- Details
- Category: Security News
 President-Elect Donald Trump
President-Elect Donald TrumpPresident-elect Donald Trump will review the nation's cyber vulnerabilities at the start of his presidency, just like Barrack Obama did. But Trump hasn't demonstrated the deep understanding of cyber that Obama did when he took office nearly eight years ago.
See Also: Forensic Files: Inside a Mock Breach Investigation
Trump didn't spend much time speaking about cybersecurity on the campaign trail - neither did Hillary Clinton. But his most coherent remarks came in a September speech on national security delivered in Philadelphia, in which he read off a teleprompter his plans to defend U.S. digital assets. In that speech, Trump said that upon assuming office, he would order an immediate review of all U.S. cyber defenses and vulnerabilities, including critical infrastructure, by a cyber review team of individuals from the military, law enforcement and the private sector.
That's reminiscent of when Obama initiated a wide-ranging cybersecurity review weeks after taking office in 2009. That review, led by senior White House cybersecurity adviser Melissa Hathaway, produced a 10-point cybersecurity action plan unveiled by President Obama in May 2009 (see The President's 10-Point Cybersecurity Action Plan).
In an October speech to a veterans' group, Trump provided more details on his plan, including having his cyber review team provide specific recommendations for safeguarding different entities with the best defense technologies tailored to the likely threats (see Donald Trump Unveils His Cybersecurity Platform). He said the team would establish detailed protocols and mandatory cyber awareness training for all government employees while remaining current on evolving methods of cyberattack.
Cybersecurity Platform
According to his cybersecurity platform posted on his campaign website, the president-elect proposed:
Instructing the Justice Department to create joint task forces throughout the U.S. to coordinate federal, state and local law enforcement responses to cyberthreats; Ordering the defense secretary and chairman of the Joint Chiefs of Staff to provide recommendations for enhancing U.S. Cyber Command, with a focus on offense and defense in the cyber domain; and Developing the offensive cyber capabilities needed to deter attacks by both state and non-state actors and, if necessary, to respond appropriately.Nation-State Threats
In the October speech, Trump acknowledged the threats posed by foreign governments, "especially China, Russia, North Korea along with non-state terrorist actors." Including Russia proved interesting. During the campaign, he praised Russian President Vladimir Putin as a strong leader, and when U.S. intelligence services blamed Russia for attacking Democratic Party information systems, Trump refused to accept those appraisals.
A week earlier, in a debate with Clinton in which she blamed Russia for the hacks, Trump responded: "She's saying Russia, Russia, Russia. Maybe it was. It could also be China, it could be someone sitting on their bed that weighs 400 pounds."
Trump has said to "truly make America safe, we must make cybersecurity a major priority, which I don't believe we're doing right now, for both government and the private sector."
Trump is wrong on that point. Obama since the beginning of his administration has made cybersecurity a priority, and the president has worked with Congress - including Republicans - and business leaders to strengthen cyber protections for the government and the private sector. Despite those efforts, cyberattacks have plagued the government and private sector. But those attacks don't mean cybersecurity isn't a priority for Obama. Cybersecurity, as we know, is hard.
Rambling Thoughts
There's little doubt that Trump is aware of the dangers in cyberspace, and it's reassuring he says cybersecurity will be a priority. But it's not clear whether he really understands the cyber threat. In impromptu remarks in September, Trump rambled on about cybersecurity (see Does Donald Trump Understand Cybersecurity?):
"Cyber is becoming so big today, it's becoming something that a number of years ago, a short number of years ago, wasn't even a word. Now the cyber is so big. You know you look at what they're doing with the internet, how they're taking, recruiting people through the internet. And part of it is the psychology because so many people think they're winning. And you know there's a whole big thing. Even today's psychology, where CNN came out with a big poll, their big poll came out today that Trump is winning. lt's good psychology."
- Details
- Category: Security News
Breach Response , Cybersecurity , Data Breach
UK's New Cybersecurity Strategy - No Strike-Back Required Britain's New Strategy and Policing Moves Promise Much More Chancellor Philip Hammond (pictured delivering a speech in 2014) says Britain must have the ability to strike back against hackers. (Photo: Patrick Tsui, Flickr/CC)
Chancellor Philip Hammond (pictured delivering a speech in 2014) says Britain must have the ability to strike back against hackers. (Photo: Patrick Tsui, Flickr/CC)U.K. Chancellor Philip Hammond used the launch of Britain's new five-year National Cyber Security Strategy to trumpet the country's strike-back capabilities. But other parts of the strategy - including more automated defenses - hold much greater promise.
