- Details
- Category: Security News

Police have arrested an employee of U.K.-based accountancy and business software developer Sage Group after a data breach. Meanwhile, a report has emerged that some customers are using its software in an unsecured manner.
See Also: How to Mitigate Credential Theft by Securing Active Directory
On Aug. 17, City of London police arrested a Sage insider, following the company warning via its website on Aug. 14 that 200 to 300 U.K. businesses may have been affected by a data breach related to the use of an insider's login credentials.
"The City of London Police arrested a 32 year-old woman on suspicion of conspiracy to defraud at Heathrow airport," a spokesman tells Information Security Media Group. "The woman was arrested in connection with an alleged fraud against the company Sage. She has since been bailed. The woman is a current employee of Sage."
Sage declined to comment on that report, citing the ongoing investigation.
A 32 y/o woman has been arrested in relation to the ongoing fraud investigation from the business firm Sage
Sage says its customers include 6.2 million businesses in 23 countries; it has 13,000 employees. The company is the only technology stock still listed on the FTSE 100 - the 100 largest companies listed on the London Stock Exchange.
Breach Tied to Insider Credential
The data breach stemmed from inappropriate use of a legitimate access credential, Sage reports. "We believe there has been some unauthorized access using an internal login to the data of a small number of our U.K. customers, so we are working closely with the authorities to investigate the situation," Sage says in a notice published on its website. "Our customers are always our first priority, so we are communicating directly with those who may be affected and giving guidance on measures they can take to protect their security." The company also published a toll-free number that all customers can call to receive further information.
Sage says it's also informed Britain's privacy watchdog, the Information Commissioner's Office, about the breach.
"We're aware of the reported incident involving Sage UK, and are making enquiries," an ICO spokeswoman tells ISMG. "The law requires organizations to have appropriate measures in place to keep people's personal data secure. Where there's a suggestion that hasn't happened, the ICO can investigate, and enforce if necessary."
Shodan Unearths Unprotected Servers
Separately, serial bug spotter Chris Vickery says that on Aug. 11, he found that more than 20 organizations were using on-premise Sage X3 servers with poorly configured versions of the MongoDB open source database, raising serious security concerns. Vickery said he spotted the databases via Shodan - a search engine for internet-connected devices and services. The servers are meant to be used by companies with 200 or more employees, he points out.
"So finding more than 20 of them completely exposed to the public internet, with no username or password required for access, was a little unnerving," Vickery says via an Aug. 18 blog post on the site of controversial anti-virus software developer MacKeeper (see MacKeeper Hid Product Update Error). MacKeeper, which last year settled a class-action lawsuit alleging deceptive advertising and false claims, hired Vickery after he warned that the company had inadvertently exposed millions of customers' personal details online, which it then fixed (see MacKeeper: 13M Customers' Details Exposed).
In the case of the Sage servers, Vickery says that some "contained massive amounts of company records in the form of PDFs, DOCs, and XLS spreadsheets," and that he initially warned Sage, believing that it controlled the servers directly. "High-level Sage staff members sent a response back within hours - rather impressive when considering the U.K. time zone difference," he says. "We engaged in a telephone conversation shortly thereafter. The Sage representatives were very clear that while they claim Sage is not at fault for these breaches, Sage is extremely concerned with any situation involving their software being implemented insecurely by clients."
Vickery says that he supplied IP addresses for vulnerable installations to Sage, and that the company has begun directly notifying affected customers. But he warned that the affected companies' information may have already been accessed by other parties.
"I've found logs indicating that I am not the first person to discover these exposed servers," he says. Sage declined to comment on that assertion.
Vickery warns all Sage X3 software users to ensure that they lock down the software. "If you are a large Sage client, make sure that your software installations are behind a firewall or, at the very least, you have some sort of access restrictions in place," he says. "Most companies do, but I know of at least 20 that did not."
- Details
- Category: Security News
Breach Notification , Breach Response , Data Breach
'Sophisticated Attack' Siphoned Card Data for 6 Months, Retailer Warns
Eddie Bauer, an outdoor apparel retailer based in Bellevue, Wash., is warning customers that point-of-sale malware infected its retail store systems for "various dates" over a six-month period before the malware was discovered and eradicated.
See Also: 2016 Annual Worldwide Infrastructure Security Update
Eddie Bauer is owned by San Francisco-based private equity firm Golden Gate Capital and counts about 360 stores in the United States and Canada that were affected by the breach, and about 40 stores in Germany, Japan, and Southeast Asia that were not.
The company's breach notification suggests that every one of its North American stores may have been affected by what it claimed to be a "sophisticated attack." But the breach notification does not detail how many customers may have had their payment card compromised via the data breach, although the retailer says it is reaching out directly to customers who might have been affected, "by mail, a press release, and a website."
