- Details
- Category: Security News
Data Breach , Fraud , Payments Fraud
Robert Schwentker Reviews Challenges Bitcoin Exchanges Face in Wake of HacksIn the wake of the recent hack of the Bitfinex bitcoin exchange in Hong Kong, the Ethereum hack earlier this year and the Mt. Gox hack in 2014, the stability and security of cryptocurrency is being questioned. Cryptocurrency expert Robert Schwentker says these attacks could raise questions about whether regulatory oversight of bitcoin exchanges is needed.
See Also: How to Mitigate Credential Theft by Securing Active Directory
"The hack of the Bitfinex exchange in Hong Kong, which resulted in approximately 120,000 bitcoins being stolen ... was not, again, a hack of bitcoin protocol itself," Schwentker says in this video interview with Information Security Media Group. "It's similar to the Mt. Gox hack, where an exchange got hacked. Certain security protocols apparently might not have been followed, and the practices that they set up were not followed. Therefore, there's been this loss of people's funds. Whether the exchange will make those people who had put their bitcoins on their exchange whole again or not, we'll have to see."
In this interview at ISMG's recent New York Fraud and Breach Prevention Summit, Schwentker also discusses:
How steps to reduce risks in the wake of a bitcoin exchange breach have created new problems; Why the so-called "hard-fork" of the Ethereum exchange could result in litigation; and Other security challenges bitcoin exchanges could face.Schwentker is co-founder and president of Blockchain University, a project developed to provide education about blockchain technologies to developers, builders and startups in Silicon Valley. Previously, Schwentker held software development positions with PayPal, American Express, Mechanics Bank and others.
- Details
- Category: Security News
The next president of the United States should establish a cabinet position focused on cybersecurity, and Congress should create a more focused approach to funding and authorizing IT security initiatives.
Those are the recommendations of the Internet Security Alliance, says Larry Clinton, the group's president and CEO, in an interview with Information Security Media Group.
The alliance calls for reducing the scores of Congressional committees with cybersecurity jurisdiction. Instead, it advocates creating committees that would only focus on authorizing and funding IT security initiatives. But he acknowledges getting members of Congress to give up cybersecurity turf won't be easy.
"The problem is that cyber is so hot everybody wants to be the cyber guy now," Clinton says. "They'll be a lot of infighting on Capitol Hill because, frankly, the biggest value on Capitol Hill is not money or politics, and sure isn't policy - it's turf. We have to cut through the turf wars and streamline the process."
In the interview (see audio player below photo), Clinton:
Explains how the next president could lead efforts to get Congress to enact legislation paving the way for a cabinet-level department focused on cybersecurity as well as reducing the number of committees with cybersecurity oversight; Advocates a significant increase in cybersecurity spending by the federal government to quickly tackle evolving cyber threats; and Discusses why Hillary Clinton and Donald Trump would likely take similar approaches to cybersecurity if elected president.Since 2003, Clinton has headed the Internet Security Alliance, an industry group that promotes a non-regulatory approach to cybersecurity. He has published a number of articles on cybersecurity and frequently testifies before House and Senate committees on information security challenges.
- Details
- Category: Security News
Business Continuity/Disaster Recovery , Governance , Risk Assessments
System Outage Grounds Delta Flights Worldwide A Tale of Failed Resiliency
Delta grounded all departing flight on August 8 after experiencing a power failure near its Atlanta headquarters that triggered a major system outage, leaving airport departure areas and customers' travel plans in chaos. But as airlines increasingly computerize processes, experts ask why this airline wasn't better prepared to deal with a related outage.
See Also: The Inconvenient Truth About API Security
"A power outage in Atlanta, which began at approximately 2:30 a.m. ET, has impacted Delta computer systems and operations worldwide, resulting in flight delays," Delta says in a statement. "Large-scale cancellations are expected today. All flights en route are operating normally."
Atlanta-based Delta, which is the second-largest U.S. airline based on miles flown, operates 5,000 flights per day. The airline has warned that the outages and disruptions could extend to August 12, and said all affected customers would receive refunds or be allowed to alter their tickets for free, for a limited time.
"That's some outage," says Alan Woodward, a computer science professor at the University of Surrey and a cybersecurity adviser to Europol - the EU's law enforcement intelligence agency.
"I think airlines have had the same exposure to system failure for some time now. What I think we're seeing is a failure to learn from history and allowing single points of failure in the system," Woodward tells me. "Whilst safety critical systems have failure modes analyzed, operational systems clearly are not undergoing the same degree of analysis. The result is not fatal, but nevertheless its impact can be enormous."
