- Details
- Category: Security News

New Zealand is rewriting the laws under which its intelligence agencies operate - a move the government says will create a clearer legal framework. But it's also one that critics fear inordinately expands electronic spying powers.
See Also: Secrets to a Simpler Security Incident Response
The Intelligence and Security Bill, introduced into Parliament on Aug. 15, seeks to replace four acts that govern the activities of the New Zealand Security Intelligence Service and the Government Communications Security Bureau, the country's equivalents of the U.S. Federal Bureau of Investigation and National Security Agency.
It's a lengthy, complicated bill that casts a broad remit for spy agencies well beyond fighting terrorism, for reasons including economic well-being and diplomacy. The government says the rewrite also means the agencies would be held to stronger, independent oversight to protect civil liberties.
Thomas Beagle, chairperson of the NZ Council for Civil Liberties, says even a strong oversight process doesn't matter if the agencies have wide leverage to spy. He contends the government's argument of creating clearer rules is misleading.
"That's actually a very loaded framing of the situation," Beagle says. "When they say 'unclear rules,' what they're actually often saying are rules that we don't want or we don't like anymore. Even if you've got a really great oversight process, if the allowable areas are too wide, the process doesn't really matter so much."
Spying Missteps
Similar to the U.S. and U.K., New Zealand has been grappling with civil liberties questions related to large-scale data collection by intelligence agencies. Over the last two decades, the rise in the use of mobile devices and the internet as communications tools has allowed spy agencies to collect granular detail about individuals' movements and communications, known in the spy business as signals intelligence.
New Zealand is part of Five Eyes, the signals intelligence collective that includes the U.S., U.K., Canada and Australia. All of the countries have laws in place that are, in theory, supposed to prevent intelligence agencies from collecting data on their own citizens without a warrant.
But the leaks of top secret NSA and British GCHQ documents in 2013 by former NSA contractor Edward Snowden detailed the impressive capabilities of spy agencies, showing deep access into the systems of telecom operators and major technology companies. New Zealand has experienced embarrassing missteps that raised questions over the oversight of its intelligence agencies.
In September 2012, Prime Minister John Key apologized after it was found GCSB provided information to New Zealand police about Megaupload founder Kim Dotcom, wanted in the U.S. on copyright infringement charges. Dotcom is a New Zealand permanent resident. Under the law, GCSB is prohibited from collecting private communications of citizens and permanent residents.
As many as 88 people, including Dotcom, may have been illegally spied upon by GCSB between 2003 and 2012, according to a 2013 compliance review of the GCSB, prompting a call for clearer legal rules be drawn up for the agency.
The Snowden documents also revealed that in 2012, the GCSB collaborated with the NSA in spying on Tony Fullman, a New Zealand citizen and activist who was mistakenly thought to have been planning a coup in Fiji. His home was raided and his passport was revoked, according to a September story in The Intercept.
The Bill's Provisions
As drafted, the bill would allow intelligence agencies to quickly obtain warrants in order to conduct surveillance on New Zealand citizens and permanent residents. Under a "triple lock" system, warrants would have to be approved by the country's attorney general and the chief commissioner of intelligence and would be subject to review by the inspector general of intelligence and security.
Although the agencies are supposed to minimize inadvertent data collection that would be illegal, the bill would allow that information to be shared - even outside New Zealand - if a situation is deemed life threatening.
New Zealand's government contends it's unclear under current law whether GCSC could be called upon, for example, to trace a New Zealand citizen's mobile phone communications if the person was lost at sea.
In a move to head off a Snowden-like leak, the bill also criminalizes the disclosure of classified information to anyone other than the inspector general of intelligence and security. That is already illegal, but the government says the changes consolidate and strengthen the law.
Oversight for how intelligence agencies operate would be conducted by the inspector general as well as the Intelligence and Security Committee.
Commenters Say Proposal Needs Refinement
The bill is now before the Foreign Affairs Defence and Trade Committee, which held hearings in October and received dozens of comments from private companies, organizations and government officials. Those submissions describe some of the concerns over the bill's language.
Vodafone New Zealand says the bill improves the clarity of the powers of the GCSB and SIS. But the telecom giant took issue with one part of the bill that would appear to encourage companies to make proactive disclosures to intelligence agencies. Vodafone says it would prefer specific warrants rather than ones requiring "discretionary assistance."