"We determined that customers' payment card information used at our retail stores on various dates between January 2, 2016 and July 17, 2016 may have been accessed," says Eddie Bauer CEO Mike Egeck in an Aug. 18 letter to customers. "Not all cardholder transactions during this period were affected. Payment card information used online at eddiebauer.com was not affected."
Eddie Bauer said attackers obtained cardholder names, payment card numbers, security codes and expiration dates for customers who bought or returned products. The retailer did not immediately respond to a request for comment about how it discovered the breach or what type of POS malware was used against it. But on July 5, the retailer told security blogger Brian Krebs, who heard reports of potential fraud at the retailer from several U.S. financial institutions, that it was not aware of any breach.
Egeck said that in the wake of the retailer learning it had been breached, it "immediately initiated a full investigation with third-party digital forensic experts to identify and contain the attack as quickly as possible" and also alerted the FBI. The retailer says the breach has now been contained.
"Out of an abundance of caution, we are offering identity protection services to all customers who made purchases or returns in our stores between January 2, 2016 and July 17, 2016," Egeck says, via Kroll.
@Crackerjen Protecting customer payment info is our top priority. We're directly notifying affected customers: https://t.co/A5sC2paBGi
Yet Another POS Malware Campaign
The retailer said that during the course of its investigation, it found that the same malware had been used to infect other organizations that use POS devices. "We learned that the malware found on our systems was part of a sophisticated attack directed at multiple restaurants, hotels, and retailers, including Eddie Bauer," Egeck says. "We are conducting a comprehensive review of our IT systems to incorporate recommended security measures in order to strengthen them and prevent this from happening again."
Security experts say that while different cybercrime gangs may employ different types of POS malware, most of it is functionally identical, unsophisticated and could be better blocked if retailers changed default passwords on their POS devices and used segmentation to better isolate POS systems (see Why POS Malware Still Works).
Eddie Bauer didn't immediately respond to a request for comment about whether its POS devices sported default passwords, and whether it employs network segmentation (see Solve Old Security Problems First).
Breach Alert: HEI Hotels & Resorts
In other POS malware news, HEI Hotels & Resorts last week began warning that anyone who used a payment card at one of 20 affected U.S. hotels that it runs - including several Hyatt and Marriott locations - may have had their card details compromised by point-of-sale malware. It's not clear if the breach is related to the Eddie Bauer attack, or to the recent warning from POS systems and services provider Oracle MICROS that revealed a breach impacting its legacy POS systems. In response, Visa issued an alert warning merchants to be on the lookout for malware attacks linked to MICROS (see Recent POS Attacks: Are They Linked?).
HEI's breach notification warns that customers at 20 hotels - ranging from the Boca Raton and Dallas Marriott to Le Meridien San Francisco and the Westin Washington D.C. may have had their payment card data exposed if they used a payment card in any of the affected hotels. According to a list of hacked hotels, the breaches began at some hotels on March 1, 2015, and lasted at some properties until June 21, 2016. HEI says all affected hotels' POS systems - including in restaurants, gift shops and spas - were potentially compromised by malware that intercepted payment card data as cards were being swiped.
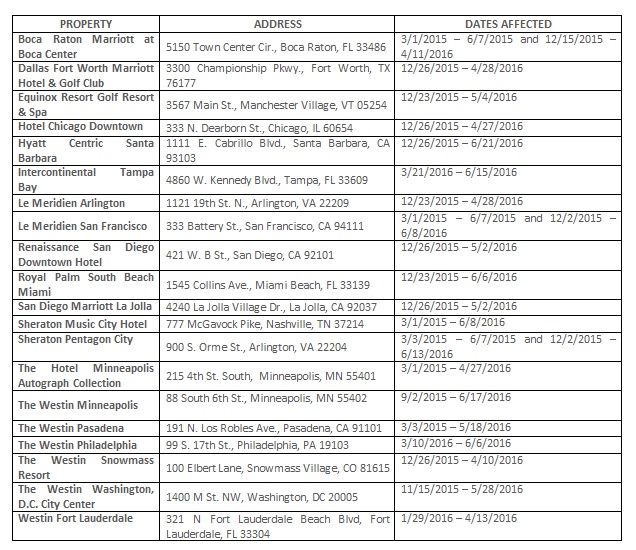 The HEI Hotels & Resorts hack attack resulted in payment card data being potentially stolen at the the listed properties, during specified dates.
The HEI Hotels & Resorts hack attack resulted in payment card data being potentially stolen at the the listed properties, during specified dates.
