- Details
- Category: Security News
DDoS , Endpoint Security , Risk Management
But True Fix Requires a More Resilient Internet, Experts Warn Detail of an IoT component manufactured by Xiongmai
Detail of an IoT component manufactured by XiongmaiChinese manufacturer Hangzhou Xiongmai Technology will recall up to 10,000 webcams in the wake of massive distributed denial-of-service attacks driven, at least in part, by infected internet of things devices, Reuters reports.
See Also: Secrets to a Simpler Security Incident Response
The DDoS attacks targeted domain name server provider Dyn on Oct. 21, resulting in widespread website access disruptions. Affected sites ranged from Amazon, GitHub and Netflix to PayPal, Reddit and Twitter. Security researchers say the attacks were driven, at least in part, by Mirai malware, which targets default and hardcoded credentials in dozens of types of IoT devices. The source code for the malware was released last month.
Some - but far from all - of the devices targeted by Mirai included IoT components manufactured by Xiongmai. As a result, the company promised to recall some webcams, but only in the United States.
Now, Liu Yuexin, Xiongmai's marketing director, tells Reuters that the company has fixed the firmware used in components that it supplied to manufacturers this year and last. He said that the company will recall surveillance cameras in the United States for which updated firmware couldn't be installed, which he estimated numbered fewer than 10,000 vulnerable devices.
But it's not clear if Xiongmai's post-Mirai reaction plan will have any demonstrable effect. Xiongmai officials have previously claimed that, in 2015, the company updated its firmware to deactivate telnet by default, as well as to prompt users to change the default username and password. The company says the updated firmware has been made available for downloading from its site.
Some security experts, however, have questioned Xiongmai's claims. "The Mirai botnet is exploiting a 'backdoor' password that cannot be changed," Johannes Ullrich, dean of research for the SANS Technology Institute, says in a recent SANS Institute newsletter. "Only a firmware update will help. Right now, I don't see the firmware update available from [Xiongmai]."
But he adds that the manufacturer is far from the only IoT device maker to include hardcoded passwords in its components (see IoT Botnets: There Will Be Pwnage).
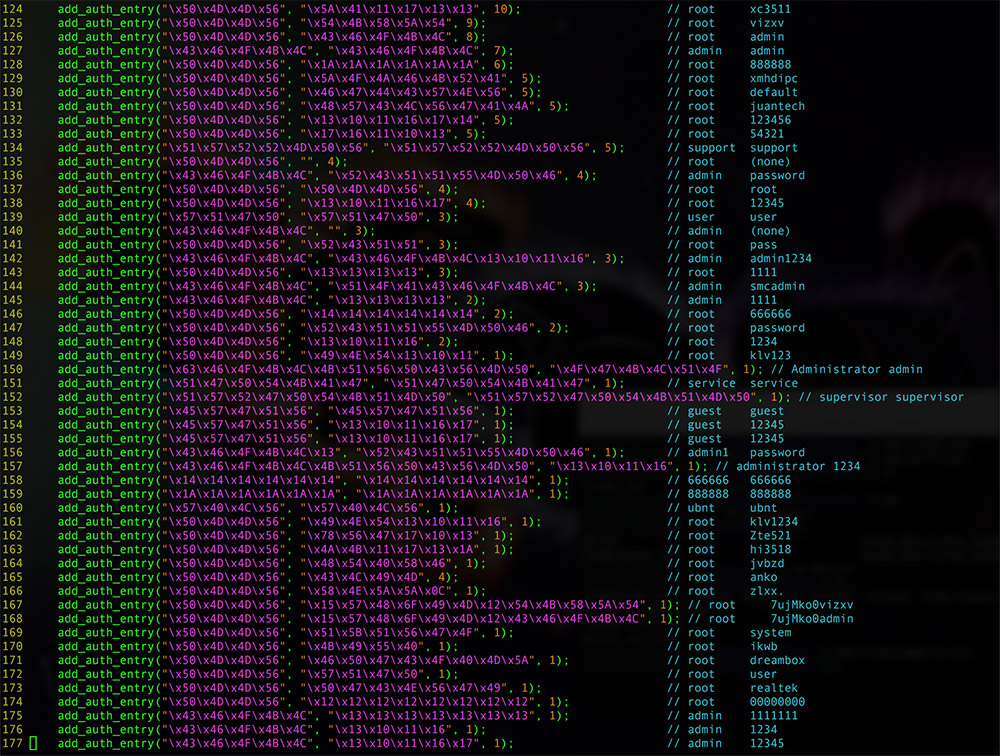 The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components.