See Also: Protect Your Identity Infrastructure
In a speech delivered last week in London, Hammond, who as Chancellor of the Exchequer is Britain's chief financial minister, promised that the U.K. "will strike back in kind" to cybersecurity attacks.
"We will not only defend ourselves in cyberspace; we will strike back in kind when we are attacked," he said.
The concept of striking back, however, presumes accurate attribution - namely, that you can tell how an attack was launched and who was behind the keyboard. It also presumes striking back is always the best option, compared to diplomatic moves, sanctions or looking the other way.
In short, Hammond's bluster suggests a lack of knowledge about how to better combat and police online attacks and cybercrime, which is worrisome from the person who was using his speech to announce the launch of Britain's new five-year National Cyber Security Strategy.
Hammond promises the program will be underpinned by £1.9 billion ($2.4 billion) of "transformational investment." It's also tied to GCHQ's newly launched National Cyber Security Center, which has absorbed Britain's computer emergency response team CERT-UK and the cyber-related responsibilities of the country's Center for the Protection of National Infrastructure.
As an example of what the program can deliver, Hammond said it will be focused, in part, on rolling out "a more active cyber defense approach - supporting industry's use of automated defense techniques to block, disrupt and neutralize malicious activity before it reaches the user."
NCSC's 'Threat-o-Matic'
Despite a reference in government documentation to various automated defenses feeding into a "threat-o-matic," University of Surrey computer science professor and Europol adviser Alan Woodward notes that the related program is "definitely not a joke."
UK's "active defence" strategy in a nutshell - from @ncsc pic.twitter.com/bhmZSjIoc3
Indeed, in a blog post, Ian Levy, technical director of GCHQ's National Cyber Security Center, says automation is key to blocking more attacks. "It's not a panacea but should help us mitigate the impact of a significant proportion of the attacks we see," he says. "It won't affect the really targeted attacks (at least initially) but we're hoping that we can reduce the noise enough to make the defenders' jobs easier when tackling those very targeted attacks."
Dropping DDoS Traffic
As an example, Levy says GCHQ wants to work with ISPs to block traffic associated with distributed denial-of-service attacks as well as text-message scams, for starters.
"We think we can get to a point where we can say a U.K. machine can't participate in a DDoS attack," Levy told Britain's Sunday Telegraph. "We think that we can fix the underpinning infrastructure of the internet through implementation changes with ISPs and CSPs [communications service providers]."
What would be required, he said, includes changes to the Border Gateway Protocol and Signaling System 7 to better block attackers from inappropriately rerouting traffic.
"I suspect this is about 'getting the house in order' before pushing [international] ISPs to do the same, which would be a big win," says Matt Tait, CEO of U.K. security consultancy Capital Alpha Security. Tait formerly served as an information security specialist for GCHQ and Google Project Zero, among other roles, and tweets as "Pwn All the Things."
I suspect this is about "getting the house in order" before pushing intl ISPs to do the same, which would be a big win.
These are constructive discussions. But the problems associated with BGP and SS7 are well known. What's not clear is whether all ISPs internationally can be brought together to put costly fixes in place.
"A large amount of hardware will need upgrading to make sure whatever changes are made are propagated throughout the world," James Blessing, chair of the Internet Service Providers Association, an ISP trade body, told the Sunday Telegraph. "Government is more than welcome to fund the efforts, like the National Security Agency does in the U.S."
The Strike-Back Follies
Still, such broadly focused moves could pay huge cybersecurity dividends. They're far superior to any strike-back threats or vows to get tough on cybercrime. As the satirical Twitter account Sir Bonar Neville-K notes, such threats have failed to blunt cybercrime, including crimes committed by individuals who are, legally speaking, children.
Indeed. The serried ranks of spotty teenagers will rue the day they sought to tweak the whiskers of Her Majesty's Government. https://t.co/gZqg6K40SX
Her Majesty Needs Hackers
While many cybercrime operations are run from non-EU countries, there are still numerous examples of hack attacks against U.K. targets being traced to U.K.-based suspects, including the attack against London-based telecommunications provider TalkTalk.