In this era of cloud-based computing, such outages should be almost entirely preventable. To do that, however, organizations must pay attention to the basics, including building in redundancy as well as employing uninterrupted power supplies. "For a power failure to cause this level of disruption in the 21st century is very surprising," Woodward says.
@ruskin147 after a 3rd major power outage in as many weeks causes chaos, why have forgotten the basics: UPS & no single point of failure.
Damage-Control Mode
Delta has been left apologizing for the outage and attempting to alert customers. "Customers should check the status of their flight before heading to the airport while the issue is being addressed," an August 8 tweet from Delta warns customers.
Somewhat maddeningly, however, Delta is also warning that flight-status systems - when they can be reached - have been relaying incorrect information. "We are aware that flight status systems, including airport screens, are incorrectly showing flights on time," it said. "We apologize to customers who are affected by this issue, and our teams are working to resolve the problem as quickly as possible."
By 8:40 a.m. ET on August 8, Delta said that some flights had been allowed to depart. Early indications suggest that Delta was able to get flights airborne after reverting to manual processes.
"Delta flights from Heathrow are experiencing delays due to the worldwide technical issue with their computer systems," a Heathrow airport spokesman tells me. "Check-in is currently operating using a backup system and airport staff are on hand to assist any passengers that are impacted by the delays. Passengers should check with the airline for updates on their flights."
1 hr.+ lines @HeathrowAirport for @Delta due to system outage #Heathrow #oldschool manual ticketing @DeltaAssist pic.twitter.com/syC0VwCBDD
Even so, Delta noted that "cancellations and delays continue," and that its website and Fly Delta mobile app, as well as the information being provided to its phone-based customer service employees, might still be inaccurate.
Follows Southwest Airlines Outage
Delta's outage follows Southwest Airlines on July 20 issuing a full "ground stop" after a one-hour "system outage" that occurred after a router failed and a backup failed to kick in, The Dallas Morning News reported. Ultimately, the outage led to five days of disruptions, with the airline canceling 2,300 flights, or about 11 percent, of all flights that it operated in that timeframe.
Industry analysts say that airlines are increasingly digitizing processes - such as allowing boarding passes to be downloaded to mobile devices - as well as adding new technological capabilities to airplanes, such as in-flight Wi-Fi, as the Guardian reports. But without proper planning - and resiliency - computerizing more systems and processes leaves them vulnerable, both to inadvertent outages as well as anyone with malicious intent (see Hack Attack Grounds Airplanes).
Outstanding Investment, Design Questions
Seeing power failures lead to widespread system outages is not unique to the aviation sector. The same day as the Southwest outage, notably, a power loss at Telecity Harbor Exchange, which houses equipment for the London Internet Exchange and which is based in London's Docklands, also led to widespread outages, disrupting about 20 percent of all traffic that was being routed via LINX. Many customers of major U.K. internet service provider BT were reportedly also affected.
But such situations can be prevented, not least by ISPs and airlines. "With sufficient investment and suitable design this need not happen," Woodward says. "That it does occur suggests that one, the other or both are missing."
- Details
- Category: Security News
Cybersecurity , Data Breach , Risk Assessments
David DeVries Seen as a 'Go-to Person for Getting Things Done' David DeVries
David DeVriesThe U.S. Office of Personnel Management - besmirched by a 2015 breach that exposed the personal information of 21.5 million individuals - turns to the military for its new chief information officer.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
OPM announced Tuesday that the principal deputy CIO of the defense department, David DeVries, will be its CIO. The post has been vacant since Donna Seymour announced her retirement in February, following extensive criticism of her role in handling the breach (see Beleaguered OPM CIO Departs).
In recent months, DeVries has worked with OPM as it stands up the National Background Investigations Bureau, which will provide background checks on individuals seeking security clearances. Although housed at OPM, the bureau's design, development, security and operation of the background investigation IT system fall under the Department of Defense.
"David has decades worth of the technical and management experience necessary to hit the ground running as we continue our technology transformation efforts, and work with our partners at DoD," OPM Acting Director Beth Cobert says in announcing DeVries appointment.
U.S. Cyber Challenge National Director Karen Evans, a former federal CIO who has worked with DeVries, says DeVries understands the importance of people and how OPM is focused on the federal workforce. "His experience at DoD and the connections he has and what OPM is doing in partnership with DoD as relates to security clearances will be key to success of the clearance process in the future."
Replacing CIO Who Left Under Fire
Silent on the naming of DeVries to the top business-technology job at OPM is Rep. Jason Chaffetz, the Utah Republican who as chairman of the House Oversight and Government Reform Committee ran a series of hearings on the OPM breach. Through a spokeswoman, Chaffetz declined to comment on DeVries appointment.
