Breach Prevention Summit, Gersh also discusses:
Common mistakes breached organizations make when regulators come knocking; Dealing with numerous regulatory bodies seeking actions against a single breached entity at one time; Steps attorneys can take to help clients address regulatory inquiries with consolidated approaches.Gersh has more than 25 years of experience advising a wide range of healthcare companies and investors about sophisticated regulatory and enforcement matters, as well as acquisitions and sales of healthcare entities. Her clients include pharmaceutical manufacturers and medical device companies, managed-care companies, dental-service organizations and practice-management companies, as well as academic medical centers and community hospitals. Gersh counsels clients on a range of compliance matters, including design and implementation of corporate compliance programs and negotiation, and implementation of corporate integrity agreements.
- Details
- Category: Security News
CISO , Governance , Video
Converged Programs Allow Faster Response, Lower Costs, Says ADP's CloutierSecurity leadership has come a long way since the days when the CIO - and later CSO or CISO - was required to just be an information security or "cyber" expert. Running a security department now requires not just technical acumen but also business acumen. But the best organizations take it even further, by creating converged programs, says Roland Cloutier, CSO of Roseland, NJ-based global business outsourcing services provider ADP.
Conceptually, this isn't a complicated approach. "Convergence is simply this: managing your security business better, for your business," he says.
See Also: Data Security Risk: A CISO's Perspective
In information security terms, for many organizations convergence means tasking a single executive to oversee not just information security, but also privacy and risk, he says.
In this video interview at Information Security Media Group's recent New York Fraud and Breach Prevention Summit, Cloutier discusses how this convergence facilitates:
Faster decision-making and incident response; Better transparency and cost management; More centralized visibility into all security, privacy and risk-related processes.Prior to working for ADP, Cloutier served as CSO of EMC, vice president of cybersecurity for Paradigm Technology Partners - acquired by Aimnet Solutions - and was the founder of Brac Solutions. For nine years, he also worked in law enforcement for the U.S. government, serving as an agent for the U.S. Air Force Combat Security Police, as a Defense Department Aerospace Protection Specialist, and as a police detective for the Department of Veterans Affairs. In November 2015, Elsevier published Cloutier's first book, "Becoming a Global Chief Security Executive Officer."
- Details
- Category: Security News
More Articles …
Page 3480 of 3546



 Disrupting the Cyber Kill Chain by Choking the Attack Where it is Most Vulnerable
API's, Server Integrity and Identities
Our adversaries follow a fairly well defined process of gaining access, establishing residency and exploiting our networks. If we understand how they act during each of these phases then we can make huge strides in curtailing their malicious endeavors. This session examines some best practices for defeating each phase of the attack:
Getting In With the growing deployment of inter application communications, attacks such as those at SnapChat, Yahoo and Tesla are increasingly leveraging insecure API's as entry points into networks. This webinar will examine why API protection must be implemented to minimize these vulnerabilities.
Staying In - Malicious code is very vulnerable while it is being installed and as it attempts to become resident. We'll explain how continuously refreshing the integrity of servers prevents malware from establishing a foothold.
Acting - If you have the keys to every door in a house, there is no need to hack through each door individually. Since one of the primary targets for attackers are credentials, they go after those with extensive privileges to a broad array of resources within your infrastructure in order to expedite their penetration. We'll see how to implement fine grained access control by granting authorization and access to resources only to those individuals that need it, decreasing the vulnerability of more users.
The "Cyber Kill Chain," adapted by Information Security Media Group experts from the military "Kill Chain" concept, has been demonstrated thoroughly over the past several years. Some of the most famous retail breaches, including the more recent OPM breach, are examples of successfully executed cyber kill chains.
Threat actors rely on their ability to:
Gain access to the network;
Remain on the network without being identified in a timely fashion;
Take action on the network.
While some see these as opportunities to exploit, they are also opportunities to shut-down and eliminate and attack.
Hear from industry experts on how to:
Keep the bad actors out of your network;
Keep the threat from staying in the network; shut down any breach by cycling systems;
Keep threat actors who have made it into the network from taking any action.
You might also be interested in …
Disrupting the Cyber Kill Chain by Choking the Attack Where it is Most Vulnerable
API's, Server Integrity and Identities
Our adversaries follow a fairly well defined process of gaining access, establishing residency and exploiting our networks. If we understand how they act during each of these phases then we can make huge strides in curtailing their malicious endeavors. This session examines some best practices for defeating each phase of the attack:
Getting In With the growing deployment of inter application communications, attacks such as those at SnapChat, Yahoo and Tesla are increasingly leveraging insecure API's as entry points into networks. This webinar will examine why API protection must be implemented to minimize these vulnerabilities.
Staying In - Malicious code is very vulnerable while it is being installed and as it attempts to become resident. We'll explain how continuously refreshing the integrity of servers prevents malware from establishing a foothold.
Acting - If you have the keys to every door in a house, there is no need to hack through each door individually. Since one of the primary targets for attackers are credentials, they go after those with extensive privileges to a broad array of resources within your infrastructure in order to expedite their penetration. We'll see how to implement fine grained access control by granting authorization and access to resources only to those individuals that need it, decreasing the vulnerability of more users.
The "Cyber Kill Chain," adapted by Information Security Media Group experts from the military "Kill Chain" concept, has been demonstrated thoroughly over the past several years. Some of the most famous retail breaches, including the more recent OPM breach, are examples of successfully executed cyber kill chains.
Threat actors rely on their ability to:
Gain access to the network;
Remain on the network without being identified in a timely fashion;
Take action on the network.
While some see these as opportunities to exploit, they are also opportunities to shut-down and eliminate and attack.
Hear from industry experts on how to:
Keep the bad actors out of your network;
Keep the threat from staying in the network; shut down any breach by cycling systems;
Keep threat actors who have made it into the network from taking any action.
You might also be interested in …