
Want a new job that features flexible hours and rewards your knowledge of technology and security? Want to impress your friends with a job title such as social engineer, freelance hacker, bot herder, DDoS specialist or carder? Don't mind the prospect of incarceration?
See Also: Cyber Insurance and Cyber Security
A career in cybercrime may be right for you.
All joking aside, a thriving market now exists to help cybercriminals promote themselves - or what they've stolen - as well as recruit new talent, Rick Holland, vice president of strategy for threat intelligence firm Digital Shadows, tells me. His firm has been studying how cybercriminals advertise for new recruits - and the types of technology skills that are most in demand (see How Do We Catch Cybercrime Kingpins?). The company released research this week at the RSA 2016 Conference in San Francisco.
On the recruitment front, what Digital Shadows found bears a startling resemblance to noncriminal hiring and firing practices - online job applications, Skype interviews and having to demonstrate one's hacking skills via sample assignments before would-be employers give job seekers the green light. Many new jobs also include a probationary period, with one noting that if a designated group of sites hadn't been hacked within three months, the employee's contract would not be renewed.
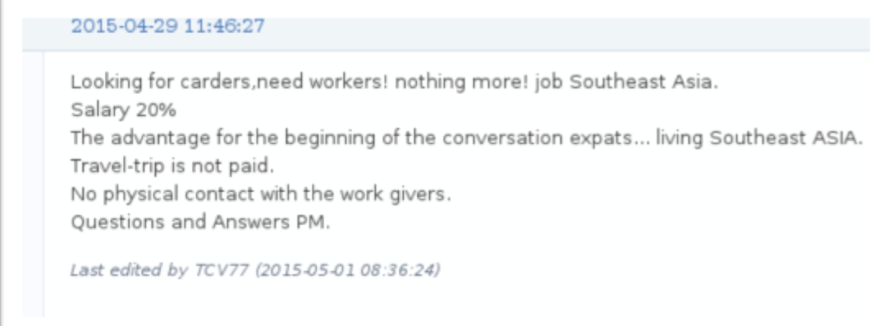 Carding forum post seeks new recruits. (Source: Digital Shadows)
Carding forum post seeks new recruits. (Source: Digital Shadows)In return, however, budding cybercriminals can benefit from flexible working arrangements, avoid having to deal with some nitty-gritty aspects of the fraud ecosystem, such as using money mules to convert stolen payment card details into cash, and can earn more if they hack more.
Just like in the information security realm, furthermore, available talent appears to be in short supply. "Adversaries, too, are struggling to find the right talent, which is critical to their profits," Holland says. Coding skills, perhaps predictably, are always in demand. In 2014, for example, a group calling itself Deletesec said knowing Perl and Python were must-have for new recruits, while "C/C#/C++, PHP, Ruby, and ASM [assembly]" languages were useful but not essential.
