Cybersecurity , Data Breach , Healthcare Information Exchange (HIE)
Healthcare is Infected With Ransomware; How Do We Treat it?- Details
- Category: Security News
Breach Response , Data Breach , Encryption
Ransomware Gang Allegedly Dumps Rival's Crypto Keys Leak of 3,500 Chimera Crypto Keys Claimed by Petya Ransomware Developers
Honor among thieves? At least in the ransomware space, don't bet on it.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
Witness the Petya ransomware gang this week claiming to have released 3,500 crypto keys stolen from developers behind the rival Chimera ransomware project.
"It should not be difficult for anti-virus companies to build a decrypter with this informations (sic)," the Petya developers said in a post to Pastebin that includes a dump of the alleged keys, in hex format.
The dump was first announced July 26 via a tweet from @JanusSecretary, which appears to be the handle of the Petya developers.
Security firms have yet to validate whether the alleged RSA private keys are legitimate. But multiple security experts that I've contacted tell me they're aware of the dump and currently reviewing it.
Most ransomware works by forcibly encrypting - or "locking" - important files on a PC, deleting the original copy, then delivering a ransom note offering to exchange a decryption key for bitcoins. Well-prepared victims can wipe their system and restore from an offline backup. Others, however, are often left with the choice between paying the ransom - and funding attackers - or else kissing their data goodbye. But a new public-private effort - a portal called "No More Ransom" - aims to give victims a third option, by providing ransomware decryptors whenever possible. With luck, these keys can be used to decrypt any system that was infected with Chimera, and a related tool made available via the portal.
"Checking if the keys are authentic and writing a decryptor will take some time - but if you are a victim of Chimera, please don't delete your encrypted files, because there is a hope that soon you can get your data back," security researchers at Malwarebytes say in a blog post.
Developers Claims to Have Hacked Rival
The Petya Pastebin post also sheds light on how the alleged encryption keys were obtained. "Like the analysts already detected, Mischa uses parts of the Chimera source [code]," the post reads. "We are NOT connected to the people behind Chimera. Earlier this year we got access to big parts of their deveolpment (sic) system, and included parts of Chimera in our project."
On a related note, Chimera appears to now be defunct, according to the Bleeping Computer anti-ransomware forum.
