- Details
- Category: Security News
CISO , Cybersecurity , Governance
Mandates for CISOs, Breach Notification Are Too Prescriptive, Some Argue
In January, banks and other financial services companies based in New York may have to comply with tough new cybersecurity requirements outlined in what Gov. Andrew Cuomo says would be the nation's first state regulation designed to help thwart cyberattacks against the financial sector.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
"This regulation helps guarantee the financial services industry upholds its obligation to protect consumers and ensure that its systems are sufficiently constructed to prevent cyberattacks to the fullest extent possible," Gov. Cuomo says of the New York State Department of Financial Services' proposal, announced last month.
But some critics contend that New York's regulatory proposal is far too prescriptive, making it challenging for banking institutions, especially smaller ones, to comply.
"Banks continue to use limited resources to keep up with regulations that bring us no closer to actual results," says Ted Tomita, CTO of Catskill Hudson Bank in Monticello, N.Y. "For smaller institutions, these regulations make it very difficult to operate. Meanwhile, larger institutions absorb this as a minor inconvenience."
New York's proposed new regulation, if left unchanged, will require that every New York banking institution, regardless of size, hire or designate a "qualified" CISO to oversee the institution's cybersecurity program. It also will require institutions to notify the state within 72 hours of any cybersecurity event that could impact business or consumer privacy.
Other requirements in the new regulation - including mandatory multifactor authentication for all employees, contractors and others who've been granted privileged access to internal systems as well as encryption of all nonpublic information that is stored or transmitted - are listed on the state department's website.
The state is accepting comments on the proposed regulation until the end of October, after which it could make refinements before the regulation is finalized.
Far Different Approach Than FFIEC
Unlike New York, the Federal Financial Institutions Examination Council has taken a less prescriptive approach to cybersecurity, focusing on outlining best practices instead (see FFIEC Plans Cybersecurity Assessments, FFIEC Issues Cyber Assessment Tool and FFIEC Issues Cyber-Resilience Guidance).
Rather than mandating, for instance, that all institutions have a CISO, the FFIEC recommends that institutions ensure that all executives and staff have "clearly defined roles and responsibilities" that carry with them assigned accountability "to identify, assess and manage cybersecurity risks."
By comparison, the state of New York is coming across like a micromanager, argues Avivah Litan, a financial fraud expert who's an analyst at the consultancy Gartner.
"The FFIEC has been at this much longer than New York state and has taken a more seasoned risk-based approach that reflects a deeper and more practical understanding of the different profiles of the wide range of banks - small and large - that they regulate," she says. "I don't think the FFIEC will move backwards and demand banks appoint CISOs, especially when they are not staffed for such functions. The banks that need CISOs -generally the larger banks - already have them. And some have multiple CISOs for different areas."
The proposed New York regulation, Litan argues, "reads more like a checklist of compliance requirements that reminds me of the PCI standard, which is a step backwards from the FFIEC's cybersecurity assessment guidelines. The FFIEC guidelines, which rightfully leverage NIST standards, demand a comprehensive, risk-based approach and assessment."
CISO Requirement Criticized
Tomita of Catskill Hudson Bank argues that requiring banks to designate a "qualified" CISO won't improve cybersecurity.
"At the end of the day, it's simply a title and 'qualified' is open to interpretation," he says. "Financial institutions are facing new challenges every day. Having someone who can understand the unique risks of their institution and implement the proper tools to address those risks is critical to having an effective security program."
Austin Berglas, head of cyber defense at cyberthreat intelligence firm K2 Intelligence, predicts the state will receive many questions during the comment period about the proposed requirement for institutions to designate a qualified CISO.
"The role of a CISO can mean different things to different organizations depending on size, internal structure and needs," he says. "The CISO role is commonly described as a senior-level position responsible for establishing and maintaining the organization's strategy and program to ensure assets are properly protected. Depending on the size and sophistication, some organizations may view this role as a more strategic versus technical role."
Breach Notification
Cybersecurity attorney James Pastore, a litigation partner at the New York law firm Debevoise & Plimpton, contends the proposed New York regulation's provision for breach notification is unrealistic.
