- Details
- Category: Security News
Anti-Malware , DDoS , Technology
Mirai Malware Drove Record-Breaking DDoS Attack Mirai botnet herders use malware-infected IoT components to unleash DDoS attacks.
Mirai botnet herders use malware-infected IoT components to unleash DDoS attacks.The malware-infected internet of things army that disrupted domain name server provider Dyn was composed of, at most, 100,000 devices.
See Also: Main Cyber Attack Destinations in 2016
That's the estimate from Dyn in its latest analysis of the Oct. 21 distributed denial-of-service attacks, noting that while attack traffic was massive, it's so far been unable to verify claims that the attacks peaked at 1.2 terabits per second.
Dyn's analysis has yet to be verified by external security researchers. Analysis of the attacks is complicated by the difficulty of distinguishing legitimate traffic from attack traffic.
"We saw both attack and legitimate traffic coming from millions of IPs across all geographies. It appears the malicious attacks were sourced from at least one botnet, with the retry storm providing a false indicator of a significantly larger set of endpoints than we now know it to be," says Scott Hilton, executive vice president of products for Dyn, in a blog post.
Dyn's investigation is ongoing. "We are still working on analyzing the data, but the estimate at the time of this report is up to 100,000 malicious endpoints," Hilton says. "We are able to confirm that a significant volume of attack traffic originated from Mirai-based botnets."
Full Bag of DDoS Tricks
Mirai targets dozens of different manufacturers' IoT devices and components - routers, CCTV cameras, digital video recorders and more - including items manufactured by Hangzhou Xiongmai Technology and Dahua Technology, among many others (see Mirai Aftermath: China's Xiongmai Details Webcam Recall).
But the Mirai malware is built to do much more than was seen in the assault against Dyn, based on a tear down of the malware's source code. The code was released in ready-to-compile form in September via HackForums - "a wretched hive of scum and villainy" regularly frequented by script kiddies - by a user called "Anna-senpai."
"For network layer assaults, Mirai is capable of launching GRE [generic routing encapsulation] IP and GRE ETH [Ethernet] floods, as well as SYN and ACK floods, STOMP [Simple Text Oriented Message Protocol] floods, DNS floods and UDP flood attacks," according to research published by cybersecurity and DDoS defense firm Imperva.
Retries Fueled Disruptions
Dyn's Hilton says the severity of the attack against his firm was compounded by legitimate DNS servers attempting to connect to its network, and these cascading retries contributing to further disruptions. He adds that the disruptions occurred despite some attack traffic having been scrubbed via Dyn's defense, as well as DDoS defenses employed by unnamed, upstream providers.
Some security experts say the DNS disruption was due, in part, to many Dyn customers, including PayPal, apparently not having any fallback plans if their primary DNS provider failed. Having secondary DNS providers in place is common in some industries, most notably for porn sites, and there have been signs that some of the large sites that were affected by the Dyn outage have been putting backup plans in place.
Another factor in the disruption, security experts say, were DNS amplification attacks. These remain a long-running problem. The U.S. Computer Emergency Readiness Team issued a related alert in 2013 warning that attackers could use "publicly accessible open DNS servers to flood a target system with DNS response traffic."
The US-CERT alert, revised last week, includes recommendations for free tools that can be used to scan for open resolvers so that organizations can lock them down.
Previous Attack Spotted
Imperva says that after the Mirai source code was released, it was able to look for historical Mirai-related attack activity that had targeted its network and found one such attack from August 17, which peaked at 280 gigibits per second. It said the attack was primarily launched by internet-connected CCTV cameras based in Vietnam, Brazil, the United States, China and Mexico, but added that devices based in 164 countries were seen.
