- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
Donald Trump pledges to conduct a review of U.S. cyber defenses and vulnerabilities as one of his first acts as president. Melissa Hathaway, who led a comprehensive review of government IT security just after Barack Obama took office nearly eight years ago, says it's crucial for an incoming president to get the lay of the land.
"It's very important for the president-elect to understand what is the state of affairs he's inheriting from President Obama," Hathaway says in an interview with Information Security Media Group. "If I were advising the president-elect, I would say that it's very important to review the current state of health of critical infrastructures."
In the interview (see audio player below photo), Hathaway:
Discusses the pre-inaugural challenge Trump faces in ramping up cybersecurity in the new administration; Addresses how Trump's cybersecurity team, when formed, will eventually develop a vision for IT defense; and Explains why the president-elect should reach out to Silicon Valley leaders to bolster government cybersecurity.As acting senior adviser to the National Security and Homeland Security councils, Hathaway led the three-month assessment in 2009 that led to Obama's Cyberspace Policy Review, which served as the basis for the administration's cybersecurity policy. She left the White House position in mid-2009, when started the cybersecurity policy consultancy Hathaway Global Strategies and joined the Harvard Kennedy School's Belfer Center as a senior adviser.
- Details
- Category: Security News
Two initiatives at the National Institute of Standards and Technology aim to close the cybersecurity skills gap in the United States.
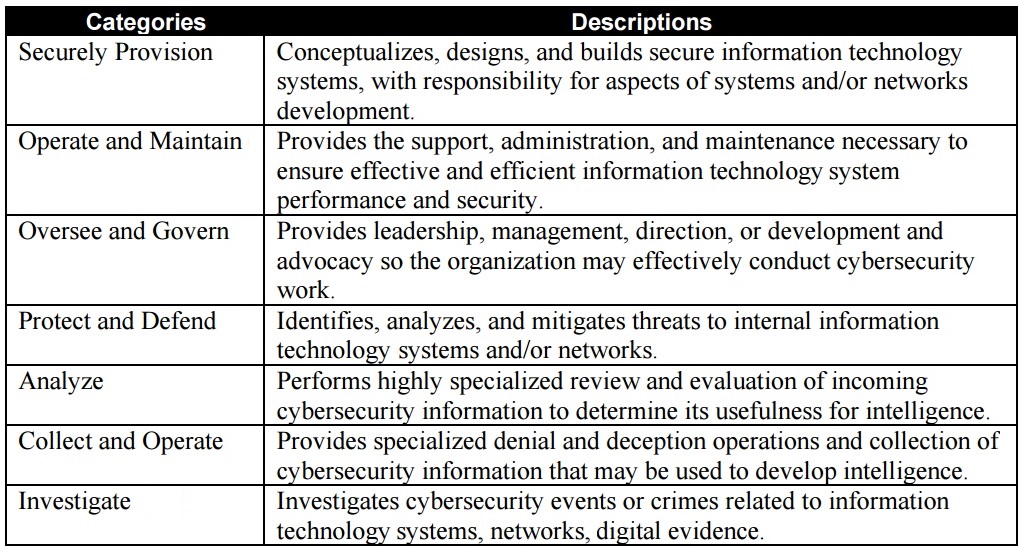
One is an interactive, online tool known as CyberSeek. The other is updated guidance known as the NICE Cybersecurity Workforce Framework, originally created four years ago by the National Initiative for Cybersecurity Education, or NICE, a public-private partnership led by NIST.
NICE Director Rodney Petersen says a synergy exists between the framework and CyberSeek. The framework defines seven broad categories of cybersecurity jobs and CyberSeek takes that information and combines it with job demand data collected by the job market analytics firm Burning Glass to create the interactive tool, Petersen explains in an interview with Information Security Media Group.
 Source: NICE Cybersecurity Workforce Framework
Source: NICE Cybersecurity Workforce FrameworkThe skills gap is immense. According to NICE, cybersecurity employment in the United States stands at more than 778,000, with the number of job openings at almost 350,000. In just one subset - information security analysts - only 88,000 positions were filled in the third quarter of 2016, according to an ISMG analysis of Bureau of Labor Statistics data (see Growth in IT Security Workforce Picks Up). Burning Glass say that's a talent shortfall of 40,000 workers.
In the interview (click on player below photo to listen), Petersen:
Discusses how the framework provides a common language in which policymakers can design programs to close the cybersecurity skills gap; Explains how different stakeholders can employ CyberSeek and the framework; and Describes the seven broad categories of cybersecurity jobs.Visibility Into Supply and Demand
CyberSeek gives policymakers, employers, security professionals and others greater visibility into the demand for cybersecurity professionals around the country, allowing them to see the skills and types of workers that employers are seeking, as well as the true supply of professionals to fill those positions.
