- Details
- Category: Security News
Cybersecurity , Info Sharing , Risk Management
FS-ISAC Doesn't Specify Why It's Automated Service Is Being Discontinued
Just two years after its launch, Soltra Edge, the automated threat-intelligence sharing platform, is being taken off the market. The Financial Services Information Sharing and Analysis Center and the private firm The Depository Trust and Clearing Corp., which partnered to introduce the platform, announced on Nov. 15 that Soltra Edge will no longer be supported or available for renewal after March 31, 2017.
See Also: Faster Payments, Faster Fraud?
"While the decision to close the business was not easy, DTCC, as a user-owned and governed market utility, and FS-ISAC, as a member-driven, non-profit organization, must regularly review our product offerings to ensure we remain in alignment with our mission to address the financial industry's most critical challenges while carefully managing our expense base," the two organizations note in a customer letter posted to the Soltra website.
"We understand the decision to close the business may impact your usage of Soltra Edge," the letter continues. "The FS-ISAC Threat Intelligence Repository uses the Soltra Edge software, and as a result, FS-ISAC will begin to look at alternatives to replace its instance of Soltra Edge after the March 31 sunset date. FS-ISAC will, however, continue to support the Threat Intelligence Repository under Soltra Edge in the interim."
The FS-ISAC and DTCC say they will be exploring options to make Soltra Edge available as open-source software.
Neither the FS-ISAC nor DTCC responded to Information Security Media Group's request for comment about their decision.
Lack of Adoption
Several cybersecurity experts say Soltra Edge was never widely adopted by financial institutions and likely is being discontinued because it hasn't been profitable.
"It's got to be financial," says David Shroyer, managing director of information and cybersecurity at Queen Associates, an IT consultancy and staffing agency. "I think it's a lack of adoption."
Shroyer, a former bank CISO, says Soltra Edge was not used by all of the country's top banks, and if penetration was low at community and regional institutions as well, that might have led to the decision to pull the plug.
"Part of Soltra was free; but the more advanced version was not. ... Not all the top 50 [banks] have adopted it, instead relying on the different groups, relationships and email lists to provide cyber intelligence," Shroyer adds.
Financial fraud expert Avivah Litan, an analyst at the consultancy Gartner, says discontinuing Soltra Edge was a business decision. "Too bad it failed," she adds. "It was a really good service."
In addition to the banking sector, Soltra Edge is also used in other industries, including retail and healthcare.
Despite Changes, Utilization Weak
The Soltra Edge model and support system changed quite a bit over the last year, says Brian Engle, executive director of the Retail Cyber Intelligence Sharing Center, which works closely with the FS-ISAC to share cross-industry threat intelligence. "But utilization of automated indicator sharing hasn't been extremely high, from what I understand," he says.
Instead, many organizations continue to rely on manual information sharing facilitated through email exchanges and message boards - services the FS-ISAC and other ISACs also provide and support, Engle adds.
"Automated indicator sharing is really only a part of the equation," Engle says. "So much of the valued sharing that is taking place is done within other methods that include deep analysis, contextual exchanges of information beyond raw indicators and collaborative conversations that include not only indicators, but also insights into techniques and effective solutions. The need for automated platforms will continue, and we'll have to see how innovators in the space step in to fill the gap that Soltra's departure will create."
Denise Anderson, president of the National Health Information Sharing and Analysis Center, says that while the news of Soltra Edge's retirement is "disappointing," information sharing within the healthcare space won't be significantly crippled or stunted by its demise.
"As one of the initial supporters and users of Soltra Edge, NH-ISAC is deeply disappointed in the announcement this week, as well as the way it was handled," she says. "That being said, the announcement should have relatively little impact on our members' abilities to share in machine-to-machine fashion. NH-ISAC currently runs its own instance of Soltra; we were already engaged in strategies to enhance automated sharing within the HPH [health/public health] sector."
Cybersecurity attorney Chris Pierson, general counsel and CISO of invoicing and payments provider Viewpost, says Soltra Edge's departure from the market will open doors for new companies and platforms to step in. "There are a number of companies that can move into this opportunity and use the same sharing formats to provide the necessary information sharing backbone," he says. "I think this provides a few companies with a very nice business opportunity and opening to an audience that has already shown great product-market fit for these tools."