"The 72-hour notice period is both short and broad," he says. "Victims of an 'actual or potential' incident rarely have many facts at that point, and if NYDFS [New York Department of Financial Services] really wants to hear about every potential unauthorized access, they will need a hotline."
The regulation also contains a built-in "tripwire," Pastore notes. Any call to another government agency, such as law enforcement, automatically requires notice to NYDFS. "That may chill some calls to law enforcement and will not help the existing tension between the company being treated as a hacking victim on the one hand and being treated by regulators as negligent for losing customer data on the other," he says.
- Details
- Category: Security News
Anti-Malware , Payments , Risk Management
Now a Second Gang - Not Bangladesh Bank's Attackers - Is Gunning for Banks
A malware-wielding gang has been targeting financial firms' SWIFT software to inject fraudulent money-moving messages since at least January in "discreet campaigns" not tied to the Bangladesh Bank hack, security firm Symantec warns.
See Also: Avoid Theft of Your Privileged Credentials
The emergence of the targeted attacks, which rely on malware called Odinaff, is bad news for banks that rely on the SWIFT network to send money-moving messages. Symantec reports that the malware includes the ability to alter client-side logs used by SWIFT software. It says the attackers appear to be seeking high-value targets and attempting to avoid discovery, rather than pursuing mass-infection campaigns.
The Society for Worldwide Interbank Financial Telecommunication, as SWIFT is formally known, is a cooperative owned by 3,000 banks that bills itself as "the world's leading provider of secure financial messaging services." It's now used by more than 11,000 banks globally to process 25 million communications daily that collectively account for billions of dollars' worth of transfers.
The payoff for attackers who can inject fraudulent money-moving messages into SWIFT's network by hacking into PCs that interface with the network is clear: They can literally transfer themselves money.
A SWIFT spokesman tells Information Security Media Group that the organization is aware of the attacks and related modus operandi, as detailed by Symantec, and that its new customer security intelligence team has issued an alert to the organization's customers.
"We published related indicators of compromise and a practical example of the MO for our community earlier this summer," the spokesman says. "This work forms part of SWIFT's information sharing initiative, which has grown significantly since its launch, and which includes detailed intelligence and analysis on the modus operandi of attackers in customer fraud cases."
Life After the Bangladesh Bank Hack
Symantec's alert says at least two groups have been actively targeting SWIFT-using banks.
The first has been tied to the February hack attack against the central bank of Bangladesh that resulted in attackers stealing $81 million from Bangladesh Bank's account at the Federal Reserve Bank of New York via fraudulent SWIFT messages. That attack, and the discovery of similar, related attacks - before and after the Bangladesh Bank theft - sent shock waves through the financial services sphere, triggering concern from regulators and legislators around the world, and resulted in SWIFT taking a more active role in securing customers' use of its messaging network and related software.
Systems at Bangladesh Bank were infected by "Banswift" malware that allowed attackers to inject fraudulent money-moving messages into the SWIFT network. Attackers also employed trojanized PDF reader software that prevented details of the transactions from being printed out on the bank's printer, thus delaying the bank's discovery of the fraud.
Security experts have traced those attacks to the Lazarus Group, as first detailed in a February report into Operation Blockbuster that was coordinated by anti-fraud and analytics firm Novetta.
Inside Odinaff
The newly identified Odinaff attacks, however, work in a slightly different way and use entirely unrelated malware. For starters, Odinaff serves as a "dropper," meaning it allows attackers to download selected, additional attack tools onto victims' systems, Symantec's Security Response team says in a blog post. One such tool is a backdoor called Batle, Symantec says, which "is capable of running payloads solely in memory, meaning the malware can maintain a stealthy presence on infected computers.
"Symantec has found evidence that the Odinaff group has mounted attacks on SWIFT users, using malware to hide customers' own records of SWIFT messages relating to fraudulent transactions," the security firm says. "The tools used are designed to monitor customers' local message logs for keywords relating to certain transactions. They will then move these logs out of customers' local SWIFT software environment. We have no indication that [the] SWIFT network was itself compromised."
