- Details
- Category: Security News
The Global Cyber Alliance is taking on small projects to come up with solutions to big cyber risk problems.
"It's essentially using a startup approach to a much bigger problem," says the alliance's chief executive, Phil Reitinger, who'll deliver a keynote address at the New York Fraud and Breach Prevention Summit on Aug. 2. "You pick part of the problem and you design a solution and you see if it works. And, if it doesn't, you want to fail fast and then try something else. You don't want to get caught up in all of the administrative overhead and workaround, trying to have an omnibus strategy that will be out of date before it's ever implanted."
In an interview with Information Security Media Group (click on player beneath photo to listen), Reitinger:
Discusses one of the alliance's first projects: mitigating phishing scams that use spoofing emails; Outlines cyber risk projects the alliance will likely tackle in the coming months; and Characterizes the current IT security environment as "the Bronze Age" and explains how the IT security community should take steps to be more scientific in its approach to cyber risks.From Witch Doctors to Scientists
"We have a long way to go toward where we have cybersecurity practitioners who are scientists as opposed to artists or witch doctors," he says.
The Center for Internet Security, a not-for-profit organization that oversees the Multistate Information Sharing and Analysis Center; the Manhattan, N.Y., district attorney's office and London police teamed up to form the Global Cyber Alliance to identify measurable ways to mitigate cyberthreats (see New Global Alliance Seeks Measurable InfoSec Solutions). In an earlier interview, Reitinger makes one thing clear: The alliance is not a coalition of the willing; it's a coalition of the angry (see Global Cyber Alliance: A Coalition of the Angry).
Before being tapped as the alliance's president and CEO last year, Reitinger served as deputy undersecretary for cybersecurity at the Department of Homeland Security, CISO at the entertainment conglomerate Sony and chief trustworthy infrastructure strategist at Microsoft.
- Details
- Category: Security News
Some security experts expect the United States government to retaliate against Moscow for interfering in the American presidential election if the Obama administration determines the Russian government was behind the hack of Democratic Party computers. An examination of the impact of the breach that helped disrupt the opening day of the Democratic Party convention to nominate Hillary Clinton for president leads the latest edition of the ISMG Security Report.
In the report, you'll also hear:
DataBreachToday Executive Editor Mathew J. Schwartz discuss the new No More Ransom initiative that aims to help PC users avoid becoming ransomware victims as well as help victims decrypt their files, and ISMG Managing Editor for Security and Technology Jeremy Kirk explain how a 14-year-old Norwegian is taking on the makers of the embattled security program for Apple computers, MacKeeper.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our July 19 and July 22 reports, which respectively analyze the human factor in the age of cyber conflict and the Republican Party cybersecurity platform. The next ISMG Security Report will be posted Friday, July 29.
Theme music for the ISMG Security Report by Ithaca Audio under Creative Commons license.
- Details
- Category: Security News
Neither ransomware nor social engineering is new, but both are more advanced and effective than ever. How can organizations improve how they detect and respond to the latest threats? James Lyne of Sophos shares insight and advice.
Lyne, global head of security research at Sophos, is fascinated by how the threat landscape and threat actors have shifted this year.
"The major trend here is really around more creative ways to make money from your data," Lyne says, and ransomware is the prime example. "Ransomware and holding your data for ransom on your own system is a pretty clever use of cryptography."
The other significant trend is what Lyne sees as a more sophisticated form of social engineering. Fraudsters aren't necessarily launching attacks through malware triggered by bogus links or watering hole attacks. Rather, they are frequently embedding exploits in innocent-looking word documents like billing invoices.
"Many of [the fraudsters] are using Word macros or Excel macros, which of course have somewhat of a use in legitimate business," Lyne says. "And they're entirely depending on the user to click this little 'enable content' button. It's almost 'Yes, please, I'd like to deploy malware.'"