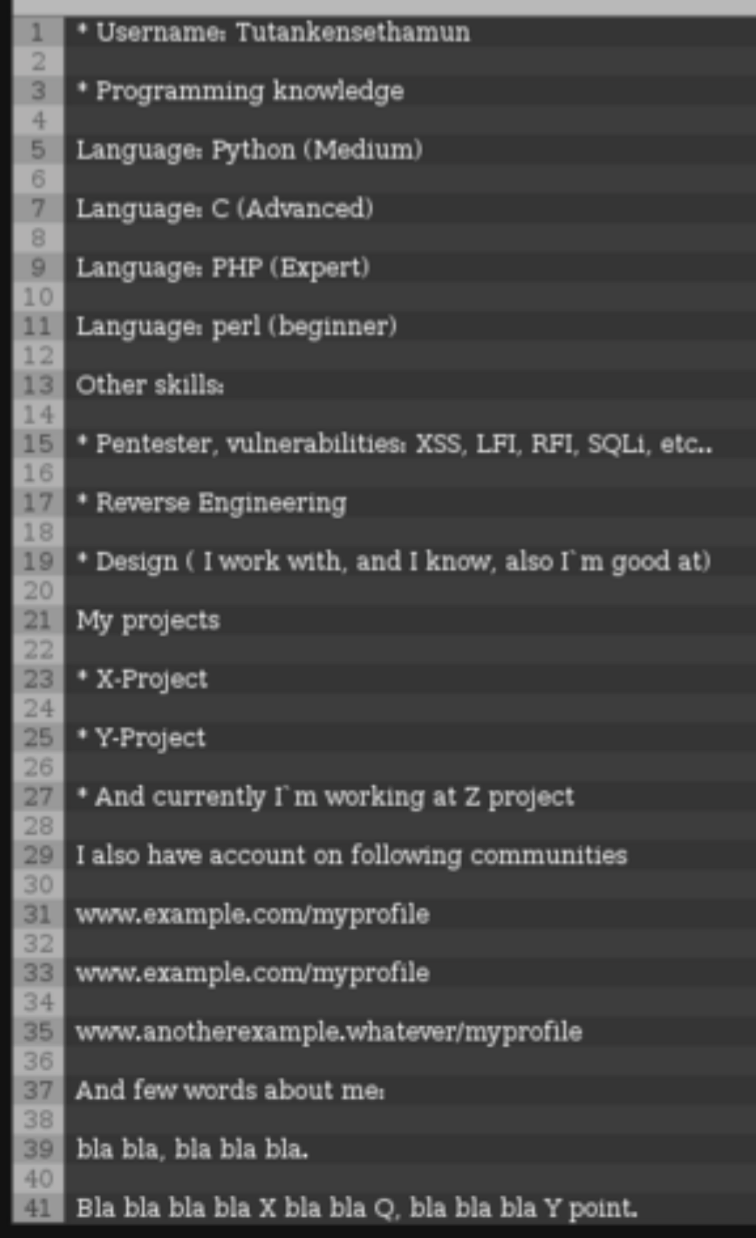 Job application form posted to a Dark Web forum. (Source: Digital Shadows)
Job application form posted to a Dark Web forum. (Source: Digital Shadows)The job listing continues: "You must speak English fluently: Bad grammar can be tolerated to a certain extent. You must be a knowledge seeker: You're motivated and thrilled to learn new programming languages, attack vectors and everything else."
But based on his review of advertisements for hacking talent, what's even more valuable than programming skills, Holland says, are native language skills for whichever regions the employer wants to target. "You also see where they're looking for people who are ex-pats, living in this particular region that have these language skills, native speakers, things along those lines, so that they can run these campaigns," he says.
Seeking: Exploit Artists
Holland says organizations that are likely to be on the receiving end of these types of hack attacks can also learn from the types of vulnerabilities that new recruits need to target. The Deletesec advertisements, for example, says would-be hires "must know how to execute these vulnerabilities: SQLI [SQL injection], Blind SQLI [blind SQL injection], XSS [cross-site scripting], CSRF [cross-site request forgery], Directory Traversal, LFI [local file inclusion], RFI [remote file inclusion], CRLF [carriage return and line feed injection], XPATH [XML document] injection and full path disclosure."
Rick Holland of Digital Shadows discusses why hackers prefer easy exploits.
In fact, Holland says, many would-be cybercrime employers likewise aren't necessarily seeking genius-level hackers with rarefied skill sets who can craft "esoteric exploits." Rather, they're sticking with tried-and-true attack techniques, such as SQL injection vulnerabilities and cross-site scripting flaws, that deliver maximum return for a minimum investment of time or drama.
Fighting Hackers
As a result, Holland stresses that potential victims can take action to fix flaws before hackers take advantage of them (see How Yahoo Hacks Itself).
For example, companies can use code reviews and penetration testing to catalog related vulnerabilities and get them fixed before hackers come calling. Or they can delay, and help keep hackers from going hungry.