Anatomy of a Mirai Botnet
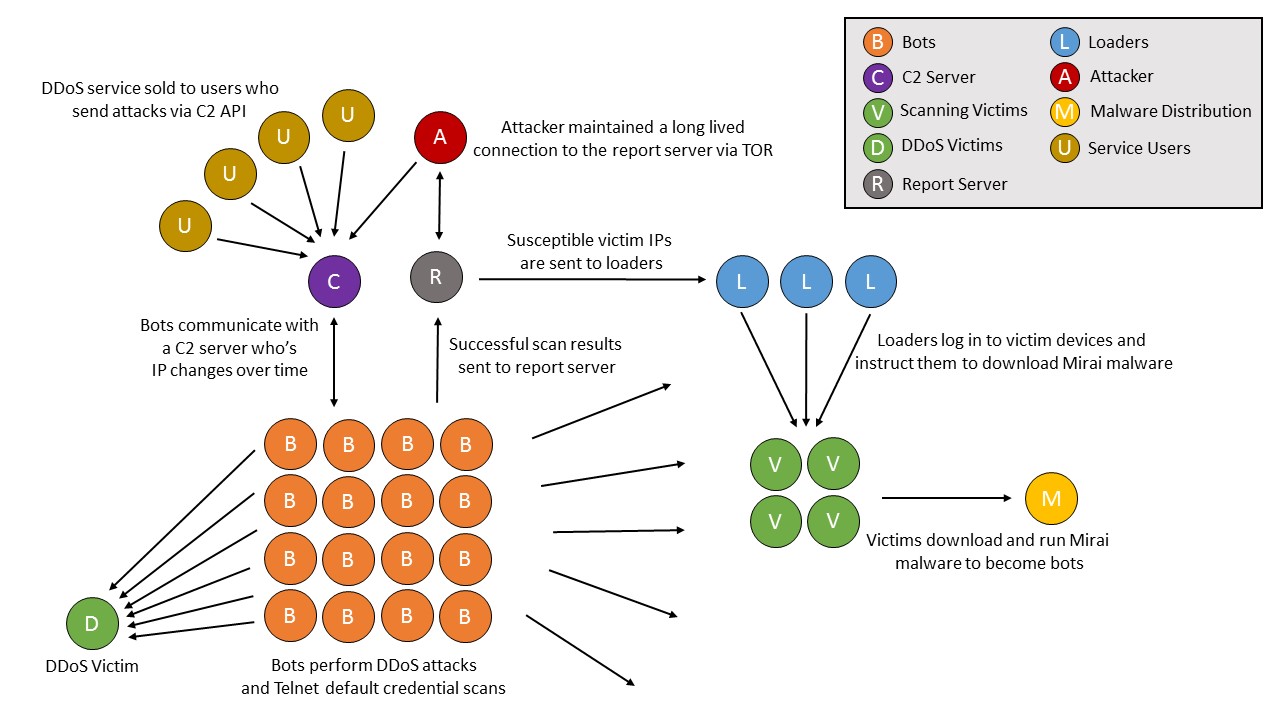 Structure of a Mirai botnet. Source: Level 3 Communications
Structure of a Mirai botnet. Source: Level 3 CommunicationsUnanswered Questions
While more details about Mirai-driven attacks continue to come to light, it's also notable which questions have yet to be answered, especially those concerning the Dyn disruption.
"With respect to our customers and the ongoing investigation, Dyn may withhold some information," Hilton says. His company has also declined to comment on the potential identity or motive of its attackers.
U.K.-based security researcher Kevin Beaumont, who's been tracking the Mirai-launched DDoS attacks, says some crucial attack-related details have yet to be made public.
Something smells around the Dyn situation and nobody confirming the bandwidth, incl the different network providers.
But he says Dyn likely doesn't want to give would-be future attackers any details on exactly how much attack volume it can - or cannot - mitigate, as well as the resiliency of its network providers.
On the upside, however, Hilton claims that Dyn is working behind the scenes "with internet infrastructure providers to share learnings and mitigation methods" in advance of what will no doubt be future, Mirai-driven attacks.
