For anyone keeping tracking of distributed denial-of-service attack volumes, you ain't seen nothing yet, says Gary Sockrider at DDoS defense firm Arbor Networks.
In the past, DDoS attacks relied on sheer volumes of packets to disrupt targets. As DDoS defenses improved, and to get more bang for their buck, attackers began bringing other techniques to bear, such as reflection/amplification attacks. Reflection refers to spoofing a packet's source address, while amplification means the ability to send a small packet to a server and get a large response back.
To date, IoT botnets - composed, for example, of devices infected with Mirai malware - haven't bothered with such techniques to launch record-setting attacks. But it would be a natural next step.
"We've already seen a new variant of the Mirai source code that actually can do spoofing of the source address, which now gives [attackers] the capacity to combine IoT botnets with reflection/amplification techniques," Sockrider says. "We haven't seen any of these in the wild yet, but we know the capability is already out there. So when you combine these two techniques, we're in the age of the multi-terabit DDoS attack now, and it's imminent."
In an audio interview at RSA Conference 2017, Sockrider discusses:
Why DDoS defense preparation remains essential; Botnet-driven IoT attack trends; The need for carriers and cloud operators to work more closely together on DDoS defense.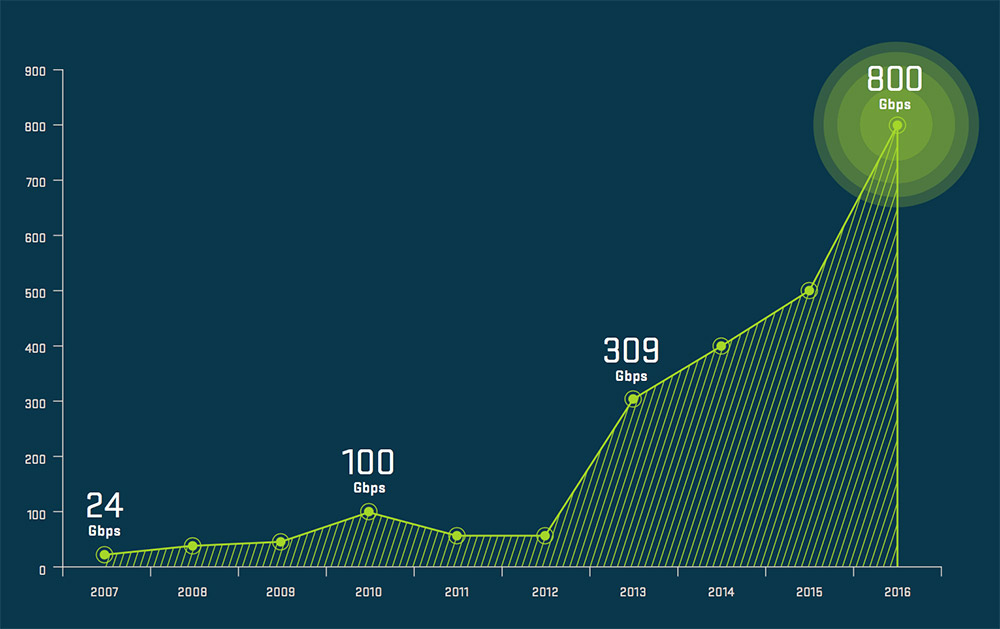 Peak DDoS attack sizes recorded by Arbor Networks.
Peak DDoS attack sizes recorded by Arbor Networks.
Sockrider is principal security technologist at Arbor Networks. Prior to joining Arbor in 2012, he spent 12 years at Cisco Systems and held positions at Avaya and Cable & Wireless.