Based on the hotel chain's related digital forensic investigation, which it launched in June, hackers potentially compromised cardholders' names, account numbers, card expiration dates and verification codes. "We are sorry for any concern or frustration that this incident may cause," HEI says, adding that it doesn't store credit card data, and that none of its POS systems allow for PIN entry, so no PIN numbers associated with debit cards were compromised.
The hotel chain doesn't know exactly how many customers might have been affected, because they may have used their payment cards at properties multiple times, HEI spokesman Chris Daly tells NBC. But he notes that during the POS malware infection period, about 8,000 transactions occurred during the affected period at the Hyatt Centric Santa Barbara hotel in California, and about 12,800 were made at the IHG Intercontinental in Tampa, Florida.
HEI says the breach has been contained and that it's continuing to work with law enforcement. "As part of the investigation, we removed the malware and are in the process of reconfiguring various components of our network and payment systems to further secure our payment card processing systems," HEI adds. Despite that work still being in progress, the hotel claims that "individuals can safely use payment cards at our properties."
POS Malware Epidemic
HEI is just the latest in a long line of hospitality organizations warning that their systems were infected by POS malware. Other breached organizations in the sector have included Hilton, Hyatt, Omni Hotels & Resorts, and Starwood Hotels and Resorts, as well as Trump Hotels, which potentially fell victim to two separate breaches.
- Details
- Category: Security News
The National Institute of Standards and Technology is revising its guidance on how organizations outside the U.S. government should protect sensitive federal data.
NIST has published a revised draft of its 14-month-old guidance, Special Publication 800-171: Controlled Unclassified Information in Nonfederal Information Systems and Organizations.
In an interview with Information Security Media Group, NIST Fellow Ron Ross says the most significant update is a proposed requirement that organizations provide, if requested, documents to show how they're securing sensitive government data on their computers or furnish plans explaining how they will do so.
"This kind of puts everybody in an accountability state," says Ross, chief author of the guidance. "It's truth in advertising."
U.S. federal agencies enter contracts with thousands of private businesses to provide credit card and other financial services, email services, conduct background checks for security clearances, process healthcare claims and furnish cloud services.
Sensitive federal information often is provided to or shared with state and local governments, colleges and universities and independent research organizations. SP 800-171 aims to help these organizations secure sensitive data. The guidance also helps government officials responsible for contracting with these organizations to determine whether federal controlled unclassified information remains secure outside the government.
In the interview (click on player beneath image to listen), Ross:
Explains how the revised draft document differs from the initial guidance published in June 2015; Defines controlled unclassified information, the sensitive data at the heart of the guidance; and Describes the rationale behind why organizations housing sensitive government data need to safeguard that information.At NIST, Ross specializes in security requirements definition, security testing and evaluation and information assurance. He leads NIST's Federal Information Security Management Act Implementation Project, which includes the development of key security standards and guidelines for the federal government and critical information infrastructure.
- Details
- Category: Security News
An update on untangling the confusion surrounding the data dump by the mysterious group Shadow Brokers, and possible links to the U.S. National Security Agency and Russian intelligence, lead the latest edition of the ISMG Security Report.
In the report (click player beneath above image to listen), you'll hear:
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Aug. 12 and Aug. 16 reports, which respectively analyze threats posed by Russian hackers and the mysterious increase in traffic that forced the Australian government to shutter a census website. The next ISMG Security Report will be Tuesday, Aug. 23.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
Encryption , Risk Management , Technology
Researchers Liken Cisco PIX Exploit to 'Internet God Mode' Image: Contributed
Image: ContributedThe U.S. National Security Agency was apparently able to decrypt any traffic sent using a Cisco PIX device that was built from at least 2002 to 2008. While Cisco stopped supporting PIX devices in 2013, more than 15,000 remain in use and are still vulnerable to related exploits.
See Also: 2016 Annual Worldwide Infrastructure Security Update
Those findings come via security researchers who continue to pore over the 250 MB Equation Group data dump from Aug. 13, which contains a bevy of firewall attack tools. The tools are designed to compromise devices built by Cisco, Fortinet, Juniper and Topsec (see Equation Group Stings Firewall Vendors with Zero-Day Flaws).
Based on security researchers' teardowns of the tools, as well as an NSA malware manual released Aug. 19 by the Intercept - via documents provided by former NSA contractor Edward Snowden - there is widespread agreement that the tools were built by the NSA. But the identity of the Shadow Brokers remains a mystery.
Cisco has confirmed that two vulnerabilities exploited via the dumped tools were legitimate and could be exploited by tools named EXTRABACON and EPICBANANA. The former exploited a zero-day flaw, which Cisco has patched, while the latter targeted a flaw that Cisco patched in 2011. Fortinet has also patched an update for a flaw contained in the dump, and Juniper says it's continuing to review the data dump.
