- Details
- Category: Security News
Breach Notification , Breach Preparedness , Breach Response
2013 Breach Appears Separate from Another Breach Involving 500 Million Users Yahoo's corporate headquarters in Sunnyvale, Calif.
Yahoo's corporate headquarters in Sunnyvale, Calif.Yahoo has the dubious distinction of having not just one but two record-shattering historical data breaches come to light in the same year.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
Yahoo on Dec. 14 warned that it's found a breach that appears to date from 2013, which put the data of 1 billion users at risk.
"We believe an unauthorized third party, in August 2013, stole data associated with more than one billion user accounts," Yahoo CISO Bob Lord says in a security alert to customers. "We have not been able to identify the intrusion associated with this theft."
Information that was potentially stolen includes names, email addresses, telephone numbers, dates of birth, passwords hashed using the outdated MD5 algorithm as well as encrypted or unencrypted security questions and answers. Yahoo says no payment card data or banking information was stored in the affected system, and thus it does not believe any such data was compromised.
Yahoo is notifying all potentially affected customers and says that it's invalidated all security questions.
The search giant believes the breach is separate from the incident that it confirmed on Sept. 22, which involved the theft of more than 500 million accounts in late 2014 (see Massive Yahoo Data Breach Shatters Records). In a recent Securities and Exchange Commission filing, Yahoo said that it detected that an attacker was inside its network in 2014, but failed to spot the data exfiltration.
The White House says the FBI is now investigating both Yahoo breaches.
In September, Lord said Yahoo believed that 2014 attack was perpetrated by "a state-sponsored actor." But security firm InfoArmor has suggested that a cybercrime gang without nation-state ties might have been behind the attack (see: Yahoo Breach Conspiracy Theories: Don't Believe the Hype).
In the latest breach alert, Yahoo says that it first learned of the 2013 intrusion from U.S. law enforcement, which shared information that an unnamed third party claimed involved Yahoo data.
"We analyzed this data with the assistance of outside forensic experts and found that it appears to be Yahoo user data," Lord says.
Yahoo declined to specify which law enforcement agency shared the set of stolen data. "We're not sharing detail with regards to methods and sources associated with our investigation," a spokesman tells ISMG. "We continue to work closely with law enforcement."
Cookie-Forging Attacks
Yahoo says that it's continued to investigate attacks involving forged cookies, referring to small pieces of code placed by websites on a user's device to track users and often also free them from having to log into a site every time they return.
But attackers appear to have reverse-engineered Yahoo's cookies, enabling them "to access users' accounts without a password," Lord says. "The outside forensic experts have identified user accounts for which they believe forged cookies were taken or used. We are notifying the affected account holders and have invalidated the forged cookies. We have connected some of this activity to the same state-sponsored actor believed to be responsible for the data theft the company disclosed on Sept. 22, 2016."
Yahoo declined to comment on the number of accounts that may have been compromised by attackers wielding compromised cookies.
In September, shortly after Yahoo announced the 2014 breach, InfoArmor claimed in a blog post that it likely knew of a specific group that was behind the hack.
InfoArmor said at the time that it had obtained a sample of the stolen Yahoo data from its sources, according to a blog post. In a Dec. 14 email to ISMG, InfoArmor's chief intelligence officer Andrew Komarov says that Yahoo's description of the type of data leaked in 2013 matches its sample.
The limited set of InfoArmor data that was provided to Yahoo - via Bloomberg - could overlap with the information shared with Yahoo by the law enforcement agency, a source familiar with Yahoo's investigation tells ISMG.