To better battle domestic cybercrime, the head of the U.K.'s national cybercrime unit at the National Crime Agency will reportedly ask the government to create a "Cyber Prevent" program designed to keep children from experimenting with hacking or other types of computer crime, the Guardian reports. The program would reportedly be modeled on the U.K. government's controversial "Prevent" program, which is designed to counter radicalization.
"A lot of kids are stumbling into this crime," Saunders told the Guardian, adding that the program would target individuals aged 12 to 25. "This activity has consequences for them and others. There are legitimate opportunities for their skills."
- Details
- Category: Security News
Breach Notification , Data Breach
Cylance's Voting Machine Hack Based on 2007 Research A Media Stunt Before the Election? Cylance Says No Pictured: Sequoia AVC Edge Mk1
Pictured: Sequoia AVC Edge Mk1Late last Friday, security upstart Cylance published a blog post and news release that unsurprisingly has since triggered a handful of news stories: An aging voting machine still used in more than a dozen U.S. states is vulnerable to tampering.
See Also: Main Cyber Attack Destinations in 2016
Titled "Cylance disclosed voting machine vulnerability," the short post contained a video showing how a ballot could be manipulated on a Sequoia AVC Edge Mk1, a machine first produced in 1990 that will be used in some states in today's presidential election.
The hack involved removing a PCMCIA card, reflashing the firmware to muddle the candidates and vote tallies and reinserting the card. In a presidential campaign where hacking has played an unprecedented role, the finding is sure to stoke more anxiety (see Clinton, Trump: Head-to-Head Over Purported Russian Hacks).
But the security problems highlighted by Cylance were first outlined in a July 2007 paper by university researchers. It doesn't appear Cylance furthered those findings except to show that the researchers work was accurate, which wasn't in doubt.
Publicity Stunt?
Cylance acknowledges the research paper in its blog post, writing that its work instead marks the first public demonstration of those vulnerabilities. The company's media blitz has raised questions as to whether the demo is beneficial right before an election that Republican candidate Donald Trump has already suggested may be corrupted.
"Obviously it's a concern that it's so close timing wise," says Pamela Smith, president of Verified Voting, a nonprofit organization that studies electronic and e-voting. "I think it's good there's been conversation about security, but it's a delicate balance. Nobody wants voters to think 'What's the point? It's all going to be hacked anyway'."
Greg Singh, director of sales engineering at Cylance who's based in Sydney, denied that the company was making a well-timed play for publicity.
"I really don't think that's the case at all," Singh says. "It's a point of interest to a number of parties in the normal realm of media and reporting. Be it presidential election time or not, Cylance would have released this type of finding, as we have with other devices and types of exploits that we've discovered in the past. It certainly wasn't done as a publicity stunt."
Weak Security Controls
Cylance's experiment largely relies on vulnerabilities described on page 31 of the research paper. The AVC Edge's PCMCIA card holds ballot information, such as candidate names. The researchers found the cryptographic and other security measures meant to protect that data from tampering were ineffective.
"Malicious Edge firmware can be configured to record and report incorrect vote data on the Results Cartridge and on the internal Audit Trail," the paper reads.
So that's what Cylance did: It inserted fake candidate names, showing in a mock 2008 election how a John Smith could lead the presidential tally with Barack Obama erased from the ballot. It tampered with both the protected and public vote counters, with the machine regurgitating a paper receipt that verified the bogus results.
There are obvious problems with the AVC Edge that date from the era in which it was made, but there are a couple of defenses: using tamper-resistant seals over the PCMCIA card and educating polling officials to keep unauthorized people away from the machines. There's also another hurdle for an attacker: To successfully modify votes, the machine has to be rebooted after the reprogrammed card is inserted.
No Paper Trail
Verified Vote has a page dedicated to the security problems around the AVC Edge. It is known as a direct recording electronic voting system, and as originally configured had no paper record to consult. A touch-sensitive screen transmits voter selections through software to memory, which is the sole record of voter entries. Such systems often have closed-source code, which doesn't allow for independent security audits.
Sometimes termed black box voting, these systems drew deep concern in the early 2000s. Smith says that Nevada was one of the first states to require that the AVC Edge also accommodate a paper trail, which was added in 2004.
She says having a paper trail is crucial requirement for DRE machines, as it allows the electronic tallies to be verified in audits and for voters to ensure their ballot has been cast correctly. Other states followed in implementing a paper trail with AVC Edge machines including California, Nevada, Arizona, Illinois, Wisconsin, Missouri, Colorado and Washington.
