- Details
- Category: Security News
Breach Preparedness , Cybersecurity , Data Breach
Should Political Parties Be Deemed Critical Infrastructure? DHS Secretary Jeh Johnson Moves to Protect Integrity of Voting System Homeland Security Secretary Jeh Johnson. Photo: DHS
Homeland Security Secretary Jeh Johnson. Photo: DHSIn mulling whether to designate the U.S. electoral system as critical infrastructure, which could lead to beefed up cybersecurity protections, the question arises whether those safeguards should focus just on the voting process itself or be extended to other components, such as political parties.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Homeland Security Secretary Jeh Johnson earlier this month suggested that the federal government should consider designating the electoral system as critical infrastructure following the revelation of breaches of various Democratic Party computer systems, with hackers tied to the Russian government being prime suspects (see Labeling U.S. Electoral Systems as Critical Infrastructure). Emails leaked from the hacks showed bias among top party leaders against the presidential candidacy of Sen. Bernie Sanders, and publication of those messages resulted in the resignation of the Democratic National Committee chairwoman, Rep. Debbie Wasserman Schultz of Florida.
But Johnson's recent actions in support of bolstering cybersecurity protections for the electoral system have focused on the more narrow voting process than the broader network of other stakeholders, such as political parties.
Johnson Meets with State Election Officials
At an Aug. 15 teleconference with state officials responsible for the voting process, Johnson offered them the assistance of DHS's National Cybersecurity and Communications Integration Center. NCCIC would conduct vulnerability scans, provide actionable information and access to other tools and resources for improving cybersecurity, according to a readout of the call.
The secretary said DHS is unaware of any specific and credible cybersecurity threats to the voting systems related to the upcoming presidential and congressional elections. Nevertheless, he announced his agency is convening a voting infrastructure cybersecurity action campaign with experts from all levels of government and the private sector to raise awareness of cybersecurity risks potentially affecting voting infrastructure and promote the security and resilience of the electoral process.
The Role of Political Parties
The hack of computers at the Democratic National Committee and Democratic Congressional Campaign Committee got Johnson started on publicly pondering elevating the electoral system to critical infrastructure. But should political party organizations be included in the definition of the electoral system?
Some in the cybersecurity community see the political parties as outside the system that could be labeled critical infrastructure. "They have no impact on citizen security, health and monetary systems," Robert Bigman, former CISO at the CIA, says in arguing against inclusion.
Bigman says the core of the electoral system could deserve critical infrastructure designation. Those central elements would include the Federal Election Committee and the 9,000 or so local and state government entities that run elections in the United States.
Sen. Tom Carper, the Delaware Democrat who serves as the ranking member of the Senate Homeland Security and Governmental Affairs Committee, encourages Johnson to explore designating the electoral system as critical infrastructure. And like Johnson, Carper cites the DNC and campaign committee hacks as rationale to elevate protections. "If these reports (of Russian hacks of Democratic Party computers) are accurate, such an intrusion raises concerns about the ability of foreign actors to interfere in the American political process during the upcoming election, including through cyberattacks targeting electronic voting machines or the information technology of state and local election officials," Carper writes in a letter to Johnson.
Safeguarding Integrity of Election Process
Clearly, designating the voting system as critical infrastructure is long overdue. It's at the core of our democracy, and safeguarding its integrity is vital. We wouldn't want the Russians, other nation-states or even political parties hacking systems used to run our elections.
But expanding the electoral system to include political parties and other political entities involved indirectly with the election process could prove problematic. "That's a tough call," says Malcolm Harkins, author of Managing Risk and Information Security: Protect to Enable and chief security and trust officer at the malware prevention provider Cylance. "Is a political action committee part of the electoral system?"
Harkins says critical infrastructure should only include the voting system because "it has direct material significant implications if the integrity or the availability or confidentiality of that system itself was manipulated."
Still, he recognizes that information systems operated by political parties and PACs, if exploited by a hacker, could have an adverse impact on the election process. "That, certainly, has some potential for manipulation that could sway things one way or another," he says. "But I think there's much more indirect impact."