Chaffetz was highly critical of Seymour and her boss, then OPM Director Katherine Archuleta, saying at a July 2015 hearing that they demonstrated "negligence" and "put the personal and sensitive information of 21.5 million Americans into the hands of our adversaries. Such incompetence is inexcusable." (see Members of Congress Intensify Criticism of Agency.)
 Donna Seymour
Donna SeymourWhen Seymour left OPM in February, Chaffetz characterized her departure as "good news and an important turning point for OPM. ... On her watch, whether through negligence or incompetence, millions of Americans lost their privacy and personal data. The national security implications of this entirely foreseeable breach are far-reaching and long-lasting. OPM now needs a qualified CIO at the helm to right the ship and restore confidence in the agency."
Although Chaffetz wouldn't comment on DeVries appointment as OPM CIO, others who have worked with him have showered him with praise.
"While outwardly focused on enterprise management, David has strong operational and strategic expertise in information security and information assurance," says Henry Sienkiewicz, who worked with DeVries when he served as the CIO at the Defense Information Systems Agency. "He knows what needs to happen and how to make it happen. I feel much more confident in the future of OPM, in regards to information security, customer service and technology vision with David at its CIO"
'Broadly Skilled'
IT consultant Roger Baker, who as former Department of Veterans Affairs assistant secretary and CIO worked with DeVries on a DoD-VA initiative to improve electronic health record exchanges between the two agencies, characterizes the new OPM CIO as "a go-to person for getting things done in DoD."
"Information security is a critical part of what OPM faces, but they face many other challenges as well," Baker says. "This is why Dave is such a good choice. His DoD background has had a lot of infosec involvement, but he is broadly skilled to address the range of issues OPM faces, including delivering on new systems and capabilities."
DeVries, Baker says, is "very solid and disciplined" and will expect employees and contractors to effectively implement the security plans laid out and hold people accountable.
Champions Cloud Adoption
As DoD's principal deputy CIO, DeVries assisted Defense CIO Terry Halvorsen as the principal adviser to the defense secretary on information management and information assurance matters. He has served as principal deputy CIO since May 2014, first on an acting basis, then permanently beginning in March 2015. DeVries joined the DoD CIO staff in May 2009 as deputy CIO for information enterprise. DeVries has played a key role in moving DoD toward adopting the Joint Information Enterprise that's based on a single and secure DoD-wide IT architecture. At DoD, DeVries championed expanding cloud computing adoption and improving mobile communications capabilities.
A West Point graduate, DeVries earned a master of science in electrical engineering degree from the University of Washington in Seattle. He also graduated from the Army Senior Service College and served as a corporate fellow with IBM business consulting services as part of the Secretary of Defense Corporate Fellowship Program.
- Details
- Category: Security News
Anti-Malware , Encryption , Endpoint Security
Active Cyber-Espionage Campaign Dates From 2011, Security Firms Warn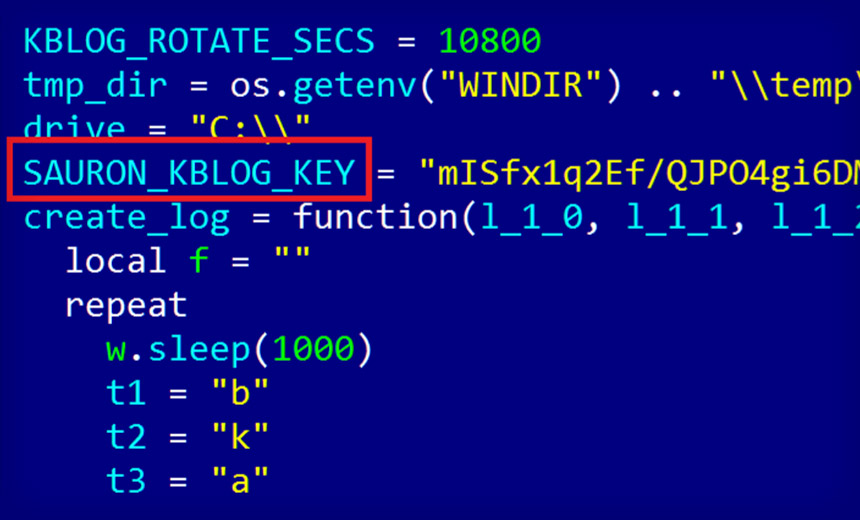 The group's malware references "Sauron" in its configuration files
The group's malware references "Sauron" in its configuration filesSecurity researchers are warning that they've discovered a highly advanced and targeted cyber-espionage campaign that appears to have been running since 2011, and which remains active. The APT malware used by the group behind the campaign is remarkable in part not only for having remained undetected for so long, but also for its ability to exfiltrate data from air-gapped networks using multiple techniques, including by piggybacking on network protocols, researchers say.