But in recent days, researchers have made a new discovery: An exploit called BENIGNCERTAIN allowed the NSA to decrypt any traffic being handled by Cisco PIX devices - including devices set to function as VPNs - from at least 2002 to 2008, according to security researcher Mustafa Al-Bassam, who has been cataloging "exploits, implants and tools for hacking firewalls" that are contained in the 250 MB Equation Group dump.
In a blog post, he says the exploit appears to allow an attacker to extract private VPN keys from a vulnerable PIX device simply by sending it Internet Key Exchange packets designed to cause the device to dump some of its memory. "The memory dump can then be parsed to extract an RSA private key and other sensitive configuration information. That's huge," he says via Twitter.
Security researcher Brian Waters has tested BENIGNCERTAIN on Cisco hardware and found that it works up to at least version 6.3(5)145.
Cisco Confirms Some PIX Devices Vulnerable
In light of those findings, Cisco's security team issued an Aug. 19 blog post confirming that PIX versions 6.x are affected by BENIGNCERTAIN, while PIX versions 7.x and the ASA series are not.
Cisco stopped supporting all PIX hardware in 2013; it's been considered "end of life" since then.
"Our investigation so far has not identified any new vulnerabilities in current products related to the [BENIGNCERTAIN] exploit," Omar Santos, principal engineer of Cisco's Product Security Incident Response Team, says in the blog post. "Even though the Cisco PIX is not supported ... out of concern for customers who are still using PIX we have investigated this issue and found PIX versions 6.x and prior are affected. PIX versions 7.0 and later are confirmed to be unaffected by BENIGNCERTAIN. The Cisco ASA is not vulnerable." But Cisco ASA devices have been vulnerable to EPICBANANAS and EXTRABACON.
Unearthing a historical flaw that shows how the NSA may have enjoyed persistent access to any PIX device for 11 years or more is worrying. But so is the prevalence of still-deployed - and no longer supported - PIX devices. Al-Bassam, for example, counts 15,000 PIX devices - including 9,000 in Russia and nearly 3,000 in the United States - that are online and vulnerable to BENIGNCERTAIN.
There's actually over 15,000 Cisco PIX firewalls online today vulnerable to BENIGNCERTAIN, most of them in Russia. pic.twitter.com/rmwHBEyGW9
PIX Devices Power Botnets
Some of those vulnerable PIX devices in Pakistan have been used by other attackers to help build three botnets, including a botnet comprised of 1,700 devices infected by Kaiten.c, an IRC-based distributed denial-of-service attack tool, Al-Bassam says. "Whoever owns this botnet, they seem to have owned an entire department of the Pakistan government: the Pakistan Software Export Board," he says. "Most likely someone is compromising Cisco firewalls to grow their botnet."
The PIX devices continue to remain vulnerable to the exploited flaw, and Cisco has given no indication that it plans to release a PIX patch.
Someone compromising Cisco PIX routers has managed to grow a botnet of 1700 bots. pic.twitter.com/cOmjZYxa15
The ability to remotely intercept and decrypt traffic from Cisco VPNs and firewalls offered the NSA the equivalent of "Internet god mode," according to "Hacker Fantastic," which is the handle of a white hat hacker who works for U.K. consultancy MDSec. "God mode" is videogame-speak for cheat code that allows players to gain invincibility as well as go anywhere and do anything in a game, including walking through walls.
Anyone calling NSA exploits released lame has literally 0 clue value of such code. Remote unauth'd cisco PIX & ASA code is Internet god mode
After Snowden Leaks, Fresh Exploit Questions
The existence of BENIGNCERTAIN is certain to prompt tough questions for the U.S. government and its approach to searching for - and weaponizing - exploits for hardware and software built by major vendors, including U.S. manufacturers.
"What is a company supposed to do when the very technology that they bought to protect them makes them vulnerable?" Jeff Pollard, a principal analyst focused on IT security at Forrester Research, asks The Washington Post.
Already, some security watchers have called on the U.S. government to more quickly release details of vulnerabilities that it finds to manufacturers.
But Robert David Graham, who heads offensive security research firm Errata Security, notes that exploits don't grow on trees; intelligence agencies go hunting for them and oftentimes develop them with specific uses in mind. In a blog post, he notes that there can be legitimate uses for exploiting these flaws - such as hacking into a terrorist network - which complicates the vulnerability-disclosure discussion.
"There are legitimate policy questions about government hacking and use of [zero] days," Graham says, while adding that he would like to see the government more clearly articulate how and when it uses such exploits. "At the bare minimum, there should be more transparency."
More Articles …
Page 3486 of 3546