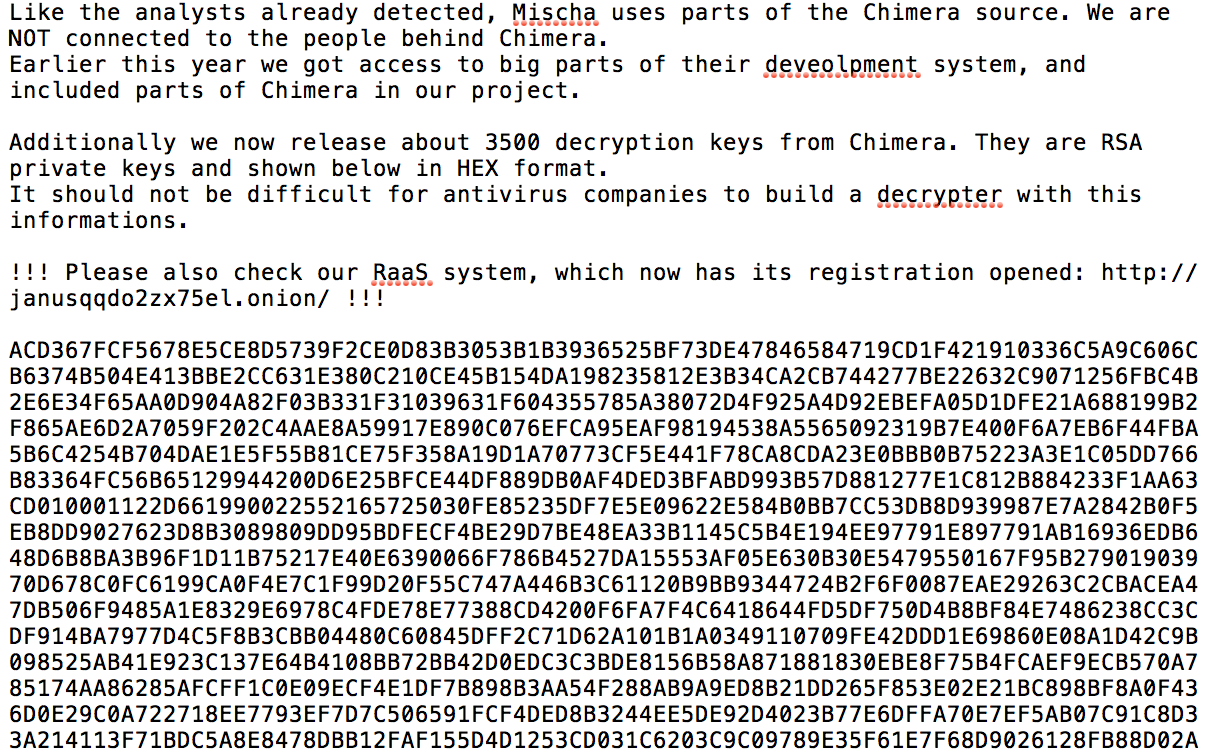 The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)
The Petya ransomware gang claims to have leaked 3,500 Chimera keys. (Source: Pastebin)
Petya's 'GoldenEye' Play
The Petya gang is using the new Chimera crypto key dump to advertise its RaaS - ransomware as a service - offering. Under such programs, developers typically take a cut of all profits generated by subscribers.
It's also notable that Petya claims to have leaked a rival's keys, since the group appeared to have fumbled its own crypto earlier this year. The gang was spreading Petya - a.k.a. Petr - ransomware, in part by spamming German-speaking HR managers with fake resumes for job candidates, according to Fedor Sinitsyn, a malware analyst at security firm Kaspersky Lab.
In April, however, security researchers were able to release a tool that could decrypt files that had been encrypted by Petya, due to a weakness in developers' encryption implementation. Of course, ransomware developers will typically fix their mistakes as quickly as possible to try to maximize their ransom haul.
As expected, the Petya gang quickly returned with an updated version of Petya, as well as another malicious payload, called Mischa. Both of those pieces of ransomware are named after satellites featured in the James Bond movie "GoldenEye."
In recent months, the gang has begun using a malware dropper that attempts to run an executable on a victim's PC, which on systems that have User Account Control enabled will generate a pop-up asking if a user wants to allow a program to make changes to their computer, Malwarebytes analyst "hasherezade" says in a blog post. If the user clicks "yes," then the dropper will have bypassed UAC, obtained administrator-level access rights, and can install the latest version of Petya, which infects the master boot record. If the dropper can't bypass UAC, it attempts to instead install Mischa.
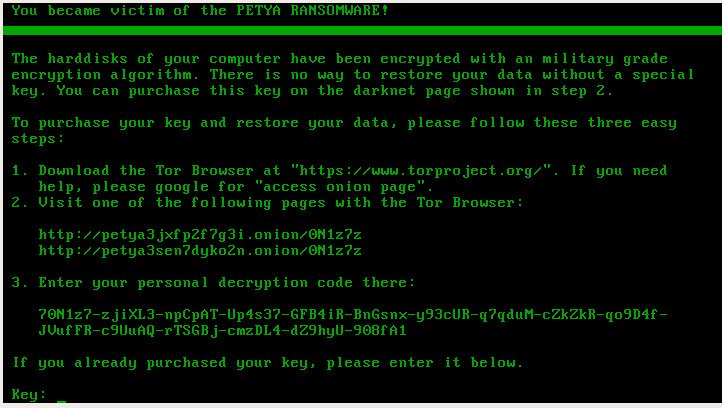 Pictured: Petya ransom demand. (Source: Malwarebytes)
Pictured: Petya ransom demand. (Source: Malwarebytes)
Ransomware Defense: UAC
One moral to the Petya ransomware infection story is that enterprises need to enable UAC to help block infections by any form of malware. "If the user launches the malicious executable file Petya, Windows will show the standard UAC request for privilege escalation," Sinitsyn of Kaspersky Lab says in a blog post. "If the system has been properly configured by the system administrators - i.e. UAC is enabled, and the user is not working from an administrator account - the Trojan won't be able to run any further."
