Endpoint Security , Technology
Warning: Microsoft Fix Freezes Some PCs With AMD Chips Meltdown and Spectre Security Update Bricks Some PCs With Athlon CPUs(euroinfosec) • January 8, 2018 The view for users of some Windows PCs based on AMD chips after Microsoft's emergency Meltdown and Spectre security update gets installed.
The view for users of some Windows PCs based on AMD chips after Microsoft's emergency Meltdown and Spectre security update gets installed.Organizations are scrambling to put in place fixes for the Meltdown and Spectre flaws as makers of operating systems, cloud services, mobile devices and more start to release patches (see Meltdown and Spectre: Patches and Workarounds Appear).
See Also: IoT is Happening Now: Are You Prepared?
But not all of the fixes are working as advertised.
Meltdown and Spectre are flaws in many microprocessors that attackers could use to steal kernel data, including passwords and encryption keys. Security experts say all organizations should put mitigations in place as soon as possible, preferably starting with browsers, because attackers could use malicious websites to try and exploit the flaws.
Numerous operating systems require updates as well, including Apple Mac OS X and iOS devices, Google's Android and Microsoft Windows. Microsoft's Windows fix for the flaws arrived Wednesday in a KB4056892 security update for Windows 10.
Some Windows users running devices with CPUs built by AMD, however, report that Microsoft's fix has been freezing their systems.
In a lengthy discussion thread on Microsoft's site, users running systems with AMD's Athlon chips report that after installing KB4056892, their machines fail to fully boot. Some are able to restore systems using a previous restore point. Even if that is successful, however, the operating system quickly attempts to reinstall the PC-freezing patch, they say.
"Woke up this morning to this particular laptop setting on desk with black screen and Microsoft logo and no animation. Nothing going on," a user with the handle "Frustrated after KB4056892 on older AMD laptop" posted to the discussion thread on Sunday, adding that the system is running a version of McAfee anti-virus that is compatible with Microsoft's security fix. "After 3 rollbacks, found this tread so I don't feel totally stupid for having wasted most of my Sunday trying to 'fix' this now known to be un-fixable problem."
Not all AMD chips appear to be incompatible with the Windows security update. The "frustrated" user, for example, reports that beyond that laptop, one desktop with a different AMD chip and three laptops with Intel chips have successfully updated.
Microsoft did not immediately respond to a request for comment.
Not Tied to Anti-Virus Software
Microsoft has warned that its fix requires all anti-virus vendors to update their software to set a new Windows registry key, or else its security update won't work. In fact, Microsoft says in a Sunday alert that neither KB4056892 nor any future security updates will be installed so long as a device is running incompatible anti-virus software. "Customers will not receive the January 2018 security updates (or any subsequent security updates) and will not be protected from security vulnerabilities unless their anti-virus software vendor sets the [required] registry key," Microsoft says.
But that registry requirement doesn't appear to be causing the problem with AMD processors, as some users report that they have compatible anti-virus software running. Others say their systems have frozen even though they're running only Windows Defender, which is anti-virus software installed by default in Windows if no other anti-virus software has been installed.
Temporary Fixes
As a temporary fix for affected AMD systems, some users report that they have been able to install a show or hide updates troubleshooter patch from Microsoft that they have used to block KB4056892 from installing.
Another potential fix is to activate metered connections in Windows 10 which can prevent the update from installing.
For anyone whose machine has not yet attempted to install the update, other users say another option is to immediately disconnect the system from the internet, then pause Windows updates for 35 days - available in "Advanced Options" via "Windows Update Settings" - before reconnecting to the internet.
Hopefully, within 35 days, Microsoft will have cooked up a fix for this problem.
What's the Risk?
So far, researchers have identified three attacks that can be used to exploit Meltdown and Spectre:
Variant 1: "bounds check bypass" (CVE-2017-5753), Spectre attack; Variant 2: "branch target injection" (CVE-2017-5715), Spectre attack; Variant 3: "rogue data cache load" (CVE-2017-5754), Meltdown attack.Security experts say it's not clear how frequently real-world attackers might attempt to exploit these flaws. No real-world attacks have yet been seen.
Cue this patch problem irony: Overall, AMD chips appear to be less at risk from Spectre and Meltdown attacks than Intel chips.
AMD: Spectre/Meltdown Variants
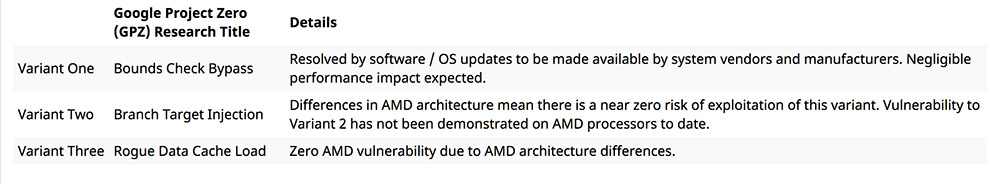 Source: AMD
Source: AMDIntel chips are vulnerable to all three flaws. But anyone using a device with an AMD microprocessor is immune to variants two and three, AMD says. It also notes that they are only at risk from variant one until they have installed operating system and software updates.