In a discussion about the shifting threat landscape, Lyne talks about:
Today's most successful cybercrime campaigns; How criminals have refined their approach to social engineering; How ransomware has matured and is evolving.Lyne is global head of security research at the security firm Sophos. A self-professed 'massive geek,' he has technical expertise spanning a variety of the security domains from forensics to offensive security. He has worked with many organizations on security strategy, handled a number of severe incidents and is a frequent industry advisor. He is a certified instructor at the SANS institute and often a headline presenter at industry conferences.
Lyne has given multiple TED talks, including at the main TED event. He's also appeared on a long list of national TV programs to educate the public including CNN, NBC, BBC News and Bill Maher. As a spokesperson for the industry, James is passionate about talent development, regularly participating in initiatives to identify and develop new talent for the industry.
- Details
- Category: Security News
Defining the security architecture for a smart city project is a most complex task, as security leaders need to acquire specialised skills to deal with the challenge, says David Dufour, head of security architecture at Webroot.
The CISO role is gaining prominence for their work in Internet of Things and smart city projects. But they often need to get involved from the outside, he says in an interview with Information Security Media Group at 2016 RSA Conference Asia Pacific & Japan in Singapore.
"Why I say they need to get involved from the outside is because CISOs do not have control over security budgets or resources that a smart city project demands," he says.
In a smart city project, the first goal is not security and technical capabilities, but how much a CISO is empowered to influence people and teams around him to define a systematic approach to defining the framework, Dufour says.
While technical capabilities are important, what it takes to define a successful secure framework revolves around how much a CISO is empowered to leverage his technical expertise.
"However, that doesn't undermine the role of security in the entire project, given that the cybersecurity challenges in the smart city environment are rising alarmingly," Dufour observes.
He argues that smart cities demand CISO intervention in identifying, containing and preventing threats and securing every endpoint in the network.
"Defining a realistic security architecture expects CISOs to move the security focus off the endpoint into the network, use device ID to develop solutions that create dynamic sensors in the network and focus on resource capable endpoints," he says.
It is all about collaboration, Dufour says, adding, "CISOs need to work closely with vendors, universities and other functions from their organizations to develop ecosystem machine models for protecting the unique aspects of each network."
In this interview (see audio player below photo), he offers insights on:
Applying threat intelligence in identifying device threats; Breaking the kill chain in securing all endpoints with layered security; A collaborative approach to effective security defences.At Webroot, Dufour is involved in designing automated threat detection and remediation solutions with top-tier software and hardware manufacturers. His nearly 30 years of experience in software engineering has led to the creation of several predictive threat algorithms and the development of new techniques for mapping threat landscapes to identifying bad actors.
- Details
- Category: Security News
Fraud , Governance , Incident Response
CEO Fraud: Lessons From an Attack Why Employees Are the Best Lines of Defense
CEO fraud email campaigns are becoming far more common. And because these scams hinge on well-crafted social engineering, employee education is the best way to mitigate risk and avoid fraud losses.
See Also: Unlocking Software Innovation with Secure Data as a Service
The scams, also known as business email compromise attacks, are designed to fool accounting staff into scheduling and approving fraudulent wire transfers.
In recent weeks, my employer, Information Security Media Group, was targeted by one of these scams, but we dodged any fraud losses thanks to the alertness of my ISMG colleague who received the request.
Most of the bankers I've spoken to about these schemes, which continue to plague their small business customers, say they're increasingly dedicating time and resources to customer education - either by going out to visit clients, hosting educational events at their branches or posting information to their websites about the common types of CEO fraud they see.
CEO Fraud Losses Exploding
The FBI warned in August 2015 that losses linked to business email compromise attacks worldwide totaled more than $1.2 billion from October 2013 through August 2015.
But David Pollino, deputy chief security officer at Bank of the West, says losses in 2015 alone likely exceeded $1 billion.
According to the 2016 Association for Financial Professionals' Payments Fraud and Control Survey, 64 percent of organizations in 2015 were exposed to business email compromise scams, a leading cause of wire fraud today. As a result, 48 percent of organizations were exposed to wire fraud, up from 27 percent in 2014, the AFP notes.