Symantec says this "suppressor" malware watches for "specific text strings," including dates and specific International Bank Account Numbers, or IBANs. It adds that another attack file that's been installed on infected systems can overwrite the first 512 bytes of a hard drive, which contains the Master Boot Record, or MBR, that the PC requires to boot. "We believe this tool is used to cover the attackers' tracks when they abandon the system and/or to thwart investigations," Symantec says.
The security firm hasn't revealed how many related infections it has seen, and it says it can't trace 60 percent of attacks to a specific industry. For those attacks that it has been able to trace, one-third have targeted financial services firms, Symantec says. Organizations in the United States have been most frequently targeted, followed by Hong Kong, Australia, the United Kingdom and Ukraine.
Multiple Malware Distribution Techniques
Odinaff is being distributed in multiple ways, including via spear-phishing documents that contain a malicious Microsoft Office macro. If the user has left macros disabled - as security experts recommend - then the lure document tries to trick them into turning macros on.
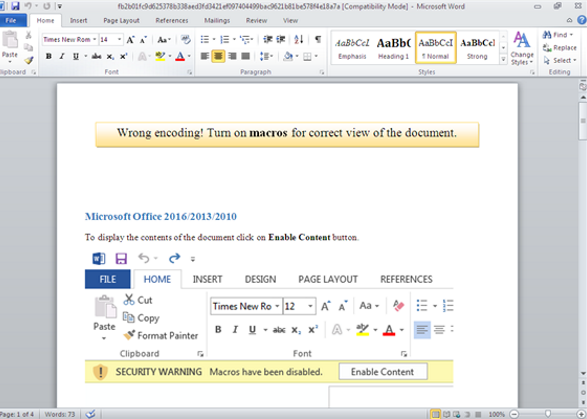 The Odinaff lure document tries to trick viewers into enabling macros in Microsoft Word (source: Symantec).
The Odinaff lure document tries to trick viewers into enabling macros in Microsoft Word (source: Symantec).Symantec says the malware is also being distributed via botnets as well as hidden inside "a Trojanized installer for AmmyyAdmin, a legitimate remote administration tool." The website that distributes AmmyyAdmin has been repeatedly hacked in recent months, with various types of malware hidden inside the software that users can download.
Potential Carbanak Tie
Three command-and-control IP addresses used to control infected Odinaff endpoints were previously used by C&C servers tied to Carbanak malware campaigns, Symantec says. The Carbanak gang was tied to at least $1 billion in fraud from 2012 to 2014, and it appears to have made a comeback starting in 2015 with a range of attacks tied to point-of-sale devices.
Of those three IP addresses, Symantec adds, one was previously used in the massive Oracle MICROS breach, which some security experts have attributed to the Carbanak gang. The reused IP addresses may only have been rented from a third-party cybercrime service provider, although Symantec said that "the infrastructure crossover is atypical, meaning it could also be a similar or cooperating group."
Another theory, however, is that the Carbanak gang has been diversifying from banking Trojan infections into targeting SWIFT-using banks and is now running a compartmentalized, highly targeted operation using Odinaff that can access and manipulate SWIFT logs and inject fraudulent money-moving messages into the SWIFT network.
- Details
- Category: Security News
President Obama sharing his thoughts on the intersection of artificial intelligence, medical viruses and cybersecurity leads this edition of the ISMG Security Report.
In the report, you'll hear (click player above to listen):
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Oct. 7 and Oct. 11 reports, which respectively analyze the PCI Security Standards Council's new requirements that are designed to help thwart attempts to defeat encryption in point-of-sale devices and Hillary Clinton's and Donald Trump's head-to-head clash over purported Russian hacks. The next ISMG Security Report will be posted on Tuesday, Oct. 18.
Theme music for the ISMG Security Report is by Creative Commons license.
- Details
- Category: Security News

Australia's latest report on its cybersecurity stance contains intriguing wording that seeks to clarify what it believes constitutes a cyberattack and why the government believes it has never actually experienced one.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
To be sure, describing computer security incidents - especially in the context of international law - has been a difficult proposition. Reaching a consensus on defining such terms as cyberwarfare, cyberweapons and cyberterrorism has proven difficult.