But there are a few places that even today do not have a paper trail for the AVC Edge, including the key battleground state of Florida. Two counties in Florida use the machines for people who for accessibility reasons can't use paper ballots, Smith says.
As in the 2000 election between George W. Bush and Al Gore, the outcome can come down to a relative handful of votes. It's not out of the question that a single county in Florida could swing the election one way or the other. Smith says Louisiana and Virginia also used the Edge with no paper trail as well as one county each in Pennsylvania and New Jersey.
A Brighter Future?
The AVC Edge was made by Sequoia Voting Systems, a company acquired by Dominion Voting Systems in June 2010. Efforts to reach Dominion officials by email and phone were unsuccessful.
Cylance's Singh says that the company notified Dominion of the vulnerabilities but didn't hear back. I asked when Cylance notified Dominion, and the company later said that its "respect of responsible disclosure extends to the confidentiality of communications" and that the timing details couldn't be disclosed. That's a bit out of the norm, as most security researchers who disclose vulnerabilities customarily provide a notification timeline.
Even if Cylance's demo is old hat to security researchers who've analyzed e-voting systems, Smith says this kind of research helps raise awareness around the vulnerability of electronic voting systems and the need to replace vulnerable machines. That movement, she says, has been building over the last decade.
"There's been a turning away from purely electronic systems and turning towards more verifiable systems," she says.
So, even if Cylance's demonstration is a cheeky rehash, perhaps it will spur federal election authorities to pursue more funding for secure voting machines and retire the AVC Edge for good.
- Details
- Category: Security News
 Source: Yahoo
Source: YahooYahoo's postmortem into one of the largest data breaches of all time continues to reveal damning information. In a Nov. 9 filing to the Securities and Exchange Commission, Yahoo says it believes that a state-sponsored attacker - which it has blamed for the compromise of at least 500 million accounts - was in its network in 2014, and reports that it detected the related intrusion at the time.
See Also: Managing Identity, Security and Device Compliance in an IT World
The disclosure complicates Yahoo's recovery from the breach, which according to the SEC filing has cost the company $1 million so far. It also casts doubts about whether Verizon will stick with its $4.8 billion bid to buy Yahoo, which it made prior to the breach details becoming public.
Yahoo tells the SEC that an independent committee is investigating how much company officials knew in 2014 about the intrusion, after it was detected. The committee is being advised by an independent counsel and a forensic expert, the filing adds. The broader investigation, which includes cooperation with law enforcement officials, also continues.
The $1 million spent so far on breach recovery has not had a material impact on its finances, according to Yahoo's filing, but the company also notes that it does not carry cybersecurity insurance, and its related costs are likely to rise. Notably, the company is facing 23 putative consumer class-action suits in U.S. federal and state courts by people who claim to have been harmed by the breach, the filing says.
Yahoo says it is not possible to estimate the potential losses from those lawsuits, since the proceedings are in early stages (see Why So Many Data Breach Lawsuits Fail).
Scrutiny Mounts
Regulators and prosecutors are watching Yahoo's breach investigation closely. Yahoo says it is providing information to the Federal Trade Commission, SEC, various state attorneys general and the U.S. Attorney's office for the Southern District of New York.
In Europe, meanwhile, data privacy officials have also expressed their concerns to Yahoo. In a letter to the search giant, Isabelle Falque-Pierrotin, chair of the Article 29 Working Party - the WP29 is composed of the EU's data protection officers - says that Yahoo must inform Europeans whose personal information was compromised "in a quick, comprehensive and easily understood manner so that Yahoo users across Europe will understand any action they need to take as a result of the breach."
In its SEC filing, Yahoo notes that actions by those organizations could result in "civil or criminal penalties which could, among other things, materially increase our data security costs, and affect how we operate our systems and collect and use customer and user information."
'State-Sponsored Actor' Claim Questioned
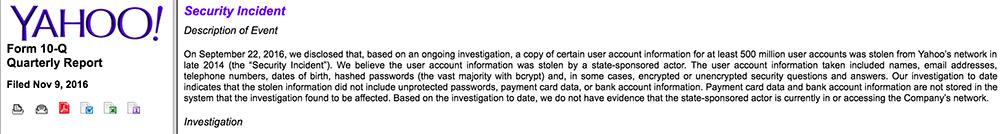 An extract from Yahoo's Nov. 9 SEC filing.