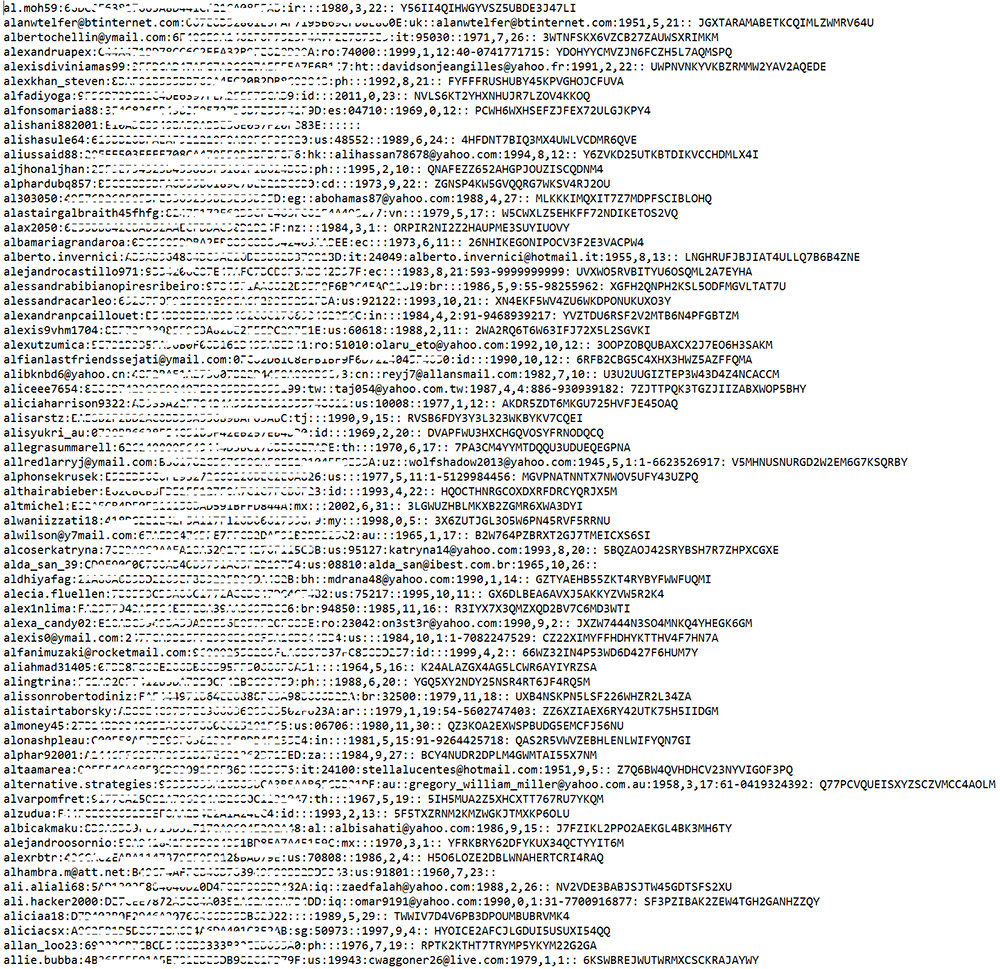 A sample of the stolen Yahoo data obtained by InfoArmor.
A sample of the stolen Yahoo data obtained by InfoArmor.In its blog post, InfoArmor said it believed that the attackers who stole the information that it later obtained were "a group of professional blackhats from Eastern Europe," which InfoArmor calls Group E.
Group E had a relationship with someone who offered batches of stolen data on underground markets from companies including LinkedIn, InfoArmor claims. The person went by the nickname "Tessa88." Tessa88 was also connected with another persona who sold underground data, "peace_of_mind" or Peace.
Both Tessa88 and Peace had advertised batches of stolen data, including the LinkedIn and MySpace breaches. But other leaks the two advertised turned out to be mislabeled and actually aggregations of data from other breaches.
Wrinkle for Yahoo
The latest breach admission comes at a tricky time for Yahoo, which has been seeing a decline in revenue. Plus, CEO Marissa Mayer has faced criticism that the company failed to devote sufficient resources to bolstering its information security program.
"What's most troubling is that this occurred so long ago, in August 2013, and no one saw any indication of a breach occurring until law enforcement came forward," Jay Kaplan, CEO of security firm Synack, tells The Wall Street Journal. "Yahoo has a long way to go to catch up to these threats."
The breach also highlights the ongoing challenges that breached organizations face when it comes to discovering that they've been breached. "This billion-person data theft illustrates two critical points: first, there is currently no single technology or blend of technology controls that currently exists to either keep a persistent and well-trained adversary from breaking into any company, and second, that technology that moves at machine speed to let a company know data is flowing out the back door is not mature enough to provide real-time alerting," Christopher Pierson, CSO of B2B payment provider Viewpost, tells ISMG.
Will Breach Impact Verizon Deal?
In late July, Verizon agreed to buy Yahoo's operating businesses for $4.8 billion. Many market watchers say the deal comes at a critical time for Yahoo, which has been seeing declining revenues. By acquiring Yahoo, furthermore, Verizon could combine it with AOL, which it acquired in 2014 for $4.4 billion, thus battling Google and Facebook for a bigger share of the world's online advertising revenue.
Following the first breach revelation, in response to questions about whether Verizon might seek to alter the terms of the deal or walk away, it said in October that it was waiting to see the full results of Yahoo's investigation (see Verizon's Yahoo Breach Question: What's 'Material'?).
On Dec. 14, Verizon now said it's awaiting the full results of both breach investigations. "As we've said all along, we will evaluate the situation as Yahoo continues its investigation," says Verizon spokesman Bob Varettoni. "We will review the impact of this new development before reaching any final conclusions."