Timeline: Mirai
Aug. 17: Imperva retroactively identifies a Mirai-powered attack against a client that peaked at 280 Gbps, involving 49,657 unique IPs located across 164 countries. Sept. 19: OVH, a French ISP, is hit by a Mirai-powered attack that peaked at 800 Gbps, and which appeared to comprise 168,000 hacked devices. Sept. 20: Mirai-powered botnet hits Brian Krebs website, topping out at 665 Gbps. Sept. 30: HackForum user "Anna-senpai" releases the Mirai source code. Oct. 21: Record-breaking DDoS attack hits Dyn, which has so far declined to confirm the true size of the attack.- Details
- Category: Security News
An evaluation of new U.S. government guidance to prevent the hacking of automotive computers and electronics leads the latest ISMG Security Report.
In the report, you'll also hear (click on player to listen):
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Oct. 21 and Oct. 25 reports, which respectively analyze the likelihood of a hack to alter votes in this year's U.S. presidential election and ways to thwart massive distributed denial of service attacks. The next ISMG Security Report will be posted on Tuesday, Nov. 1.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
SecurityScorecard is out with its 2016 Healthcare Industry Cybersecurity Report, and it paints a grim picture about how vulnerable healthcare entities are to socially engineered schemes. CEO Aleksandr Yampolskiy shares insight from the study.
How low does healthcare score? Out of 18 industry sectors reviewed, healthcare placed 15 as one whose employees are most susceptible to fall for socially engineered schemes.
"This clearly suggests that there is a bigger security awareness problem among the personnel of healthcare organizations," says Yampolskiy.
Other causes for concern:
The healthcare industry falls below the industry average in six out of 10 critical security categories measured by SecurityScorecard; 63 percent of the 27 largest hospitals in the U.S. received a letter grade of C or lower for prompt patching of IT systems. Healthcare IoT devices - including patient medical devices - are particularly vulnerable to malware infection."We've seen all kinds of endpoints, including the IoT devices, emanating signatures of malware because they were infected," Yampolskiy says. "The bad guys are going to compromise those devices more and more, and the healthcare sector is very much affected."
In an interview about the 2016 Healthcare Industry Cybersecurity Report, Yampolskiy discusses:
Key findings from the study; How healthcare entities are responding to their unique security challenges; How SecurityScorecard helps organizations understand and improve their security posture.Yampolskiy is the co-founder and CEO of SecurityScorecard, the leading security ratings and continuous risk monitoring platform. SecurityScorecard actively monitors over 100,000 companies, 200% more than any other security rating service. Nearly 200 enterprises rely on SecurityScorecard to monitor third party risk.
Previously he was a CTO of Cinchcast and BlogTalkRadio. BlogTalkRadio is the largest online radio network averaging over 40 million visitors a month. Prior to Cinchcast, Alex was Head of Security and Compliance at Gilt Groupe companies, responsible for all aspects of IT infrastructure security, secure application development, and PCI compliance.
Before that he worked at Goldman Sachs, Oracle, and Microsoft, where he was a lead technologist building large scale, enterprise software focused on IDM, SSO, authentication and authorization. He's been cited in New York Times, ComputerWorld, Observer, and other media. He's a published author and speaks regularly on security and software development processes.
- Details
- Category: Security News
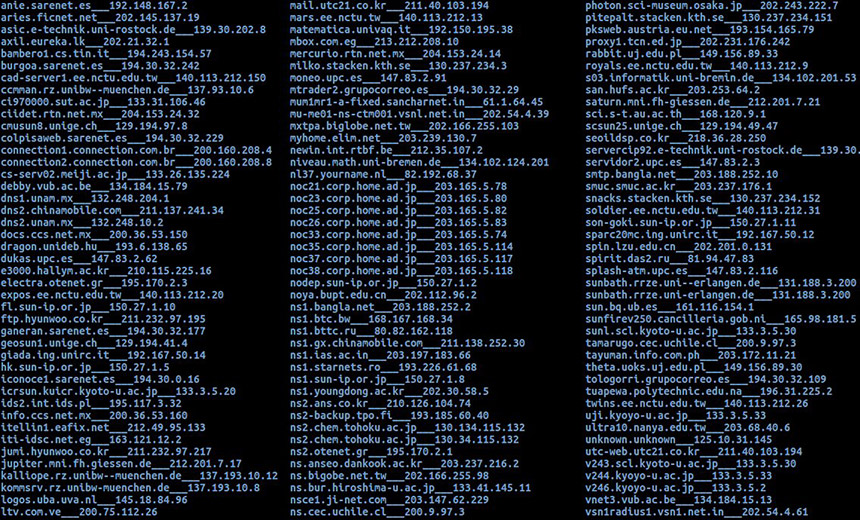 The latest Shadow Brokers leak lists alleged NSA staging servers.
