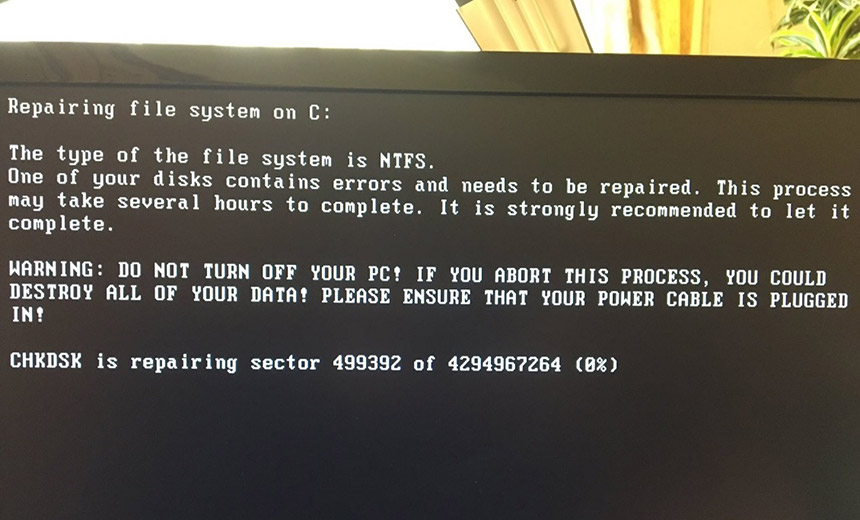
 Screenshot of an affected PC, posted online on June 27 by Ukraine's deputy prime minister.
Screenshot of an affected PC, posted online on June 27 by Ukraine's deputy prime minister.(This story has been updated.)
See Also: How the New World of Digital Banking is Transforming Fraud Detection
A massive, global ransomware outbreak has been hitting airports, banks, shipping firms and other businesses across Ukraine, Russia, the United Kingdom, Denmark, India and beyond.
Organizations ranging from Ukraine's central bank and Kiev's Boryspil Airport to Russian oil producer Rosneft and Danish shipping giant Maersk all appear to have had systems compromised by the attack.
Late Tuesday morning local time, the global pharmaceutical giant Merck confirmed it was hit by hackers, but the New Jersey-based company did not say whether the attack struck its computers in the United States or elsewhere. In Twitter postings, Merck said: "We confirm our company's computer network was compromised today as part of global attack. ... We are investigating the matter and will provide additional information as we learn more."
The Philadelphia Inquirer reported: "The attack was detected at computers in Merck facilities in Pennsylvania and New Jersey around 8 a.m., and the company acknowledged it in a statement a few hours later."
But by late Tuesday afternoon, it was confirmed that Merck wasn't the only health sector company affected in the U.S. by the attacks. Heritage Valley Health System, based in Beaver, Pennsylvania, issued a statement saying it facilities, including two hospitals, were affected by the same ransomware. "Heritage Valley Health System was impacted by a cybersecurity incident the morning of June 27," the statement notes. "This incident has been identified as the same ransomware attack that affected a number of organizations globally."
On Wednesday, Heritage Valley said it was "confident that it has identified the cause and is systematically restoring registration, clinical patient and ancillary care systems. Information technology teams in collaboration with cybersecurity experts continue to mitigate the situation in order to ensure ongoing safe patient care. We are diligently working to determine whether the incident involved any access to confidential information. At this time we have found no evidence that information has been accessed, but our investigation continues."
In addition, the multinational law firm DLA Piper, which has headquarters in the United States and Britain, also said it was attacked. "The firm, like many other reported companies, has experienced issues with some of its systems due to suspected malware," the company said in a statement posted on its website. "We are taking steps to remedy the issue as quickly as possible."
The new attacks follow the WannaCry ransomware outbreak that began spreading globally on May 12. Security experts say the latest attack may also be spreading thanks to it targeting a server messaging block - SMB - flaw in Windows, which has been patched by Microsoft.
Kaspersky Lab researcher Costin Raiu says the attack involves a recently compiled version Petya ransomware, which first emerged in 2016 (see Crypto-Locking Ransomware Attacks Spike). Raiu says the ransomware also has "a fake Microsoft digital signature appended."