Otherwise, users might give ransomware carte blanche access to crypto-lock their files or even lock down their entire operating system. "Unfortunately, a user who has the privileges to agree to a UAC request often underestimates the potential risks associated with launching unknown software with elevated rights," Sinitsyn says.
- Details
- Category: Security News
Breach Response , Data Breach , Forensics
Debate: Guccifer 2.0's Potential Link to Russia Mystery Seems No Closer to Being Solved
As the U.S. probes a Russian connection to the hack of the Democratic National Committee, more details have been released about Guccifer 2.0, the mysterious figure who released DNC documents via a WordPress blog.
See Also: How to Mitigate Credential Theft by Securing Active Directory
ThreatConnect, an Arlington, Va.-based security company, suggests that Guccifer 2.0 has a close connection with Russia, although it adds that he doesn't have the technical sophistication of the two Russian hacking groups believed to have compromised the DNC's network.
But the "Guccifer 2.0" persona is likely not a hacker at all, ThreatConnect says, suggesting that it's instead a Russian disinformation group tasked with stirring the pot.
That analysis adds to the mix of publicly available information relating to Guccifer, including his claim of being Romanian - although he apparently struggles to speak Romanian - as well as his claimed use of a zero-day vulnerability to access the DNC's network, according to Vice's Motherboard.
ThreatConnect's conclusion, which some observers find problematic, highlights an unsolvable problem in computer forensics - namely, that definitive attribution is often impossible due to technical tricks that attackers use to stay hidden.
Obama: 'Anything's Possible'
In a case involving two countries already at odds, of course, inaccurate attribution could also trigger a larger geopolitical crisis. The FBI, for example, has confirmed that it's investigating the DNC hack, but has so far not commented further.
In an NBC News interview on July 26, President Barack Obama was asked if he believed Russia was behind the hack and if the country is trying to interfere with the U.S. election. "Anything's possible," he said.
"What we do know is that the Russians hack our systems, not just government systems but private systems," Obama said, in what were his first public comments on the incident. "But what the motives were in terms of the leaks, all that, I can't say directly."
As he continued, Obama stoked a related conspiracy theory: "What I do know is that Donald Trump has repeatedly expressed admiration for Vladimir Putin."
Was Hacker an Amateur?
Guccifer 2.0 published some of the DNC files on a WordPress blog, shortly following the DNC saying, in mid-June, that its network had been compromised. CrowdStrike, the DNC's appointed incident response firm, attributed the attack to two long-known Russian groups - Cozy Bear and Fancy Bear - and its conclusion has been supported by FireEye's Mandiant unit and Fidelis Cybersecurity (see Report: Russia's 'Best' Hackers Access DNC's Trump Research).
Since state-sponsored actors rarely go public, Guccifer's document dump and thirst for attention was an odd piece of the hacking puzzle. But the dump has already had some dramatic political effects.
The internal emails, which Guccifer 2.0 claimed to pass to WikiLeaks, exposed bias against Democratic presidential candidate Bernie Sanders and prompted the resignation of Debbie Wasserman Schultz, the DNC's chairwoman. Hillary Clinton's campaign later alleged that the leaks might be a Russian scheme to boost Republican Donald Trump's chances of winning the presidency.
