- Details
- Category: Security News
Breach Preparedness , Cybersecurity , Data Breach
Internet of Things: Hacker Eavesdropping Smorgasbord Sheer Network Scale Offers Hope for Solving Related Challenges Phil Reitinger of the Global Cyber Alliance
Phil Reitinger of the Global Cyber AllianceImagine the cybersecurity implications of a world in which hundreds of millions of people have a physical impairment that leaves them internet-connected.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Thanks to the "internet of things," that scenario is fast becoming reality in the form of internet-connected hearing aids. But like so many aspects of the internet of things, such devices carry upsides as well as big, potential data breach downsides, according to Phil Reitinger, the chief executive of the Global Cyber Alliance. He formerly was the Department of Homeland Security's top cybersecurity official as well as CISO for Sony.
In an opening keynote presentation Aug. 2 at Information Security Media Group's Fraud & Breach Prevention Summit New York, Reitinger noted that unlike some internet of things devices - toasters come to mind - internet-connected hearing aids, which are still in their infancy, offer a lot of promise for improving users' quality of life. When a user is watching a television show, for example, their hearing aids could identify the audio and instead of amplifying it, begin downloading a live audio stream of the broadcast.
But what happens when internet-enabled hearing aids enter the workplace? As with smartphones, the devices would be a natural target for attackers, because they could be exploited and used to facilitate remote surveillance, allowing hackers to "hear" whatever the wearer hears. And that would create risks for any such device wearer who works for an organization with access to classified or sensitive information.
Without appropriate safeguards being put in place, Reitinger claimed we risk a future in which attackers could perpetrate targeted breaches with little risk of their attacks being spotted or traced.
In that sort of a future, "things like the DNC [Democratic National Committee] hack, those are small potatoes ... because a huge number of people are walking listening devices," Reitinger said. "Everything is connected, everything is tied together."
Security Essential: Think Big
Everything will only continue to become more connected, and more data generated; that's our inevitable internet of things future. But from a security standpoint, it's possible to avoid some doomsday-style scenarios, provided we make some related moves, chief among them building networks that are as big as possible, Reitinger said.
"Right now, I think the bad guys have almost all of the advantages," he said. "But ... it's much tougher on the good guys than the bad guys. The bad guys operate at scale much better than the good guys."
Defenders, however, can learn to operate at scale, too. "We have to have an ecosystem that takes advantage of the one thing that the good guys and girls have, and that's the size of the network," he said.
At first glance, network size might seem to be a disadvantage, because it makes systems more complex and thus more difficult to secure. But larger networks also give organizations the ability to create what many organizations and vendors have been pushing for in recent years - larger sensor platforms, in which each endpoint or node can be tied into a massive, distributed security monitoring system. Together with better analysis and automation tools, these sensor platforms could be built to better spot an emerging attack, "acting like a biodefense system" that shuts the attack down, Reitinger said.
Some attacks would still get through, but such a system would enable defenders to more quickly block them, and continue to block them.
Short Term: Getting Worse
Of course, this approach might take decades to put into place. "My opinion is that things are very bad right now ... [and] that things are going to get worse, for at least the next 10 years," Reitinger said.
Even so, it's important to start identifying solutions to small parts of the problem now, finding ways to solve them and then building on that success, he said. In a call to arms that applies not just to addressing the internet of things but any enterprise information security challenge, no matter how insurmountable it might seem, Reitinger proclaimed: "Don't admire the problem - try to find something to solve, and then solve it."
- Details
- Category: Security News

The theft of $69 million worth of bitcoins from a Hong Kong-based exchange highlights the continuing challenges around keeping large quantities digital currency out of the reach of hackers.
See Also: How to Mitigate Credential Theft by Securing Active Directory
Bitfinex, one of the largest U.S. dollar bitcoin exchanges, said on Aug. 2 that it lost 119,756 bitcoins after its platform was hacked. Law enforcement has been contacted, the company said in a statement.
Bitcoin's market rate dropped 20 percent following Bitfinex's announcement, although it has since bounced back to about $580. The company's losses amounted to approximately $69 million, according to exchange rates on Aug. 4.
Bitcoin is a virtual currency that is exchanged using peer-to-peer software. Transactions are verified by computers contributing data to a cryptographic ledger known as the blockhain, which is increasingly being explored by the finance industry for broader applications.
Zane Tackett, Bitfinex director of community and product development, writes on Reddit that the company is evaluating its options for addressing customer losses.