The latest Shadow Brokers leak lists alleged NSA staging servers.The Shadow Brokers - the group that released what are purported to be hacking tools tied to the U.S. National Security Agency - is back with what it claims to be a list of exploit-staging servers that were hacked by the agency and used to launch online attacks over the course of a decade. The group labels the Oct. 31 data dump as a "special trick or treat for Amerikanskis."
See Also: Main Cyber Attack Destinations in 2016
It's the group's first release of material since Aug. 13, when it dumped exploits and software implants that it said came from the Equation Group, which is the nickname for an advanced hacking group that experts say is likely the NSA's Tailored Access Operations team (see Confirmed: Leaked Equation Group Hacking Tools Are Real).
The leak contains a list of systems in 49 countries, according to an analysis by U.K.-based cybersecurity firm Hacker House. The greatest numbers of compromised servers are located in China, Japan and South Korea.
Security experts say the NSA's TAO launches operations from compromised servers to help mask its activities. Experts have theorized that the Shadow Brokers' first leak came from such a server, and that it either hadn't been scrubbed after an operation or had already been hacked when the agency first began using it.
The latest data dump, which contains 306 domain names and 352 IP addresses, will give affected network operators good reason to conduct further digital forensic investigations.
"These hosts may still contain forensic artifacts of the Equation Group APT group and should be subject to incident response handling procedures," Hacker House writes.
The Shadow Brokers imparted a warning to people doing that kind of analysis, writing that infected computers had rootkits, which is the term for hard-to-detect malware deeply embedded in an operation system. It claimed the rootkits "will self destruct." The group may be referring to capabilities built within a rootkit to erase itself before discovery. The Shadow Brokers cautioned that investigators should create a "cold forensic image" of any computer before subjecting it to analysis, to preserve an undamaged copy of its contents.
Expert: List Looks Legit
Multiple security experts, including Mustafa Al-Bassam, who has been cataloging alleged Equation Group "exploits, implants and tools for hacking firewalls" that have been released by the Shadow Brokers, believes the latest information is tied to NSA operations.
New Shadow Brokers dump contains list of servers compromised by the NSA to use as exploit staging servers. pic.twitter.com/rVNjWCvgoG
— Mustafa Al-Bassam (@musalbas) October 31, 2016The latest Shadow Brokers leak, however, appears to be quite old. The most recent time stamps on some of the systems date from 2010, while some stretch back to 2000. It's unlikely that many of the systems are still in the same state, Vitali Kremez, a senior cybercrime intelligence analyst with security intelligence firm Flashpoint, tells Information Security Media Group.
In an analysis of the latest dump, meanwhile, Kremez highlights the apparent age of the information contained in the leak. "This is almost like looking at dinosaur remnants," he writes.
More Setbacks for the NSA?
If the list is genuine, it would mark another setback for the NSA, which has been grappling with damaging leaks. The arrest of Booze Allen Hamilton contractor Hal Martin in August marked the second time since Edward Snowden that the NSA has faced a large leak of internal data (see NSA Contractor's Alleged Theft 'Breathtaking').
Martin, 51, is alleged to have hoarded terabytes of highly classified material in his car and house. Martin allegedly also possessed some of the same information released by the Shadow Brokers, The New York Times has reported. But it is unclear if he is connected with the group and if the overlap in material is merely coincidence.