"This is because discretionary provision of data is not consistent with our commitment to protect the privacy of our customers," Vodafone writes. "It would require us to make difficult judgments that we are unlikely to have the necessary information to support."
The New Zealand Law Society took issue with clauses in the bill that would allow citizens to be targeted with a warrant for activities that fall under the broad category of affecting the "economic well-being of New Zealand." For example, a New Zealand lawyer could be targeted on the suspicion of acting on behalf of an Australian. "The Australian person for whom the lawyer is acting need not even have any relevance to the intelligence sought to be gathered under the warrant," the Law Society writes.
- Details
- Category: Security News
This special edition of the ISMG Security Report focuses on cybersecurity matters related to President-elect Donald Trump.
In the report, you'll hear (click on player beneath above image to listen):
Purdue University Computer Science Gene Spafford discuss whether the IT security community should conduct a self-assessment regarding weak security implementation that failed to prevent a breach of Democratic Party computers, resulting in the release of emails embarrassing to Hillary Clinton that might have influenced the outcome of the presidential election; Ari Schwartz, former special assistant to the president for cybersecurity, voice concern about Trump's praising Russian President Vladimir Putin when the U.S. intelligence community blames Russia for the attack on DNC computers; Former Homeland Security Deputy Undersecretary Phil Reitinger and former White House senior cybersecurity adviser Melissa Hathaway discuss how more detailed intelligence briefings could change how Trump views the Russians; and Mark Weatherford, another former DHS deputy undersecretary; Reitinger and Hathaway discuss whether Trump should adopt a cross-agency, uniform approach to cybersecurity.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Nov. 4 and Nov. 8 reports, which respectively analyzed potential cyberthreats that could have damaged the integrity of the U.S. presidential election and how the FBI likely reviewed 650,000 emails found on a computer used by a top Hillary Clinton aide. The next ISMG Security Report will be posted on Tuesday, Nov. 15.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
Breach Preparedness , Data Breach , Info Sharing
Information Sharing: A Powerful Crime-Fighting Weapon Law Enforcement, Government Agencies Stress that Threat Intelligence is Critical Jason Tunn of London Metropolitan Police Service
Jason Tunn of London Metropolitan Police ServiceIn October 2015, collaborative efforts to take down hackers linked to the notorious banking Trojan known as Dridex paid off for law enforcement.
See Also: Faster Payments, Faster Fraud?
Operation SAMBRE was a global cybercrime investigation into the theft of billions of dollars from banks throughout the world, with top-tier banks in the U.K. and U.S. hit particularly hard. The cooperation of law enforcement officials in the U.S., U.K. and other nations resulted in the arrest of three individuals, two of whom are now serving jail time.
It was a massive undertaking, one that hinged on a mix of good old-fashioned detective work and technical savviness, Jason Tunn of the Metropolitan Police Service in London said in his keynote address at our Fraud & Breach Prevention Summit on Nov. 9.
Authorities arrested the two men now serving jail time after surveilling their apartment in London, awaiting just the right moment to nab them after they stepped outside to take a smoke break, Tunn explained.
But Operation SAMBRE wasn't just about good detective work. It also was about strong cyber threat intelligence and information sharing that hinged on trusted relationships with banks willing to share their fraud and attack details with police.
Banks Have to Be Willing to Share
Without banks' willingness to proactively share information with law enforcement, Operation SAMBRE would not have been a success.
Information sharing may sound cliché. Since the emergence of the Financial Services Information Sharing and Analysis Center, which got a significant boost in global recognition in the wake of the 2012-2013 distributed denial-of-service attacks waged against leading U.S. banks and financial firms, the term "information sharing" has been overused and, some might argue, diluted.
What does "information sharing" really mean? Tunn's description of Operation SAMBRE provides the perfect definition: communication of the details about cybercrime and fraud activity among financial institutions and, ultimately, with law enforcement.
 The closing day panel, "We've Been Breached. Now What? How to Effectively Work With Law Enforcement," included, from left, Peter Yapp of the National Cyber Security Centre, Jason Tunn of the Metropolitan Police Service, John Salmon of Hogan Lovells and Paul Simmonds of the Global Identity Foundation.
The closing day panel, "We've Been Breached. Now What? How to Effectively Work With Law Enforcement," included, from left, Peter Yapp of the National Cyber Security Centre, Jason Tunn of the Metropolitan Police Service, John Salmon of Hogan Lovells and Paul Simmonds of the Global Identity Foundation.I walked away from the London Summit reminded of just how critical information sharing is, especially when it comes to financial cybercrime.