Nevertheless, that indirect impact could have significant consequences on the integrity of the election process. So when considering the electoral system as critical infrastructure, the government shouldn't automatically rule out those indirect stakeholders.
- Details
- Category: Security News
 Photograph: Berlinale/EPA
Photograph: Berlinale/EPAAn unparalleled mystery has piqued the security community's curiosity. A group calling itself the "Shadow Brokers" has claimed to have stolen code and exploits from the Equation Group, a nation-state spying group suspected to be linked to the U.S. National Security Agency.
See Also: Protecting Your Assets Across Applications, Services and Tiers
Security experts are cautiously saying that the sample code appears to be legitimate and isn't simply a repackaging of something else. The Shadow Brokers is auctioning the information, but said if it receives an absurd 1 million bitcoins - worth some $568 million - it will release all of the data publicly. As a teaser, the group released a 256MB batch of code and exploits. Tumblr and GitHub quickly removed the files, but it's now widely circulating among security experts.
"We hack Equation Group," the Shadow Brokers write on Pastebin. "We find many, many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof, no? You enjoy!!!"
The English is so poor it almost seems like it's a put-on. They also encouraged bidders for a nonsensical auction where losing bidders still lose their bitcoins. The winner of the auction gets the password to an encrypted file that comprises the rest of the data.
 A screenshot, released by the Shadow Brokers, showing directories filled with dumped data.
A screenshot, released by the Shadow Brokers, showing directories filled with dumped data.
But the code samples they've released are no joke. The dump contains offensive tools designed for someone who's aiming to do larger-scale, network-level monitoring. Some of the code specifically targets firewall products from Cisco, Fortinet, Juniper and the Chinese vendor TopSec (see Juniper Backdoor: How Are Vendors Responding?). Other code is aimed at modifying firmware, adding hidden user accounts or slipping backdoors into network equipment.
"This is definitely not for cybercriminals," says Andrew Komarov, chief intelligence officer with InfoArmor, who has been studying the dump. "It looks very, very comprehensive, but some samples of code don't make any sense."
The nature of some of the code and files suggests an intelligence agency or one of its partners left its virtual garage door open, allowing the Shadow Brokers to swipe some of its half-finished tools. Many of the files contain comments and test strings that suggest the Shadow Brokers maybe have breached a developer's repository, Komarov says.
Sloppy Code
The leaked code is also not terribly current. Some of the most recent files are from 2013, with others date back to 2010. The code isn't sexy, either.
"Most of the code appears to be batch scripts and poorly coded Python scripts," writes Matt Suiche, a security expert and founder of Comae Technologies, in a blog post. "Nonetheless, this appears to be legitimate code."
The NSA has a powerful collection of hacking tools and exploits, which were confirmed three years ago through the leaks from former contractor Edward Snowden. The once-in-a-lifetime leak gave deep insight into the methods and techniques the agency uses.
So does the Shadow Brokers' code belong to the NSA? It's hard to say, and experts are reluctant to tag anything on the spy agency given the difficulty of attribution. But the samples of the code - and their tongue-in-cheek code names - echo the NSA's Tailored Access Operations catalog revealed by the publication Der Spiegel in December 2013.
For example, some of the files and folders have names including EPIC BANANA, EXTRA BACON, ELIGIBLE BACHELOR and ELIGIBLE CONTESTANT. The naming conventions, of course, could just be part of be an elaborate ruse.
But some experts suspect otherwise. "It looks genuine," Nicholas Weaver, a researcher with the International Computer Science Institute - a nonprofit research center affiliated with the University of California, Berkeley - tells The Wall Street Journal. According to Weaver, the router-hacking tools, as well as tie-ins to software to which only the NSA would have had access, suggest that the dumped code is legitimate.
There should be some really uncomfortable oversight questions asked of the NSA over the Equation Group dump.
