Anti-Malware , Risk Management , Technology
Millions of Users at Risk as Developer Piriform Issues Fixed Updates A trojanized version of CCleaner. (Source: Cisco Talos)
A trojanized version of CCleaner. (Source: Cisco Talos)For one month, the installer for a widely used, free Windows utility called CCleaner also installed a malicious payload that was designed to allow attackers to push additional malware onto infected PCs.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
The alert over the software flaw was publicly sounded Monday by security researchers at Cisco Talos, who say they discovered the flaw last week and immediately alerted CCleaners' developer Piriform, which has since confirmed the security problem and issued new, clean versions of CCleaner.
CCleaner is a Windows utility designed to enable users to perform routine maintenance on their systems, including removing temporary files and optimizing hard disk performance.
Prague-based anti-virus firm Avast, which acquired Piriform in July, says CCleaner is used by 130 million, although some of those use the Android version, which was not affected. Piriform says that 3 percent of CCleaner users may have used the trojanized versions.
Piriform says that it did not issue an immediate security alert because it was working with law enforcement to seize the command-and-control server. "Working with U.S. law enforcement, we caused this server to be shut down on the 15th of September before any known harm was done. It would have been an impediment to the law enforcement agency's investigation to have gone public with this before the server was disabled and we completed our initial assessment," the company says.
This type of campaign - trojanizing a legitimate application - is often referred to as a supply chain attack, in which attackers subvert the relationship between a supplier and its customers. "This trust relationship is ... abused to attack organizations and individuals and may be performed for a number of different reasons," according to Cisco Talos.
In another campaign earlier this year, NotPetya malware was infecting Ukrainian organizations after attackers compromised an update server - and potentially also software development environment - maintained by Kiev-based accounting software vendor M.E. Doc.
CCleaner Installer: Malicious Behavior
In the case of the trojanized CCleaner installer, Cisco Talos said that on Wednesday, while conducting a beta test of its exploit detection technology at a customer site, its software flagged a specific executable file as exhibiting malicious behavior.
"We identified that even though the downloaded installation executable was signed using a valid digital signature issued to Piriform, CCleaner was not the only application that came with the download. During the installation of CCleaner 5.33, the 32-bit CCleaner binary that was included also contained a malicious payload that featured a Domain Generation Algorithm (DGA) as well as hardcoded Command and Control (C2) functionality," according to Cisco Talos. "We confirmed that this malicious version of CCleaner was being hosted directly on CCleaner's download server as recently as Sept. 11."
Cisco Talos says that given the potential risk to users, it immediately alerted Piriform.
"Unfortunately no one [had yet] detected the backdoor when we initially disclosed ... hopefully [security products'] blocks pick up quickly," Craig Williams, the senior technical lead for Cisco Talos and a co-author of the report into the trojanized versions of CCleaner, says via Twitter.
It was out for about a solid month, this was no short shelf life
Piriform Apologizes
In a Monday security notification, Paul Yung vice president of products for Piriform, apologized for the security mishap.
Yung says Piriform began investigating suspicious behavior in CCleaner version 5.33.6162 and CCleaner Cloud version 1.07.3191, both for 32-bit Windows, on Sept. 13, apparently after receiving the Cisco Talos alert.
The company found that both versions had been "illegally modified before [being] released to the public." In particular, "an unauthorized modification of the CCleaner.exe binary resulted in an insertion of a two-stage backdoor capable of running code received from a remote IP address on affected systems."
As a failsafe in case that server was compromised, whoever developed the malicious software programmed it to ping a backup instead, using a DGA.
"The algorithm used by this malware is time-based and can be calculated using the values of year and month," according to Cisco Talos, meaning that the security researchers were able to deduce which domains the malware might attempt to contact. Those domains have now been proactively registered, according to Piriform.
Timeline
The trojanized version of CCleaner was released Aug. 15, and an update without the malicious code was released Tuesday. A trojanized version of CCleaner Cloud was issued Aug. 24, and a patched version released Friday.
After discovering the code tampering, Piriform says it immediately alerted law enforcement agencies and began assisting in their investigations. It also says it worked to remove the affected software from all download sites as well as disseminate safe versions to all users and it distributed safe versions via Avast Antivirus for anyone who was already using that product.
Piriform says that the server with which the trojanized versions of CCleaner were communicating has been taken offline.
"The threat has now been resolved in the sense that the rogue server is down, other potential servers are out of the control of the attacker, and we're moving all existing CCleaner v5.33.6162 users to the latest version," he says. The latest version is version 5.34. "Users of CCleaner Cloud version 1.07.3191 have received an automatic update. In other words, to the best of our knowledge, we were able to disarm the threat before it was able to do any harm."
To be safe, Cisco Talos also recommends that anyone who used one of the infected installers revert their PC to a backup that predates the malicious installation to defuse any additional, malicious software that attackers might have pushed to infected PCs. "This isn't a vulnerability," Williams writes in a comment on the Cisco Talos blog post. "The 5.33 installer had malware included with it during the [aforementioned] time window. ... If you upgraded from 5.33 which was installed in the [attack] window you should recover from a backup prior to that version."
Asked to comment on how the code may have been tampered with, and whether it had been subjected to rigorous code-quality checks, Avast directed Information Security Media Group to Piriform's Monday communications, including Yung's security alert.
Investigation Continues
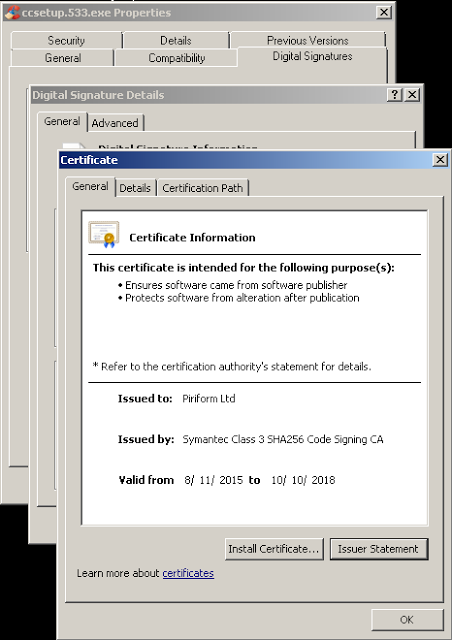 Digital signature used to validate CCleaner 5.33. (Source: Cisco Talos)
Digital signature used to validate CCleaner 5.33. (Source: Cisco Talos)Yung's security alert says Piriform is still tracing how the malicious code was added to the company's software. "At this stage, we don't want to speculate how the unauthorized code appeared in the CCleaner software, where the attack originated from, how long it was being prepared and who stood behind it," he says. "The investigation is still ongoing. We want to thank the Avast Threat Labs for their help and assistance with this analysis."
Cisco Talos notes that the trojanized CCleaner binary file was being distributed using a valid digital signature assigned to Piriform, and should thus be treated as compromised. It urged Avast to revoke the signature.
"The presence of a valid digital signature on the malicious CCleaner binary may be indicative of a larger issue that resulted in portions of the development or signing process being compromised," Cisco Talos says. "Ideally this certificate should be revoked and untrusted moving forward. When generating a new cert, care must be taken to ensure attackers have no foothold within the environment with which to compromise the new certificate."
Cisco Talos says two likely explanations for the insertion of the malicious code are that it was added by an "insider with access to either the development or build environments," or else that an external attacker compromised an insider's account and was able to add the code into a build.

