- Details
- Category: Security News
Anti-Malware , DDoS , DDoS Attacks
Mirai Malware Is Still Launching DDoS Attacks But Code Flaws and Attack Track-Backs Could Help Battle IoT Botnets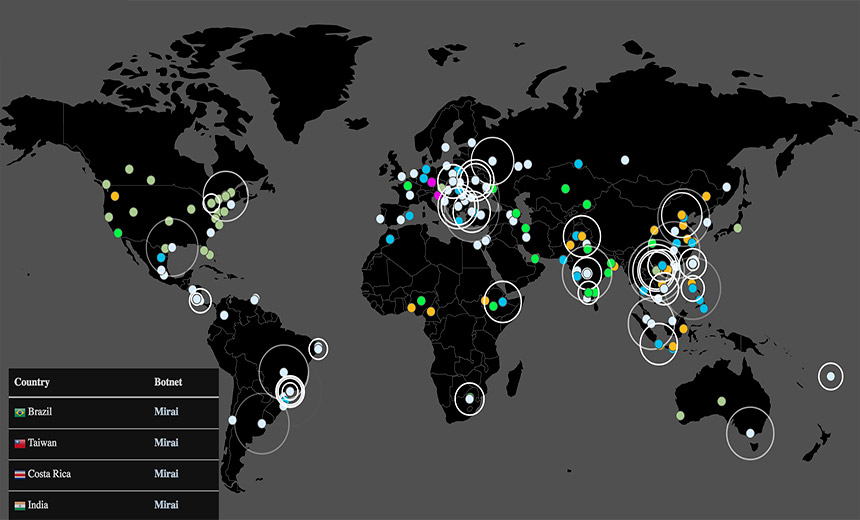 Mirai botnet tracker via MalwareTech.
Mirai botnet tracker via MalwareTech.We were promised flying cars. Instead, we get malware-infected surveillance cameras serving as remote launch pads for digital attacks that help criminals earn cryptocurrency by disrupting large parts of our global computer network.
See Also: Main Cyber Attack Destinations in 2016
The Oct. 21 IoT botnet attacks against domain name server provider Dyn, largely driven by Mirai malware, resulted in intermittent disruptions for internet users attempting to access many major sites, including Amazon, GitHub, Reddit, SoundCloud, Spotify, Tumblr and Twitter.
But that wasn't the end of DNS-targeting distributed denial-of-service attacks launched by purloined IoT devices.
The next day, Singaporean ISP StarHub's DNS services were also attacked and disrupted. And that happened again on Oct. 24.
To date, the ISP hasn't divulged what type of malware was used to target it. In addition to Mirai, Bashlite is another likely culprit. It's also not clear whether attackers might directly control the botnet or if they coughed up some bitcoins to rent someone else's stresser/booter DDoS-on-demand service.
But StarHub CTO Mock Pak Lum did say that his company traced the attacks to malware-infected IoT devices owned by its home broadband subscribers. StarHub has so far declined to tell me which malware was used, or if any of the hacked devices had been issued by the ISP to its customers.
Whether or not Mirai malware targeted StarHub, attackers are continuing to use it, according to Peter Kruse, a partner and e-crime specialist working with CSIS Security Group in Denmark.
#Mirai DDoS targets observed with in the past 24 hours. pic.twitter.com/CkgdTqlYaO
"Mirai continues to be used in a string of DDoS attacks. It may not be in the headlines but it hasn't gone away," Alan Woodward, a University of Surrey computer science professor, warns via Twitter. "Just think of all that bandwidth being used up in what is effectively friction loss," he adds.
Mirai Diversifies
Following the release of the Mirai source code last month, Mirai botnet variants in the wild are being run by multiple groups, according to a blog post from Roland Dobbins and Steinthor Bjarnason, security engineers at DDoS defense firm Arbor Networks.
"The original Mirai botnet ... currently consists of a floating population of approximately 500,000 compromised IoT devices worldwide," they say.
Thankfully, some weaknesses in the internet of things attack landscape are already starting to appear.
Scott Tenaglia, a research director at security firm Invincea Labs, reports that in Mirai, there's "a stack buffer overflow vulnerability in the HTTP flood attack code," which can be exploited to "cause a segmentation fault (i.e. SIGSEV [segmentation violation]) to occur, crash the process, and therefore terminate the attack from that bot."
In other words, one of the leading types of IoT-device-infecting malware, Mirai, has a flaw that could be targeted to crash the attack code.