"At this time we don't have any details that we can share on this, nor have we made any decisions regarding this," Tackett writes. "We'll continue to push out updates on this as information becomes available."
Tackett refuted a suggestion that the theft might have been an inside job, but he did not share details how the exchange was compromised.
"We have a pretty small team and most of us have been here for a while," he writes. "We also have strict permission limits for who has access to what. Furthermore, I've been on the phone with our entire team and am nearly 100 percent certain that nobody on our team did this."
Bitfinex says in a status update that it is trying to restore limited functionality that will allow customers to view their accounts. However, bitcoin trading will remain suspended.
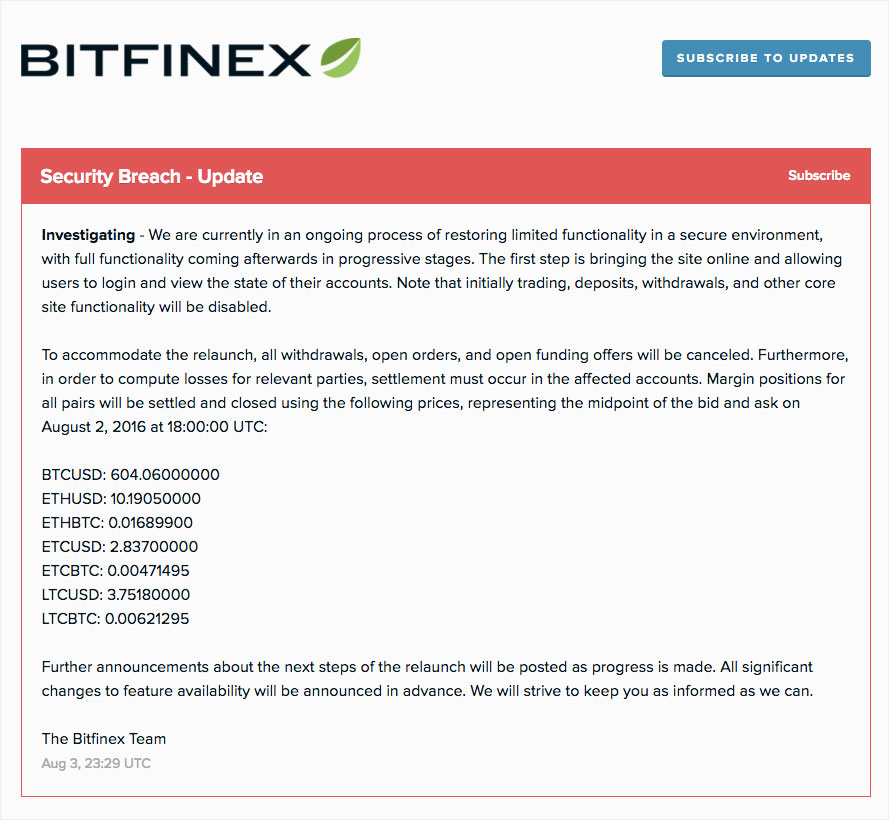 Notice from Bitfinex posted online
Notice from Bitfinex posted onlineSecond Largest Loss
Bitfinex's losses are the second largest behind Mt. Gox, the Tokyo-based bitcoin marketplace that collapsed in February 2014. The exchange lost 850,000 bitcoins, worth about $474 million, but later found 200,000 of those bitcoins (see Bitcoin Trading Website Goes Dark).
Mt. Gox blamed the loss on a security issue called transaction malleability. But Japanese prosecutors charged CEO Mark Karpeles in September 2015 with embezzlement for allegedly transferring some funds from the exchange into accounts he controlled. It remains unknown who stole the majority of the bitcoins, and Mt. Gox is still in liquidation proceedings.
In June, hackers stole $55 million worth of ether, another digital currency, in an attack against an experimental investment fund called the Decentralized Autonomous Organization (see $55 Million in Digital Currency Stolen from Investment Fund). Ether developers made a software modification to the virtual currency's code that froze the funds.
Despite numerous exchange hacks and scammers, supporters of digital currencies have remained largely positive about the potential to revolutionize what they contend is an antiquated financial system.
But security breaches are a reminder of the vulnerabilities of cryptocurrency technologies, writes Peter Van Valkenburgh, director of research at the Washington-based Coin Center, which is a digital currency advocacy group.
"Every hack is also an opportunity to learn and grow resilient: Let's make sure we don't learn the wrong lessons this time around by drawing hasty conclusions," he writes.
