DDoS , Forensics , Technology
Separately, Lauri Love Allowed to Fight US Extradition Request Adam Mudd pleaded guilty to running an on-demand DDoS service tied to over 1.7 million attacks (Photo: Bedfordshire police)
Adam Mudd pleaded guilty to running an on-demand DDoS service tied to over 1.7 million attacks (Photo: Bedfordshire police)A British man has received a two-year prison sentence at London's Old Bailey courthouse after he pleaded guilty to developing and selling "Titanium Stresser," a distributed denial-of-service attack tool that was tied to strikes against organizations such as Microsoft and Sony.
See Also: Balancing Fraud Detection & the Consumer Banking Experience
Adam Mudd, now 20, of Hertfordshire, England, admitted to creating Titanium Stresser in 2013, when he was just 16 years old. Police say the service has been tied to more than 1.7 million DDoS attacks worldwide, and generated an estimated £300,000 ($385,000), part of it in bitcoins, for Mudd (see DDoS Stresser/Booter Services Feel the Heat).
Sites disrupted by Titanium Stresser included Minecraft, Microsoft, Xbox Live and TeamSpeak, a VoIP chat tool used by gamers.
Mudd was arrested at his home in March 2015, and a number of computing devices were confiscated by police.
In October 2016, Mudd had pleaded guilty to three offenses under the Computer Misuse Act as well as one offense of money laundering under the Proceeds of Crime Act. Police say he also admitted to attacking West Herts College, where he was a student.
On April 25, he was sentenced to 24 months imprisonment for having launched his own DDoS attacks, nine months for running the Titanium Stresser DDoS-as-a-service offering, and 24 months for money laundering the proceeds made from the stressor service, with all sentences set to run concurrently.
Mudd's attorney, Ben Cooper, had requested a suspended sentence, reportedly telling the court that his client had been "'lost in an alternate reality' after withdrawing from school because of bullying." The court also heard how Mudd had been diagnosed with Asperger syndrome.
But Judge Michael Topolski instead imposed a prison sentence, saying it would serve as a "real element of deterrent," the Guardian reports. "I'm entirely satisfied that you knew full well and understood completely this was not a game for fun," the judge reportedly told Mudd. "It was a serious money-making business and your software was doing exactly what you created it to do."
Topolski also noted that Mudd came from a "perfectly respectable and caring family," and noted that attacks launched with his tool had caused damage "from Greenland to New Zealand, from Russia to Chile."
Prosecutor Jonathan Polnay reportedly told the court that Mudd was motivated by a desire to cultivate status with members of the gaming community. He also said Titanium Stresser had counted more than 112,000 registered users, who used it to target 666,000 IP addresses in total, including 53,000 in the United Kingdom.
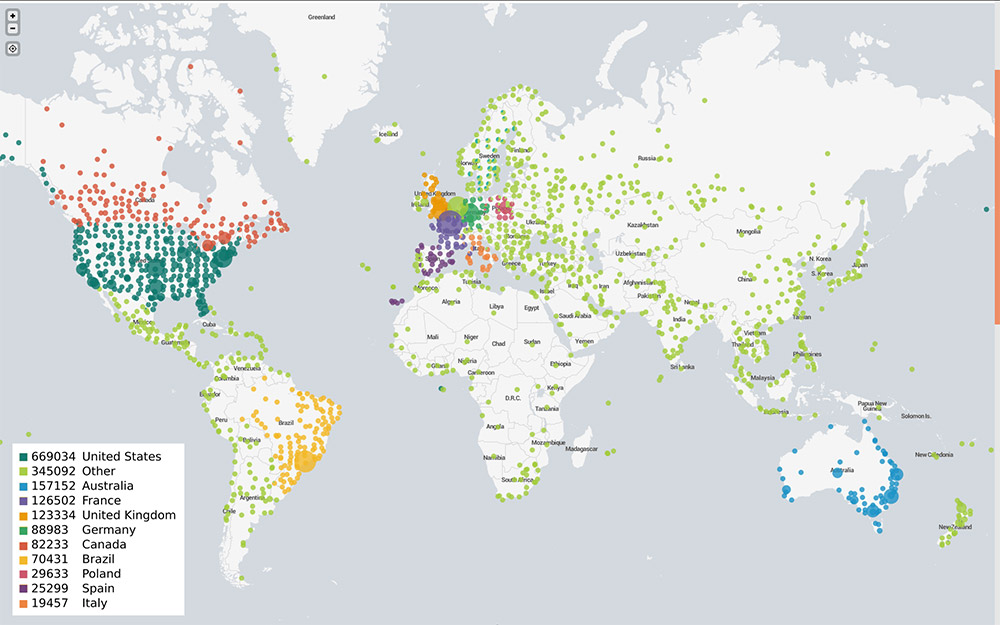 Heat map of attacks tied to Titanium Stresser. (Source: ERSOU)
Heat map of attacks tied to Titanium Stresser. (Source: ERSOU)Operation Polarity
Mudd's case was investigated by England's Eastern Region Special Operations Unit - ERSOU - regional cybercrime unit, working with the U.K.'s National Crime Agency, as part of what was dubbed Operation Polarity.
Police said the case was complex, involving advanced digital forensics work that ultimately led to investigators receiving a commendation from the National Police Chiefs Council.
"It is important that this case sends out a clear message to others who may be tempted by committing cybercrime or who are already engaging in cyber scams from the comfort of their own bedrooms, to consider what they are doing and it is for parents to know and understand what your children are doing online," Detective Chief Inspector Martin Peters of ERSOU's regional cybercrime unit says in a statement.
"Criminality is now no longer solely on the streets and harm can be caused to individuals and globally, but that does not mean we cannot trace you and bring you to justice if you over step the line. We will work with law enforcement agencies, locally, regionally, nationally and globally to combat this criminality," he added.
Pathways to Cybercrime
A report released last week by the National Crime Agency, looking at pathways to cybercrime, says that many teenage cybercrime offenders don't appear to be motivated by money.
Rather the report, which has been backed by some former hackers, says cybercriminals often come to hacking via online gaming communities.
"Completing the challenge, sense of accomplishment, proving oneself to peers is a key motivation for those involved in cybercriminality," the report says.
Richard Jones, head of the NCA's cybercrime prevention team, says more work is needed to warn potential young offenders and direct them into legitimate activities. "That can be as simple as highlighting opportunities in coding and programming, or jobs in the gaming and cyber industries, which still give them the sense of accomplishment and respect they are seeking."
Lauri Love Can Contest Extradition
Mudd's sentence was handed down the same day that Britain's high court ruled that another British man, Lauri Love, 32, could appeal its decision to allow him to be extradited to the United States to face hacking charges (see Brits Arrest Alleged Fed Reserve Hacker).
Love has been charged with 2012 and 2013 hack attacks against U.S. government computers, including systems operated by the Federal Reserve, U.S. Army and NASA. He faces a maximum prison sentence of 99 years.
Love, who has been diagnosed with Asperger syndrome and severe depression, hailed the High Court ruling.
"Every day you wake up to some good news is a blessing, and we can't take any blessings for granted these days," he says in a statement. "I'm thankful the High Court have recognized the strength of our grounds for appeal and the great importance of the issues raised by the case."
Last year, a cross-party group of 114 members of Parliament wrote to President Obama, requesting that he quash the U.S. request for Love's extradition.




 Sixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.
Sixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.


