Data Breach , Fraud , Payments Fraud
5 Business Secrets of Cybercrime Masterminds How 'Vendetta Network' Maximizes Profit, Minimizes Risk Vendetta Network advertises for freelancers who want to install malware on POS terminals.
Vendetta Network advertises for freelancers who want to install malware on POS terminals.Want to create a cybercrime empire built on selling stolen payment card data? Prioritize your use of outsourcing, partnerships and best-of-breed tools to maximize profits while minimizing risk.
See Also: Managing Identity, Security and Device Compliance in an IT World
At least that's the strategy being employed by the administrators behind a cybercrime forum called Vendetta Network, which is profiled in a new report from cybersecurity firm FireEye.
"We're seeing their group at least use some tactics from legitimate business or even organized crime - if you want to look it that way - in terms of using proxies, outsourcing some of the tedious work, and even purchasing leads through other sources to scale their operation and defend themselves from investigation," FireEye threat analyst Will Glass tells me.
For example, the forum often relies on freelance operators to help it infect point-of-sale systems with malware, which it then uses to harvest payment card data.
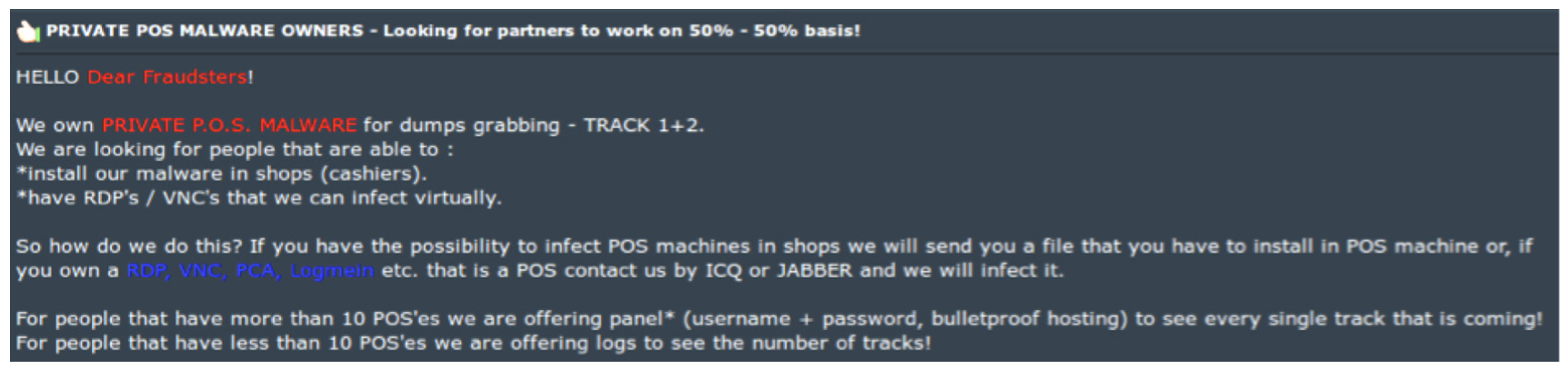 Vendetta World's advertisement for freelance POS malware installation talent. (Source: FireEye)
Vendetta World's advertisement for freelance POS malware installation talent. (Source: FireEye)Here's the recruitment pitch, Glass says: "If you have access to point-of-sale terminals and you're feeling like you want to make a little extra money we can give you the malware that you need to install and then we'll share some of the profits with you." Or, Glass tells me, "they'll say, 'if you have a spam service ... we'll give you the malware that you can spam people with.' So they never actually seem to do the compromising themselves, at least as far as I can tell; they tend to try and outsource it."
Glass declined to detail exactly how FireEye managed to access Vendetta Network operations, nor which ones it accessed. But the report makes clear that the firm accessed at least some of the forum's online operations, including customer support chat logs.
FireEye's Will Glass details innovative techniques used by the "Vendetta Brothers" to build and run their business.
5 Cybercrime Secrets, No MBA Required
FireEye's report offers a picture of how the forum's two administrators - "1nsider" and "p0s3id0n," who it dubs the "Vendetta Brothers" - run their operations on a day-to-day basis. Glass says the administrators appear to be based in Eastern Europe and Spain.
Here are five of the group's more notable business tactics:
Contractors: Vendetta Network appears to "outsource the grunt work" of installing POS malware to freelance operators, Glass says. This approach sets up the malware installers to act as fall guys if investigators come calling. Partnerships: The group also partners with some criminals who already have access to POS systems, sometimes paying spam services to send phishing emails to victims and also offers skimming services, involving physically tampering with POS devices and capturing PIN codes via video recording. Specialization: Obtaining POS data via others provides not just separation and safety, but also allows the administrators to "to spend their time doing the higher-level 'brainiac' brains of the operation thinking," including identifying new targets, building a robust technical infrastructure and handling HR-related issues, Glass says. Best-of-breed tools: The POS malware recently used by Vendetta World appears to be a lightly modified copy of the Dexter malware. From a crime perspective, using off-the-shelf POS malware makes sense, as security experts say POS malware is commoditized and functionally nearly all the same - so why build your own? Customer service: The group understands that maximizing profits requires keeping customers happy with the quality of your product and maintaining a good reputation.Budding Business
As cybercrime empires go, however, Vendetta Network appears to be a relatively small concern.
Earlier this year, the shop was selling data relating to about 10,000 stolen payment cards issued by banks in the United States and the Nordic region - Denmark, Finland, Iceland, Norway and Sweden, Glass says.
Compare that to competing carder marketplace Rescator, which once listed for sale a single batch of data - labeled "Desert Strike" - that it claimed contained information on 282,000 payment cards, which many security experts believed had been stolen from Sally Beauty.
The 'Lamer' is Always Right?
The Vendetta Network report offers a useful window into a cybercrime operation, demonstrating that running an illicit business predicated on harvesting POS data isn't all fun and games.
For example, as anyone who's ever run a business knows, retaining your customers is much cheaper than trying to find new ones. But at least for this carder forum, customer satisfaction is an ongoing bugbear.
One episode documented in FireEye's report - included "to humanize the perpetrators a little bit," Glass says - involves Vendetta Brothers customer "Liban" threatening to leak data to information security journalist Brian Krebs unless his concerns over payment data quality get resolved. "I swear to god," Liban promises. "Bye now."
"Bye," replies admin p0s3id0n, adding: "Lamer."
No word on whether Liban became one of the carder forum's repeat customers.