Accordingly, finding a strong connection between Guccifer 2.0, Cozy Bear and Fancy Bear could be an important part of figuring out the timing and motivation behind the leaks.
Technical Details
ThreatConnect's analysis is drawn from an email supplied by Kevin Collier from media firm Vocativ. Guccifer 2.0 wrote to Collier using a French AOL account, which gave ThreatConnect a loose thread to pull.
Email headers reveal information about the technical path a message took from sender to receiver. But analyzing headers can be misleading. Information is sometimes missing, and other data can be spoofed.
AOL's email headers, however, are different and show the originating IP address from which an email was sent. Guccifer's IP address is verified by DKIM, an email authentication feature, which means it wasn't spoofed, ThreatConnect writes. The IP address, 95.130.15[.]34, belongs to DigiCube, a French hosting provider.
"Very few hackers with Guccifer 2.0's self-acclaimed skills would use a free webmail service that would give away a useful indicator like the originating IP address," ThreatConnect writes.
Potential Smoking Gun: Russian VPN
Further investigation into the IP address showed it had been Secure Shell, or SSH, enabled, which indicated it was likely a VPN. SSH is a protocol for connecting to other computers using encryption.
ThreatConnect used Shodan, a search engine for Internet-connected devices, to find other servers that used the same public SSH encryption key fingerprint as the server Guccifer 2.0 employed. It found six other IP addresses shared the same fingerprint, which was eventually linked to a Russia-based VPN service called Elite VPN Service. ThreatConnect registered an account with Elite and discovered that the IP address used by Guccifer 2.0 is not actually offered to customers.
"This demonstrates the server was cloned from the same server image as all the Elite VPN servers but may be a private, dedicated version of the service," ThreatConnect writes.
Debate Continues
Via Twitter, ThreatConnect has received a fair amount of praise for its sleuthing. But not everyone finds the firm's technical details to be convincing. Of course, that's not unusual, as disagreements over attribution are common.
"Still a @threatconnect fan- but this (nice) article unfortunately pits weak evidence against equally weak evidence," writes Greg Barnes, a former chief information security officer for Blue Cross Blue Shield, on Twitter.
Scot A. Terban, a threat intelligence analyst, put it more bluntly: "My. God. The attribution here is akin to me farting and blaming the dog."
- Details
- Category: Security News

As a report surfaced July 29 that the campaign website of presidential nominee Hillary Clinton was hacked, the Democratic Congressional Campaign Committee confirmed that it was breached shortly after the Democratic National Committee announced that it, too, had been hacked.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
News service Reuters, citing people familiar with the matter, reported that Clinton's presidential campaign website was hacked as part of a broad cyberattack on Democratic Party institutions. The New York Times reported the Clinton campaign site hack appears to have originated from Russia's intelligence services. The Clinton campaign didn't immediately comment, according to a federal law enforcement official.
The U.S. Department of Justice national security division is investigating whether the attacks on Democratic political organizations threatened U.S. security, sources familiar with the matter said, Reuters reports. The involvement of the Justice Department's national security division is a sign that the Obama administration has concluded that the hacking was state sponsored, individuals with knowledge of the investigation told the news service.
Meanwhile, DCCC spokeswoman Meredith Kelly said in a statement issued July 29 confirming its breach: "Based on the information we have to date, we've been advised by investigators that this is similar to other recent incidents, including the DNC breach. We are cooperating with the federal law enforcement with respect to their ongoing investigation."
Broad Attack on Democrats?
The breach at the DCCC, which raises money for Democratic House candidates, may have been launched by Russian hackers who also attacked Democratic National Committee, according to several news reports, quoting unnamed sources. The Washington Post reports that the FBI is treating the DNC and DCC breaches as a single investigation.
At a White House briefing held after the revelation of the DCCC breach but before word of the Clinton campaign site hack, White House Deputy Press Secretary Eric Schultz said of the investigations of the DNC and DCCC attacks: "So if there are connected events that they would look at, that would be part of their investigation. Obviously, we expect that investigation to be thorough and deliberate and look at all the facts ... and to where they lead."