"Each year, payments and cyber fraud schemes grow in sophistication, and knowing how to recognize and manage these threats is critical to protecting your organization," notes Nancy McDonnell, managing director and treasury executive for JPMorgan Chase, the underwriter for the AFP's annual survey. "Investing in the appropriate data-protection tools, infrastructure controls and employee education is essential for all businesses."
Simple Attacks Have Big Payout Potential
CEO fraud attacks are relatively unsophisticated, but nevertheless, often successful. They're typically waged with a spoofed email address that mimics that of a CEO, with the email demanding that an accounting staff member schedule an urgent wire transfer. The more sophisticated versions of these scams are well-researched and well-written, using company details that make the message appear legitimate.
Because of the success these types of attacks have seen in recent years, I'm not surprised ISMG was targeted.
The spoofed request we received, which went to an employee on our marketing team, immediately raised red flags. The URL for the reply-to email address feigning to be from our CEO was nothing close to the URL we use for email. What's more, the first name of our CEO was misspelled in the reply-to line as well as the body of the message.
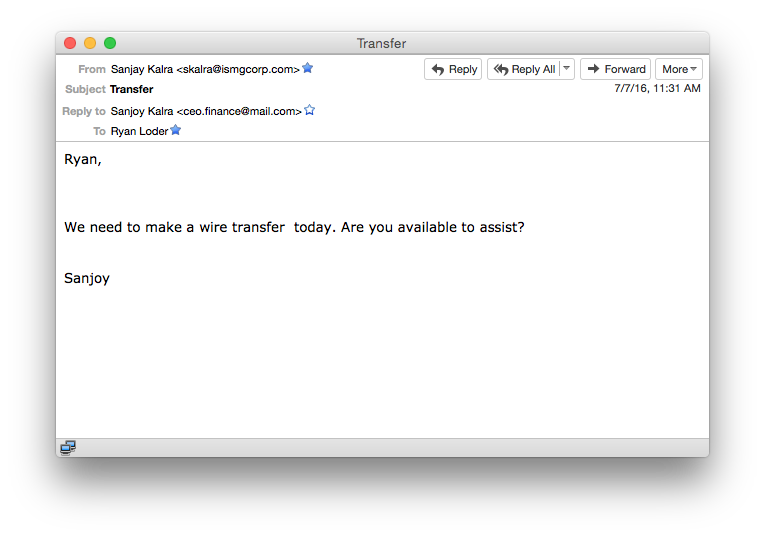 The first email ISMG received requesting a fraudulent wire. Note the URL for the reply-to line and the misspelling of our CEO's first name, which is spelled correctly in the from line. Also note the misspelling of his name in the body of the email message.
The first email ISMG received requesting a fraudulent wire. Note the URL for the reply-to line and the misspelling of our CEO's first name, which is spelled correctly in the from line. Also note the misspelling of his name in the body of the email message.The fraudster sent multiple requests asking our employee to transfer nearly $18,000 to an account at a top-tier bank in Texas. When we didn't comply, the requests eventually stopped.
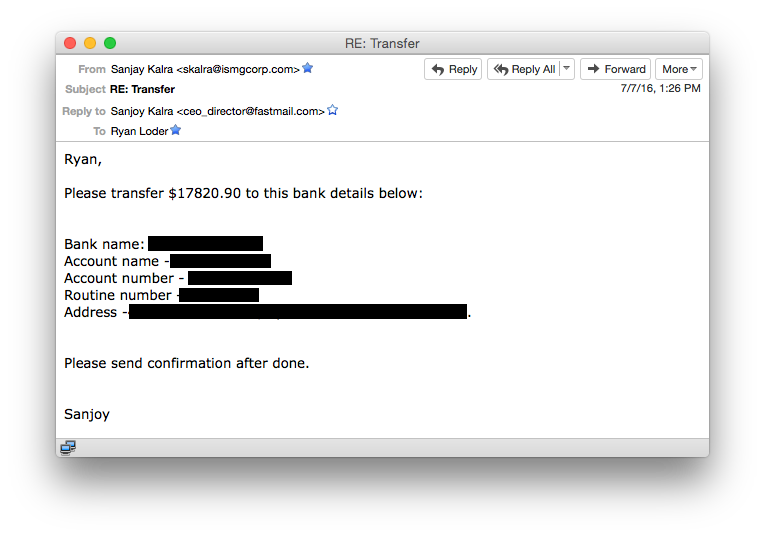 After a couple of email exchanges, the fraudster goes in for the kill, naming the amount and account to which the urgent wire should be sent.