Use of Automated Threat-Intelligence Sharing
Soltra Edge has been downloaded more than 11,000 times and used by nearly 3,000 organizations in nearly 80 countries, according to the Nov. 15 statement from FS-ISAC and DTCC. But the statement does not address what percentage of those downloads were for the free, basic-license version of Soltra Edge versus the more advanced version, which requires payment.
Martin Voorzanger, spokesman for automated threat-intelligence platform provider EclecticIQ, a Soltra Edge competitor, claims most Soltra users relied on the free version of the platform.
"We would be the first to step up, when FS-ISAC and DTCC open-source the product, to offer support," he adds.
FS-ISAC will need to find a replacement for Soltra Edge to ensure that its Threat Intelligence Repository continues to operate. And Shroyer says banking institutions and organizations that have relied on Soltra Edge will have to replace their software, too. "Without a capable replacement for Soltra Edge, it will leave a gap for threat-intelligence sharing," he says. "Banks will have to go to another company."
STIX and TAXII Will Survive
Soltra Edge helped to propel automated information sharing through the use of open-source standards, such as the Structured Threat Information eXpression, or STIX, and the Trusted Automated eXchange of Indicator Information, or TAXII.
STIX is a uniform format for threat information; TAXII is a protocol for routing threat information.
The use of STIX and TAXII will continue, even without Soltra Edge, says Shroyer of Queen Associates. "The framework that STIX/TAXII provides should continue, as it is a solid method for exchanging information," he says. "What tool is adopted across the board will be interesting. I think it will depend on how valuable the users see the software being, and how well it ensures integration into new systems surrounding the space."
(Executive Editor Marianne Kolbasuk McGee contributed to this story).
- Details
- Category: Security News
DDoS , Endpoint Security , Risk Management
Experts Testify on IoT Dangers and the Need for Standards, Regulations Cybersecurity experts Bruce Schneier and Kevin Fu testify.
Cybersecurity experts Bruce Schneier and Kevin Fu testify.What's needed to bolster the security of internet of things devices to help prevent cyberattacks, such as the October botnet-driven distributed denial-of-service attack on web services provider Dyn that crippled Netflix, Twitter and many other websites?
See Also: Protect Your Identity Infrastructure
It could boil down to a combination of implementing industry standards, incentives and regulations, a panel of experts testified at a joint House committee hearing on Nov. 16 exploring the role of connected devices in cyberattacks.
The hearing was aimed at helping Congress review recent DDoS attacks waged using botnets built on connected devices, understand current countermeasures and consider efforts to combat malicious actors that could target vulnerabilities, Rep. Greg Walden, R-Ore., noted in his opening remarks.
Worse Attacks on Horizon?
The recent DDoS attack on Dyn, which involved more than 100,000 IoT devices ranging from baby monitors to webcams, was relatively "benign" and could be a precursor to more sophisticated cyberattacks exploiting IoT device vulnerabilities, according to Bruce Schneier, a fellow at the Kennedy School of Government at Harvard University and CTO of Resilient, an IBM company.
In the Dyn cyberattack, he testified, "some websites went offline for a while. No one was killed. No property was destroyed. But computers have permeated our lives. The internet now affects the world in a direct physical manner. The internet of things is bringing computerization and connectivity to many tens of millions of devices worldwide. We are connecting cars, drones, medical devices and home thermostats. What was once benign is now dangerous."
Medical device cybersecurity expert Kevin Fu, CEO of Virta Labs and professor of electrical engineering and computer science at the University of Michigan, testified: "No one has been able to provide assurance that a future Dyn-like attack will not cause a massive, nationwide healthcare outage" or cause other major disruptions to, for example, power grids.
Multifaceted Approach?
Under questioning by committee members, the experts testified that shoring up security of IoT devices - without killing innovation - might require a multifaceted approach that includes incentives, regulations and standards designed to make sure security is built into products.