The fast-spreading Petya ransomware sample we have was compiled on June 18, 2017 according to its PE timestamp. pic.twitter.com/CHUYvsiQ08
Mikko Hypponen, chief research officer at Finnish anti-virus firm F-Secure, says this version of Petya has been demanding about $300 worth of bitcoins as a ransom payment, in return for victims receiving a decryptor. A handful of victims already appear to have paid.
Or Is Ransomware GoldenEye?
Security experts have been sharing samples of the ransomware and urging anti-virus vendors to immediately add signatures for the malware to their products to help blunt the outbreak.
Here's latest #Petya ransomware sample for those wanting to analyse https://t.co/l3YMl2V6ML
One security firm has suggested that the attacks might trace not to Petya but a similar type of ransomware. Security firm BitDefender believes the ransomware is GoldenEye, and that it encrypts files on a PC as well as NTFS structures. "This approach prevents victims' computers from being booted up in a live OS environment and retreiving stored information or samples," BitDefender security researcher Bogdan Botezatu says in a blog post.
"Just like Petya, GoldenEye encrypts the entire hard disk drive and denies the user access to the computer," he says. "However, unlike Petya, there is no workaround to help victims retrieve the decryption keys from the computer."
EternalBlue Use Suspected
But security firms Avira and Symantec have both confirmed that the ransomware involved in these attacks is Petya. They say that like WannaCry, it is spreading via MS17-010, an SMB version 1 flaw that existed in all versions of Windows since XP and came to light in April, via a dump by the Shadow Brokers of "Equation Group" tools, which many believe to be from the National Security Agency. Microsoft quietly patched the SMB flaw - exploited by an Equation Group tool called "EternalBlue" - in all supported operating systems in March, followed by releasing free, emergency patches for Windows XP, Windows Server 2003 and Windows 8 users late on the same day of the WannaCry outbreak.
Symantec analysts have confirmed #Petya #ransomware, like #WannaCry, is using #EternalBlue exploit to spread
Security experts say the outbreak serves as yet another reminder to ensure that all affected Windows systems have either been patched or otherwise protected against EternalBlue (see Bug-Fixing Imperative: 'Patch, Protect or Pray').
"New Petya uses the NSA EternalBlue exploit," Hypponen says via Twitter. "So Wannacry was not enough of a wake-up call. You would think everybody would be patched by now."
"Old Petya wrapped in EternalBlue is going to hurt," says Alan Woodward, a computer science professor and cybersecurity adviser to the EU law enforcement intelligence agency Europol, via Twitter.
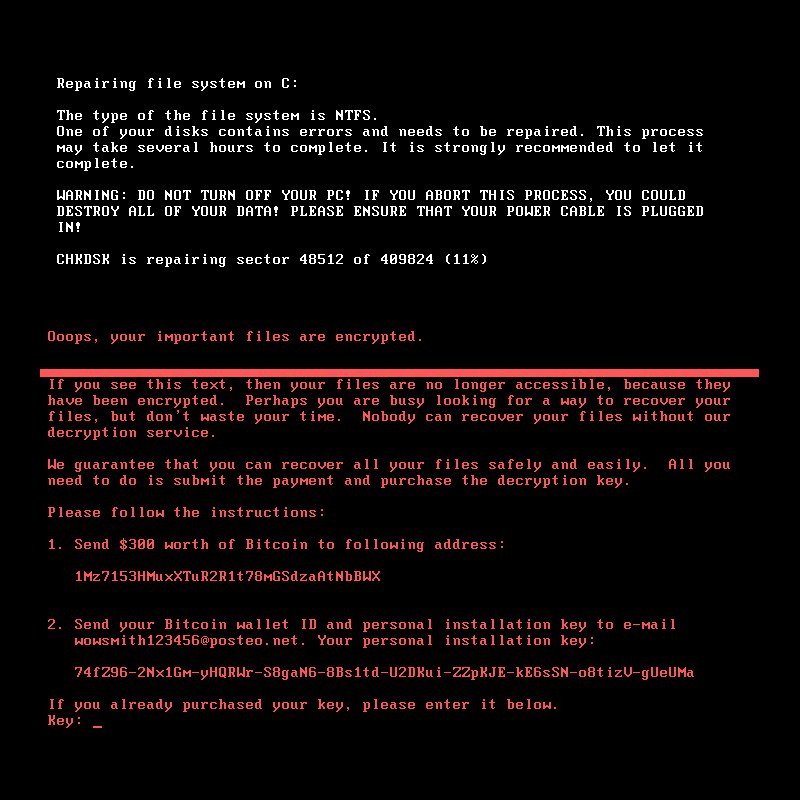 Ransom note attached to Petya ransomware outbreak. (Source: Avira)
Ransom note attached to Petya ransomware outbreak. (Source: Avira)Ukraine Hit Hard
Initial reports suggest organizations in Ukraine may have been hardest hit.