The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components."While [Xiongmai] was somewhat singled out in this event, many other devices suffer from hardcoded 'backdoor' or 'support' passwords that the user cannot change," he says. After attackers begin targeting these hardcoded passwords, he adds, rather than removing them entirely, manufacturers often just update firmware with "a different password instead of eliminating this function."
Mounting Evidence: No Nation-State Attacker
To date, it's not clear who launched the DDoS attacks against Dyn, how many botnets might have been used, whether all of the attacks were enabled via IoT devices infected by Mirai or other malware, or if DDoS-on-demand stresser/booter services were also brought to bear.
The U.S. Department of Homeland Security is investigating the attacks, as well as "working with law enforcement, the private sector and the research community to develop ways to mitigate against [Mirai] and other related malware."
Sen. Mark Warner, D-Va., who heads the Senate Cybersecurity Caucus, has also written letters to DHS, the Federal Communications Commission and the Federal Trade Commission querying what tools and tactics are available to battle IoT malware - and which new ones the agencies might want to see get developed.
"The weak security of many of the new connected consumer devices provides an attractive target for attackers, leveraging the bandwidth and processing power of millions of devices, many of them with few privacy or security measures, to swamp internet sites and servers with an overwhelming volume of traffic," Warner says in a statement. "I am interested in a range of expert opinions and meaningful action on new and improved tools to better protect American consumers, manufacturers, retailers, internet sites and service providers."
Asking @FCC @FTC @DHSgov to look look into the #zombie #cyber attacks that swamped popular sites. https://t.co/RuG3dgabBY
Not Suspected: Nation-State Attackers
As Information Security Media Group has previously reported, security experts say the DDoS attacks against Dyn were likely launched by attackers who are also gamers, in part because the attacks were announced in advance as targeting the launch of a new Electronic Arts game. That implies that the attackers are relatively young men with no particular agenda to advance, except perhaps advertising their own stresser/booter services.
Supporting evidence for that theory continues to mount. Speaking at the Council on Foreign Relations in New York on Oct. 25, National Intelligence Director James Clapper said early indications are that the DDoS attack against Dyn were launched by a "non-state actor," the Associated Press reports.
Security intelligence firm Flashpoint, meanwhile, says that the release of the Mirai source code and related chatter on the script-kiddie forum known as HackForums suggest that individuals with an interest in stresser/booter services might have been involved in the Dyn disruptions.
"The technical and social indicators of this attack align more closely with attacks from the Hackforums community than the other type of actors that may be involved, such as higher-tier criminal actors, hacktivists, nation-states and terrorist groups," Flashpoint researchers say in a blog post. "These other types of threat actors are unlikely to launch such an attack without a clear financial, political or strategic objective, and they are very unlikely to launch an attack against a video game company."
Required: More Internet Resiliency
The internet disruptions triggered by IoT-powered DDoS attacks against Dyn are far from the first time that attackers have marshaled infected IoT devices to do their bidding.
"This issue highlights a bigger problem that I feel is often overlooked with IoT," information security consultant Brian Honan, who is a cybersecurity adviser to the EU's law enforcement intelligence agency Europol, writes in a recent SANS Institute newsletter. "We struggle to convince companies and individuals to keep their PCs patched. This is going to be a bigger challenge in IoT. We need to make the internet more resilient as more and more of these devices will become security threats over time."
With luck, the attacks against Dyn will serve as a wake-up call for the industry, says Dan Kaminsky, chief scientist at anti-malware firm White Ops.
"Nothing survives floods of this nature, existing or theoretical, centralized or decentralized," Kaminksi tells The Guardian. "It all falls over. The hard questions here are about preventing this sort of exposure in the first place, and about improving our ability to respond and remediate when we do get it wrong."
"DNS sucks!"
"And what would you replace it with?"