But Schultz would not say whether Russians were behind the attacks. "There's sort of a usual list of suspects when it comes to malicious cyber activity, so they're looking at those suspects," he said. "But at this point, they don't have any public confirmation to announce at this time."
Cybersecurity firm FireEye compiled a report on the DCCC hack that claims a Russia-based hacking group called APT 28 is the likely culprit, according to the website Morning Consult. Hackers targeted information on DCCC donors, FireEye claims.
Report: Hackers Redirected Traffic to Fake Website
The FireEye investigation revealed that the hackers created a website called Act Blues, which is similar to the DCCC's Act Blue domain, redirecting traffic to the fake one, CNBC reports. The hackers didn't steal money but might have collected information on donors for future illicit use. The hack lasted from at least June 19 to June 27, according to FireEye.
The FBI is trying to determine whether emails obtained in the DNC hack are the same ones that were leaked on the website of the anti-secrecy group WikiLeaks, the Washington Post reports. The DNC's leaked emails, which allegedly show bias by committee officials against unsuccessful presidential candidate Bernie Sanders, forced the resignation of DNC Chairwoman Debbie Wasserman Schultz (see Leaked DNC Emails Show Lax Cybersecurity).
A spokesman for Russia's embassy in Washington denied Russian involvement in the DNS and DCC hacks, according to several news media reports.
(Watch for updates on this developing story.)
- Details
- Category: Security News
Data Breach , Litigation , Privacy
Company CEO Michael Daugherty Plans to Appeal
The Federal Trade Commission has overturned a decision made last fall by its own administrative law judge to dismiss the agency's longstanding data security enforcement case against the now-shuttered medical testing laboratory LabMD. Company CEO Michael Daugherty plans to appeal in the federal courts.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
In the commissioners' unanimous opinion announced on July 28, FTC Chairwoman Edith Ramirez writes that the agency concludes that Administrative Law Judge Michael Chappell "applied the wrong legal standard for unfairness" in his ruling last November to dismiss the FTC's case against LabMD.
Chappell had ruled that the FTC's counsel had not shown that LabMD's data security practices either caused or were likely to cause substantial injury. In reversing Chappell's ruling, the commissioners concluded that LabMD's data security practices constitute an unfair act or practice that violated Section 5 of the Federal Trade Commission Act.
"We also find that LabMD's security practices were unreasonable, lacking even basic precautions to protect the sensitive consumer information maintained on its computer system," Ramirez writes in the decision. "Among other things, [LabMD] failed to use an intrusion detection system or file integrity monitoring; neglected to monitor traffic coming across its firewalls; provided essentially no data security training to its employees; and never deleted any of the consumer data it had collected," she wrote.
"These failures resulted in the installation of file-sharing software that exposed the medical and other sensitive personal information of 9,300 consumers on a peer-to-peer network accessible by millions of users. LabMD then left it there, freely available, for 11 months, leading to the unauthorized disclosure of the information."
In addition to the ruling, FTC also issued a final order requiring that LabMD notify affected consumers, establish a comprehensive information security program reasonably designed to protect the security and confidentiality of the personal consumer information in its possession, and obtain independent assessments regarding its implementation of the program.
In its ruling, the FTC notes: "Although LabMD stopped accepting specimen samples and conducting tests in January 2014, LabMD continues to exist as a corporation and has not ruled out a resumption of operations. Moreover, LabMD continues to maintain the personal information of approximately 750,000 consumers on its computer system. Because LabMD continues to hold consumers' personal information and may resume operations at some future time, the order is appropriate and necessary."
The FTC declined an Information Security Media Group request for comment.
Appeal Planned
Michael Daugherty, CEO of LabMD, says he'll fight the FTC's latest decision in the federal appellate courts. Daugherty, who has been battling the FTC since 2013 over the enforcement case stemming from two alleged data breaches, has written a book about his long battle with the agency.