The Shadow Brokers has continued to issue new blog posts following Martin's arrest. In announcing the latest leak, the group attempts to address tensions between the United States and Russia over the latter's alleged interference with the presidential election, but in a seemingly nonsensical manner. The poor grammar and syntax of the Shadow Brokers' writings, however, have led some security experts to speculate that the writer might be a native English speaker attempting to appear to be a non-native speaker by making intentional errors.
"Why is DirtyGrandpa threating CIA cyberwar with Russia?" the group writes. It's not clear what the group means with the name DirtyGrandpa.
The United States believes Russia is responsible for hacking the Democratic National Committee and compromising email accounts of high-profile officials. Despite compelling circumstantial evidence, Russia has dismissed the accusations.
New Hacking Toolkits?
The Shadow Brokers dumps have provided security experts with a trove of information into what appear to be at least one intelligence agency's historical attack capabilities, with earlier dumps revealing previously unknown zero-day flaws in Cisco networking gear, which the manufacturer has been patching.
The latest data dump, meanwhile, includes information related to how those tools were likely used. The data includes domain names, IP addresses, the operating systems of the compromised systems as well as related time stamps, which range from 2000 to 2010. Most of the systems were running a version of Sun's Solaris, which is a Unix-based operating system. Other details include names - Dewdrop, Incision, Jackladder, Orangutan, Patchicillin, Stoicsurgeon, Reticulum - that appear to refer to hacking toolkits.
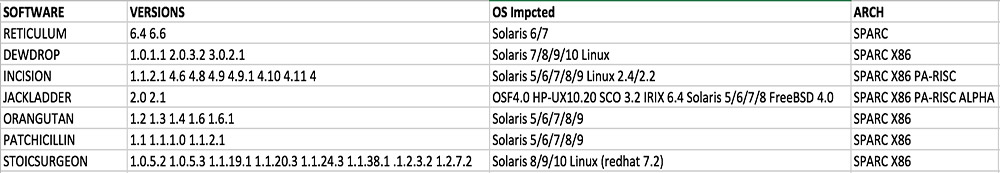 The latest Shadow Brokers data dump includes a list of apparent attack tools. Source: Hacker House.
The latest Shadow Brokers data dump includes a list of apparent attack tools. Source: Hacker House.The Shadow Brokers' post described one such likely tool, called Pinchimpair, as a redirector tool. Hacker House writes that the redirector might be a backdoor or implant that is used for tunneling attacks.
The toolkits appear to not have been publicly named before, and thus it is possible the related attacks may still be ongoing, Hacker House writes. Notably, the company conducted a search using Shodan, which indexes internet-connected devices, and found that some of the domains listed in the leak are still active as well as running the same software listed in the leak. As a result, they would likely still be vulnerable to whatever methods were first used to allegedly compromise them.
"It is strongly advised that if you or your organization are amongst the impacted parties, you perform incident response on identified hosts, and contact security professionals to help determine [the] impact on your network," Hacker House writes. "You may have inadvertently been hosting Equation Group APT cyber attacks from your environment."
While the Shadow Brokers leaks have been continuing, some of what the group has promised to do has yet to materialize. After the group's first release, in particular, it promised to auction the password for a second, encrypted file. The Shadow Brokers said they would release the password to the archive if they received 1 million bitcoins. But that improbable sum that has yet to materialize.
- Details
- Category: Security News
Anti-Malware , DDoS , DDoS Attacks
Notorious Hack Forums Blocks Offerings, But Cybercrime Services Surge On The 19-year-old administrator of Titanium Stresser recently pleaded guilty to related computer crime charges.
The 19-year-old administrator of Titanium Stresser recently pleaded guilty to related computer crime charges.The administrators and enablers of so-called stresser/booter services may be feeling some heat.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
Such services are often marketed as tools for stress-testing one's website by providing on-demand distributed denial-of-service attacks. But the tools have long been used by individuals who want to disrupt others' websites, and cybercrime experts say they can be a source of easy money for unscrupulous developers and administrators.
In a sign that investigators are paying more attention to disrupting stresser/booter services, the notorious Hack Forums, a site that security experts say caters especially to script kiddies and cybercrime wannabes, recently announced that it will be shutting down its Server Stress Testing forum.