Tenaglia, in a blog post, stresses that he's sharing this finding for informational purposes only. "We are not advocating counterattack, but merely showing the possibility of using an active defense strategy to combat a new form of an old threat," he says (see Could a Defensive Hack Fix the Internet of Things?).
Unfortunately, targeting buffer overflow vulnerabilities wouldn't spell the end of IoT botnets. As ransomware developers have done, IoT malware developers would likely just improve their code to remove the bugs, then keep on attacking.
Tracing Attacks Back
Another potential defense against IoT-launched DDoS attacks might be to find better ways to separate attack traffic from legitimate traffic, so that the former can be blocked while the latter still flows. And one potential aid could be identifying attack packets' origins.
On that front, researchers at the Center for IT Security, Privacy, and Accountability - CISPA - in Germany report that they've developed a technique that can mix data collected via distributed honeypots with trilateration techniques, which look at the "time to live" field in packet headers to approximate where packets originated. "If attacks abuse many honeypots at the same time, the honeypots allow measuring the path lengths between the packet origin and the various honeypot placements," the researchers write in their paper, "Identifying the Scan and Attack Infrastructures Behind Amplification DDoS Attacks," which they presented this week in Vienna at the 23rd ACM Conference on Computer and Communications Security.
Amplification attacks of the type experienced by Dyn typically begin with a scanner that conducts reconnaissance on the target, followed by attack nodes being directed against the target. The researchers, however, claim they found that their combination of techniques could be used to reliably identify the origin of DNS amplification attacks, including associated scanners, 58 percent of the time, as well as almost 100 percent of the attacking endpoints.
Tracing DDoS attacks back to their origin may give law enforcement agencies and ISPs greater impetus to at least quarantine offending devices. "We have shared our findings with law enforcement agencies - in particular, Europol and the FBI - and a closed circle of tier-1 network providers that use our insights on an operational basis," the researchers write. "Our output can be used as forensic evidence both in legal complaints and in ways to add social pressure against spoofing sources."
It's unclear if police or social pressure will help lock down hacked IoT devices. StarHub, meanwhile, tells me that it's now dispatching customer service teams to subscribers' residences to patch or otherwise deal with infected IoT devices.
Neither approach offers a full-fledged fix. But for mitigating attacks driven by botnets of IoT devices, every little bit might help.
- Details
- Category: Security News
Audit , Data Breach , Governance
Lawyers in Breach-Related Suit Argue OPM Audit Findings Are Relevant
Plaintiffs suing Anthem Inc. in the wake of a cyberattack that exposed information on nearly 80 million individuals in 2015 want a court to open the door to revealing more of the results of audits of the insurer conducted by the U.S. Office of Personnel Management.
See Also: Faster Payments, Faster Fraud?
An 827-page document recently filed in U.S. district court in Washington by attorneys representing the plaintiffs in the consolidated class action lawsuit against Anthem seeks a court order compelling OPM to produce "a small number of documents" that OPM has identified as relating to a 2013 security audit and a 2015 "follow-on audit" of the insurer's information systems.
OPM's Office of Inspector General performs a variety of audits on health insurers - including Anthem - that provide health plans to federal employees under the Federal Employee Health Benefits Program. The court filing notes that among those affected by the Anthem breach were "millions" of federal employees enrolled in health insurance offered by Anthem affiliates through FEHBP, which is administered by OPM.
The court filing notes that the OPM audit documents pertaining to Anthem, formerly known as Wellpoint, likely contain highly "probative information" related to:
The state of IT security at WellPoint/Anthem at the time of the 2013 audit and 2015 follow-on audit; The insurer's knowledge of IT security vulnerabilities; Whether the company failed to undertake measures to appropriately monitor and secure personal information; What actions the insurer took to circumvent OPM's efforts to conduct IT security audits.Such information will assist the plaintiffs in proving their claims against Anthem and other defendants in the breach lawsuit, the filing claims.
About 100 lawsuits against Anthem have been consolidated into one federal class-action case in a California, in which plaintiffs, among other things, are seeking actual and statutory damages and restitution.
Audit Requests
Anthem in 2013 refused to allow OMP OIG auditors to conduct a vulnerability test as part of a full security audit of the insurer's systems. OPM had noted that Anthem said its corporate policy prohibited external entities from connecting to the Anthem network. The insurer did, however, allow the watchdog agency to conduct an information systems general and application control audit in 2013.