"The FTC's own judge tossed all their evidence and now they waste taxpayer dollars to go to ... court relying on hearsay," Daugherty tells Information Security Media Group. "I am so relieved to be away from their dirty, biased system and into a ... court. Shame on every commissioner. They have, without remorse, made a mockery of legal ethics, regulatory boundaries and HHS [Department of Health and Human Services]. Yet in their magical thinking they carry forward, and I can't wait. Villainy wears many masks, none more dangerous than the mask of virtue."
Case History
The FTC ruling reverses Chappell's decision to dismiss the FTC Bureau of Consumer Protection's 2013 case against LabMD that alleged that the Atlanta-based company had failed to protect the security of consumers' personal data, putting them at risk for identity theft.
In dismissing the FTC's case against LabMD, Chappell had said the FTC "failed to prove its case" that two alleged data security incidents at LabMD in 2008 and 2012 caused, or were likely to cause, "substantial injury to consumers," such as identity theft, medical identity theft, reputational harm or privacy harm, and would, therefore, constitute unfair trade practices.
The FTC's complaint against LabMD alleged that the company "failed to reasonably protect the security of consumers' personal data, including medical information." The complaint alleged that in two separate incidents, LabMD collectively exposed the personal information of approximately 10,000 consumers. The FTC alleged that LabMD billing information for more than 9,000 consumers was found in 2008 on a peer-to-peer file-sharing network and then, in 2012, LabMD documents containing sensitive personal information on at least 500 consumers were found by police in Sacramento, Calif., in the possession of "identity thieves."
In its ruling, however, the FTC agreed with the administrative law judge's decision that the FTC's counsel did not establish that the Sacramento security incident was caused by deficiencies in LabMD's computer security practices.
Back in August 2013, the FTC proposed a consent order against LabMD requiring the company to implement a comprehensive information security program that an independent, certified security professional would evaluate every two years over the next 20 years. The order - which is now finalized as part of the ruling - also required that LabMD provide notice to consumers whose information LabMD has reason to believe was or could have been accessible to unauthorized persons and to consumers' health insurance companies.
In addition to battling with the FTC, Daugherty has also waged a legal battle against Philadelphia-based peer-to-peer security firm Tiversa, which allegedly discovered the supposedly unsecured LabMD spreadsheet on a peer-to-peer network in 2008 and reported the matter to the FTC.
During testimony at the case's FTC administrative hearing, some witnesses, including a former Tiversa employee, discredited Tiversa's account to the FTC of the alleged LabMD security incident.
The former Tiversa employee testified that it was a "common practice" of Tiversa to approach prospective clients with exaggerated information about their allegedly unsecured files that the security firm found "spreading" on the internet in an attempt to sell the company's security monitoring and remedial services.
Daugherty also alleged that Tiversa reported false information to the FTC about the supposed security incident involving LabMD's data after the lab refused to buy Tiversa's remedial services.
In 2014, the House Committee on Oversight and Government Reform conducted an investigation into the business practices of Tiversa (see LabMD Case: House Committee Gets Involved). A resulting staff report by the committee alleges that Tiversa "often acted unethically and sometimes unlawfully in its use of documents unintentionally exposed on peer-to-peer networks."
Ruling's Message
A regulatory expert says the FTC's decision to overturn its own administrative law judge's ruling to dismiss the LabMD case fits a pattern of other recent FTC data security enforcement actions against for-profit organizations.
"I am not at all surprised by the ruling," says privacy attorney Kirk Nahra of the law firm Wiley Rein. "The FTC overturned the surprising administrative law judge decision, which had seemed out of line with the previous FTC enforcement activity," he says. "This means that the FTC - until a court or Congress tells them otherwise - will continue to exercise its authority to take enforcement action against what it views - through its own standards developed over the years - as unreasonable security practices, even in the absence of a specific measureable consumer harm."