After a couple of email exchanges, the fraudster goes in for the kill, naming the amount and account to which the urgent wire should be sent.Why Employees Are Fooled
Of course, some CEO fraud campaigns are far more sophisticated than the one that hit us at ISMG. So it can be relatively easy to trick someone not suspicious of the signs of danger to simply push payments through as a result of what appears to be urgent, persistent requests from the CEO.
Even in the campaign that hit one of our marketing employees, you can see the urgency the fraudster keeps stressing. In one of the requests, the fraudster notes that the wire must be scheduled immediately.
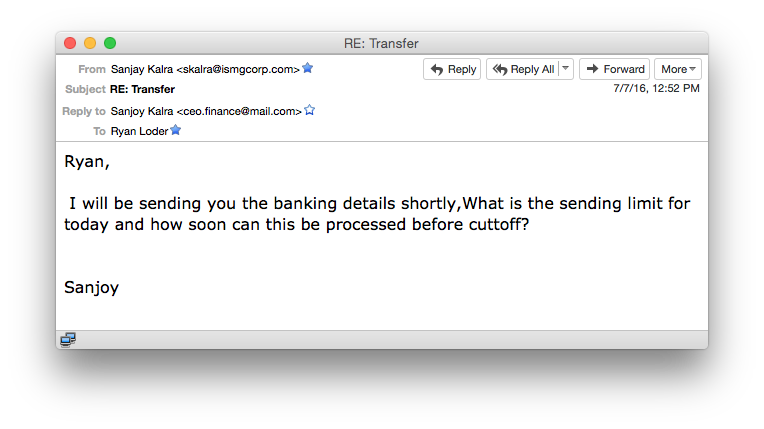 Urgency is typically part of all socially engineered schemes, and the CEO fraud attack that targeted ISMG was no different.
Urgency is typically part of all socially engineered schemes, and the CEO fraud attack that targeted ISMG was no different.It's easy to see how these scams often trick otherwise diligent employees into bypassing basic security measures designed to authenticate wire transfers, especially those going to unknown accounts.
Mitigating the Risks
Email authentication can help mitigate the risks, but nothing beats good old-fashioned employee education.
What should businesses do first if they fall victim to a CEO fraud scam? Fraud-fighting experts advise them to contact the fraud department at their banking institution, explain what happened and ask the bank to contact the fraud department at the recipient bank. After that, contact law enforcement.
After ISMG was targeted by a scam, we were advised by a U.S. attorney's office to file a complaint with the FBI's Internet Crime Complaint Center.
We did quite a bit of outreach to see if we could help law enforcement catch the fraudster. But so far, we haven't made much headway.
We're thankful that we didn't fall for the scam and glad we could share some of our experience with you.
And next week, at our New York Fraud and Breach Prevention Summit, we'll offer an important opportunity for banking institutions to learn more about what they should be doing to keep their business customers informed about emerging CEO fraud schemes - as well as the steps they should take when a scam is identified.
John Wilson, chief technology officer at online security firm Agari, will review some of the latest trends in email fraud schemes and describe what businesses can do to reduce their risks and what banks should be doing to educate their customers. I hope you'll join us.
More Articles …
Page 3471 of 3546