Broken Equation
The Equation Group first surfaced publicly in February 2015, when Russian security vendor Kaspersky Lab published a lengthy report calling it the "god of cyberespionage." The group had the ability to infect the firmware of hard drives from many manufacturers, an achievement that was unknown and required intimate knowledge of undocumented drive specifications.
Equation also engineered the worm Fanny, which was used against targets in Asia and the Middle East. Fanny used the same two zero-day exploits that were coded into Stuxnet. The United States and Israel are suspected of creating Stuxnet, which was aimed at bridging Iran's air-gapped networks in order to sabotage its uranium centrifuges, disrupting the country's nuclear program.
Kaspersky Lab officials couldn't immediately be reached for comment on the new data dump. The company has never said the Equation Group was part of the NSA, but the group's tactics and targets left little doubt that it was likely part of some Western intelligence operation.
It seems unlikely that the Equation Group would make a mistake that would allow some of its older tools to be stolen by hackers. But it's not unheard of for hackers and cybercriminals to make mistakes. The Equation Group may have just made its first big one.
- Details
- Category: Security News

Over the last several weeks, my colleagues and I have reviewed the state of PCI compliance in recognition of the upcoming 10-year anniversary of the PCI Security Standards Council.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
We've asked experts in the U.S. Europe, India and Australia to offer their opinions about the efficacy of the PCI Data Security Standard and whether it will still be needed 10 years from now (see PCI DSS: The Asian Journey to Compliance). We've also spoken with experts on the PCI Council, too, including General Manager Stephen Orfei, Chief Security Officer Troy Leach and International Director Jeremy King. And the over-arching message has been the same - PCI may not be perfect, but its widespread adoption has dramatically improved card security. And the need for PCI is not going away anytime soon.
It's easy to look at the payments landscape and see only the flaws, the security lapses and the breaches. Even with EMV chip deployment taking hold in the U.S. and in other parts of the world, important security issues remain (see Alleged EMV Flaw Stirs Debate). Payment card data is going to be vulnerable for quite some time - at least until the magnetic stripe is completely replaced with the chip, whether on a card or within a mobile device.
But if we step back a bit and get some perspective, we have to appreciate how far payments security has come.
Plenty of Progress
Think back to 10 years ago, when hackers, including Albert Gonzalez - one of the masterminds behind the attacks against retailers TJX, Hannaford Brothers and 7-Eleven and payments processor Heartland Payment Systems - were breaking through network firewalls with relative ease to steal credit and debit numbers.
Those attacks opened our eyes to just how insecure security practices surrounding payment card transactions actually were.
Beyond storing card data in the clear, weak perimeter security had made it relatively easy for hackers to infiltrate networks and systems to exfiltrate card data at rest and in transit.
Today, we would never consider a firewall, on its own, sufficient network protection. And anyone storing card data without encrypting it would be slapped with a huge fine from the card brands for blatant disregard for complying with PCI security requirements.
"Ten years ago, people weren't doing anything," Bob Russo, the former general manager of the PCI Security Standards Council, says of inadequate security measures. "A breach opens everybody's eyes. But you have to keep reminding them."
PCI expert Anton Chuvakin, a research director at the consultancy Gartner, says most merchants today understand that PCI compliance is a baseline for security. Ten years ago, that was not the case.
"PCI has been a major positive," he says. "Compare 2007 to 2016. A lot of blatantly idiotic insecurities have been 'PCI-ed out,' making it safer for everybody. Has PCI 'fixed' everything? No, of course not. But nothing can 'fix' crime."
The Long-Term Impact
The breaches we've seen over the last decade have become increasingly more sophisticated. But our breach response strategies have become more sophisticated, too, in part because of widespread acceptance and adoption of PCI DSS, says Jeffrey Man, security advocate at Tenable Network Security.
"When I first started with PCI back in 2004, unencrypted cardholder data (including sensitive authentication data) was everywhere," Man says. "One of my first clients was one of the major payment processors. There was pretty much no encryption available back then, at least for databases, so millions of records were being stored unencrypted and compensating controls were relied upon to protect that data. But there were also stored caches and flat files of transaction data on the POS systems, routers, switches, file servers - just about any place you could think of to look for cardholder data back then you could find it."
