Endpoint Security , Ransomware , Technology
Trump Administration: 'North Korea Launched WannaCry' Why White House Is Suddenly Airing Ransomware Attribution(euroinfosec) • December 19, 2017 WannaCry's ransom note
WannaCry's ransom noteThe U.S. government has belatedly announced that hackers tied to the government of North Korea were behind the WannaCry outbreak that began in May. The ransomware infected more than 200,000 endpoints across 150 countries.
See Also: Ransomware: The Look at Future Trends
"It's Official: North Korea Is Behind WannaCry," reads the title of an op-ed published Monday in the Wall Street Journal, written by Thomas P. Bossert, assistant to the president for homeland security and counterterrorism.
"After careful investigation, the U.S. today publicly attributes the massive 'WannaCry' cyberattack to North Korea," Bossert writes. "It was cowardly, costly and careless. The attack was widespread and cost billions, and North Korea is directly responsible."
Now tell us something we didn't already know.
Spotlight: Lazarus Group
The U.S. government's allegations follow multiple reports from information security firms that fingered the Lazarus Group - a team of hackers with ties to North Korea - as the culprits. In May, The Washington Post reported that the National Security Agency had "moderate confidence" that WannaCry was linked to North Korea. In June, the BBC also reported that a government source told it that the U.K.'s GCHQ intelligence agency believed North Korea was behind WannaCry. Likewise, security researchers at Cybereason, Google, Kaspersky Lab, Microsoft and Symantec said that the tools used in the attack at least suggested that the Lazarus Group had been involved (see US Government Warns of North Korean Hacking).
And yet relatively speaking, WannaCry was mostly a dud. Mistakes in the ransomware code meant that developers couldn't tie individual victims' PCs to bitcoin payments. Poor coding also led to new infections of WannaCry being blocked after a British security researcher accidentally found the equivalent of a kill switch.
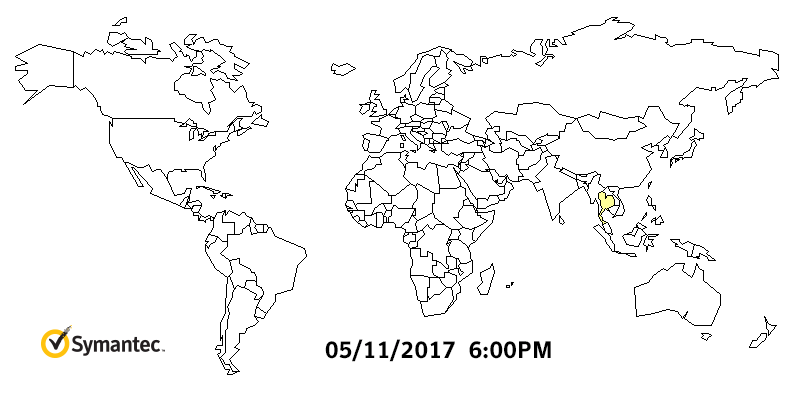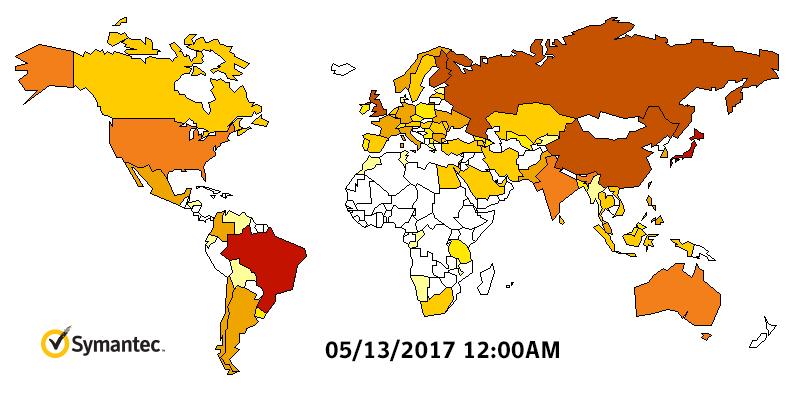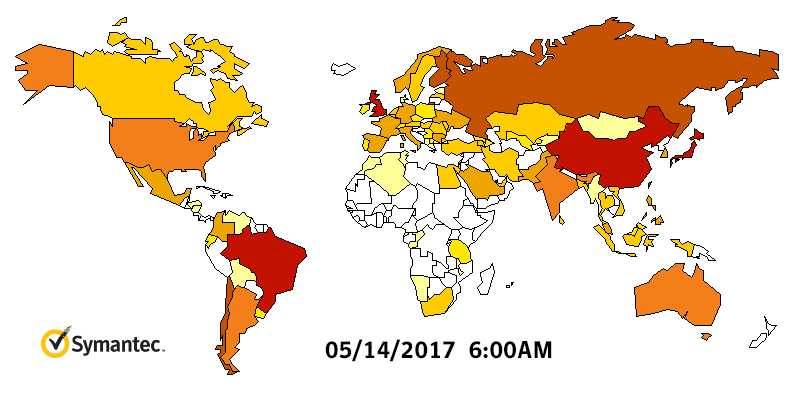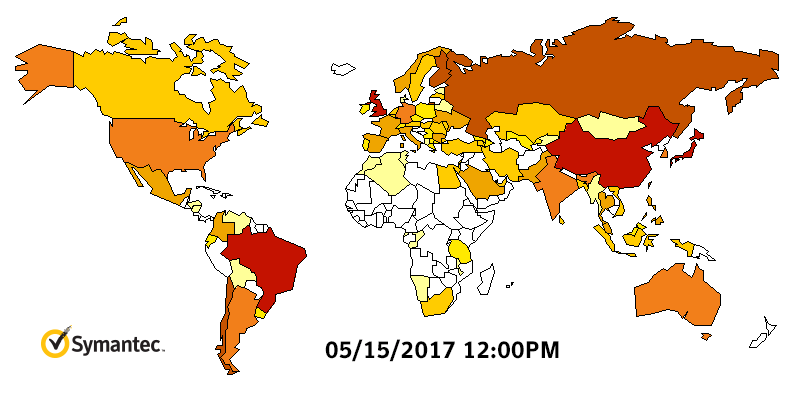 Heatmap shows WannaCry outbreak. Source: Symantec
Heatmap shows WannaCry outbreak. Source: SymantecThe Lazarus Group has also been tied to the theft of $81 million from the central bank of Bangladesh's New York Federal Reserve account via fraudulent SWIFT messages, the use of Adylkuzz cryptocurrency mining malware as well as other attacks aimed at stealing cryptocurrency (see Lazarus Hackers Phish For Bitcoins, Researchers Warn).
