- Details
- Category: Security News
Authentication , Biometrics , CISO
Multifactor Authentication - A Key Component of the "STOP. THINK. CONNECT." Initiative By Michael Magrath @ VASCO
Too often security experts and security companies focus on the business to business (B2B) or business to government markets (B2G). STOP. THINK. CONNECT.™ is the global online safety awareness campaign to help all digital citizens stay safer and more secure online addressing the consumer.
Last month, the White House and the National Cyber Security Alliance (NCSA) launched "Lock Down Your Login," a STOP. THINK. CONNECT.™ Initiative. "We were basically approached by the White House. The president wanted to do something on online security education and awareness, and the White House thought strong authentication was an important point to stress," Michael Kaiser, the NCSA's executive director, told CBS News.
Kaiser said the "Lock Down Your Login" campaign will urge consumers and businesses alike to be more cognizant of the security threats posed by traditional username-password combinations that many cybersecurity experts see as behind the times in the face of increasingly sophisticated and widespread hacks. The NCSA reports that an incredibly high 72 percent of all Americans believe that their accounts are already secure with just a username and password."
"Lock Down Your Login" recommends that you as consumer "fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media." I would also add healthcare records to that list given the personal nature of health information and the wealth of personally identifiable information they contain.
On October 4, the Healthcare Information and Management Systems Society (HIMSS) North America and the NCSA released "2016 Practical Tips on Safeguarding Information for Healthcare Organizations". Among the tips, "Use multi-factor authentication". Use two different factors of something you know, have, and are.
The HIMSS/NCSA tip sheet supports HHS's Office of the National Coordinator for Health IT's (ONC) strategic roadmap milestone of "Verifiable Identity and Authentication of All Participants" calling for strong authentication to access patient portals in lieu of passwords to reduce vulnerabilities in identity theft and for health care organizations to implemented identity-proofing and authentication best practices.
Earlier this year the HIMSS Identity Management Task Force, which I chair, published identity proofing and authentication recommendations for patients accessing their health information electronically. Included in the guidance are discussions about how to conduct identity-proofing and authentication at a high level of confidence, with the smartphone as the key use case, how to handle delegating access to patient information and addressing situations where a user would like to remain anonymous.
Virtually every industry is prone to cyberattacks, online fraud and identity theft. For years banks have secured online transactions for commercial accounts and private banking customers via multifactor authentication. Now through organizations like the NCSA and HIMSS, multifactor authentication may finally become mainstream in industries including healthcare, personal banking, e-commerce, education and online gaming. Having the White House lead the charge can't hurt.
- Details
- Category: Security News
Audit , CISO , Cloud Computing
Security Through Visibility: Seeing Into Virtual and Cloud Networks Comprehensive Network Modeling Helps Security Engineers Extend Traditional Security Processes into Hybrid Enterprise Networks; by Skybox VP Products Ravid Circus
Imagine an IT security team as a navy crew at sea. A torpedo blasts the ship's side below the water line. As the water floods in, they can't even see the hole, let alone fix it. Instead, everyone turns to the pumps to keep the ship afloat.
This is the state of many security programs today. Despite a plethora of point solutions, security teams lack visibility into what they're trying to protect, their most pressing risks and the security tools at their disposal. Thus security teams operate in constant reactionary mode, while a strategic, proactive security program remains elusive.
The growing popularity of virtual networks further complicates visibility issues. Virtual machines are spun up at a moment's notice, and security groups and tags are assigned - but not necessarily in line with broader security policies. Network security teams may have no access to management consoles and limited insight as to how changing network architectures affect their attack surface.
But with comprehensive network modeling extending into virtual networks, network security engineers can gain the needed visibility to unify security and compliance processes across their hybrid hardware and virtual environments.
Verifying Access
A major challenge to policy and access verification in hybrid environments is complexity. The mixture of physical, virtual and cloud networks with their various security groups and tags, as well as traditional ACLs, makes manual comparison and analysis almost impossible. But by normalizing this data and combining hybrid network policies, network access can be analyzed end to end and visualized within the model.
Microsegmentation Challenges
Historically, data centers have been protected by perimeter security technologies analyzing north-south traffic -traffic into and out of the data center. Traditional data center designs assume that all east-west traffic - traveling within the data center - occurs in trusted, well-protected zones. Recent data breaches, however, have shown that this assumption is no longer valid. Microsegmentation is capable of dividing east-west traffic within the data center into smaller, more protected zones; but without security visibility into how microsegmentation is implemented, it's difficult to verify policy is adhered to across the network.
