- Details
- Category: Security News
The head of the nearly year-old ISAO Standards Organization, Greg White, describes how fledgling Information Sharing and Analysis Organizations can help create an information sharing ecosystem aimed at making IT more secure at enterprises of all sizes.
President Obama, in an early 2015 executive order, proposed the creation of ISAOs by encouraging the formation of communities to share cyber threat information across a region or in response to a specific cyber threat. An ISAO could be a not-for-profit community, a membership organization or a single company facilitating sharing among its customers or partners (see Private Sector to Develop ISAO Standards).
ISAOs (pronounced eye-sows - as in cows) should focus on sharing information beyond a specific incident response, says White says in an interview with Information Security Media Group.
Sharing Solutions
"That's limiting; that really limits the type of information sharing that can go on," says Greg White, executive director of the ISAO Standards Organization, which is developing guidance for fledgling ISAOs. "There's a lot of information sharing that can occur before incidents that will help individuals with their security posture. Different entities, those who may have more robust security programs could help those who have less robust security programs by telling them, 'Okay, here's what we've done; here's what we've seen; here's how we handled this; here's how we've conduct these kind of operations.' There's a lot of learning that can go on."
In the interview (click on player beneath image to listen), White:
Explains the difference between ISAOs and ISACs, Information Sharing and Analysis Centers, serving most critical infrastructure sectors; Discusses how the smaller ISAOs can help build trust among members, a key element in sharing cyberthreat information; and Reviews some of the early activities of the ISAO Standards Organization.Mariachi and ISAOs
White, in the interview, also employs the hypothetical Mariachi band sector to demonstrate how ISAOs work.
A computer science professor focused on information security at the University of Texas at San Antonio, White also serves as the executive director of the Center for Infrastructure Assurance and Security at the university.
White, who holds a Ph.D. in computer science from Texas A&M University, has spent 30 years in the Air Force and Air Force Reserves, and helped build the nation's first undergraduate information warfare laboratory at the U.S. Air Force Academy.
- Details
- Category: Security News
Anti-Malware , Forensics , Technology
FireEye Says Ransomware Up, Earnings Down But Blaming Revenue Shortfall on Fewer APT Attacks Doesn't Add Up
Reporting lower than expected quarterly earnings, cybersecurity heavyweight FireEye (FEYE) has blamed a well-known villain: ransomware gangs. But many of the firm's assertions don't appear to hold up.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Last week, FireEye reported $175 million in second quarter 2016 revenue, which fell short of its previous projection of $178 million to $185 million.
FireEye CEO Kevin Mandia blamed the shortfall on attackers increasingly favoring extortion-style attacks, rather than more traditional advanced persistent threats, such as those practiced by cyber espionage groups.
"The biggest difference with the incidents we are responding to, and I think FireEye had a big influence in this factor, is the scale and scope went from hundreds of compromised machines by attackers who wanted to maintain and keep access, to more of the ransomware-type attacks and extortion attacks that are simply easier to remediate at times," Mandia said on an Aug. 4 earnings call.
"As the current threat environment shifts to smaller scoped breaches, some organizations may be opting for 'good enough' over 'best of breed' detection," he also said.
In June, FireEye released a report saying that it had seen a dramatic decline in Chinese cyber espionage attacks targeting U.S. firms (see U.S., China Advance Infosec Cooperation).
Mandia also became FireEye's CEO in June, taking over from David DeWalt, who moved to the role of executive chairman. Mandia came to FireEye via its nearly $1 billion acquisition of cybersecurity firm Mandiant in 2014, after which he was reportedly groomed to take the helm of FireEye, first serving as its COO and then president.
How Ransomware Gangs Really Operate
But Mandia's recent assertions overlook several key points. First of all, ransomware is often an attacker's coup de grace. The Gameover Zeus gang, for example, typically deployed keystroke-stealing malware designed to help them drain organizations' and individuals' bank accounts, then deployed Cryptolocker ransomware to lock PCs and further monetize their attacks.