Among the findings of that more general 2013 audit, OIG found that Anthem, "has established a series of IT policies and procedures to create an awareness of IT security at the plan. We also verified that [Anthem] has adequate human resources policies related to the security aspects of hiring, training, transferring, and terminating employees," according to the OIG audit report released in September 2013.
After Anthem revealed the cyberattack in February 2015, OPM OIG requested to conduct a follow-up audit of the health plan's security in the summer of 2015, but the watchdog agency was again met with resistance. OPM OIG, in a March 2015 statement provided to Information Security Media Group, said Anthem had again refused to allow the agency to perform "standard vulnerability scans and configuration compliance tests" (see Anthem Refuses Full Security Audit).
However, an OPM OIG spokeswoman on Nov. 3 told ISMG that OPM OIG did indeed conduct a narrow security audit on Anthem in 2015, following the breach. "In 2015 we went back to Anthem to conduct a limited-scope security audit where we performed additional testing. A limited-scope audit is where we intentionally look at only certain items. A scope limitation means that we were unable to conduct all work we intended," she says. "We cannot provide any additional comments due to pending litigation."
The plaintiffs' motion seeks a subpoena for the documents related to the 2015 OPM audit. The court filing also does not indicate the extent of the watchdog agency's 2015 review.
"Plaintiffs' counsel have been informed by the Department of Justice that OPM did conduct a 2015 follow-on audit and that a 2015 draft audit report was provided by OPM to Anthem in the spring 2016. The 2015 draft audit report is not privileged and plaintiffs' counsel are currently seeking production of the 2015 draft audit report from Anthem," the plaintiff's motion states.
"On October 6, 2016, the DOJ informed plaintiffs' counsel that OPM is currently administratively reviewing the 2015 final audit report to redact any confidential business information provided to OPM by Anthem and that it will be publicly releasing a redacted 2015 final audit report 'shortly.' A 2015 final audit report has not been produced in the litigation by Anthem," the plaintiffs' filing notes.
Privileged Information?
Although OPM has provided about 150 pages of various audit documents to the plaintiffs, the court filing noted that OPM was "withholding documents for which it asserted privilege and not merely because documents contained confidential information."
The plaintiffs' attorneys, argue, however, that their clients "need for the documents and the compelling interest of millions of Federal Employee Class members and 80 million affected persons is sufficient to overcome the minimal, if any, potential for harm to OPM in light of the protections already in place for the handling and use of such documents."
The court filing also notes: "The very purpose of OPM's IT security audits was ... to protect the [federal class] members from unauthorized disclosure of their personal information and to ensure they are getting state-of-the-art IT security of their personal information. ... Where those audits revealed security flaws that if timely corrected may have thwarted the massive Anthem data breach, it would be a perversion of the system to deny the victims of the data breach access to work done by OPM on their behalf."
As an alternative to OPM segregating and releasing to the plaintiffs the requested documentation related to the IT security audits of Anthem, the plaintiffs ask that OPM should instead submit the documents to the court for review, which would permit a judge to determine whether the documents should be allowed in open court.
Anthem and an attorney representing plaintiffs in the class action lawsuit did not immediately respond to ISMG requests for comment on the case.
Bad Idea?
But one legal expert argues that the release of documentation related to OPM's security audits of Anthem is a bad idea.
"I would generally be concerned about the release of any kind of audit report like this," says privacy attorney Kirk Nahra of the law firm Wiley Rein LLP. "First, it can create ongoing new security problems by revealing information. Second, any time these kinds of reports - which are designed to improve security activity - end up being used against someone - that creates terrible incentives. It will be bad for both individuals and industry if efforts to review and improve security end up being used after the fact to create problems and liability."
Public disclosure of security audit findings will also potentially "create more reasons for companies to refuse to share this kind of information with other business partners and to refuse to cooperate in efforts to evaluate security, which also creates both business tensions and additional security risks," Nahra says.
- Details
- Category: Security News
Anti-Malware , DDoS , DDoS Attacks
Volume of Infected Devices, Lack of IoT Standards Are Cause for Concern
Security experts are concerned that there may be millions of infected internet of things devices, given the intensity of recent distributed denial-of-service attacks such as the one that hit Singaporean ISP StarHub last week (see: DDoS Attacks Also Slammed Singapore ISP's DNS Services).
See Also: Avoid Theft of Your Privileged Credentials
Investigations continue to determine whether any links exist between the StarHub attacks and previous Mirai botnet assaults that hit DNS service provider Dyn on Oct. 21. The perpetrators and motives as yet remain unknown (see: Mirai Botnet Pummels Internet DNS in Unprecedented Attack).