Resembling a weather map, CyberSeek uses varying shades of color to reveal relative concentrations of cybersecurity job postings and worker supply. Users can search by state or more than 300 metropolitan areas, seeing total job openings, worker supply supply/demand ratio, a quotient for geographic concentration of workers and an area's top cybersecurity jobs by title.
Here's an example NICE provides for the Kansas City metropolitan area: CyberSeek reveals that in the past year there were 2,134 job openings and 6,829 employed workers, representing a higher-than-average cybersecurity workforce supply than the rest of the nation along with a lower concentration of cybersecurity job demand when compared with the national average. The Kansas City area's top three positions are cybersecurity analyst/specialist, cybersecurity engineer and auditor.
 Source: CyberSeek
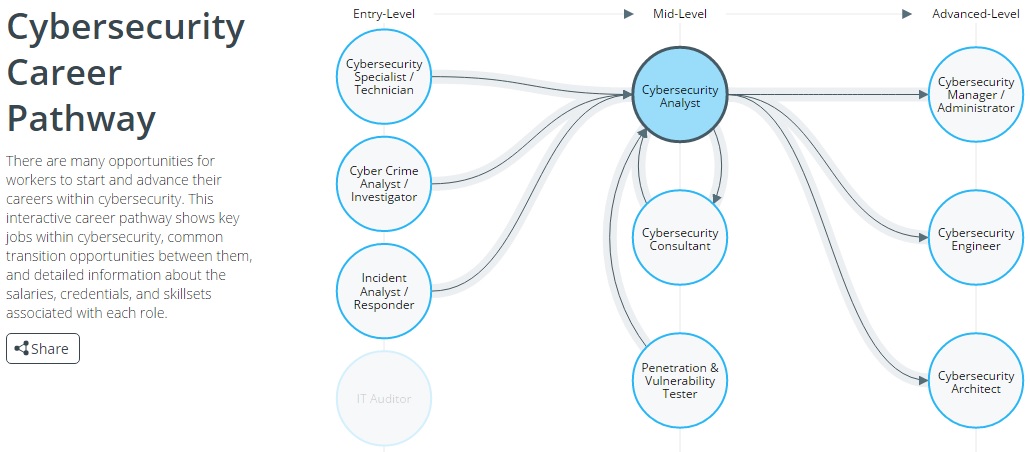
Source: CyberSeekCyberSeek also features a section titled Career Pathway, which furnishes job seekers, students and workforce trainers with information on common job titles, salaries, online job openings, in-demand skills, education and certifications related to careers in cybersecurity. It also illustrates how career advancement can move from entry-level to mid-level to advanced-level positions.
Before becoming NICE director, Petersen served as the managing director of the Washington office of EDUCAUSE, a not-for-profit association that promotes the intelligent use of information technology at colleges and universities. He founded and directed the EDUCAUSE cybersecurity initiative.
- Details
- Category: Security News
Thank Mark Zuckerberg and Kim Kardashian West for waking up the average consumer to the types of risks they face from using technology and social media, says social engineering expert Sharon Conheady.
"For the most part, if you break down the actual social engineering attacks, it's the same thing we've been seeing for years and years," Conheady says in an interview with Information Security Media Group at Black Hat Europe 2016 in London. But there was a sea change in the public's understanding of related concerns thanks, in part, to Facebook CEO Mark Zuckerberg revealing in June via Instagram that he covers his laptop webcam with tape to deter anyone who might be attempting to remotely spy on him, says Conheady, who heads London-based computer security firm First Defence Information Security.
Mass awareness was further bolstered when reality television star Kim Kardashian West was robbed at gunpoint at a luxury apartment in Paris in October. Two men dressed as police officers stole a box containing jewelry worth an estimated $6.7 million, French police say. "It was really the celebrity who was targeted, with possessions that had been seen and noticed via social media, and it was these goods that the attackers targeted," Paris police department spokeswoman Johanna Primevert told CNN following the robbery.
Kardashian West has 87 million Instagram followers and 49 million Twitter followers. Privacy is not a trait most would associate with her brand-building efforts.
Conheady says the robbery woke people up to the danger of oversharing. "Suddenly, people realized, if you post all this information on social media, it can be used against you," she says. "This is what security experts have been saying for years now."
In this interview (see audio link below photo), Conheady discusses:
The need for individuals to understand how information they share can be used against them; The danger posed by sharing or revealing metadata; The recent move by Admiral Insurance to provide discounts to first-time car owners who share access to their Facebook page with the insurer; How employees in enterprises too often reveal more than they should.In addition to leading First Defence Information Security, Conheady is also a partner in The Risk Avengers, a consultancy. She's previously served as a professional services director for vulnerability management firm Outpost24 and worked as a penetration tester for Ernst & Young, among other roles. She specializes in the human side of security and has social engineered her way into dozens of organizations, including company offices, sports stadiums, government facilities and more. Conheady is the author of Social Engineering in IT Security: Tools, Tactics, and Techniques.
More Articles …
Page 3528 of 3545