Even with the Gameover Zeus gang behind bars, many attackers still emulate that model, especially in attacks against healthcare organizations, Ondrej Krehel, CEO of New York-based digital forensic investigation firm LIFARS, tells me. "What we've seen in the healthcare [sector] is, the ransomware is the last component ... it really happens after the data has been exfiltrated and taken to the black market," he says. "For the bad guys, it's just a beautiful way to get another dinner ticket."
On the cyber espionage front, meanwhile, if Chinese operators were less frequently attacking U.S. organizations - as FireEye claims - that would be great news. But not all security experts are convinced that's even the case. "It's hard to prove, but I haven't seen evidence that the Chinese are targeting us less frequently," Lawrence Orans, a research vice president at Gartner who covers network security, tells me.
Sandbox Competition Heats Up
Rather than the rise of ransomware and a decline in APT - and cyber espionage - attacks hitting FireEye's bottom line, the more likely explanation is increased competition for sandboxing technologies, which use virtual environments to analyze files and identify malware. "The flagship solution for FireEye is their sandbox or sandboxes, and there's more competition for those flagship products," Orans says.
Many other firewall and secure web gateway vendors - including Palo Alto Networks, Check Point, Bluecoat, Websense and Zscaler, amongst others - now offer such technology, Orans says.
FireEye's lower-than-expected profits "did not catch me totally by surprise - they grew very quickly," Orans says. That included acquiring threat-intelligence firm iSight Partners in January (see Why FireEye Snapped Up iSight Partners).
Furthermore, the company's second quarter 2016 earnings still represent an increase of 19 percent from the second quarter of 2015. "The company is still growing, it's just that the market dynamics have changed, and now they face more competition," Orans says. "And it's being reflected in the stock price."
FireEye Announces Layoffs
FireEye's stock price has declined about 14 percent in value since Aug. 4, when it released its second-quarter 2016 financial results - with revenue and billings that were lower than it had predicted - and announced layoffs. "Unfortunately we do expect this to probably affect 300 employees to 400 employees," Michael J. Berry, FireEye's CFO and COO, said on the earnings call. "It's a reduction of about 9 percent of our, call it, controllable costs. We will try to go after as much as we can non-head count, but ... we do expect it to probably be about that level."
Mandia says the need to restructure is a consequence of the company's growth. "We always knew somewhere around 2016, we'd have to change this company as we got scale," he tells financial site Marketwatch. "I want to balance growth with profitability, and we're serious about that path to profitability."
- Details
- Category: Security News
Data Breach , Fraud , Payments Fraud
MICROS, Hotel Breaches Illustrate Why Vendors Remain 'Weakest Links'
Just days after POS systems and services provider Oracle MICROS revealed a breach impacting its legacy POS systems, Visa issued an alert warning merchants to be on the lookout for malware attacks linked to MICROS.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
Visa's alert, which was provided to Information Security Media Group by a third-party source under the condition that it not be posted, notes that merchants should be scanning their networks for indicators of compromise related to two specific malware strains - Carbanak and MalumPOS. The alert also suggests a correlation between the group behind Carbanak and the breach at MICROS.
But Alex Holden, CISO at security and forensics firm Hold Security, says 10 POS vendors, in addition to MICROS, have been attacked in recent weeks. And he contends there is no definitive link to MICROS or the gang behind Carbanak.
Meanwhile, hotel management company HEI Hotels & Resorts last weekend reported a POS-related breach at 20 properties, including several Marriott, Sheraton and Westin hotels. The breach likely exposed cardholder names, card numbers, expirations dates and verification codes used between March 2015 and June 2016, the company says. The number of cards exposed is not known.
Oversight of Vendors
While security experts can't say whether the latest hotel breaches are linked to the breach at MICROS - which has POS systems deployed at more than 330,000 locations, including hotels, across 180 countries - they do say that recent developments point to the need for more stringent oversight of POS vendors and other suppliers.
"Hackers no longer seem to be focused on a single merchant," Holden says. "They are focused on doing mass-production attacks across multiple merchants, which makes it difficult to pinpoint the point of breach. That's extremely concerning to me, because this changes the game. It's not just individual merchants that have to protect themselves; it's also the support infrastructure, the POS systems and services providers - and they are typically not as secure as the merchants."