More such attacks can be expected unless IoT device security is ramped up and standardization enforced. An attack this severe means millions of connected devices may now be outside the control of the original owners, says Pierre Noel, chief security and privacy officer at communications technology vendor Huawei. For instance, in the case of the Dyn attack alone, in a blog post following the attack, Dyn shared analysis that it had observed "tens of millions of discrete IP addresses associated with the Mirai botnet that were part of the attack."
DDoS affects two categories of users: the targets and the owners of the devices used to launch the attack. "Let's make no mistake: The problem for me is not so much DDoS on the receiving end - DDoS attacks are very well known, not very sophisticated in their nature, and can be deflected reasonably easily," Noel says. "The problem is those millions of devices that are infected, and therefore controlled by the 'bad guys.'" He says this will affect societies like Singapore that are experiencing a pervasive use of internet and technology.
StarHub Background
Following close on the heels of the Mirai botnet DDoS attack on DNS service provider Dyn, Singaporean ISP StarHub was hit by two separate DDoS attacks that affected its DNS services for several hours, bringing down its home broadband service. In a statement, StarHub said it was able to mitigate the attacks within hours and restore services on both occasions and blamed the attacks on malware-infected IoT devices owned by customers. StarHub confirmed in a follow-up statement that it would send technicians to help customers secure these devices.
However, Michael R. K. Mudd, managing partner at Hong Kong-based Asia Policy Partners, says the problem cannot be blamed on the consumer if they are buying products in good faith. StarHub shifting blame to their customers will not prevent it from happening again; customers buying a device or using a service have the reasonable expectation it will be safe, he says.
"It reminds me of Ralph Nader's expose of the 1960s U.S. car industry that were making cars the way they always had without making them safe for the new high speed freeways that had just been built. It was not the consumer's fault they were poorly engineered," Mudd says.
Mudd says he believes that a core requirement for IoT to gain widespread acceptance is that manufacturers need to build devices that are secure by design, and can be updated automatically whenever the device connects to the internet - seamlessly and without human intervention. There is a need today for a standardized enforcement mechanism for IoT - or indeed any connected device, he says (see: IoT: How Standards Would Help Security).
IoT: Security Nonexistent
Aloysius Cheang, executive vice president and managing director APAC , of the not-for-profit industry group Cloud Security Alliance, agrees that security on IoT devices is nonexistent. "The CSA had predicted this new attack vector two years ago," he says. "With number of smart devices set to hit 15.7 billion by 2018, the traditional vectors via mobile and PC combined at 10.4 billion, will pale by comparison," Cheang says, citing the 2016 Ericsson Mobility Report. "We are going to see a tsunami of attacks with similar footprint, and we are all going to be collateral damage."
While the StarHub incident may have only affected IoT devices in households, Cheang says that as connected devices increasingly find use in the enterprise, the threat will become much more relevant to enterprises. Besides, he says, many of these consumer devices such as televisions and refrigerators can also be found in offices today.
Raise Security Visibility
Tom Wills, director at Singapore-based Ontrack Advisory, agrees, saying: "More such attacks can only be expected to continue in the future, and no country on earth is immune. The StarHub incident highlights the global nature of cyber threats against operators of critical infrastructure services."
While security readiness across Asia against DDoS, data breach and other key threats varies greatly by country, in general a high state of readiness is only developed after a major incident has taken place, he says. This results in a far more costly program of security controls than would be necessary had a proactive approach been taken.
Wills advises that practitioners build adequate defenses proactively, through an continuing process of risk assessment, vulnerability scanning and penetration testing, and deployment of comprehensive enterprise security controls in line with global standards such as COBIT and ISO 27001.
"Most security practitioners are already well aware of this: The issue they face is a lack of adequate funding and top management support for their programs, without which strong security to prevent, detect and respond to the kind of incident that StarHub suffered is very difficult to put in place," Wills says, adding that security professionals should work to raise the visibility of security issues to the top management - in business terms, not technical terms.
- Details
- Category: Security News
Anti-Malware , Fraud , Phishing
Google Detailed Bugs Targeted by 'Fancy Bear' Before Windows Patch Prepped
Microsoft says a zero-day flaw in Windows that was publicly revealed by Google - before a patch was ready - was being exploited by Russian hackers via spear-phishing attacks.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
"This attack campaign, originally identified by Google's Threat Analysis Group, used two zero-day vulnerabilities in Adobe Flash and the down-level Windows kernel to target a specific set of customers," Terry Myerson, Microsoft's executive vice president of the Windows and Devices Group, says in a Nov. 1 blog post.