By combining and modeling north-south and east-west policies network security teams can gain end-to-end access visibility throughout their hybrid network. Model-driven visibility also provides a more realistic view of applied policy at the host level rather than verifying access only at "chokepoints" or gateways to the virtual network.
Vulnerability Detection in Virtual Networks
One added benefit of modeling virtual and cloud environments is scanless vulnerability detection. Security analytics applied to the model can deduce vulnerabilities using product configuration and version information. This can significantly decrease reliance on active or third-party scans which are harder to operate on virtual and cloud networks. Incorporating vulnerability intelligence gives a fuller picture of how these networks impact overall risk.
Visualization
By unifying hybrid IT environments in one model and normalizing their data, organizations can break down the barriers that traditionally existed between physical, virtual and cloud networks for comprehensive, streamlined security management.
This information can be further distilled into a simple picture of the organization's unique attack surface. Using attack surface visualizations, CISOs to "in-the-trenches" security practitioners to board members can quickly see the interconnectedness of their IT infrastructure and where their most critical security exposures lurk. Attack surface visibility gives an intuitive and deeply analytical tool to make fast, informed decisions regarding incident response, operations and security investments. It provides a common language and reference to stop reacting to symptoms and start treating root causes of security issues, creating a proactive, holistic security program.
- Details
- Category: Security News
Data Breach , Messaging , Technology
But Full Breach Impact Still Unclear as Yahoo Negotiates Sale to Verizon Yahoo's Sunnyvale campus in California. Credit: Yahoo (Flickr/CC)
Yahoo's Sunnyvale campus in California. Credit: Yahoo (Flickr/CC)Yahoo has become the world's poster child for the short-term business perils of suffering a massive data breach. Last week, Verizon's general counsel warned that the breach might constitute a "material impact" that gives Verizon an out from its $4.8 billion bid to buy the flagging search giant.
See Also: Main Cyber Attack Destinations in 2016
But Yahoo's fortunes are looking a little brighter this week after it posted a rise in third-quarter profit, exceeding analysts' expectations. The technology giant also reports that page view counts and use of its email service increased after the breach.
With Yahoo delivering its breach notification to the public just one week before the end of its third quarter, however, the jury is arguably still out on whether the breach's full impact has yet to be felt.
On Oct. 18, Yahoo released its quarterly results for July 1 to Sept. 30, reporting quarterly net earnings of $162.8 million, up from $76.3 million in the third quarter of 2015. Analysts expected the company to report earnings of 14 cents per share - minus certain expenses - compared to 15 cents in the same period last year. But Yahoo exceeded expectations by reporting earnings of 20 cents per share. The company says that it's also on track to post stronger-than-expected earnings for the current quarter.
Yahoo, however, declined to hold its usual earnings call with investors. The company said it made that decision in light of its in-progress sale to Verizon, which is expected to close in the first quarter of 2017. But the move also enabled Yahoo to avoid any pointed questions about its massive data breach, which it discovered in August.
The company announced the breach on Sept. 22, just eight days shy of the end of its third quarter, saying that in late 2014, it suffered a massive data breach that resulted in the theft of "information associated with at least 500 million user accounts."
In its earnings report, Yahoo offered no insights into exactly how it suffered its data breach, which is the largest that's ever been seen.
Instead, CEO Marissa Mayer said in a statement that the company has been working hard to retain users and is "heartened" by the increased page views and email usage since its breach. "We remain very confident, not only in the value of our business, but also in the value Yahoo products bring to our users' lives," she said.