Reflecting back on the early days of the council, Russo says its members initially believed they could create a standard, work for about five years to ensure it was adopted, and then card security would no longer be a major issue.
"We thought everything would be secure by then," he says. "We thought EMV was going to be the panacea; and we thought PCI might go away. Now we know that is not the case. Will PCI have to evolve? Yes. But I think PCI and EMV will come closer and closer together. In 10 years, they may not call it PCI. But there will be some form of PCI security 10 years from now."
We also now know that PCI compliance is not a one-time goal, but an ongoing process, Man says.
"The payment industry is changing quickly, with new payment methods, mobile payments, EMV and tokenization," Man says. "All of these will change the landscape significantly. But what will not change is the effort of hackers to steal data and commit fraud. The technology is evolving, but the fundamentals of sound data, information and cybersecurity do not change. The challenge of security is due diligence and a certain amount of paranoia. No company is compliant (or secure) if they focus on an annual compliance assessment and overly rely on automated tools and security solutions to provide the necessary level of security. There is no substitute for trained personnel that know the network, the data flows, what's 'normal' and can more likely and quickly detect the abnormalities that are the indicators of compromise."
The Biggest Challenge
PCI has been criticized and challenged, but it's finally evolving into a set of standards to ensure basic card security. The biggest challenge, however, continues to be global adoption, especially among smaller merchants who find the PCI DSS to be quite complex.
Last month, the PCI Council addressed this issue in a compliance resource guide designed for small to mid-sized merchants (see Can Banks Help Small Merchants with PCI?). The resource aims to simplify the compliance process for merchants by helping them identify the requirements that are most critical.
Taking the complexity out of PCI DSS compliance is a huge first step. Also important is educating merchants about why the basic security measures outlined in PCI DSS and other standards are so critical.
Today, most merchants, regardless of their size, finally recognize the need for security. And that's huge progress from where we were 10 years ago.
So, is PCI working? Yes. But its impact will continue to evolve.
- Details
- Category: Security News
ID & Access Management , Risk Management , Technology
Amnesia Project Tackles Password Security App Splits Up Information Needed to Generate Full Password
There's no lack of enthusiasm for trying to change the way we log into services. The weaknesses of passwords are well known, ranging from poor password choices to reusing the same ones over and over. There aren't a lot of good alternatives that can easily supplant the current system, so we're stuck with trying to raise the authentication fence a bit higher in hopes of improving security.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
A former undergraduate student in the computer science department at the College of William and Mary thinks he's come up with a more secure system. He recently presented his peer-reviewed research paper at the 36th IEEE International Conference on Distributed Computing Systems in Nara, Japan.
His system is a password manager without a vault. Password managers are helpful in that they aid in creating and storing complex passwords, but most store those passwords in an encrypted vault. Often, that vault is protected by a master password. All accounts are compromised if the master password is stolen.
Luren Wang's project, called Amnesia, isn't perfect, but it eliminates the weakness of password vaults. It's a generative password manager that uses a combination of information from different sources to reconstruct a password.
Amnesia uses a secret, 256-bit value that is stored in a table on a user's phone. When a user needs a password for a website, the phones passes the secret token to the Amnesia server, which combines it with other secrets stored on the server to construct the password and sends it back to the computer.
"The information that generates the passwords is decentralized, so there's no one point of failure," says Wang, who is now studying for a master's degree in machine learning at Columbia University.
Still a Research Project
Rick Redman of the security consultancy KoreLogic, who reviewed Wang's paper, says the idea of a secret token sent from the phone could be used to augment one-time passcodes sent by SMS, used by many two-factor authentication schemes.
"This is a nice touch," Redman says. "This idea could easily be incorporated into other phone-based 2FA software products that are already well-vetted and tested."