"Unfortunately once again the few ruin it for the many. I am sure this is going to upset some members but also please many, some of whom aren't even members," site admin Jesse "Omniscient" LaBrocca said in an Oct. 28 post. "I'm personally disappointed that this is the path I have to take in order to protect the community. I loathe having to censor material that could be beneficial to members. But I do need to make sure that we continue to exist and given the recent events I think it's more important that the section be permanently shut down."
 Hack Forums announced Oct. 28 that it would no longer allow information relating to stresser/booter services to be posted.
Hack Forums announced Oct. 28 that it would no longer allow information relating to stresser/booter services to be posted.What is yet to be seen, however, is if the move by Hack Forums leads to any reduction in on-demand DDoS attacks (see Cybercrime-as-a-Service Economy: Stronger Than Ever).
On-demand DDoS attacks can be tough to trace, especially if service operators use infected endpoints to launch their attacks. To date, for example, it's unclear if the record-setting DDoS attacks tied to infected internet of things devices - and IoT malware such as Mirai - have been launched by stresser/booter services. But historically, cybercriminals have only infected large numbers of IoT devices to monetize their efforts by offering on-demand DDoS attacks.
Recently, however, there have been a number of arrests of alleged stresser/booter operators. In September, for example, two 18-year-old men - Itay Huri, a.k.a. "P1st" and "M30w," and Yarden Bidani, a.k.a. "AppleJ4ck" - were arrested in Israel at the FBI's request in connection with an investigation into the vDos site, which provided DDoS attacks on demand.
"Based on a subscription scheme, starting from $19.99 per month, tens of thousands of customers paid more than $600,000 over the past two years to vDos," according to a new DDoS attack trends report released by Moscow-based security firm Kaspersky Lab. "In just four months between April and July, vDos launched more than 277 million seconds of attack time, or approximately 8.81 years' worth of attack traffic," it adds.
Europol Sees DDoS Threat
The threat posed by stresser/booter services was cited in the Internet Organized Crime Assessment for 2016, published in September by the EU's law enforcement intelligence agency Europol, as one of the top cybercrime challenges that police are currently battling.
"DDoS attacks continue to grow in intensity and complexity, with many attacks blending network and application layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an increasing number of DDoS attacks." Such services are often also used to extort victims.
The problem is international in scope. Kaspersky Lab says that from July to September, the top countries hosting victims targeted by DDoS attacks were China, the United States and South Korea. It said SYN floods remain by far the most prevalent type of DDoS attack.
DDoS Attacks: Most-Targeted Countries
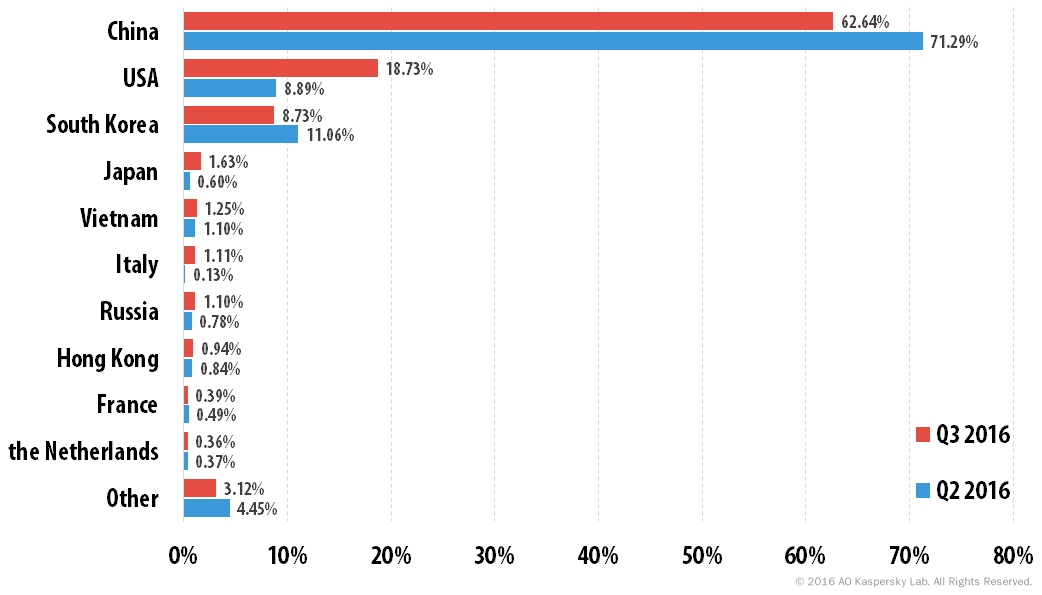 Distribution of unique DDoS attack targets by country, Q2 2016 vs. Q3 2016 (source: Kaspersky Lab).