And I got the sense that sharing information with law enforcement is less common in the U.K. than it is in the U.S. What's more, up until recently, it's not been very common for U.K. banks to share much among themselves, either.
GDPR Provides a Boost
But information sharing in the U.K. could get a substantial boost from the General Data Protection Regulation, which takes effect in May 2018.
The GDPR sets requirements for reporting data breaches or cybersecurity incidents in Europe. In the U.K., that means notifying the newly created National Cyber Security Centre of a cyber incident within 72 hours of its occurrence.
The purpose of the GDPR is to ensure more transparency with the government on cybersecurity incidents, as well as to protect consumers' privacy.
While "information sharing" is not an explicit requirement of GDPR, the more accustomed banks and others get to sharing cyber threat details with each other and law enforcement, the easier GDPR compliance will be.
And despite the U.K.'s plans to exit the European Union, British businesses are still required to comply with GDPR. Cybersecurity attorney John Salmon, a panelist at the summit, says U.K. organizations need to start moving forward with GDPR compliance plans now and start getting used to working with the NCSC.
Another panelist at the summit, Paul Simmonds, CEO of the Global Identity Foundation, says he's glad to see the formation of the NCSC, the new lead agency for cybersecurity and incident response and investigation in the U.K. One of its first tasks is to work with the Bank of England to come up with guidelines for managing cybersecurity within the financial sector.
But Simmonds argues that the formation of NCSC comes too late. The government is stepping in to ensure more collaboration many years after cyber threats reached a tipping point, he claims.
Many of the attendees at our summit had not yet heard of the NCSC, which was just launched on Oct. 31. So when it comes to information sharing, there's clearly a need for more awareness - and lot more action.
- Details
- Category: Security News
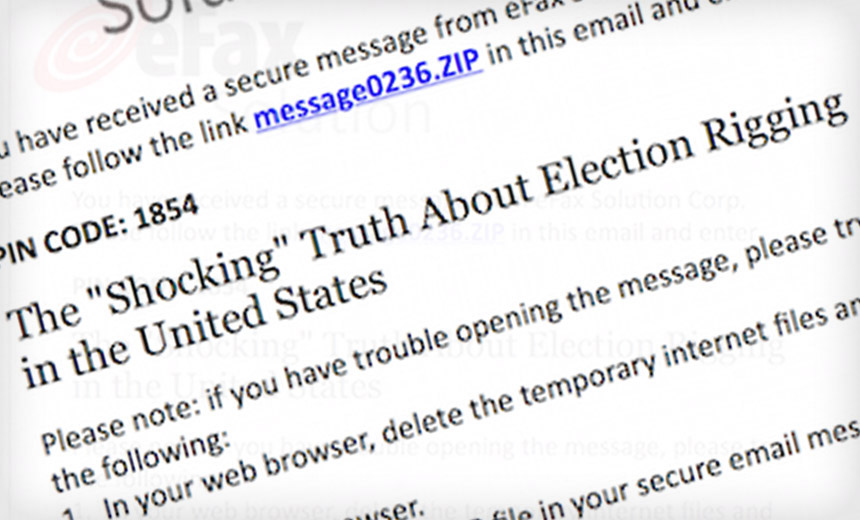 Spear-phishing message. Source: Volexity
Spear-phishing message. Source: VolexityOne of the two groups that hacked the Democratic National Committee - both believed to be operating from Russia - has been spotted lurching into action again, targeting a range of organizations and even sending fake emails bearing the Clinton Foundation name.
See Also: Managing Identity, Security and Device Compliance in an IT World
Shortly after Donald Trump became president-elect, the group that security researchers have nicknamed Cozy Bear - aka CozyDuke or APT 29 - launched a volley of malware-laced emails that targeted a range of organizations relating to national security, defense, international affairs, public policy as well as European and Asian studies, according to Volexity, a security firm based in Washington, D.C. Volexity refers to the group as "The Dukes."
"They have had tremendous success evading anti-virus and anti-malware solutions at both the desktop and mail gateway levels," writes Volexity's founder, Steven Adair, who has worked with the Shadowserver Foundation, a volunteer effort that gathers information relating to online attacks, including malware and botnets.