Redman advised that an organization would probably want to host its own Amnesia server rather than relying on cloud providers to host one as suggested in Wang's paper.
One big advantage to Amnesia is that it doesn't require website operators to make any modifications to their login systems while increasing security. In order to compromise a password, an attacker would have to compromise both the Amnesia server and a person's phone. That's far from impossible, but still increases the security around the passwords.
If someone's phone is stolen or lost, the Amnesia master password can be used to set up a new phone. If the Amnesia server is compromised, there's not enough information to successfully steal someone's passwords.
"Though the attackers are able to compromise either the user's smartphone or the master password of the password manager, we assume they cannot compromise both the smartphone and the master password without the user noticing and taking reactive measures," the paper notes.
Areas of Concern
Still, there are other avenues of attack, such as if someone's computer has become infected with a keylogger. Also, the storage of the phone-side secret could be stronger, Redman says. Changing passwords can also be tricky, as generative password managers rely on static information to deliver a password. Wang's paper outlines other potential problems, such as a compromised HTTPS connection and a breach of an Amnesia server, which, while not divulging full passwords, could present social engineering opportunities for an attacker.
It's also not quite as convenient as a password manager, such as LastPass, which quickly autofills stored passwords. With Amnesia, users have to perform an extra click to request a password. A notification of the request pops up on the phone with an IP address, which the user has to approve before it is processed. But it's still easier that two-factor authentication, which often requires a six-digit code to be submitted.
Amnesia is still in the realm of a research project and isn't product ready, Wang says. But a prototype of Amnesia for Android was built, although Wang admits the code wasn't that smooth. Testing of Amnesia with users went well, with the primary complaint of an "ugly UI," he says.
- Details
- Category: Security News
Anti-Malware , Fraud , Phishing
Attackers Increasingly Favor Ransomware Over Banking Trojans, FireEye Says
Cybercriminals wielding Locky crypto-locking ransomware are continuing to ramp up their assaults, especially in the healthcare sector, with attackers distributing less banking malware and more ransomware, according to new research.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
So far this month, several "massive" new phishing campaigns have been launched, targeting victims in multiple industries with Locky ransomware, security researcher Chong Rong Hwa from cybersecurity firm FireEye says in a blog post (see Report: Most Phishing Emails Pack Ransomware).
As in recent months, healthcare remains the sector most frequently targeted by Locky ransomware. So far in August, other oft-targeted industries include telecommunications, manufacturing, aerospace/defense, financial services and government agencies, according to FireEye. Organizations in the United States were most targeted, followed by Japan, South Korea, Thailand, Singapore and Germany.
Attackers often focus on healthcare organizations and other firms that have "time-sensitive records," according to Mark Rasch, security evangelist at Verizon Enterprise Solutions. That's because even if those organizations are well-prepared to detect, block or recover from a ransomware infection, they may not have the time to do so, and thus may have greater incentives to pay a ransom in exchange for decryption keys (see Ransomware: Is It Ever OK to Pay?).
The Rise of Locky
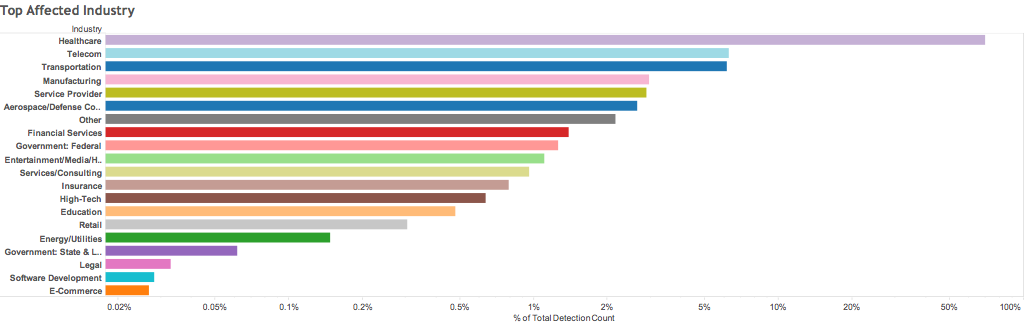 Industries most targeted by Locky ransomware in August 2016. Source: FireEye
Industries most targeted by Locky ransomware in August 2016. Source: FireEye
Locky, which first appeared early this year, has become one of the most prevalent types of ransomware. Its name derives from it adding a .locky extension to encrypted files. Once the ransomware encrypts data on a PC, it typically demands a ransom of between 0.5 and 1 bitcoins ($288 to $577), according to Paul Ducklin, a senior security adviser at security firm Sophos. He says spam emails with Locky attachments often urge recipients to enable macros, so the ransomware can run. "Don't do it," he stresses.