Historical Mega-Breach Discoveries Continue
Yahoo isn't the only company to have revealed this year that it discovered a massive, historical breach that put users and their data at risk for years before it was discovered or fully understood. Other organizations that have found themselves in a similar situation this year have included Dropbox, LinkedIn, MySpace and Tumblr, among others. In some cases, organizations discovered that breaches that they had spotted were much worse than they believed. LinkedIn, in particular, found that a 2012 breach hadn't resulted in the theft of 6.5 million uses' accounts details, but rather involved 165 million accounts.
"We truly are under major siege and we're unprepared for it. It really is a national emergency," Avivah Litan, vice president at Gartner Research, tells USA Today. "We need a national response plan for this."
Managing Editor Jeremy Kirk also contributed to this story.
- Details
- Category: Security News
Ransomware is going to get personal. Password managers will be huge targets. And we will see the rise of a whole new exploit kit. These are among the 2017 security predictions from Malwarebytes Laboratories.
And because these attacks are going to continue to result in big headlines, cybersecurity is going to grow as a boardroom issue - which is good news for security leaders, says Marcin Kleczynski, CEO of Malwarebytes.
"I think 2016 was a period where a reset button was pressed, and more companies started thinking about cybersecurity," Kleczynski says. In 2017, he says, "more cybersecurity leaders will become board members; CISOs will be hired; and potentially CIOs will be displaced by CISOs."
In an interview about 2017 security predictions, Kleczynski discusses:
How ransomware defense must change; Why password managers and digital wallets will be bigger targets; What we can expect to see from large-scale, IoT-enabled attacks.Marcin is the founder of Malwarebytes. He oversees the strategic expansion of the business, as well as the long-term vision for the research and development teams. Marcin has been recognized for his work in cybersecurity, receiving the Ernst and Young Entrepreneur of the Year award, and being named to the Forbes 30 Under 30.
- Details
- Category: Security News
Hack attack victims often ask two questions: "Who did it? And can we hack them back?"
But after an attack, with time of the essence for blocking further damage, those are the wrong questions for breached organizations to be asking, says data breach prevention and response expert Alan Brill of the corporate investigations and risk consulting firm Kroll.
"If you spend a bunch of money trying to figure out who did it, how's that going to help you?" he asks. "You're not cops. You're not going to go arrest somebody. You're probably not going to go file civil suits against foreign governments, [so] is that a wise use of funds?"
Focusing on attribution so that an organization can "hack back" - rather than focusing on how to quickly recover from a breach - doesn't make a lot of sense, Brill contends in an interview with Information Security Media Group.
Misguided Calls for Vigilantism
Following this year's belated discovery that Yahoo suffered the biggest known data breach ever, some commentators called for pre-emptive strikes against attackers. Meanwhile, a French ransomware researcher earlier this year described how he'd attempted to infect India-based tech support scammers with Locky ransomware after they allegedly targeted his parents with their online scams.
While this type of "hacking back" vigilantism may earn public plaudits and satiate a desire for revenge, it's often illegal - and it could easily cause collateral damage. In addition, it too often detracts from the rapid triage that must occur following any breach, Brill notes. "The resource in the shortest supply when a breach occurs is time," he points out.
In this interview (see audio link below photo), Brill also discusses:
Crisis management steps every organization should take both before and after a suspected breach; The legal risks faced by any firm that attempts to hack back; Lessons learned from hundreds of data breaches.Brill is a senior managing director with Kroll's cybersecurity and investigations practice. As the founder of Kroll's global high-tech investigations practice, he has led engagements that range from large-scale reviews of information security and cyber incidents for multibillion-dollar corporations to criminal investigations of computer intrusions. He's also the co-author of a report issued by the nonprofit organization Center for Democracy and Technology titled: "Private Sector Hack-Backs and the Law of Unintended Consequences."
- Details
- Category: Security News
Fraud , Privacy , Risk Management
GAO Report on Privacy and Security: A Wake-up Call for HHS? It's Time to Recognize Healthcare as One of the 16 Critical Infrastructure Sectors
For years, I have been a vocal proponent of securing protected health information. It is no secret that The U.S. Department of Health and Human Services (HHS) swept security and authentication under the rug during the rollout of electronic health records (EHRs) as to not to impede adoption of electronic records by providers by making it difficult to use them. The current minimum requirements for identity assurance are set low, requiring only a strong password. The reality is HHS played Russian roulette, hoping that security breaches would not occur due to weak username and static password authentication. Putting convenience of security has led to breaches impacting millions of lives.
As Chair of the HIMSS Identity Management Task Force, I am constantly seeking news as it relates to security, identity management, and breaches to name of few topics and their effect on the nation's healthcare system.