Cozy Bear was identified by cybersecurity firm Crowdstrike as being one of two suspected Russia-leaning groups that penetrated the DNC, later causing turmoil in the party after it released batches of emails (see DNC Breach More Severe Than First Believed).
With the 2016 U.S. presidential election over, it appears the group, which Crowdstrike suspects is affiliated with Russian intelligence, has resumed its regular operations. In the case of these attacks, the group appears to be trying to milk post-election chatter to trick people into clicking on malicious emails.
Spoofed Messages
Adair writes that Volexity has been watching Cozy Bear closely since August, when the group launched spear-phishing attacks on U.S. think tanks and other non-governmental organizations. Spear-phishing refers to attackers crafting fake emails that they send to carefully selected targets. The emails, which arrive with malicious links or attached malware, are designed to trick users into opening them, leading to attackers seizing control of the target's PC, stealing the data it stores and using it to penetrate additional networks or systems to which the endpoint connects.
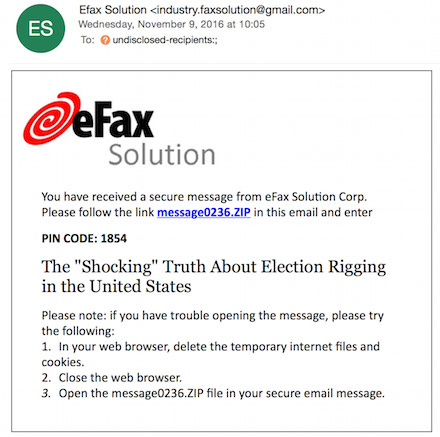 A spear-phishing email attributed to Cozy Bear by Volexity.
A spear-phishing email attributed to Cozy Bear by Volexity.In August, Volexity saw Cozy Bear send spoofed messages to victims that appeared to come from such respected groups as Transparency International, the Center for a New American Security, the Institute for Strategic Studies, Eurasia Group and the Council on Foreign Relations.
Those emails contained Microsoft Word or Excel attachments that included legitimate content. But the documents were rigged with malicious macros - a type of small application designed to enable some other kind of functionality - that downloaded a PNG image file from another server. Inside that PNG file was a backdoor hidden using steganographic techniques, which means hiding data inside another file.
The latest volley of emails, meanwhile, came from Gmail accounts created by the attackers, using what appears to have been compromised email accounts belonging to individuals within Harvard University's Faculty of Arts and Sciences. Adair notes that two of the messages pretended to have been forwarded from the Clinton Foundation, officially known as the Bill, Hillary & Chelsea Clinton Foundation.
Some of the messages sought to exploit suggestions by President-elect Donald Trump prior to the election that the process could be corrupted, sporting such subject lines as "Why American Elections Are Flawed." But Trump's surprising victory on Nov. 8 probably diminishes interest in that kind of bait, at least from his supporters.
Another email spotted by Volexity was headlined: "The shocking truth about election rigging in the United States." That sample purported to come from online fax service provider eFax. Adair writes that it included a link to a zip file with a ".lnk" Microsoft shortcut file.
"This shortcut file contains PowerShell commands that conduct anti-VM [virtual machine] checks, drop a backdoor and launch a clean decoy document," he writes.
Reminder: Email Is Dangerous
The tactics purported to be used by Cozy Bear are similar to the ones reportedly employed by its more flamboyant brother, known as Fancy Bear, to compromise the DNC and the World Anti-Doping Agency. Both breaches caused considerable embarrassment and controversy, but technologically speaking the attacks weren't sophisticated (see Hackers Dump U.S. Olympic Athletes' Drug-Testing Results).
The breaches are a reminder of this fact: Email is dangerous. If a spear-phishing email manages to pass security checks, even hardened security experts can be tricked by messages that look real or that were sent from an email account used by someone they know, but which may have been hacked.
While security software has improved, it's still a leaky defense. Accordingly, the usual advice applies: Patch regularly, run security software and if there's any whiff of doubt about an email or an attachment, don't open it.
- Details
- Category: Security News
 President-elect Donald Trump
President-elect Donald TrumpPresident-elect Donald Trump hasn't been clear about his plans for ensuring the cybersecurity of the nation's critical infrastructure, including the financial services sector.
See Also: Managing Identity, Security and Device Compliance in an IT World
But Trump's transition team has made it very clear the new administration wants Congress to dismantle the Dodd-Frank Wall Street Reform and Consumer Protection Act, which was signed into law by President Barack Obama in 2010.