It's not clear who created Locky, although some security experts suspect it's the work of whoever created the Dridex banking Trojan and that the culprits are most likely Russian. Security firm Symantec says that Locky and Dridex have in some cases been distributed by the same spam affiliate group.
JavaScript Out, DCOM Files In
In August, FireEye's Chong says, many Locky-wielding attackers appear to have shifted away from using a JavaScript-based downloader contained in a compressed ZIP file to infect endpoints with Locky. Instead, they're using XML-based .docm files attached to phishing emails. Microsoft Word .docm files are like .docx Word files, except they can also be used to execute macros.
Many cybercrime groups employ automated cybercrime exploit kits to distribute not just banking malware but also ransomware, as was seen in a recent campaign that used the Necurs exploit kit to distribute Dridex banking malware as well as Locky (see Cisco Eyes Ties Between Angler and Lurk Malware).
But at least recently, attackers are distributing less banking malware and more ransomware, Chong says. "We have observed that the delivery of Dridex via this distribution channel seems to have stopped, or nearly so, which could explain why we are seeing the Locky uptick."
Other security firms confirm that in recent weeks, Locky attacks have surged. "These attacks were among the largest campaigns we have ever observed, peaking at hundreds of millions of messages a day," according to a report released last month by the cybersecurity firm Proofpoint. Between April and June, it adds, 69 percent of all malicious email attachments seen in the wild were some form of Locky.
Brazilian Locky Taps Windows Script Files
Whoever is distributing - or helping to distribute - Locky recently began using Windows Script Files to download the ransomware onto victims' PCs, researchers at security firm Trend Micro say in a blog post. The new variant, first seen in the wild on July 15, is being sold on underground Brazilian cybercrime sites, the researchers say.
"WSF is a file that allows the combination of multiple scripting languages within a single file," they say, noting that the WSF files arrive via inside .zip files attached to spam emails that sport email subject lines such as "annual report," "bank account record" and "company database."
The gang behind Cerber ransomware also has used WSF files since May, the Trend Micro researchers say (see Cerber 2 Ransomware: Free Decryption Tool Released). "It would seem that the attackers behind Locky followed Cerber in using WSF files after seeing how such a tactic was successful in bypassing security measures like sandbox and blacklisting technologies ... since it has no static file type," the researchers say. "In addition, using blended scripting languages could result to the samples being encoded, making these arduous to analyze."
Opening Unknown Attachments: Think Twice
Locky is designed to encrypt not just the hard drive of the PC it infects, but also any attached drives and network shares, potentially including any other PC or server that it can access via a local area network. Like many other types of ransomware, Locky also deletes Volume Snapshot Service files, a.k.a. shadow copies, that could otherwise be used to help restore forcibly encrypted files.
Locky often spreads via email attachments. "These latest campaigns are a reminder that users must be cautious when it comes to opening attachments in emails or they run the risk of becoming infected and possibly disrupting business operations," Chong says.
Ducklin at Sophos says one related defense is to download Microsoft Office viewers - applications that "let you see what documents look like without opening them in Word or Excel itself." The viewers do not support macros, thus automatically preventing macro-based malware from executing.
To help block Locky attacks, Trend Micro also recommends stripping all WSF files from incoming emails.
More Articles …
Page 3483 of 3546