I just read the Government Accountability Office's report to the U.S. Senate's Committee on Health, Education, Labor and Pensions. The title tells the story, "HHS Needs to Strengthen Security and Privacy Guidance and Oversight".
Having been immersed in identity management and the security side of health IT, nothing in the report surprised me. The GAO report touches on the key findings and cites the historic breaches in 2015 affecting over 113 million individual health care records due to hacking or other incidents as well as HHS' shortcomings as it relates to securing our healthcare system.
We are at a point where HHS needs to wake up and realize that our healthcare system is one of the 16 critical infrastructure sectors defined in 2013's Presidential Policy Directive 21. The Directive includes many provisions, one of which tasked NIST to develop a Cybersecurity Framework. Although conforming to NIST's Cybersecurity Framework is voluntary, its core set of security controls represents a consensus of topics to consider when developing information security programs. The Framework includes 98 subcategories.
HHS' Office of Civil Rights (OCR) proactively developed a "crosswalk toolkit" that mapped 2003's HIPAA Security Rule to the 2014 Cybersecurity Framework to show how organizations' existing HIPAA compliance efforts fit into the Framework. GAO points out that, "of the 98 framework subcategories, the toolkit fully addresses only 19. Many of the specific controls detailed within the framework's 98 subcategories are not addressed in the either the HHS security assessment guidance or in its other risk management guidance." If you are a baseball fan, 19 for 98 is below the Mendoza Line, batting .194.
Over the years HHS, has released several guidance documents, but all are weak and without mandates as it relates to identity management and authentication of entities accessing protected health information. Guidance documents typically include words like "may" and "should," but rarely include words like "shall" or "must," especially when it comes to identity management and the authentication of users accessing PHI.
The GAO reinforces my statements in the report stating, "However, the guidance published by HHS does not address all of the elements in the NIST guidance. HHS officials said they intended their guidance to be minimally prescriptive to allow flexible implementation by a wide variety of covered entities. However, until these entities address all the elements of the NIST Cybersecurity Framework, their EHR systems and data are likely to remain unnecessarily exposed to security threats."
The GAO provides five recommendations for executive action. The first two are most notable:
Update security guidance for covered entities and business associates to ensure that the guidance addresses implementation of controls described in the NIST Cybersecurity Framework; Update technical assistance that is provided to covered entities and business associates to address technical security concerns;HHS can no longer stick its head in the sand and hope this cyberwar will just go away. I am pleased with the GAO's report and I hope it will serve as a wake-up call for HHS. Honestly, what else needs to happen to urge HHS to update the 13-year-old HIPAA Security Rule so that it maps to identity proofing and multi-factor authentication milestones included in ONC's 2015 Shared Nationwide Interoperability Roadmap and NIST's Cybersecurity Framework. It is my hope that HHS will collaborate with organizations like the HIMSS Identity Management Task Force, the HIMSS Privacy & Security Committee and the Identity Ecosystem Steering Group.
For more information on VASCO security solutions for healthcare visit https://www.vasco.com/solutions/healthcare-information-security/.
- Details
- Category: Security News
Rodney Petersen sees too many government agencies and businesses using old-school methods to identify and recruit IT security professionals. And, as a result, they often fail to build their cybersecurity staffs.
Petersen is director of the National Institute of Standards and Technology's National Initiative for Cybersecurity Education, known by the acronym NICE.
In an interview with Information Security Media Group (click player below photo to listen), Petersen says employers too often ignore qualified job prospects because they might hold an associate's degree, but not the obligatory bachelor's degree, despite having the right know-how to get the job done.
"HR and job descriptions quite often try to do what everybody else is doing, and therefore if everybody else is requiring a bachelor's degree, three-to-five years' experience and XYZ certification, then that must be good for us, too," Petersen says. "There is really no direct evidence [those requirements are] measuring the knowledge skills and abilities needed."
Petersen, in the interview:
Explains the importance of accurately describing job characteristics to attract the right people for the positions; Encourages employers to hire quick learners because the rapidly evolving IT security field requires professionals who can absorb new knowledge and pick up new skills swiftly; Describes the significance to job seekers, employers and educators of a new visualization mapping tool NICE is funding that will identify geographically IT security needs.NICE, a government-private sector initiative housed at NIST, aims to develop IT security programs to accelerate learning and skills development, nurture a diverse learning community and guide career development and workforce planning.
Petersen, before joining NIST, served as managing director of the EDUCAUSE, a not-for-profit association of IT leaders aimed at advancing higher education, where he founded and directed its Cybersecurity Initiative and was the lead staff liaison for the Higher Education Information Security Council. He coedited the book titled Computer and Network Security in Higher Education.
Page 3545 of 3545