Tough to Secure
A bitcoin is actually just a secret number. To transfer a bitcoin, a person must verify a planned transaction with a private encryption key. But if the private key is stolen, the attacker can steal the bitcoin.
Because all bitcoin transactions are recorded in the public blockchain, it is possible to follow the movement of stolen coins. Bitcoins are transferred between 34-character alphanumeric addresses, which appear in the blockchain.
Bitcoin addresses don't reveal information about who controls the funds. But stolen funds are often difficult to convert to fiat currency. Exchanges usually have strict identification requirements for account holders to comply with anti-money laundering regulations. Suddenly cashing out a large quantity of stolen bitcoins at a reputable exchange from a closely watched bitcoin address is unfeasible.
Bitcoin marketplaces employ a variety of methods to protect their vaults and the private keys for the bitcoins. But the companies are highly attractive targets because stolen bitcoins can be nearly impossible to recover. Unlike bank wire transfers, bitcoin transactions are irreversible.
Raising the level of security around bitcoins invariably makes the virtual currency more cumbersome to access, which is why exchanges must make difficult trade-offs.
"There is a balance between security and convenience," says Antony Lewis, a Singapore-based adviser on blockchain technology. "Customers say they want security, but their behavior suggests they prefer convenience. Exchanges who cater to this and put private keys on online machines put themselves at a higher risk of attack."
- Details
- Category: Security News
Breach Notification , Breach Response , Data Breach
Payment Card Data as Well as Patient Information Exposed
Arizona-based Banner Health, which operates 29 hospitals, says it's notifying 3.7 million individuals that their data was exposed in a "sophisticated cyberattack." The organization has hired a forensics firm to investigate the attack after taking steps to block the attackers and contacting law enforcement officials.
See Also: Data Center Security Study - The Results
The data breach, which started when attackers gained unauthorized acess to payment card processing systems at some of the organization's food and beverage outlets, apparently also opened the door to the attackers accessing a variety of healthcare-related information, Banner Health says in an Aug. 3 statement. But the statement doesn't make clear how that additional access was gained.
On July 7, Banner Health discovered the hack of card processing systems that exposed cardholders' names, card numbers, expiration dates and verification codes as the data was being routed through the affected systems, the organization reports. Cards used at affected outlets between June 23 and July 7 were affected. Card transactions used to pay for medical services were not affected.
Affected individuals are being offered one year of credit and identity theft monitoring services. Plus, Banner Health says it's "further enhancing the security of our systems to help prevent something like this from happening again."
In addition to the card-related breach, "On July 13, Banner Health learned that cyberattackers may have gained unauthorized access to patient information, health plan member and beneficiary information, as well as information about physician and healthcare providers," the organization says in the statement, without offering further explanation. Data exposed could include patient names, birthdates and addresses as well as clinical details, such as physician names, dates of service, claims information "and possibly health insurance information and Social Security numbers." Also potentially exposed were physicians' names, addresses, dates of birth and Social Security numbers.
The investigation revealed that the attack was initiated on June 17, Banner Health reports.
Banner Health did not immediately respond to an Information Security Media Group's request for additional comment.
All Data At Risk
The eye-opening report of a breach affecting both payment card transactions and patient data highlights that "healthcare must consider all aspects of its business when addressing security," says security expert Mac McMillan, CEO of the consulting firm CynergisTek.
Attacks targeting the payment card systems of retailers - including high-profile attacks against Target and Home Depot - have become common in recent years, but few have been publicized in the healthcare sector.
"Although this is not necessarily a new phenomenon, covered entities and business associates need to not only keep a close eye on HIPAA privacy and security attacks/breaches, but also ramp up their Payment Card Industry Data Security Standards compliance efforts," says security and privacy expert Thad Phillips, principal consultant at tw-Security. "These PCI DSS compliance efforts include not only their financial departments, but also any food, beverage and gift shop points of sale that are accepting and processing credit card payments."
The healthcare sector, a leading target for hacker attacks due to the value of health data, "cannot expect that PCI DSS compliance will take care of itself while they are primarily focused on HIPAA privacy and security [compliance]," Phillips says. "Once the attacker is in any system on the network, the chances of them breaching additional systems within the organization are much higher. Thus, the organization's overall risk can't go anywhere but up."
Dan Berger, CEO of the security consultancy Redspin, says the Banner Health attack "underscores the necessity to conduct truly comprehensive network security assessments, including external and internal penetration testing. One has to assume that any device, system or workstation that connects to the network is a potential entry point for hackers."
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
More Articles …
Page 3475 of 3546