And that's when the Ninja Smoke Bombs come out. *whoosh*
But massive outages often focus attention on developing and implementing fixes, says Kaminsky, who in 2008 discovered - and single-handedly patched - a serious flaw in DNS. "The unifying principle of the internet is reliability, and systems went down," he said. "That tends to cause improvement. 'If we don't do this, bad things will happen' is not as compelling as 'if we don't do this, bad things will happen again.'"
- Details
- Category: Security News
Application Security , Breach Preparedness , Cybersecurity
2 Senators Say Guidelines Don't Go Far Enough, Seek Regulations Cover of NHTSA's new auto cybersecurity guide.
Cover of NHTSA's new auto cybersecurity guide.Stopping well short of issuing regulations, the U.S. federal government is proposing voluntary cybersecurity guidelines aimed at getting carmakers and their suppliers to secure computers and electronics in automobiles.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
The proposed guidance from the Transportation Department's National Highway Traffic Safety Administration, Cybersecurity Best Practices for Modern Vehicles, focuses on hardening a vehicle's electronic architecture against potential cyberattacks and ensuriing vehicle systems take appropriate actions even if an attack succeeds.
Hackers' Points of Entry
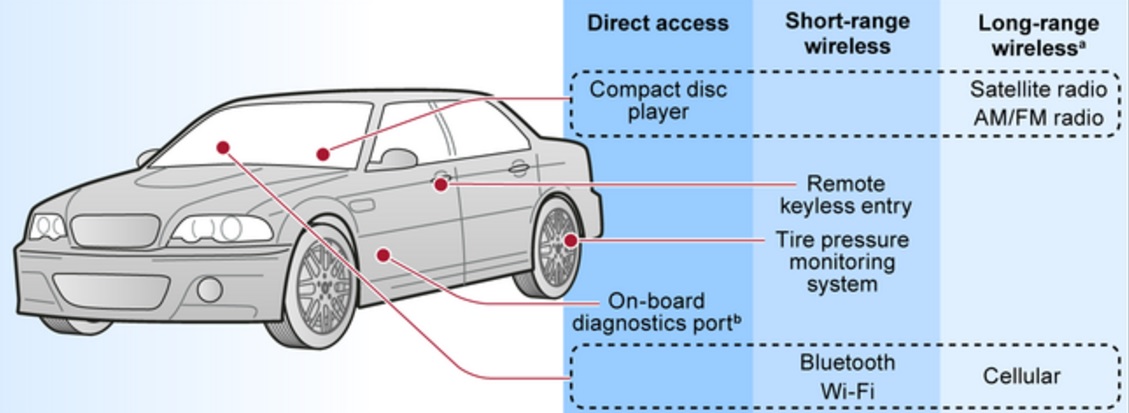 Source: Government Accountability Office
Source: Government Accountability Office"In the constantly changing environment of technology and cybersecurity, no single or static approach is sufficient," NHTSA Administrator Mark Rosekind says. "Everyone involved must keep moving, adapting and improving to stay ahead of the bad guys."
Layered Approach
The guidelines offer a layered approach to cybersecurity, which NHTSA contends would reduce the possibility of an attack's success and mitigate the ramifications of potential unauthorized access to a vehicle's computerized systems.
NHTSA says a layered method should:
Incorporate a risk-based approach to security that protects the vehicle's control systems and safeguards personally identifiable information contained in automotive systems; Provide for timely detection and rapid response to potential vehicle cybersecurity incidents; Include measures to facilitate rapid recovery from incidents when they occur; and Institutionalize methods for accelerated adoption of lessons learned across the industry through effective information sharing, such as through participation in the Automotive Information Sharing and Analysis Center.Mandatory Standards Sought
But the voluntary approach to implementing automotive cybersecurity standards didn't please two Democratic senators, Edward Markey of Massachusetts and Richard Blumenthal of Connecticut. "This new cybersecurity guidance from the Department of Transportation is like giving a take-home exam on the honor code to failing students," the senators say in a joint statement. "If modern day cars are computers on wheels, we need mandatory standards, not voluntary guidance, to ensure that our vehicles cannot be hacked and lives and information put in danger. In this new internet of things era, we cannot let safety, cybersecurity and privacy be an afterthought."