Classifying cyber incidents accurately is incredibly important, especially if a country decides to take retributive action against another. The issue of vocabulary is so important that a cybersecurity research center run by NATO in Estonia has published a manual with no fewer than 50 terms with the prefix "cyber" in an attempt to reach agreement.
"There are no common definitions for cyber terms," according to a preface to the guide. "They are understood to mean different things by different nations/organizations, despite prevalence in mainstream media and in national and international organizational statements."
What's a Cyberatttack?
On Oct. 12, the Australian Cyber Security Centre released its second-ever report on threats facing the country. It expends considerable effort in the first few pages to take umbrage at how people describe what I'll now just refer to as cyber incidents.
The ACSC says that in order for the public to have a more mature discussion, "it is important that we get the language right - calling every incident a 'hack' or 'attack' is not helpful for a proportionate understanding of the range of threats and only promotes sensationalism."
Cybersecurity isn't an easy subject to cover, and the closer you follow it, the harder it can be to convey situations, particularly to people with less technical knowledge. Was a person's Twitter account "hacked" if someone else logs in with a victim's login credentials? To a layperson, that description might be fine, but those in the industry know that guessing someone's login credentials or convincing them to divulging the information is more trick than hack.
In 2011, Australia defined a cyberattack "as a deliberate act through cyberspace to manipulate, disrupt, deny, degrade or destroy computers or networks, or the information resident on them, with the effect of seriously compromising national security, stability or economic prosperity." That weighty definition underpins a treaty between the U.S. and Australia.
"Fortunately, Australia still has not been subjected to malicious cyber activity that could constitute a cyberattack as defined," the report reads.
Deeper into the report, the ACSC gives the most detailed information released so far about a cybersecurity incident that occurred last year at the Bureau of Meteorology. It apparently does not constitute a cyberattack.
Suspicious activity was detected on two computers, and an investigation by the Australian Signals Directorate showed a remote access tool had been installed. The report says the particular RAT is "popular with state-sponsored cyber activities." The attackers had copied an unknown number of documents from bureau. The discovery of password-dumping tools led the ASD to conclude that "all passwords on the bureau's network were already compromised at the time of the investigation." It was speculated, though never confirmed, that China was involved.
Media Sensationalism
The report doesn't get into the intent of Bureau of Meteorology hackers, which according to the second half of the government's definition would likely tip opinions in favor of labeling that incident a cyberattack. But trying to classify cyber incidents wanders into the same squishy territory faced by U.S. Supreme Court Justice Potter Stewart in 1964. When he was grappling with a First Amendment case over what constituted obscene material that would not be protected by the Constitution, he offered the famous phrase, "I know it when I see it."
The ACSC also takes issue with the way the news media described the distributed denial-of-service attacks that resulted in the disruption of the Australian government's census on Aug. 9. The census, which the Australian Bureau of Statistics had encouraged people to fill out online that day, had to be taken offline following fears that the DDoS attacks might be a warm-up to a larger data breach. Further investigation showed no data had been leaked (see Australian Census Disrupted by DDoS).
"This incident was initially described in some media reporting as being the result of a 'foreign cyberattack' - a description that led to a heightened sense of threat and risk, increased concerns from the public about the security of their personal information and triggered media speculation about nation state motivations, tradecraft and the possibility of further 'attacks'," the report reads.
Keep in mind that in the immediate aftermath of the census failure, the ABS's chief, David W. Kalisch, described the DDoS attacks in an interview as intended to disrupt the census and originating from overseas.
Journalists often defend stories that may not, in retrospect, have had the right tone as the first rough draft of history. But there were undeniably real concerns over the safety of census data, which were also particularly relevant following a fierce debate over changes the ABS made to how it stores data. It also wasn't far-fetched to speculate that a foreign government might be interested in a chance to collect the personal data of 23 million people submitted online through a web-based form.
Unfortunately, the ACSC doesn't offer suggestions for better terminology relating to cybersecurity. But we'll keep an eye out for the first "cyberattack" in Australia that meets the government's current definition.
- Details
- Category: Security News
Anti-Malware , Fraud , Payments Fraud
Sites Have One Feature in Common: Software Vulnerabilities Items for sale from the National Republican Senatorial Committee's online store.