By some estimates, hacking could account for one-third of cash-strapped North Korea's gross domestic product.
A Question of Timing
So seven months after WannaCry hit PCs worldwide, why is the White House only now blaming North Korea?
Figuring out who launched an attack often involves technical clues, although ideally, investigators will have visibility into not just the systems used in the attacks, but the precise identity of whoever was behind the keyboard.
After the hack of Sony Pictures Entertainment, the FBI announced that it had proof that North Korean hackers had launched the attack. Officials, however, said they weren't going to release that evidence. Seemingly, doing so might have revealed the extent to which U.S. intelligence was able to track and monitor individuals suspected of being tied to the regime.
Bossert said as much when fielding questions about the timing of the WannaCry attribution in a Tuesday press briefing. "Did we do it too slowly? ... My answer is, no," he told reporters. "The most important thing is to do it right and not to do it fast. We took a lot of time to look through classified, sensitive information. What we did was, rely on - and some of it I can't share, unfortunately - technical links to previously identified North Korean cyber tools, tradecraft, operational infrastructure. We had to examine a lot. And we had to put it together in a way that allowed us to make a confident attribution."
He added that Australia, Canada, Japan, New Zealand and the United Kingdom concur with the U.S. assessment.
Political Exercise
But some security experts say that whatever technical evidence intelligence agencies may gather, attribution remains a political exercise. If there's no good political reason to accuse another country of having done something, then it won't be done.
Timing-wise, the U.S. government imposed stronger sanctions on North Korea last month over the country's nuclear and ballistic missile programs, and it's likely that it's now seeking further diplomatic leverage. Indeed, Bossert's op-ed appeared the same day that President Donald Trump declared that the U.S. would take "all necessary steps" to denuclearize North Korea.
Those steps now include the White House officially accusing Pyongyang of being responsible for WannaCry.
"We will continue to use our maximum pressure strategy to curb Pyongyang's ability to mount attacks, cyber or otherwise," Bossert writes.