In the current Congress, both lawmakers introduced the Security and Privacy in Your Car Act, or the Spy Car Act, to require auto manufacturers to equip cars for sale in the U.S. "with reasonable measures to protect against hacking attacks." The legislation would require vehicles to be armed with the capabilities to immediately detect, report and stop attempts to intercept driving data or control of the vehicle.
But the bill is unlikely to get out of committee this year, let alone come up for a vote. Lawmakers and the Obama administration have been reluctant to issue cybersecurity regulations, and no groundswell exists in Washington to mandate automotive security standards. Instead, most lawmakers favor a voluntary collaborative approach between government and business to develop security standards. "These best practices, coupled with the continued partnership of government, academia, industry, security researchers and consumer groups, is a critical element of getting these technologies ready for our roads in the safest and securest manner possible," says Sen. Gary Peters, D-Mich., co-founder of the Senate Smart Transportation Caucus.
Regs Seen Stymieing Innovation
One automotive industry observer says the time isn't right for mandatory standards. "The technology is still in the process of developing, figuring out what is the best way to do this, how to address the problem of automotive security," says Sam Abuelsamid, senior research analyst at Navigant Research, a market research consultancy. "If we were to try and put a more solid regulation in place right now, it could stymie the development of some ideas."
Still, Abuelsamid says he could forsee the government requiring the auto industry to employ third-party auditors to review the software and architecture developed to secure vehicles. Cars and trucks contain much more code than other types of vehicles. According to the Battelle Memorial Institute, the not-for-profit research organization, a luxury sedan could contain more than 100 million lines of code; that's about 15 times more code than needed to operate systems in a Boeing 787 Dreamliner.
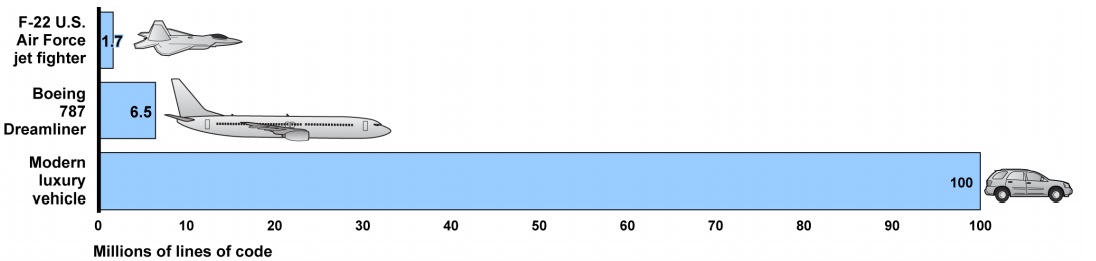 Source: Battelle
Source: Battelle
"A separate set of eyes are needed to look at the code for potential vulnerabilities because the people creating them tend not to see those [weaknesses]," Abuelsamid says. "Requiring some sort of process that includes third-party validation is probably a good thing."
The threat of cyberattacks on automobiles is real. So far, though, attacks have occurred in laboratory-type settings. For instance, Chinese researchers earlier this year remotely turned on the windshield wipers, opened a trunk and applied the brakes of a Tesla Model S sedan (see Tesla Patches Cars Against Wi-Fi 'Braking' Attack ).
In 2015, two hackers remotely triggered a 2014 Jeep Cherokee's brakes on a California highway. Also in 2015, the NHTSA issued a recall of 1.4 million Chrysler automobiles equipped with radios that have software vulnerabilities that could allow third parties access to networked vehicle control systems. "Exploitation of the software vulnerability may result in unauthorized remote modification and control of certain vehicle systems, increasing the risk of a crash," the recall notice states.
Future Prospects
In a report issued earlier this year by the Government Accountability Office, federal examiners contend a cyberattack on automobiles isn't imminent, but remains a possibility in the not-too-distant future. "To say that it hasn't happened in the past doesn't mean that it couldn't happen, because there are an awful lot of things that we didn't see happening in the past that have happened," says David Wise, GAO physical infrastructure issues director (see An In-Depth Analysis of How Automobiles Can Be Hacked).
If and when hackers begin to breach automotive IT systems, they'll likely seek profit over creating havoc on the highways. "There's probably going to be more attackers that are interested in trying to make money off of it," Abuelsamid says. "Ransomware and data theft are probably the two most likely scenarios. For the most part, most hackers are interested in making some money off of whatever [they're] doing."