"We're asking consumers to shore up security," Scheier said, expecting buyers of IoT products, for example, to change default passwords. "There shouldn't be default passwords [in devices]; this shouldn't be consumers' problem."
Dale Drew, chief security officer of Level 3 Communications, testified: "The best place to start is with standards ... and then apply pressure. If, for example, IoT devices were capable of 'auto-patching,' ... [that would] help keep infrastructure healthy."
But many manufacturers aren't embedding security into their products because of a lack of economic incentives, the security experts said. Consumers and businesses aren't necessarily willing to pay extra for security - or often aren't even aware of the risks, the experts testified.
Also, manufacturers of IoT products containing software and hardware components from many different vendors - including foreign suppliers - aren't necessarily building security into all those components. To complicate matters, "there's no national testing lab" to assess the cybersecurity of IoT devices, and there are no clear national or global standards, Fu noted.
The experts didn't agree on whether one set of cybersecurity-related standards could fit all IoT devices or if standards and best practices should vary depending upon the industry where devices are used.
The National Institute of Standards and Technology has done a good job of setting standards and principles for cybersecurity, Fu noted (see: NIST Guidance Takes Engineering Approach to InfoSec). But that doesn't necessarily mean companies comply with principles, "many that have been known for 30 years," he said.
Potential Dangers
Potential risks posed by cyberattacks against medical devices are similar to preventable risks involved in automobile travel before airbags were implemented, Fu said.
"IoT security is woefully inadequate," he testified. "I do believe this will require some kind of government mandate. We don't have economic drivers."
Rep. Ann Eshoo, D-Calif., noted that she had previously introduced legislation "that hasn't gained much traction" proposing creation of "a good housekeeping seal of approval" for IoT devices meeting a set of cybersecurity standards. The idea is to promote "security without dampening innovation," she noted.
Schneier suggested that there may be a need for a new federal government agency to address the cybersecurity concerns of connected devices.
"The choice isn't between government or no government [involvement] - it's a choice between smart and stupid government involvement," Schneier testified. "I'm not a regulatory fan, but this is the world of dangerous things. There's a fundamental difference between [a cyberattack causing] a spreadsheet to crash and me losing data - and a car crashing and losing life. The internet era of fun and games is over."
Workforce Challenges
Fu suggested that to better protect the U.S. infrastructure, the nationwide cybersecurity talent shortage needs to be addressed.
"Universities, industry and government must find the strength and resolve to invest in embedded cybersecurity with interdisciplinary science and engineering, industrial partnerships for research and education, and service to the nation," he testified.
- Details
- Category: Security News
Mobility , Privacy , Risk Management
Code Sent Call Logs, Texts and More to Shanghai
In what's being chalked up as an apparent mistake, more than 120,000 Android phones sold in the U.S. were shipped with spying code that sent text messages, call logs and other sensitive data to a server in Shanghai.
See Also: Secrets to a Simpler Security Incident Response
The New York Times reported on Nov. 15 that Kryptologic, a mobile enterprise security company, discovered the code on a lower-end smartphone made by BLU Products of Doral, Fla. The phones are sold at Best Buy and Amazon.com, among other retail outlets.
Kryptologic says the code, which it found on a BLU R1 HD devices, transmitted fine-grained location information and allowed for the remote installation of other apps. Text message and call logs were transmitted every 72 hours to the Shanghai server, and once a day for other personally identifiable data, the company says.
It turns out, however, that other security researchers noticed suspicious and faulty code on BLU devices as early as March 2015, and it has taken nearly that long to remove it from the company's devices.
The finding, in part, shows the risk that can come in opting for less expensive smartphones, whose manufacturers may not diligently fix security vulnerabilities. It's also raising eyebrows because of the connection with China, which has frequently sparred with the U.S. over cyber espionage.
BLU Products has now updated its phones to remove the spying code, which most likely would have never been detected by regular users. The code never informed phone users that it was collecting that data, a behavior uniformly viewed by many as a serious security concern.
The developer of the code, Shanghai Adups Technology Co., has apologized, contending that the code was intended for another one of its clients who requested better blocking of junk text messages and marketing calls.