The LabMD case also "confirms that the FTC can decide to bring cases against healthcare entities, but there is nothing specific in this decision - or in any other FTC actions since the initial decision - to indicate that the FTC intends to go after the healthcare industry broadly," Nahra says.
"Also, it is important to understand that there are large segments of the healthcare industry - mainly health insurers and non-profits - where the FTC does not actually have jurisdiction at all," he notes. "So, the message for the healthcare industry is that the FTC is definitely out there, but the Department of Health and Human Services is still the big enforcement concern. This ruling mainly impacts 'everyone else,' where the FTC re-affirms its overall approach to information security enforcement."
Privacy attorney David Holtzman, vice president of compliance at security consulting firm CynergisTek, also urges other entities that deal with health data to take notice of the FTC's ruling in the LabMD case.
"This is a shot across the bow to companies that handle patient information that reasonable security practices mean putting real teeth into a data security program," he says. "The FTC will look for evidence that companies can demonstrate that they have in place a program of risk assessments to identify threats and vulnerabilities to the confidentiality and integrity of data, putting into place technologies that monitor and respond to network intrusions or unauthorized access, and taking steps to evaluate the effectiveness of security measures to ensure that sensitive consumer information is protected," he says.
- Details
- Category: Security News
More Articles …
Page 3472 of 3546

 Healthcare, more than any other industry, is increasingly in the crosshairs of attackers who seek to cause business disruption through evolving attacks such as ransomware. It's inevitable, frankly, that the vast majority of healthcare organizations will be diagnosed with ransomware. How must they prepare? What treatment is available for when they are struck?
FireEye's Dan McWhorter offers insight and strategies, including:
The size and scope of current attacks on healthcare entities;
Strategies and tools to help avoid being crippled by ransomware;
How organizations can harness threat intelligence in their defenses.
A surge in ransomware attacks on hospitals is driving healthcare organizations large and small to consider new and improved approaches to dealing with this evolving threat. In fact, one healthcare expert recently reported that one large East Coast health system turned away over 1 million ransomware emails in the month of March alone, more than any other industry. What can organizations do to avoid being the next victim - or the next big news headline?
Register for this session and get first-hand advice from Dan McWhorter, FireEye's Chief Intelligence Strategist. McWhorter is a member of the Department of Health and Human Services Health Care Industry Cybersecurity Task Force and has spent years analyzing cyberattacks on healthcare entities. In this informative webinar, McWhorter will provide you with case studies and first-hand advice on ways to leverage your threat intelligence - and prevent ransomware from victimizing your organization.
You might also be interested in …
Healthcare, more than any other industry, is increasingly in the crosshairs of attackers who seek to cause business disruption through evolving attacks such as ransomware. It's inevitable, frankly, that the vast majority of healthcare organizations will be diagnosed with ransomware. How must they prepare? What treatment is available for when they are struck?
FireEye's Dan McWhorter offers insight and strategies, including:
The size and scope of current attacks on healthcare entities;
Strategies and tools to help avoid being crippled by ransomware;
How organizations can harness threat intelligence in their defenses.
A surge in ransomware attacks on hospitals is driving healthcare organizations large and small to consider new and improved approaches to dealing with this evolving threat. In fact, one healthcare expert recently reported that one large East Coast health system turned away over 1 million ransomware emails in the month of March alone, more than any other industry. What can organizations do to avoid being the next victim - or the next big news headline?
Register for this session and get first-hand advice from Dan McWhorter, FireEye's Chief Intelligence Strategist. McWhorter is a member of the Department of Health and Human Services Health Care Industry Cybersecurity Task Force and has spent years analyzing cyberattacks on healthcare entities. In this informative webinar, McWhorter will provide you with case studies and first-hand advice on ways to leverage your threat intelligence - and prevent ransomware from victimizing your organization.
You might also be interested in …