- Details
- Category: Security News
DDoS , Governance , Incident Response
Child Custody Case Allegedly Triggered Attacks in the Name of Anonymous
The hacktivist who allegedly launched distributed denial-of-service attacks in 2014 on Children's Hospital of Boston and another local healthcare facility in protest of a controversial child custody case has been indicted on federal charges.
See Also: Protect Your Microsoft Identity Infrastructure
Martin Gottesfeld, a 32-year-old biotech professional from Somerville, Mass., faces up to 15 years in federal prison if convicted on one count of conspiracy and one count of intentional damage to a protected computer. He'll be arraigned Oct. 26 in the U.S. district court in Boston.
Attorney Tor Ekeland, who is representing Gottesfeld in the case, tells Information Security Media Group that his client is being detained in a Rhode Island facility. The attorney, who says he expects the case will proceed to trial, had no comment about a Sept. 18 statement Gottesfeld provided the Huffington Post about "why I knocked Boston Children's Hospital off the Internet."
In the statement, Gottesfeld said he was motivated to launch the assault because, "I had heard ... too many ... horror stories of institutionalized children who were killed or took their own lives in the so-called 'troubled teen industry.'" With Boston Children's involvement in one high-profile case, Gottesfeld said an attack on the hospital during an important fundraising campaign "would hit [the hospital] where they appear to care the most, the pocket book and reputation."
Gottesfeld was arrested in February after he was found in a small boat off the coast of Cuba. Gottesfeld and his wife made a distress call after their boat ran into trouble (see DDoS Suspect Arrested After Rescue at Sea). A nearby Disney Cruise Ship responded to the distress call and rescued the couple.
In a statement issued at the time of his arrest, the U.S. Department of Justice said Gottesfeld had been aware of a federal investigation since October 2014, when the FBI searched his home in relation to a computer attack on the hospital network.
The DDoS Attack
On April 25, 2014, Children's Hospital of Boston confirmed that its website had been undergoing cyberattacks for nearly a week, which made some online services, such as patient appointment scheduling, sporadically inaccessible. At the time, the hospital said its website had been "the target of multiple attacks designed to bring down the site by overwhelming its capacity."
The hacktivist group Anonymous had been suspected of launching the attacks against the hospital in retaliation for its involvement in an ongoing child custody case that had drawn national attention. That case involved two Connecticut parents who had lost custody of their teenage daughter, Justina Pelletier, to the state of Massachusetts over allegations by the hospital that the parents medically abused the girl.
In addition to the DDoS attack on Children's Hospital, the indictment against Gottesfeld charges that he was also responsible for directing the launch of a DDoS attack on Wayside Youth and Family Support Network, a Framingham, Mass.-based residential treatment facility where Pelletier had been transferred for care during the custody dispute.
The indictment says that on March 23, 2014, Gottesfeld and an unindicted co-conspirator exchanged a series of Twitter direct messages discussing attacking the computer networks of institutions involved in Pelletier's treatment. Gottesfeld suggested that the first target be Wayside, according to the indictment.
Two days later, after the news media reported that a judge had granted permanent custody of Pelletier to the Massachusetts Department of Children and Families, Gottesfeld issued a series of public Twitter messages, which included the hashtag #Anonymous, calling for attacks on the Wayside network, the court documents say.
"The conspirators launched a DDoS attack against Wayside that day. The attack lasted for more than a week, crippled Wayside's website during that time, and caused it to spend more than $18,000 on response and mitigation efforts," the indictment says.
You Tube Video
Federal prosecutors also contend that on March 23, 2014, Gottesfeld posted a YouTube video calling, in the name of the hacking organization Anonymous, for action against Children's Hospital in response to its treatment of Pelletier. The video, which was narrated by a computer-generated voice, stated that Anonymous "will punish all those held accountable and will not relent until [Pelletier] is free."
Prosecutors say the YouTube video also directed viewers to a posting on the website pastebin.com that contained information about the Children's Hospital's server necessary to initiate a DDoS attack against that server.
Court documents say that on April 19, 2014, Gottesfeld and the conspirators initiated a DDoS attack against the Children's Hospital server that was identified in the pastebin.com posting.