An extract from Yahoo's Nov. 9 SEC filing.The filing is revealing because it's the company's first acknowledgement that it may have detected the 2014 breach shortly after it happened.
Yahoo explains that in July 2016 it investigated a purported breach but could not substantiate a hacker's claim of having obtained Yahoo user data. It then launched a broader security review, which included "a review of prior access to the company's network by a state-sponsored actor that the company had identified in late 2014." The company now believes that attacker is the same one who compromised 500 million accounts.
But one private security company, InfoArmor, has disputed Yahoo's claim that it was hacked by a state-sponsored actor, arguing instead that the attack was launched by a group of professional cybercriminals from Eastern Europe (see Yahoo Hacked by Cybercrime Gang, Security Firm Reports).
Breach Details
On Sept. 22, Yahoo began notifying regulators and users of a massive breach. It was the latest in a spate of mega-breaches to come to light - some historical - involving such companies as LinkedIn, MySpace, Dropbox and Tumblr (see Dropbox's Big, Bad, Belated Breach Notification).
Yahoo also provided technical details relating to how hackers accessed accounts, writing that an intruder "created cookies that could have enabled such intruder to bypass the need for a password to access certain users' accounts or account information."
Cookies are small data files that websites or services place on users' devices. After someone logs into a web service, a cookie will allow someone to repeatedly access a service without requiring login details again. Those types of cookies are usually short-lived and set with an expiration time.
The breach included the compromise of encrypted passwords, names, email addresses, phone numbers and birthdates. Also stolen were the security questions and answers users had selected to verify their accounts, only some of which were encrypted. No payment card or bank account information was compromised, Yahoo said.
How Will Breach Impact Verizon Deal?
With the breach having occurred in 2014 and been detected by the search giant, Yahoo may now face a backlash if regulators conclude that the company waited two years to warn affected users. Many regulators have been moving to make technology companies more accountable for computer security incidents that threaten user data.
The data breach has already complicated Yahoo's acquisition by Verizon, which agreed on July 23 to buy the once-hot internet giant for $4.8 billion. Yahoo warns in its filing that the deal may now not be completed quickly or at all (see Verizon Reportedly Demands $1B Yahoo Discount After Breach).
Either Yahoo or Verizon could back out of the deal. According to the filing, if the stock-purchase agreement is nixed, Yahoo may also have to pay Verizon a termination fee close to $145 million.
It also warned that the ongoing investigation into the data breach, combined with civil litigation and regulatory scrutiny, could have a "material" effect on the business, meaning a significant impact on its finances or operations.
- Details
- Category: Security News
Endpoint Security , Mobility , Risk Management
Expert Kevin Fu on How to Mitigate Today's Top VulnerabilitiesIt's been a hot topic for years, but we are still only in the earliest stages of ensuring medical device security, according to expert Kevin Fu of Virta Laboratories. In this video interview, Fu discusses the top security gaps and how to mitigate them.
See Also: How to Identify and Mitigate Threats on Your Network by Using a CASB
To start with, Fu says, many healthcare organizations simply have the wrong mindset, i.e. "Will hackers disrupt someone's pacemaker?"
"We tend to focus on the most sensational [aspects], as opposed to the most important, in terms of patient outcomes," Fu says. "So although I think improving the security of some of these easy-to-relate-to-the-public scenarios is important, the real problem is much more basic."
The key questions to answer are: Will the devices be working all the time? Will they be available to help deliver treatment?
"It's not necessarily hackers breaking into medical devices that's the biggest problem," Fu says. "There's much more low-hanging fruit, such as how to ensure that hospitals stay online."
In this interview at Information Security Media Group's recent Healthcare Security Summit in New York, Fu discusses:
Myths and realities of medical device security; How to articulate the business risk of device security; What he envisions as the 2017 medical device security agenda.Fu is associate professor of electrical engineering and computer science at the University of Michigan, where he directs the Archimedes Research Center for Medical Device Security. Previously, he served as an associate professor of computer science and adjunct associate professor of electrical and computer engineering at the University of Massachusetts, Amherst. Fu also has served as a visiting scientist at the Food and Drug Administration, the Beth Israel Deaconess Medical Center, Microsoft Research and Massachusetts Institute of Technology Computer Science and Artificial Intelligence Lab. He's also founder, CEO and chief scientist at malware-detection startup firm Virta Laboratories.
More Articles …
Page 3529 of 3545