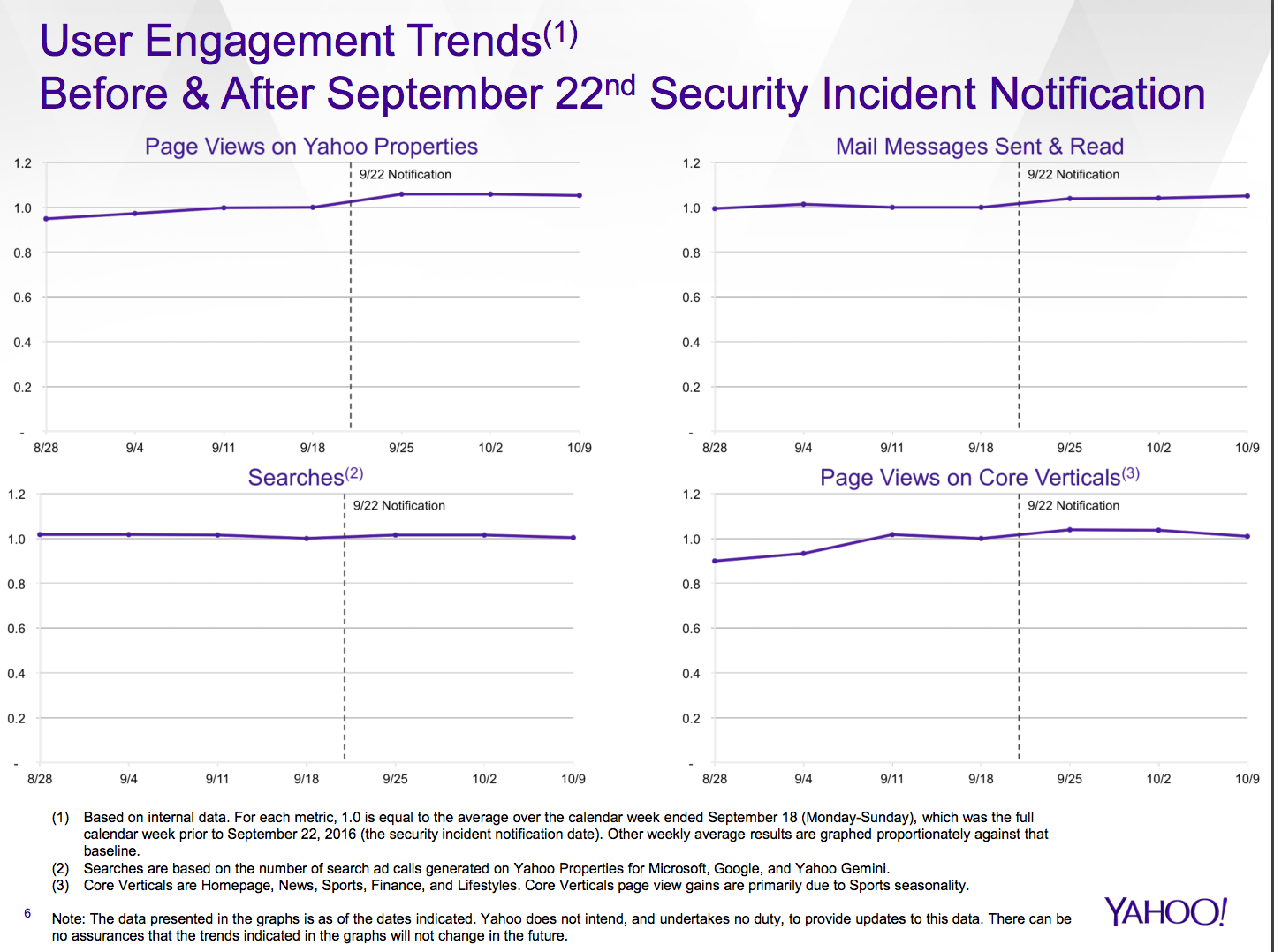 Yahoo reports that page views and email usage increased after its Sept. 22 breach notification.
Yahoo reports that page views and email usage increased after its Sept. 22 breach notification.On the Rocks
But analysts warn that the company is running out of time, unless it successfully wraps up the Verizon deal. Notably, its third-quarter EBITDA - earnings before interest, tax, depreciation and amortization, which is a more accurate measure of a company's operational performance than looking at net income - fell by 6 percent from the same period last year, hitting $229 million.
Yahoo's core advertising revenue business is in decline. After subtracting advertising commissions paid by Yahoo to partners, its third-quarter ad revenue was $857.7 million, a decline of 14 percent from the same period last year. In seven of the last eight quarters, furthermore, it's seen ad revenue decline.
And Yahoo will continue to lose market share to Google and Facebook, accounting for just 1.8 percent of net digital ad revenue worldwide this year, down from 2.4 percent in 2015, eMarketer predicts. The market researcher also expects Yahoo's worldwide ad revenue to drop 10.2 percent in 2016, after they declined 3.5 percent in 2015.
Short-Term Bump?
Many experts say it's too soon to tell whether the breach - or revelations over an alleged U.S. government email-spying order - have irrevocably damaged Yahoo. Facing questions about the email-scanning report, company officials have described Yahoo as a "law-abiding company." But Yahoo has also called on the U.S. government to publicly divulge exactly what it requested of Yahoo (see Yahoo Asks US Government to Declassify Spying Order) .