Attackers have been using malicious code to exploit the Adobe flaws and gain control of the browser process, exploiting the Windows kernel bug - present in Windows Vista to Windows 10 - to gain elevation of privileges, then installing a backdoor providing persistent access to the infected PC, Microsoft says.
The attacks were launched by the Russian hacking group variously known as APT28, Fancy Bear, Sofacy or Strontium, Microsoft says. Many security firms suspect the group tied to the Russian military intelligence agency known as the GRU. The group has been tied to attacks against the Democratic National Committee, amongst many others. The group's DNC attack and other hacks led the White House to formally accuse the Russian government of attempting to interfere in U.S. elections.
"Microsoft has attributed more 0-day exploits to Strontium than any other tracked group in 2016," Myerson says.
Flaw Revealed Before Patch Prepped
Microsoft says it plans to release a patch for the flaw as part of its next, regularly scheduled release of software and security updates, on Nov. 8.
"We have coordinated with Google and Adobe to investigate this malicious campaign and to create a patch for down-level versions of Windows," Myerson says. "Along these lines, patches for all versions of Windows are now being tested by many industry participants, and we plan to release them publicly on the next Update Tuesday, Nov. 8."
Google says it first alerted Microsoft and Adobe to the flaw on Oct. 21. The search giant says it gives vendors seven days to either acknowledge a flaw or release a patch, if the flaw is being targeted via in-the-wild attacks. In this case, it described the flaw as being "critical" and posing a "particularly serious" risk to users.
Adobe on Oct. 26 issued a new version of Flash that includes a patch for the exploited vulnerability, designated CVE-2016-7855. It said exploits for the flaw were "being used in limited, targeted attacks against users running Windows versions 7, 8.1 and 10."
Microsoft has continued to criticize Google for publicizing the flaw before a full Windows flaw was ready, especially since Adobe's Flash patch would have blocked this particular spear-phishing campaign.
"We believe responsible technology industry participation puts the customer first, and requires coordinated vulnerability disclosure," Myerson says. "Google's decision to disclose these vulnerabilities before patches are broadly available and tested is disappointing, and puts customers at increased risk."
The operational security expert known as the Grugq has also criticized Google's moves via Twitter. "It was absolutely critical that everyone not specifically targeted by GRU get exposed to every other threat actor instead. Disclosure works!"
He suggests the bug disclosure - before the flaw has been fully patched - would do nothing to deter the original attackers' exploits against high-value targets, while giving other attackers - intelligence agencies, cybercrime syndicates - a new tool for their attacks.
Giving everyone who isn't GRU the chance to recreate the exploit and use it before there is a patch. I feel safer already. Thanks guys!
Windows 10 Anniversary Update Blocks Exploits
One upside for anyone using the Windows 10 Anniversary Update version - released in August - together with the Microsoft Edge browser, is that they're protected against this attack campaign, even though the flaw still exists in the latest build of Windows 10, Microsoft says. "Prior to this attack, Microsoft implemented new exploit mitigations in the Windows 10 Anniversary Update version of the win32k kernel component," Myerson says. "These Windows 10 Anniversary Update mitigations, which were developed based on proactive internal research, stop all observed in-the-wild instances of this exploit."
Microsoft has used the incident to urge all Windows users to upgrade to Windows 10. "To address these types of sophisticated attacks, Microsoft recommends that all customers upgrade to Windows 10, the most secure operating system we've ever built," Myerson says. He adds that anyone who enabled the built-in Windows Defender Advanced Threat Protection feature would have enabled the OS to also detect and block related attacks.
- Details
- Category: Security News
The latest ISMG Security Report features a special report on potential cyberthreats that could damage the integrity of the U.S. presidential election. Weighing in on the issue are election security researchers Candice Hoke and Douglas Jones, human rights activist Garry Kasparov and election security author Greg Mancusi-Ungaro.
You'll also hear ISMG Security and Technology Managing Editor Jeremy Kirk analyze the damage caused by Australia's largest breach of personal information.
To listen to the ISMG Security Report, click on player beneath above image.
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Oct. 28 and Nov. 1 reports, which respectively analyze new U.S. government guidance to prevent the hacking of automotive computers and electronics and how lessons to remediate the year 2000 date problem can be applied to IT modernization. The next ISMG Security Report will be posted on Tuesday, Nov. 8.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
More Articles …
Page 3524 of 3545