And John Buzzard, fraud specialist at CO-OP Financial Services, a credit union network that provides ATM, card payment and mobile services, says these incidents should serve as a reminder of just how easy it continues to be for hackers to exploit poorly monitored security at vendors.
"We have seen vendors as the weakest link before, as with the Target breach," Buzzard says. "Organizations need to consider one-time access credentials that expire quickly and require reissuance for vendors to avoid the classic case of backdoor vulnerabilities via login credentials. Does your vendor really need 365-day access to your system? Ninety-day password expiration may simply not be adequate in some circumstances, as an example."
Visa's Alert
In addition to a possible connection to Carbanak, Visa's alert also notes a potential connection between the MICROS breach and MalumPOS, a malware strain discovered in 2015 by Trend Micro that is "still actively used by cybercriminals."
Visa recommends that retailers scan their networks for the presence of MalumPOS, and that "all" retailers, even those that don't use MICROS systems, as well as financial institutions, scan their networks for the presence of Carbanak.
Visa's alert offers no dates of possible compromise surrounding the MICROS breach, and MICROS has repeatedly declined to offer additional information beyond what it reported in its recent letter to customers.
Other POS Vendors Targeted?
Days after security blogger Brian Krebs on Aug. 8 broke news of the MICROS breach, noting a possible link to the Russian cybercrime gang behind Carbanak, Hold Security began scanning the Web and customer systems for suspicious activity, Holden says (see MICROS Breach: What Happened?).
The firm quickly identified 10 other POS suppliers that also had been compromised, he says.
"We looked through our monitoring system and identified the way the hackers broke into MICROS and 10 other organizations," he says. But Holden would only name five of those additional POS providers - Cin7, ECRS, NavyZebra, PAR Technology and Uniwell - saying that it was not yet known whether the other five had addressed their vulnerabilities.
Holden contends the attacks against the POS vendors do not appear to be linked to the Carbanak gang.
After reviewing communications and chat logs in underground forums exchanged between the attackers, he says, researchers at Hold Security concluded those responsible are "a Russian actor and an actor from West Africa who speaks with a definitive dialect in English. We know this because it is not the type of dialect you would see in Chinese or a hacker from some other country. The Russian is breaking into the systems and the English-speaking actor is more like a broker, trying to sell the back-end data. ... This is not how the Carbanak gang operates; they typically do not sell data or work with hackers outside of Russia."
Multiple groups, including the gang behind Carbanak, however, could have simultaneously targeted MICROS, Holden acknowledges. But Hold Security could not find a connection between MICROS and Carbanak, he says.
Holden says the attacks his firm identified date back to July 15 or 16, with the exposure window lasting about two or three weeks. And huge amounts of data - anywhere from 14 kilobytes to 16 kilobytes - were exfiltrated by hackers from most of the 10 identified POS providers, he says.
"It's very difficult to tie the actors we've seen to the malware strains identified by Visa," Holden says. "But I can tell you from experience that when hackers download that amount of data, they are trying to understand the infrastructure of the POS network."
Hotel Breaches Raise New Questions
Similarly, it is difficult to link any of these POS vendor attacks to the breach of hotel management firm HEI, which manages properties for Starwood Hotels and Resorts, Marriott, Hilton, Hyatt and InterContinental Hotels Group, Holden adds.
"It's technically possible they are linked to HEI, but we can't say for sure," he explains.
And some security experts say it's possible that HEI's breach is linked to earlier attacks against hotel chains Starwood, Hilton, Hyatt, and, most recently Kimpton, part of Intercontinental.
Whether any of those attacks are linked to the MICROS breach is unclear. HEI has not revealed whether MICROS devices and systems are used by any of its properties.
"Without being involved in the actual forensics investigation, it's pure speculation whether these attacks are related or not," says Christopher Budd, a global threat communications manager at Trend Micro. "However, there is one key difference between the MICROS attack and some of the other retail point-of-sale attacks: The MICROS attack appears to focus on the POS maker/vendor, where previous attacks have focused on compromising the endpoint POS devices on the target's premises."
