- Details
- Category: Security News

Patrick Wardle, director of research for the security company Synack, often ponders new ways to hack Apple Macs. His latest research project focuses on Mac's webcam, highlighting how malware could secretly record a webcam session.
See Also: Secure Access in a Hybrid IT World
Wardle's research, which he presented at the VirusBulletin conference in Denver on Oct. 6, doesn't focus on how to exploit vulnerabilities in macOS, Apple's latest desktop operating system. Instead, it demonstrates how to take advantage of how Apple allows a webcam to be accessed by more than one program at a time, a feature that could be helpful to users, but also potentially pose a security risk.
"That was something I was concerned about," Wardle says. "It would be naïve to think that other people haven't thought about this who are designing Mac malware, and if they haven't, I would say they're not doing their jobs."
Targeted Recording
Increasingly, Mac malware programs try to access a webcam, but there's a dead giveaway when it's turned on: A webcam's green LED light comes on. Apple has strong security protections around the webcam that make it very difficult, but not impossible, for malware to turn the light off, Wardle says.
"Without physical access, you are probably not going to be able to manipulate that in a way that would allow you to record without the light going on," Wardle says.
But he came up with a better idea. Rather than randomly turn the webcam on and only see or record someone sitting silently at their computer, why not write malware that begins recording video sessions when, for example, a FaceTime or Skype call starts?
"These are the things malware or a nation-state or cybercriminal would want to record anyways," Wardle says. "If you record my entire day, I'm just sitting at my desk picking my nose. When I hop on that webcam session and talk about sensitive business details ... those are the interesting snippets."
The webcam's green light comes on when a FaceTime session is started. But there's no additional notification or warning if a second application simultaneously taps into the video stream using AV Foundation, Apple's framework for accessing the webcam. There are advantages to this arrangement for users. During a FaceTime call, a user can also snap a photo using Apple's mugshot program, Photo Booth.
Wardle says he doesn't want to overhype his findings, because the attack scenario is based on several assumptions. For example, malware has to get on a system, and Apple has several security features. such as XProtect, an anti-malware tool, and Gatekeeper, which can restrict what applications can be installed based on digital signatures.
"Really, it's a neat capability that existing malware could very trivially add that would allow them to record the local user while they're using the webcam without detection," he says. "As a Mac user, that's something I would want to be aware of if there was some undetected malware on my system."
OverSight, A Security Tool
Wardle had some informal chats with Apple's security team about the issue. They agreed that allowing multiple programs to access a webcam is legitimate OS functionality. But Wardle thinks it might be better to notify users when such behavior happens and enable them to make a decision on whether to allow it. At least three types of Mac malware are out there that try to access the webcam: Crisis, Eleanor and Mokes.
Apple locks down other critical components of its operating system. Take Keychain, macOS's built-in password manager. Access to Keychain requires a system password, so it would be evident to users immediately if malware tried to access it.
In the meantime, Wardle built a free tool that alerts users. The tool, called OverSight, detects any new processes trying to gain access. Users can choose to allow or block, giving more insight into what's happening on their Mac. It's possible for malware writers to change the name of a malicious process, to, for example, FaceTime. But if users are suspicious of such a ruse, OverSight can show the file path and process ID, which can be cross referenced to see if it is legitimate.
- Details
- Category: Security News
 Photo: Diego Cambiaso (Flickr/CC)
Photo: Diego Cambiaso (Flickr/CC)In an unprecedented move, the U.S. intelligence community has blamed the Russian government for attempting to interfere in U.S. elections by hacking and leaking documents.
See Also: Managing Identity, Security and Device Compliance in an IT World
"We believe, based on the scope and sensitivity of these efforts, that only Russia's senior-most officials could have authorized these activities," according to a joint statement released by the U.S. Department Of Homeland Security and Office of the Director of National Intelligence.
In particular, it cited "the recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona," which it noted have been "consistent with the methods and motivations of Russian-directed efforts," and which are "intended to interfere with the U.S. election process."
DHS and ODNI also said Russia could be behind recent attempts to probe the security of states' election systems, but stopped short of attributing the attacks to Moscow, although they did say most of these efforts originated from servers run by an unnamed Russian company. The agencies added that "the decentralized nature of our election system in this country and the number of protections state and local election officials have in place" would make it very difficult for a hacker, even one with nation-state backing, to alter ballot counts or election results via a cyberattack.
The attack campaign has included the leak of emails stolen from the Democratic National Committee, which triggered an FBI investigation into the broader attack campaign (see Ex-FBI Agent on DNC Breach Investigation).
But the Kremlin on Oct. 7 fired back at the attack attribution, calling it "nonsense." "Tens of thousands of hackers attack the site of [Russian President Vladimir] Putin every day," Kremlin spokesman Dmitry Peskov told private Russian news agency Interfax. "Many attacks are traced back to U.S. territory. We don't blame the White House or ... [the CIA] every time," Peskov reportedly said.
