Researchers Highlight Concerns for Banks, Credit Unions

Ransomware attacks are on the rise, and some emerging attacks are going beyond PCs to target mobile devices used by banking customers, researchers say (see Banking Cyber-Attack Trends to Watch).
In attacks that researchers have identified within the last three weeks, fraudsters fooled PC users into downloading malicious attachments through skillful spear-phishing schemes used to spread the ransomware known as Cryptolocker.
And a new form of ransomware attack taking aim at employees and customers of banking institutions in Europe has infected mobile phones with the Trojan known as Svpeng.
To help minimize the risks of ransomware, banks and credit unions need to make it a priority to educate customers and employees on how to avoid becoming a victim by following safe Web browsing habits as well as recognizing social engineering tactics used in phishing attacks, says Jeremy Demar, director of the threat research team at online security firm Damballa.
But Etay Maor, a malware researcher at the security firm Trusteer, says banking institutions also need to do more to identify customers' infected or jail-broken devices.
"Banks could be proactive by having a solution that detects that something suspicious is going on with the device," Maor says. "Having software installed on the device that gives the bank a warning if the device is infected is the only way to do this, really."
Ransomware Examples
Ransomware works in two ways. One involves blackmailing users into paying a fee. This is often called "police" or "law enforcement" ransomware because it takes over and freezes a user's device and then displays a message telling the user he or she must pay a fine for allegedly breaking a law by visiting a fraudster's website disguised as a legitimate site.
Kovter, which emerged earlier this year, works in this way, Demar says. "It tells you you've done something bad, and until you pay a fine, your computer will be locked. It's a blackmail attack, but it does not steal anything," he says (see example below).
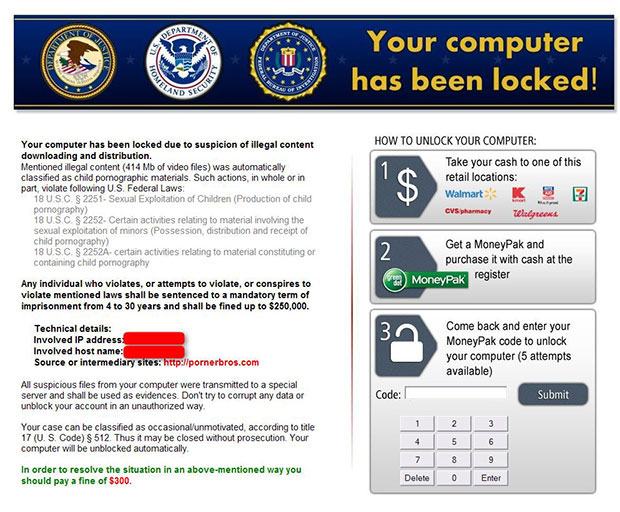
The second method of applying ransomware is a file-locker attack. Cryptolocker, which emerged in 2013, uses this approach. It encrypts files and then demands that the infected user pay a fee to have the files decrypted.
Kovter and Cryptolocker have increasingly targeted U.S. users, with both strains of ransomware showing signs of gaining momentum in recent weeks, researchers say. Neither ransomware strain has been specifically used to target online-banking users, but researchers say any ransomware attack can be used as a mode of distraction, allowing attackers to steal information in the background.
Now enter Svpeng. This mobile malware used to steal online banking credentials from mobile banking applications has recently been enhanced by its developers to have a dual ransomware feature, Maor says.
Svpeng is the first mobile malware to emulate attacks in ways historically only waged against PCs, he says. "When we first saw this malware, it was an overlay attack," he notes.
Overlay attacks in the PC environment, which have been around for years, are designed to steal online banking credentials, Maor says. When users visit an online banking site's log-in page, the malware launches an overlay site, which appears to the user to be the online-banking login screen. Thus, the user is fooled into entering his login credentials into the overlay, which ultimately allows the hackers to steal the credentials and take over the account, he says.
In Svpeng's case, the overlay is launched when a user opens a mobile banking application, he says. "Earlier this year was the first time we saw this type of attack specifically being used on mobile."
Soon after Svpeng made its debut in Europe, it was tailored to wage two types of attacks - overlay and ransomware, Maor says.
Svpeng infects mobile devices in the same way as PCs, through a drive-by download or malicious e-mail attachment, such as an Adobe Flash Player download, he explains. Once a mobile device has been infected, the attackers can launch an overlay or ransomware attack, Maor says.