Vulnerabilities Reported
BLU Products, founded in 2009, makes lower-end Android-powered smartphones that sell for as little as $50 on Amazon. Like many original equipment manufacturers, it uses software components from other developers.
The company uses a type of software from Adups that's nicknamed FOTA, short for firmware over-the-air. The software manages the delivery of firmware updates over-the-air, the term used for transmission via a mobile network. Firmware is low-level code deep in an operating system that often has high access privileges, so it's critical that it's verified and contains no software vulnerabilities.
Long before Kryptologic's announcement, Tim Strazzere, a mobile security researcher with RedNaga Security, contacted BLU Products in March 2015 after he found two vulnerabilities that could be traced to Adup's code. Those vulnerabilities could have enabled someone to gain broad access to an Android device.
Strazzere's colleague, Jon Sawyer, suggested on Twitter that the vulnerabilities might have not been there by mistake, but rather included as intentionally coded backdoors. He posted a tweet to The New York Times report, sarcastically writing, "If only two people had called this company out for their backdoors several times over the last few years."
Strazzere's experience in trying to contact both vendors last year is typical of the frustrations frequently faced by security researchers.
"I tried reaching out to Adups and never heard back," Strazzere tells Information Security Media Group. "BLU said they had no security department when I emailed them."
Strazzere says he also failed to reach MediaTek, a Taiwanese fabless semiconductor manufacturer whose chipsets that powered BLU phones also contained Adups software. To their credit, both Google and Amazon appear to have put pressure on device manufacturers to fix their devices when flaws are found, Strazzere says.
For Google, Android security issues - even if not in the core operating code - are a reputation threat, and for Amazon, a product quality issue. But devices sold outside of Amazon "might not have ever seen fixes," he says.
Officials at BLU couldn't be immediately reached for comment.
Attitude Change
The disinterest in the issues appears to have changed with The New York Times report, which lit a fire underneath Adups and BLU.
Adups addressed the issue in a Nov. 16 news release, writing that some products made by BLU were updated in June with a version of its FOTA that had actually been intended for other clients who had requested an ability to stop text spam.
That version flags messages "containing certain language associated with junk texts and flags numbers associated with junk calls and not in a user's contacts," the company says.
Manufacturers should be keeping close tabs on what software ends up on their devices. But it would appear that BLU only took action after Kryptologic notified it along with Google, Adups and Amazon.
"When BLU raised objections, Adups took immediate measures to disable that functionality on BLU phones," Adups says.
The greater worry is that these situations may sometimes not be simple mistakes. Security experts have long warned of the ability of advanced adversaries to subvert hardware and software supply chains. Also, the software vulnerabilities pointed out in the FOTA software by Strazzere in 2015 could have been taken advantage of by cybercriminals looking to steal bank account details or execute other frauds.
Strazzere advises that consumers should look at the pedigree of mobile manufacturers and take a close look at their security track record before making a decision on what device to buy.
"In the end, the consumer needs to vote with their wallet," he says.
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
Endpoint Security , Risk Management , Technology
Locked PCs No Match for Samy Kamkar's Latest Hacking Tool PoisonTap Sneaks Into Computers, Even If They're Locked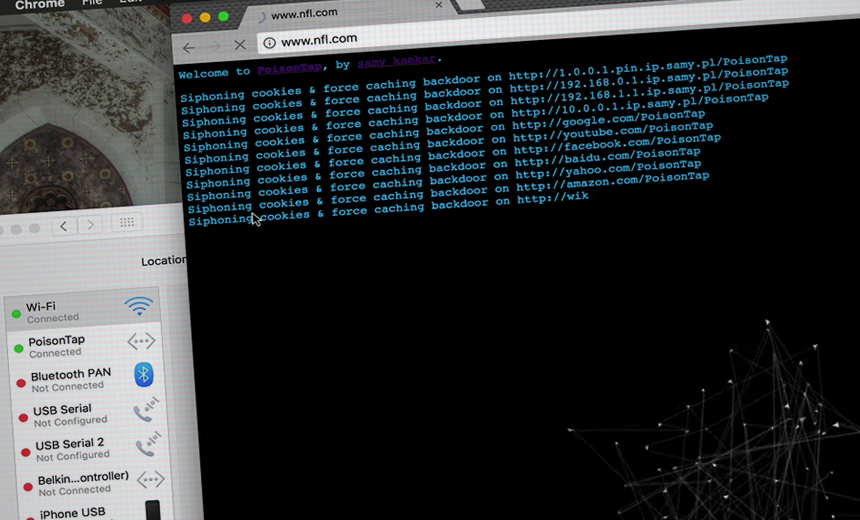 Image from Samy Kamkar video on PoisonTap
Image from Samy Kamkar video on PoisonTapIt's an innocent act: Close the lid on the laptop and go for a burrito at lunch. The laptop locks itself and goes into a mid-day snooze. But as prolific hacker Samy Kamkar shows with his latest experiment, this feeling of security is an illusion.