Items for sale from the National Republican Senatorial Committee's online store.If you bought a reproduction vintage Reagan-Bush '84 T-shirt earlier this year from a group that raises funds to support Republican Senate candidates, you may want to double-check your credit card statements.
See Also: Key Cybercrime Trends in 2016
Willem de Groot, a product developer with the Dutch hosting company Byte, found that credit card data from the National Republican Senatorial Committee's online store was siphoned and shipped to a server in Russia. The NRSC's website was just one of 5,900 sites hit by the attacks. Many have now been patched.
E-commerce websites are secure only if they're diligently patched. Attackers often hunt for online stores running popular e-commerce platforms such as Magento, hoping to catch outdated software versions that are vulnerable.
The NRSC fixed its website about two days after de Groot published a blog post. But attackers had been harvesting credit card data between March 16 through Oct. 5 - a long exposure window that means many shoppers could have been hit, de Groot says.
De Groot writes that it's difficult to estimate the number of victims, but the NRSC's store had been receiving 350,000 visits per month. If only 1 percent of those visitors actually purchased something, he estimates that 21,000 card details could have been stolen since March.
"Black market value per card is between $4 and $120, so I assume a modest $30 per card," de Groot writes. "The villains could have made roughly $600K on this store alone."
It's important to note that what de Groot detected doesn't appear to have been specifically intended to cause problems for Republicans along the lines of the hacking woes that the Democratic Party has experienced over the last several months. Rather, the motivation here would appear to be purely financial (see Leaked DNC Emails Show Lax Cybersecurity).
Straight to Russia
The malware installed on the NRSC's site essentially "skims" payment card details. The term is usually applied to physical devices attached to ATMs or payment terminals that copy payment card information encoded on a card's magnetic stripe.
"Once a store is under control of a perpetrator, a (JavaScript) wiretap is installed that funnels live payment data to an off-shore collection server (mostly in Russia)," de Groot writes in a subsequent blog post.
De Groot posted 17 samples of card-skimming JavaScript that he's collected on GitHub. His analysis shows that the malware developers have taken steps to obfuscate the code, meaning it takes programmers "a fair bit of time" to reverse engineer. When such code is planted on a website, it is hard to detect and nearly impossible to trace the thieves, he writes.
He found that in one case, the developers had appended "UPS delivery code START" and "UPS delivery code END" to a chunk of malicious JavaScript in an attempt to deflect cursory investigations of the code.
In the case of the NRSC, the card data was sent to two domains that are hosted by a company called Dataflow, which has a Russian-language website, but is registered in Belize, de Groot writes. Dataflow is a tiny operation, with just two IP blocks consisting of 512 IP addresses. Other services hosted on Dataflow don't appear to be very reputable.
"Its owners deserve praise for collecting about every kind of online fraud known to man: money laundering, synthetic drug trade, darknet messaging, phishing and spam," de Groot writes.
Soft targets
Not only are e-commerce stores often vulnerable, those running the stores can be blasé about security.
De Groot writes that he manually reported some compromises to merchants. Their responses unfortunately indicate a fundamental misunderstanding of the problems. One merchant wrote: "Thanks for your suggestion, but our shop is totally safe. There is just an annoying JavaScript error." Another wrote: "Our shop is safe because we use https."
De Groot's employer, Byte, runs a service called MageReport.com, which scans e-commerce sites using the Magento platform and reports on security problems. Last November, de Groot blogged on Byte's site that he found 3,500 websites that had been hacked, some for as long as six months. He noticed a key difference in those attacks compared to others: The malicious script captured credit card numbers as soon as a shopper types one into a web-based form in a browser.
"Until now, credit card thieves mainly targeted transaction servers, where payment data is generally encrypted and thus hard to extract," he writes. "With this new attack, credit cards are captured before they can be encrypted."
All of the vulnerable sites it found either had outdated versions of Magento or had not applied other security mitigations. But the attack isn't Magento-specific. The vulnerable shops that Byte detected happened to be running Magento, but the JavaScript code could run on any site and accomplish the same end, de Groot writes.
More Articles …
Page 3514 of 3545