Dodd-Frank, drafted in response to the 2008 financial crisis, called for, among other things, establishing the Consumer Financial Protection Bureau, a government agency responsible for protecting consumers from unfair, deceptive and fraudulent business practices.
Although Trump stated during the campaign that he would work to repeal Dodd-Frank, his specific views on dismantling CFPB are not known, USA Today reports. And CFPB's structure makes it even harder to dismantle than Obamacare, so complete elimination is unlikely, one consumer advocate told the publication.
Some fraud-prevention experts and former regulators, however, surmise that dismantling Dodd-Frank would greatly reduce the powers of the CFPB - the agency that in September led the charge to fine the country's third-largest bank, Wells Fargo, $185 million for identity theft and violating the privacy of bank customers (see Regulators Slam Wells Fargo for Identity Theft).
This week, Sen. Elizabeth Warren, D-Mass., who served as special adviser for the CFPB from 2010 to 2011, said a hard-fought battle to defend Dodd-Frank reform is likely on the horizon, Politico reports.
Dodd-Frank Law Criticized
In an August 2011 interview with Information Security Media Group, William Isaac, former head of the Federal Deposit Insurance Corp., called Dodd-Frank "the worst piece of financial legislation in history." He added: "I can tell you, if I were president, one of the first things I would do is I would send up to the Hill legislation to basically start over again on financial reform and do it right."
Isaac claimed Dodd-Frank "politicized the bank regulatory system," by keeping it "fragmented, with different people looking at different parts of things."
Some banks and credit unions have questioned the CFPB's role within the Federal Financial Institutions Examination Council. While the other FFIEC agencies oversee specific banks or credit unions, the CFPB is a watchdog over all institutions and other financial businesses, and acts more as an independent agency (see CFPB: What is New Regulator's Role?).
Michael Fryzel, former chairman of the National Credit Union Administration, says he hopes CFPB Director Richard Cordray will step down, "accepting the fact that the new president is entitled to name his own team to run the government.
"Once that takes place, I am confident President Trump will then appoint an individual to oversee a complete review of what the agency has done since its inception, what changes need to be made to make it more efficient and responsive, and conduct a comprehensive review on what regulations that are in effect or proposed need to be changed or eliminated," Fryzel adds. "The burden of excessive government and unnecessary regulation will end."
But What About Consumer Protections?
One former FDIC examiner and cyberfraud specialist, who asked not to be named, tells ISMG that the CFPB will likely be underfunded and, thus, provide limited oversight of banks. The CFPB is funded by the Federal Reserve, not Congress. But under a new administration, that built-in funding protection could be undermined, the former examiner says.
"Regulators will be ordered to ignore most of Dodd-Frank," the former examiner says. "The Fed ignored parts of Dodd-Frank already, i.e., the Durbin Amendment."
The CFPB will not be dissolved, but will linger with much less power, the former examiner predicts.
Al Pascual, head of fraud and security at Javelin Strategy & Research, says defunding the CFPB could affect how much banks scrutinize their internal practices for new account opening, which was the issue that got Wells Fargo into trouble. Wells was accused of allowing employees to access customers' personal information - and in some cases forge data - to subscribe customers to products, such as credit cards, that generated revenue for the bank and commissions for employees. Some 2 million ghost deposit and credit card accounts were opened without customers' knowledge, or through misrepresentation, according to prosecutors.
"If the threat of a similar enforcement action or settlement by regulators for unauthorized account opening was off the table, financial institutions' efforts to examine and redesign their sales-incentive and related risk-oversight programs would likely come to a standstill," Pascual says.
The CFPB could decide to slow down its reviews and investigations as a way to brace for change expected from the new administration, says cybersecurity attorney Chris Pierson, general counsel and CISO for invoicing and payments provider Viewpost.
Cybersecurity Issues
Although it seems clear the next president will support some deregulation of financial institutions, Trump's views on cybersecurity strategies are far less clear.
"As it relates to cybersecurity and privacy, the path forward is less clear because the understanding of President-elect Trump in these areas is uncertain," Pierson says. "But there are some statements or references to privacy that are more concerning regarding encryption, the Apple case and other timely topics. Similarly, responses on cybersecurity have not been too illustrative of a candidate with a solid grasp on cybersecurity or its import in 2017, and certainly remarks condoning the illegal access to private documents or other sensitive materials is reckless."
More Articles …
Page 3530 of 3545
