Business Continuity/Disaster Recovery , Governance , Ransomware
Ransomware: Your Money or Your Life 9 Ransomware Defenses Thwart Cybercrime Scoundrels Brian Honan talks ransomware at the AppSec Europe 2017 conference May 11 in Belfast, Northern Ireland. (Photo: Mathew J. Schwartz)
Brian Honan talks ransomware at the AppSec Europe 2017 conference May 11 in Belfast, Northern Ireland. (Photo: Mathew J. Schwartz)Criminals have been separating people from their possessions since possessions were first invented.
So for anyone who follows ransomware, the emergence of the WannaCry outbreak - aka WCry, WannaCrypt - Friday won't come as a shock.
True, the attack's efficacy has been enhanced by attackers marrying their crypto-locking code with a worm, allowing it to spread more easily. But these small innovations are designed with a clear purpose: to allow them to more easily steal more money from victims.
In other words, what's old is new again, now in cyber-enabled form.
The advice for blocking these attacks is simple: Spend time and money on proper prevention, or else you may be forced into considering whether it makes business sense to pay a ransom when attempting to recover from a ransomware infection. Even then, however, there's no guarantee that the criminals that have infected your systems will bother giving you a decryption key.
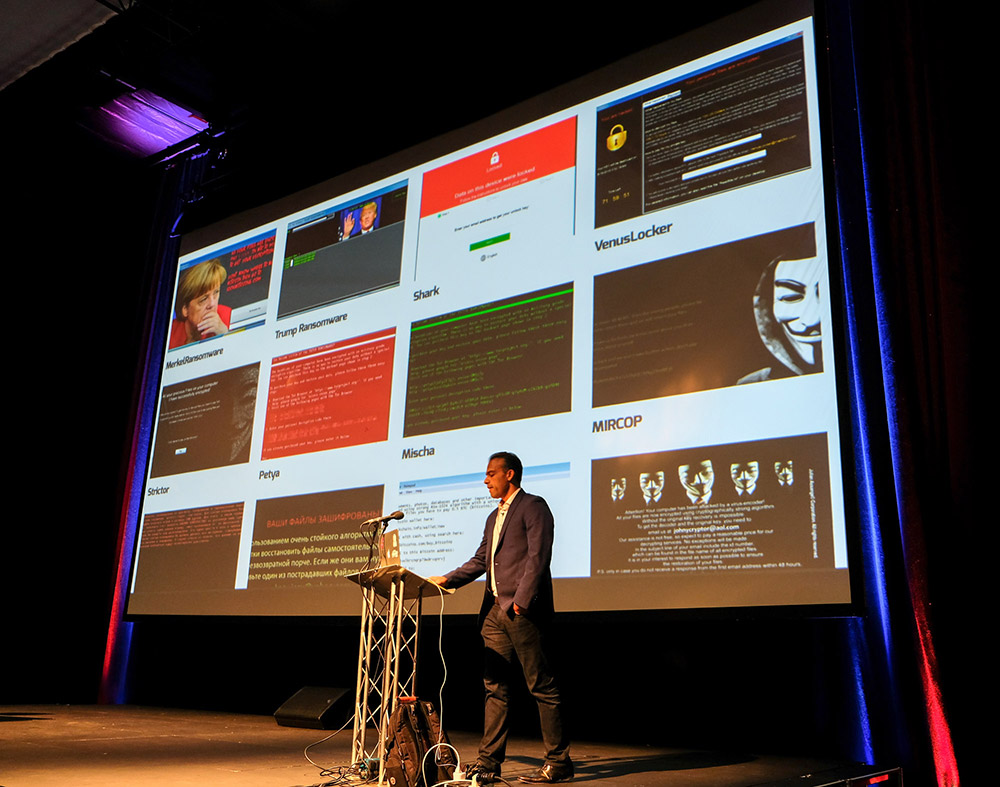 Jeremiah Grossman highlights some of the many different faces of ransomware May 12 in a presentation at the AppSec Europe 2017 conference.
Jeremiah Grossman highlights some of the many different faces of ransomware May 12 in a presentation at the AppSec Europe 2017 conference.Brian Honan, a Dublin-based information security consultant who founded Ireland's first computer emergency response team - IRISSCERT - warns that there's no silver bullet for fixing ransomware. In an interview at last week's AppSec Europe 2017 conference in Belfast, Northern Ireland, he told me that too often, organizations' poor information security practices are partially to blame for their failure to prevent security incidents, including ransomware outbreaks, notwithstanding whatever tools they may have purchased.
"We go into numerous companies that have put in security technologies, but failed to configure them properly," Honan told me. "Why? 'Oh, we ran out of time,' they say."
9 Essential Ransomware Defenses
The basics of battling crypto-locking ransomware haven't changed of late. In the case of WannaCry, the ransomware can be spread via a worm that targets an SMB flaw in Windows, which all organizations should have fixed now regardless (see 5 Emergency Mitigation Strategies to Combat WannaCry Outbreak).
Following the WannaCry outbreak, the U.S. Computer Emergency Response Team - part of the Department of Homeland Security - has reiterated its advice for combating ransomware, as have multiple security experts.
Here's my summary of the experts' recommendations:
Maintain backups: Whitelist applications: Update and patch: Use anti-virus: Think 'least privilege': Kill email-borne macros: Don't click: Virtualize: Consider creating systems that use fast system recovery, via virtualization, to better respond to any malware outbreak. For example, Grossman says he knows of a New York bank that uses thin-client desktops running virtual machines. "Anytime they think there's an infection, they just reset" the virtual image running on all clients, he said. Work with law enforcement: "We're going to need help from law enforcement to investigate and arrest ransomware gangs," Grossman said (see FBI to Ransomware Victims: Please Come Forward).Scant Honor Among Thieves
Reminder: there's no guarantee that any individual or organization that does pay a ransom will ever receive the promised decryption key.
DO NOT PAY the ransom for WCRY, a manual human operator must activate decryption from the Tor C2. See screenshots, I've tried to hack it... pic.twitter.com/xzbK8eqw3Q
Security experts, including the researcher known as "Hacker Fantastic," say that's especially true for WannaCry. Many ransomware campaigns now use automated tools to receive bitcoin payments and send decryption keys to victims. But WannaCry's operators only have a manual process in place. As a result, computer science professor Alan Woodward at the University of Surrey tells me, it's likely that the attackers have no intention to trade decryption keys for ransom payments.
That's why the best, simplest and most effective advice remains: Prepare to battle ransomware outbreaks, or else prepare to pay the consequences.