See Also: How to Mitigate Credential Theft by Securing Active Directory
Based on a reference to "Sauron" in the malware configuration files, the APT campaign has been dubbed "ProjectSauron" by Kaspersky Lab - referring to an all-seeing villain "The Lord of the Rings" - as well as "Strider" by Symantec, referring to a character who fights against Sauron.
Kaspersky Lab, in an Aug. 8 blog post, says it first discovered related attacks in September 2015, after finding "anomalous network traffic in a government organization network," which it ultimately traced to malware that it describes as being "a top-of-the-top modular cyber-espionage platform."
The government target has not been named, although the security firm says that it's found more than 30 infected organizations in Russia, Iran and Rwanda, although believes that's "just a tiny tip of the iceberg." It adds that the ProjectSauron malware works on all modern versions of Windows, and that related infections have infected systems running Windows XP x86 as well as Windows 2012 R2 Server Edition x64, and likely everything in between.
In some cases, the malware appears to have been used to target and exfiltrate data related to "communication encryption software" used by government organizations and agencies, Kaspersky Lab says. "It steals encryption keys, configuration files, and IP addresses of the key infrastructure servers related to the software," it says, adding that the malware includes the ability to install backdoors on infected systems, record keystrokes and steal documents.
Symantec, in an Aug. 7 blog post based on data collected by its anti-virus products, says it's found 36 related infections in seven organizations, across four countries, involving "a number of organizations and individuals located in Russia, an airline in China, an organization in Sweden and an embassy in Belgium." It refers to the related malware as Remsec.
This isn't the first time that two separate security firms have issued nearly simultaneous research reports into long-running malware campaigns. But security researchers say that they often work together, and across organizational boundaries, to identify and study advanced malware campaigns (see AV Firms Defend Regin Alert Timing).
Nation State Suspected
To date, researchers don't know how this malware first infects systems, nor do they know who is responsible. But all signs point to a "very advanced actor," Kaspersky Lab says. The security firm's chief researcher, Costin Raiu, notes that the malware - written in English, although with some Italian words - rivals the sophistication of such advanced malware as Duqu, Flame, Equation and Regin. "Whether related or unrelated to these advanced actors, the ProjectSauron attackers have definitely learned from these others," the company's report says.
ProjectSauron network sniffer captures files matching these patterns. Interesting Italian keywords: pic.twitter.com/HhDFiMUn9w
The malware is designed to be stealthy, for example remaining hidden until specified network protocols awaken it. "Much of the malware's functionality is deployed over the network, meaning it resides only in a computer's memory and is never stored on disk," Symantec says. "This also makes the malware more difficult to detect."
According to a technical teardown published by Kaspersky Lab, the malware can draw on 50 different modules, all of which appear to have been customized for individual targets.
After infecting a system, the malware pretends to be a Windows Local System Authority password filter on domain controllers, which is typically used by IT administrators to enforce password policies and validate that new passwords meet specified requirements, for example, involving length or complexity. "This way, the ProjectSauron passive backdoor module starts every time any domain, local user, or administrator logs in or changes a password, and promptly harvests the passwords in plaintext," Kaspersky Lab says.
The security firm says the malware has been distributed in some organizations via legitimate scripts that system administrators use to distribute software to end users, and that the malware has been disguised with names that resemble executable filenames used by Hewlett-Packard, Kaspersky Lab, Microsoft, Symantec and VMware.
Malware Penetrates Air-Gapped Networks
One standout feature of the malware is its ability to penetrate air-gapped networks, using one of those 50 modules. Kaspersky Lab says this attack technique begins by infecting a networked system, which waits for a USB drive to be attached. When that happens, it reformats the drive to add a hidden, encrypted partition that's several hundred megabytes in size, inside which it installs its own virtual file system, which won't be recognized by a "common operating system" such as Windows.
This infected USB key is used to exfiltrate data from air-gapped systems, with the data getting grabbed back off of the device once it gets plugged into an infected, network-connected system, the researchers say.
But it's not yet clear how attackers are gaining control of the air-gapped systems themselves, which would be required before they could exfiltrate data. "There has to be another component such as a zero-day exploit placed on the main partition of the USB drive," Kaspersky Lab says. "Unfortunately we haven't found any zero-day exploit embedded in the body of any of the malware we analyzed, and we believe it was probably deployed in rare, hard-to-catch instances."
Five Years and Counting
One reason the malware has been so difficult to spot, thus far, has been attackers' customizing their malicious code so that it's unique to each victim. "The attackers clearly understand that we as researchers are always looking for patterns," Kaspersky Lab says. "Remove the patterns and the operation will be harder to discover."
More Articles …
Page 3478 of 3546