- Details
- Category: Security News
Anti-Malware , Encryption , Risk Management
Malware Developer Earns $1 Million Annually via Affiliates, Researchers Say
Limited-time offer for Cerber 2 ransomware victims: Recover your forcibly encrypted files without resorting to paying a ransom to attackers to obtain a decryption program.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
Check Point Software Technologies has released a free Cerber ransomware decryption tool that it says victims can download and use to restore forcibly encrypted ransomware files, including files encrypted by Cerber version 2, which debuted July 29. "The tool analyzes the sample file the user uploads and generates a private decryption key for the user, which they can then unlock other files with," a Check Point spokesman tells Information Security Media Group.
Cerber, which first appeared in March, is notable for often containing an audio file with a ransom message. The ransomware largely spreads via spear-phishing campaigns, security experts say.
Cerber 2, according to anti-ransomware forum Bleeping Computer, encrypts 455 files extensions, ranging from .backupdb, .doc and .html, to .mp3, .pptx and .zip. Many current versions of Cerber demand a ransom payment of 1 bitcoin, currently worth about $570, according to security researchers. Cerber campaigns are also backed by a customer service team designed to field customer queries, in an attempt to maximize attackers' illicit profits (see Ransomware Gangs Take 'Customer Service' Approach).
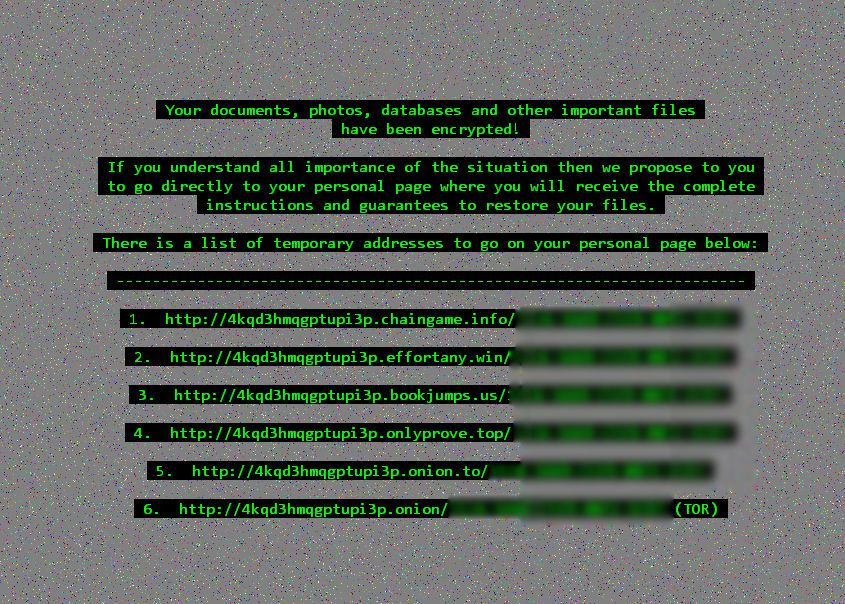 The ransom notice displayed by Cerber 2. Source: Bleeping Computer
The ransom notice displayed by Cerber 2. Source: Bleeping Computer
Don't, however, expect the new decryption tool to work indefinitely. Indeed, Cerber 2 appeared to be developers' reaction to a free decryptor released by security firm Trend Micro, which could decrypt some - although not all - Cerber-encrypted files. "We can decrypt the data because of the weak key that Cerber used," the developer of Trend Micro's decryption tool, an employee known as Panicall, said in a discussion on a Bleeping Computer forum. He added that the weakness could only be used in some cases, suggesting that the average victim might only be able to decrypt about 70 percent of encrypted files using the tool.
But Cerber 2 fixes the weakness that Trend Micro was been able to exploit, Panicall said Aug. 2 via Twitter. "The author must have read my code," Panicall said.