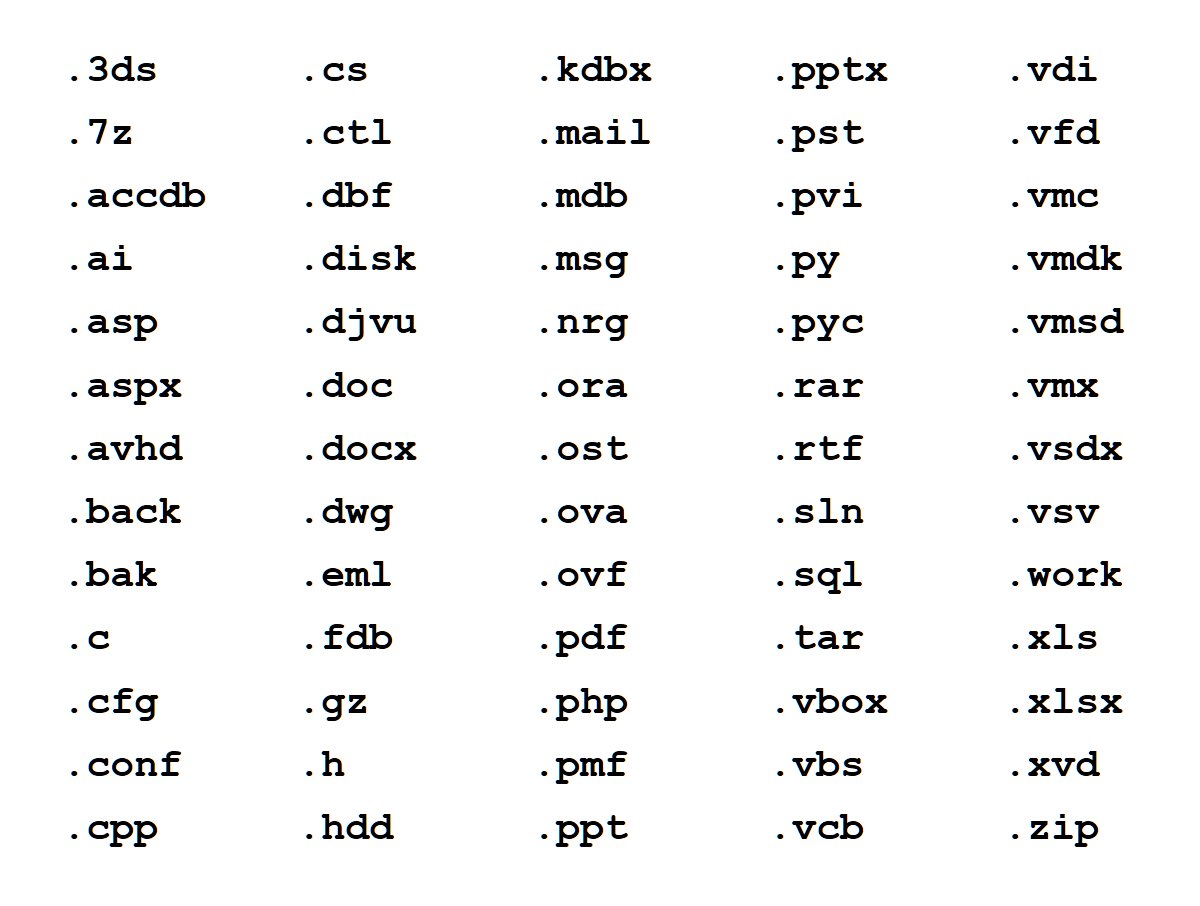 File types encrypted by the Petya variant. (Source: F-Secure)
File types encrypted by the Petya variant. (Source: F-Secure)Ukraine's central bank, as well as numerous banks and businesses, including the state postal system and telecommunications agency, as well as at least one power distributor, apparently have been affected. Kiev's Boryspil Airport also warned that flight delays were possible.