"The DDoS attack, which directed hostile traffic at the hospital's network for at least seven days, disrupted that network and took the hospital's website out of service. The attack also disrupted the hospital's day-to-day operations as well as the research being done at the hospital," the indictment alleges.
"In an effort to ensure the attack did not compromise patient information, the hospital decided to shut down the portions of its network that communicated with the internet and its email servers. This effort successfully prevented the attackers from accessing any patient records or other internal hospital information," the indictment states.
The shutdown of the Children's Hospital's website, external internet porta, and email servers impacted communication throughout the Boston-area medical community, prosecutors note. It also disrupted an important fundraising period for the hospital by disabling the Children's Hospital fundraising portal.
Responding to, and mitigating, the damage from this DDoS attack cost Children's Hospital more than $300,000, court documents say. In addition, Children's Hospital estimates it also lost more than $300,000 in donations because the DDoS attack disabled the hospital's fundraising portal, the indictment states.
Neither Wayside nor Boston Children's Hospital immediately responded to ISMG's request for comment.
Difficult Cases
A federal law enforcement official tells ISMG that it's rare for DDoS-related cases to be prosecuted. "These are hard cases. It's so easy for bad actors to rent a DDoS platform, and many of these attacks are launched outside the U.S," he says.
Privacy attorney David Holtzman, vice president of compliance at security consulting firm CynergisTek, notes: "DDoS attacks like those experienced by Boston Children's Hospital, and the more recent incident involving the domain name system provider that disabled access to several cloud-based electronic health record systems, are a call to action for every healthcare organization."
Holtzman is referring to the recent DDoS attack on Dyn, which reportedly affected some EHR vendors' websites.
"It is critical that healthcare organizations have an incident response plan in place that ensures safe patient care when faced with a downtime incident involving the loss of access to electronic health record systems," he says.
Attorney Martin Tully, co-chair of the data law practice at law firm Akerman LLP, predicts there are likely to be more attacks like the recent one on Dyn, which leveraged numerous hacked internet of things devices to create a botnet. "This is because, among other things, many IoT devices are not designed with cybersecurity in mind," he says.
"The rising frequency and cost of cyberattacks in the healthcare industry is definitely a cause for concern for all institutions, especially those most ill-equipped to rebuff and respond to them," he says.
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
For more than a decade, Christy Wyatt was immersed in mobile security - most recently as CEO of Good Technology. Now she has re-emerged as CEO of Dtex Systems. What new challenges does this role pose to the veteran security and technology leader?
Primarily, Wyatt says, her new company and position give her the opportunity for a fresh look at endpoint security.
"What is sort of striking to me is that despite all of the investment companies have made in locking things down, and blocking technology and managing things, we still have such little information about what's actually going on at the endpoint," Wyatt says. "What really kind of caught my eye about Dtex is that they're not just throwing out alerts ... they're giving answers. They're giving a storyline that's saying 'Here's what's going on. The user accessed this, and then they did that, and they put it there ...' and it's in a fully auditable trail."
For Wyatt, this approach created an "aha" moment.
"With that kind of visibility, imagine all of the interesting questions you could answer for your organization," she says.
In an Executive Sessions interview (see audio link below photo) about her new leadership role at Dtex, Wyatt discusses:
What attracted her to Dtex from Good Technology; How she helps Dtex stand out in a crowded cybersecurity marketplace; Ideas for how the security industry will evolve in 2017.Wyatt is CEO of Dtex Systems and serves as a member of the board. Formerly, she was chairman, CEO and president of Good Technology, which specializes in mobile security. During her tenure at Good Technology, she led the company through significant transformation and aggressive growth - and its subsequent acquisition by Blackberry in 2015. Prior to Good Technology, Wyatt held leadership positions at Citigroup, Motorola, Apple, Palm and Sun. In 2015 she was named one of Inc. Magazine's Top 50 Women Entrepreneurs in America. Also in 2015, she was named CEO of the Year by the Information Security Global Excellence Awards. She was named one of the top 100 Women Leaders in STEM in 2012 and named one of Fierce Wireless' "Most Influential Women in Wireless" several years in a row.
More Articles …
Page 3520 of 3545