Check Point didn't immediately respond to a request for comment about whether it planned to participate in the No More Ransom portal, a public-private partnership designed to give ransomware victims a one-stop shop for decrypting their data, if and when related tools are available (see Ransomware Gangs Take 'Customer Service' Approach).
New variant of Cerber ransomware confirmed today, not supported by our tool now. The author must have read my code. @demonslay335
Best Strategy: Avoid Infection
The cat-and-mouse game between Cerber's developer and security firms - working on behalf of victims - is a reminder that the best way to deal with a ransomware infection is to never get infected in the first place. For any individual or organization that does suffer a ransomware infection, however, the next step involves mitigation, and deciding on a course of action: Pay the ransom, kiss the data goodbye or decrypt the data using a freely available tool.
Decisions can be complicated by time-related factors. "Institutions that have time-sensitive records, like hospitals and banks that need to get access immediately, are increasingly being the targets for ransomware," says Mark Rasch, security evangelist at Verizon Enterprise Solutions (see Hospitals and Ransomware: The Temptation to Pay).
That's because cleaning up from a ransomware infection takes time. Any organization that can't afford to spare that time - not just hospitals and banks but also law firms and any organization involved in sensitive merger-and-acquisition discussions - will face incentives to pay attackers.
Affiliate Program
The rise of ransomware has been aided by automated attack tools, such as Cerber, that are designed to be used by those who are not technically proficient. In fact, Cerber gets distributed via an affiliate program, Check Point says in a new report into the gang behind Cerber. Check Point notes that it first found a Russian-language advertisement soliciting new affiliates posted by an individual using the handle "crbr" on an underground forum in February. "The ad includes an extensive and accurate explanation about the malware itself, the landing pages, the partnership program through which the malware is sold and the estimated profit," the Check Point report says.
Based on its researchers' subsequent, presumably anonymous, interactions with crbr, Check Point says that crbr's job is to recruit new affiliates to infect PCs with Cerber. "In return, the participating affiliate receives part of the profit," it says. "In the ad's example, the participating affiliate earns 60 percent of the profits with an additional 5 percent for recruiting a new member to the program. The rest of the money goes to the developer."
The control panel offered to affiliates is available in 12 languages, including Arabic, Chinese, Portuguese and Turkish, crbr told Check Point researchers.
According to figures supplied by crbr, 3 percent of all victims - largely hailing from Australia, Canada, France, Germany, Great Britain, India, Italy, South Korea and the United States - pay to purchase the decoder.
Cerber Gang: Russians Suspected
By tracing communications between Cerber ransomware infections and the dedicated servers used by the developer to manage the infections, Check Point estimates that Cerber ransom payments in July amounted to $195,000 via 161 active campaigns that infected nearly 150,000 victims. Accordingly, the developer's monthly takings would have been about $78,000, while affiliates would have split the rest.
If those takings remain constant, Cerber's developer stands to earn about $1 million per year. "We believe Cerber originates in Russia, as some of the advertisements appeared in Russian," Check Point's report says. "In addition, Cerber's configuration file reveals that the ransomware does not infect targets in the following countries: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine and Uzbekistan. Typical for Russian malware, this approach allows actors to avoid legal consequences by law enforcement agencies in these countries."
According to a portion of the Cerber 2 configuration file extracted by Trend Micro's Panicall, the ransomware also won't run if it detect anti-virus software from one of 17 vendors, including Avast, Bitdefender, ESET, F-Secure, Kaspersky Lab and Lavasoft.
Check Point says many Cerber infections get spread via exploit kits, noting that Neutrino exploit kit victims account for 11 percent of all Cerber ransom payments, while Magnitude exploit kit victims account for 8 percent.
- Details
- Category: Security News
A lesson from down under: A report on unintentionally creating a distributed-denial-of-service attack aimed at oneself highlights the latest edition of the ISMG Security Report.
In this report, you'll hear:
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Aug. 9 and Aug. 12 reports, which respectively analyze the reopening of the encryption bypass debate and threats posed by Russian hackers. The next ISMG Security Report will be Friday, Aug. 19.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
More Articles …
Page 3482 of 3546