While Yahoo has emphasized that page views and email usage increased after the breach, such a turn of events was predicted last month by Mikko Hypponen, chief research officer of Finnish security firm F-Secure. He said that Yahoo would see a surge of advertising revenue from users who heard about the breach and logged on to Yahoo to change their password or perhaps attempt to shut down their accounts. Such behavior would likely have inflated page views and Yahoo mail usage.
Yahoo's ad revenue is skyrocketing, as 500 million users log in to Yahoo for the first time in years. To change their password and log out.
Following the earnings report, however, Ronald Josey, an analyst for investment bank JMP Securities, told Reuters that it's still too soon to tell if the breach caused irrevocable damage. But he said that the customer trends detailed by Yahoo are "encouraging."
"The message here is email and messaging is a very sticky product and people want to get to their messages," Josey said.
Question: Material Impact
Verizon, however, has already signaled that it may be getting antsy over its Yahoo bid. While Verizon CEO Lowell McAdam dismissed a report that the company would seek a $1 billion discount in Yahoo's sale price as "speculation," he didn't rule it out. And last week, Verizon's top lawyer said the company "has a reasonable basis" to question whether the breach will have a material impact on Yahoo's value.
"We're looking to Yahoo to demonstrate to us the full impact if they believe it's not [material]," Verizon general counsel Craig Silliman told reporters, according to The Washington Post. "They'll need to show us that, but the process is in the works."
Yahoo, meanwhile, says in a statement: "We are confident in Yahoo's value and we continue to work toward integration with Verizon."
- Details
- Category: Security News
Messaging , Privacy , Technology
Yahoo Says It Is Prohibited From Discussing Surveillance Operation
Yahoo is appealing to the U.S. director of national intelligence to declassify an order that allegedly required the company to install secret spying software that scanned incoming email accounts for specific content.
See Also: Secrets to a Simpler Security Incident Response
The company complied with the classified order, although the spying code was removed earlier this year after Yahoo's security team suspected hackers had planted it, Reuters reported on Oct. 4.
The decision by Yahoo CEO Marissa Mayer to comply rankled some employees concerned about privacy and U.S. government overreach. Yahoo has contested media coverage around the situation but has not provided more information, presumably because it legally can't.
Technology companies must comply with orders obtained by the intelligence community through the Foreign Intelligence Surveillance Court. The court's decisions aren't public and can't be discussed by entities receiving orders due to national security concerns. Yahoo's letter, posted on its website, takes pains to keep within those bounds.
"Yahoo was specifically mentioned in these reports, and we find ourselves unable to respond in detail," writes Yahoo General Counsel Ron Bell. "Your office, however, is well positioned to clarify this matter of public interest."
The company asks James Clapper, director of national intelligence, to confirm whether an order exists, and if so, declassify all or parts of it. It also pleads to have the government "make a sufficiently detailed public and contextual comment to clarify the alleged facts and circumstances."
Also on Oct. 19, the American Civil Liberties Union said it filed a motion with the Foreign Intelligence Surveillance Court to release court records that contain "novel or significant interpretations" of law between Sept. 11, 2001 through June 2015.
The FISC is supposed to made significant rulings public, as required by the USA Freedom Act, the ACLU says. But that act doesn't apply to secret court orders released prior to when it was passed in June 2015. The ACLU contends that those decisions may shed light on the U.S. government's legal rationale for its Yahoo order.
The USA Freedom Act restricted direct bulk collection of U.S. citizens' information by intelligence agencies and strengthened legal protections over how data is accessed. But the limited information released so far about what happened to Yahoo has raised fears that the U.S. may be stretching the law.
Secret Court Battles
Long before former National Security Agency contractor Edward Snowden leaked documents that showed the extent of U.S. government's spying, Yahoo had fought surveillance-related legal orders. In 2007 and 2008, Yahoo waged a secret court battle in which the company contended that the bulk surveillance program PRISM violated the U.S. Constitution.
Yahoo lost the case, but the company pressed the U.S. government for years to release some of the court files. In 2014, more than 1,500 pages of material was released, much of it redacted. But it was one of the first times material from the Foreign Intelligence Surveillance Court was made public.