"As a result of these cyberattacks, these banks are having difficulties with client services and carrying out banking operations," according to a statement issued by Ukraine's central bank, which blamed the outages on an "unknown virus."
Ukrainian Deputy Prime Minister Pavlo Rozenko reported that at least some government computer systems had been compromised by the ransomware. On Twitter, he posted a picture of a compromised government system. Security experts say the image showed the ransomware actively crypto-locking the contents of the PC.
Vice Prime Minister of Ukraine, Павло Розенко (Pavlo Rozenko) on Facebook. This is what Petya looks like when it's encrypting your drive. pic.twitter.com/RgPtfuWK7p
Ukraine's security council secretary, Oleksandr Turchynov, speaking just after news of the attacks broke, suggested that they may have been launched from Russia. "Already on first analysis of the virus, it is possible to talk of Russian fingerprints," Ukraine's National Security and Defense Council quoted Turchynov as saying, the New York Times reports.
Attacks Appear to Be Connected
Some security experts say multiple reports of new cyberattacks all appear to involve the same ransomware.
Russia's Rosnoft - one of the world's biggest crude oil producers, by volume - also disclosed via Twitter that it has been hit by "a powerful hacker attack" that has affected some of the company's servers. "We hope that this has nothing to do with the current judicial procedures," the statement added, in reference to a court case the producer is fighting against the Sistema conglomerate.
But Rosnoft says its production systems have not been affected by the attack. "A hacker attack could have serious consequences, but thanks to the fact that the company switched to a standby system for managing production processes, neither the production nor the preparation of oil was stopped," the company tells the Financial Times.
Copenhagen-based shipping group A.P. Moller-Maersk first confirmed attacks Tuesday afternoon, European time. It says business units in multiple regions, including Britain and Ireland, had been affected.
We can confirm that Maersk IT systems are down across multiple sites and business units. We are currently assessing the situation.
Moscow-based cybersecurity firm Group-IB tells Reuters that one of Maersk's logistics firms, Russia-based Damco, was also affected by the attack.
Attacks Continuing
Meanwhile, the attacks are continuing. "It is too early to tell what we are dealing with right now - is this another wave of WannaCry? A new variant? The same actors or - as we predicted some time ago - a new adversary taking the lessons that WannaCry provided and running with them?" asks Galina Antova, co-founder and chief business development officer at cybersecurity firm Claroty.
"We will know more in hours and days - but what should be very clear at this point in time is the fact that the threat landscape has evolved rapidly ... over the past few years - and that evolution seems to be speeding up in 2017," she says.
Current situation of Petrwrap/wowsmith123456 ransomware - percentage of infections by country. pic.twitter.com/Q42WPlBlja
The U.S. Department of Health and Human Services sent out several alerts on Tuesday and Wednesday with links to ransomware resources similar to those the federal government promoted during the recent Wannacry attacks, including recommendations to contact the FBI if organizations become victims to ransomware assaults.
Included in the HHS alerts was also new advice to contact the Food and Drug administration's emergency line to report if a facility "experiences a suspected cyberattack affecting medical devices." During the Wannacry attacks, at least two unidentified U.S. hospitals reported that their imaging systems from Bayer AG had been infected (see HHS Ramps Up Cyber Threat Information Sharing).
(Executive Editors Eric Chabrow and Marianne Kolbasuk McGee contributed to this story.)