See Also: Faster Payments, Faster Fraud?
Kamkar, who most famously created the MySpace worm a decade ago, pushes the bounds of hacking possibilities, finding creative ways to disrupt systems. And his most recent work, which he calls PoisonTap, is yet another illustration of how tradeoffs made between security and convenience can open up dangerous security holes.
Kamkar built PoisonTap using a $5 Raspberry Pi Zero computer, a microUSB cable and a microSD card. Although physical access to a computer is required to insert the device, from there it doesn't rely on any software vulnerabilities to accomplish its misdeeds. Instead, it takes advantage of the implicit trust put in connected devices and produces "a snowball effect of information exfiltration, network access and installation of semi-permanent backdoors," Kamkar writes on his blog.
Kamkar has released the source code for PoisonTap on GitHub along with a demonstration video.
Locked, But Not Really Locked
When computers go into a locked state, most users would think nothing gets in or out. But Kamkar found that even if a computer requires a password to gain access again, he could skip over that step by inserting his malicious USB device.
When the computer then asks PoisonTap for an IP address, it impersonates an ethernet device. And rather than just responding as a local network device, PoisonTap pretends it's the entire internet IPv4 address space. The computer then prioritizes PoisonTap's connection because it's a local area network and subsequently routes all of its internet traffic over it.
The trouble starts there, and Kamkar found all kinds of ways to tamper with a computer even if PoisonTap is physically connected to a computer for only a short period. He found he could easily steal certain types of cookies, which are small data files stored within a web browser that allow, for example, visitors to continue to access a website without logging in again.
By spoofing DNS requests, Kamkar could deliver hidden iframes to a person's web browser that impersonated popular websites and then collect those sites' cookies. It should be noted that this attack will not work if websites are encrypted, designated by "https" in the URL window, or if cookies have been flagged with the "secure" setting.
The implanted iframes, though, don't disappear - even if PoisonTap is removed. The browser caches them, which makes them essentially backdoors unless someone flushes their browser's cache, which regular users rarely do. The backdoor could also allow an attacker to have access to the user's router, Kamar writes.
"This can lead to other attacks on the router which the attacker may have never had access to in the first place, such as default admin credentials on the router being used to overwrite DNS servers or other authentication vulnerabilities being exposed," he writes.
The Glue Defense
The sure-fire defense against PoisonTap is one that has been used for a long time: permanently plugging USB ports with epoxy.
As noted before, PoisonTap is also ineffective if websites are encrypted. Following the leaks from former National Security Agecy contractor Edward Snowden that revealed large-scale government spying operations, more and more websites are implementing encryption, but the massive effort is far from complete.
Closing web browsers when leaving a computer unattended is another defense, although Kamkar notes that behavior "is entirely impractical."
There are also some platform-specific tips: Enabling FileVault, macOS's full-disk encryption feature, is recommended. When Macs go into a deep sleep, "your browser will no longer make requests, even if woken up," Kamkar writes.
Even though macOS has a setting that requires an administrator password before a change to network setting is allowed, Kamkar wrote on Twitter that "it only prevents *manual* network changes, yet still auto-provisions new devices."
More Articles …
Page 3532 of 3545