Distribution of unique DDoS attack targets by country, Q2 2016 vs. Q3 2016 (source: Kaspersky Lab).Related Arrests Continue
But Europol says related DDoS-disruption efforts are underway. "Providers are taking more responsibility for the security and health of their own networks and services," according to the IOCTA report. In addition, "ISPs are actively detecting and filtering DDoS attacks, implementing standards such as BCP38 to reduce IP spoofing, detecting fraudulent logins and other malicious activity."
Law enforcement agencies are also continuing to investigate stresser/booter services as well as their users. But security experts say such efforts are complicated in part by the relative ease with which such services can be designed, hosted or procured, as well as the criminal profits to be made by running a stresser/booter service.
Last year, for example, as part of "Operation Vivarium" British police arrested four individuals - a 15-year-old, 16-year-old and two 18-year-olds - on suspicion of having used the Lizard Squad's Lizard Stresser DDoS-on-demand service. Police said the suspects bought attack time "using alternative payment services such as Bitcoin in a bid to remain anonymous."
Previous stresser/booter arrests - including suspected ringleaders behind the Lizard Squad group - in some cases revealed that they too were, legally speaking, only children, at least when they first designed and began selling such services.
Titanium Stresser Admin Pleads Guilty
The same is true for 19-year-old Adam Mudd in England, who ran "Titanium Stresser," a service that police say was tapped by international users to launch 1.8 million attacks over two years.
On Oct. 21, Mudd pleaded guilty at the Central Criminal Court of England and Wales in London - better known as the Old Bailey - to three related charges: two counts of computer misuse, related to creating and administrating his stressor tool; and one count of money laundering in relation to financial gains made via his stressor tool being used by others. He also admitted to attacking his old college - as a pupil studying computer science - while testing his tool.
According to England's Eastern Region Special Operations Unit, Mudd earned more than £300,000 ($365,000) before he turned 18 years old, and allege that from September 2013 until March 2015, his service was used to launch 1.8 million attacks. Prosecutors said in court that he first developed the software when he was only 15 years old, and that he used it himself 594 times against 181 individual IP addresses, employing the username "themuddfamily," Britain's Evening Standard reports, adding that the service logged every attack - and related username - that it launched.
Lizards Learned from Mudd
They also said that Mudd's software was copied by the Lizard Squad, becoming the basis for its Lizard Stresser service.
Mudd has been freed on bail - on condition of not using any internet-connected devices - until Dec. 16, when he faces sentencing, and Judge Michael Topolski indicated that he might serve time in a young offenders' institution, Evening Standard reports. It adds that Mudd's attorney, Ben Cooper, told the court that his client has been diagnosed as autistic, is currently undergoing psychological evaluation, lives with his parents and works as a hotel porter.
"Adam Mudd's case is a regrettable one, because this young man clearly has a lot of skill, but he has been utilizing that talent for personal gain at the expense of others," Detective Inspector Martin Peters, head of the Eastern Region Special Operations Unit's cybercrime team, which arrested Mudd, said in a statement issued after the suspect pleaded guilty.
"We want to make clear it is not our wish to unnecessarily criminalize young people, but want to harness those skills before they accelerate into crime," Peters added.
More Articles …
Page 3522 of 3545