That's why Yahoo employees were dismayed by the company's decision to comply with the latest order. Alex Stamos, who then was the company's CIO, contended the spying code was buggy and could have allowed hackers to access email. He resigned from Yahoo in May 2015 and is now in the same position at Facebook (see Report: Yahoo Complied with Government Spying Order).
The disclosure of the court order came at a tough time for Yahoo, which in mid-September acknowledged a breach that leaked 500 million accounts. That data breach complicated Verizon's planned $4.8 billion acquisition of Yahoo (see Massive Yahoo Data Breach Shatters Records).
Privacy Shield Impact
Yahoo contends that media reports about the order had led to broad speculation concerning the Privacy Shield, a new data transfer agreement between the U.S. and European Union (see Europe's New Privacy Shield: Will It Hold?).
The Privacy Shield is a new framework for how U.S. companies can collect personal information in a way that complies with E.U. data protection and privacy rules. The framework is a replacement for Safe Harbour, which the European Court of Justice found failed to protect privacy in light of U.S. mass surveillance programs.
"That speculation results in part from lack of transparency and because U.S. laws significantly constrain - and severely punish - companies' ability to speak for themselves about national-security related orders even in ways that do not compromise U.S. government investigations," Bell writes.
Yahoo says that while confidentiality is needed for national security, it's important that the U.S. government discloses how and under what circumstances it uses law such as the Foreign Intelligence Surveillance Act to obtain private online activity or communications.
"Citizens in a democracy require such information to understand and debate the appropriateness of such authorities and how the government employs them," Bell writes.
- Details
- Category: Security News
Breach Preparedness , Cybersecurity , Data Breach
3 Regulators Unveil Plan for Protecting Banks from Cyberattacks
Federal banking regulators are proposing tough new standards designed to bolster cybersecurity at the nation's largest banking institutions.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
The proposed standards, published on Oct. 19 by the Federal Deposit Insurance Corp., the Federal Reserve Board and the Office of the Comptroller of the Currency, are aimed at institutions with $50 billion or more in assets. They will be finalized after a comment period that ends Jan. 17. But FDIC spokesman David Barr tells Information Security Media Group that no timeframe has been set for when the new standards could take effect.
The proposal comes after a February hack that drained $81 million from Bangladesh's central bank and the 2014 hack at JPMorgan Chase that compromised data on millions of customers.
"Due to the increasing interconnectedness of the U.S. financial system, a cyber incident or IT failure at one entity may impact the safety and soundness of other financial entities and introduce potentially systemic consequences," the draft proposal states.
Two-Tiered Approach
The proposed standards call for two tiers of requirements, with higher standards being set for institutions that manage, maintain and/or operate systems that provide key functionality to the financial sector, posing the greatest risk to the financial system.
"For these sector-critical systems, the agencies are considering requiring firms to substantially mitigate the risk of a disruption or failure due to a cyber-event," according to a release from the agencies.
The proposed standards for all large banks cover five key areas:
Cyber risk governance; Cyber risk management; Internal dependency management; External dependency management; and Incident response, cyber resilience and situational awareness.Among some of the points addressed in the proposed standards are the need for more stringent cybersecurity requirements for third-party service providers as well as nonbank financial companies, such as payments processors, that are supervised by federal regulators.
The Board's Role
The proposal also calls for more cybersecurity oversight from boards of directors and senior management by holding them accountable for implementing cyber risk management frameworks. It also notes that federal regulators are considering whether they should mandate that bank board members have "adequate expertise" in cybersecurity.
Cybersecurity attorney Chris Pierson, CISO and general counsel at invoicing and payments provider Viewpost, says regulators' call for more qualified board members could potentially have the greatest impact on banks' cybersecurity and cyber risk governance.
"Similar to the requirements under Sarbanes-Oxley that require boards to have persons of financial expertise on the board or audit committee, this change will ensure that there is proper governance over risk, cybersecurity and privacy from an outside director perspective," he says. "Nothing these days is more important than having effective, knowledgeable experts who can understand business objectives and goals and provide some balance to cybersecurity business advantages and risks. These requirements are helpful to amplify the need for board access and governance over cybersecurity and business goals."
The proposed standards "would not apply to community banks," FDIC Chairman Martin J. Gruenberg points out in a statement. "They ... would continue to be subject to current generally applicable guidance and standards."
The federal regulators' announcement comes just weeks after the New York Department of Financial Services announced plans for new cybersecurity regulation (see Critics Blast New York's Proposed Cybersecurity Regulation).
More Articles …
Page 3516 of 3545