Escalating Tensions
The DNC leaks began in June, when Guccifer 2.0 - who claimed to have no affiliation to the Russian government - began posting DNC files to the internet. It was followed by further leaks via "hacktivist" website DCleaks.com as well as via WikiLeaks.
Multiple security experts have said the DNC network infiltration appeared to be the work of the advanced persistent threat group known as Fancy Bear - a.k.a. Sofacy or APT 28 - which they suspect is part of Russia's military intelligence agency GRU.
Experts say the election meddling is only the latest episode in what's been a long-running series of political skirmishes that date from at least 2008, when the United States advocated for Ukraine to become part of NATO. Since then, tensions have escalated over Russia's annexation of Crimea in 2014 and more recently over Russia's backing of the Syrian government in that country's five-year civil war, as well as last month's breakdown of a ceasefire negotiated by the Russian and U.S. governments.
"For the past two years, there has been a massive increase in hacking by the Russians," Dmitri Alperovitch, CTO of cybersecurity firm CrowdStrike - which has been retained by the DNC to investigate the hack attacks against it - told NBC News.
"Not all of it is politics. It is across the board," said Alperovitch, who's been involved in the DNC investigation. "But it got more intense this year with the election."
Last month, the emails of one prominent Republican, former Secretary of State Colin Powell, were leaked via the DC Leaks site.
But as part of the same cyber-espionage campaign that targeted the DNC and Powell, hackers have also targeted "hundreds" of other people, including numerous high-ranking Republicans, an unnamed cybersecurity expert who's assisting with the U.S. government investigation tells NBC News.
Victims have included "high-profile former officials, political figures, current officials," the expert said. "I can't tell you who the Russians are going to leak information about next. ... "The only thing I can tell you is that there are going to be more leaks."
Presidential Debates Talk Hacking - Or Not
The subject of Russia's alleged hacking of U.S. systems in an attempt to influence the election was raised at the second presidential debate between Democratic nominee Hillary Clinton and Republican nominee Donald Trump, held Oct. 9.
During the debates, Clinton again criticized Trump for having praised Russian President Vladimir Putin, especially in the wake of the new election hacking attribution. "The Kremlin - meaning Putin and the Russian government - are directing the attacks, the hacking on American accounts to influence our election. And WikiLeaks is part of that," Clinton said.
"Never in the history of our country been in a situation where an adversary, a foreign power, [worked] so hard to influence the outcome of the election," she added.
In response, Trump said there's a propensity to blame Russia for any type of online hacking. He added: "Maybe there is no hacking."
Information Warfare
The Russian government has previously been accused of running propaganda campaigns using what's often referred to as the 4D approach: dismiss, distort, distract and dismay.
The U.S. Ambassador to Germany, John B. Emerson, described the approach in a 2015 speech in Berlin to the Atlantic Council think tank, noting that the Kremlin runs a $400 million media operation that covers 100 countries, and which includes its Russia Today - a.k.a. RT - news network.
"The Russian government, and the media that it controls, are trying to prevent the publication of information that doesn't conform to Russia's aims, and are manipulating the presentation of information to cloak Russia's actions," Emerson said. "The Kremlin's disinformation campaign goes far beyond controlling its own media. It is aimed at nothing less than presenting a parallel version of reality and disseminating it as if it were news. The Kremlin's goal is to make people question the value of media at all; to reject the idea of an absolute truth; and to persuade the public that 'reality' is relative."
WikiLeaks Cited
While the U.S. intelligence community's election-hacking attribution doesn't cite the 4D strategy by name, it does note that Russian-led disinformation campaigns are not new. "The Russians have used similar tactics and techniques across Europe and Eurasia, for example, to influence public opinion there," the statement reads.
Thomas Rid, a professor in security studies at King's College London, says it's notable that the U.S. intelligence agency statement explicitly names WikiLeaks - calling it a tool of "Russian-directed efforts" against the United States - and adds that related Russian disinformation campaigns may be continuing.
"The U.S. intelligence community jointly [and] explicitly named WikiLeaks as an outlet of a Russian influence [operation]. They did not do so lightly," Rid says via Twitter. "Note that Wikileaks has no way of knowing individual files are doctored or not," he added. "Do not take hacked [and] leaked files at face value, on WikiLeaks or elsewhere."
2-Assange may be unaware his site is used as such an outlet-this is good tradecraft, makes the op more credible. This is not the first time.
Next Step: Sanctions?
The intelligence community statement now leaves the White House in a difficult position: How should it respond?
One obvious approach would be employ sanctions against individuals or organizations that that U.S. government suspects ordered or enabled the election-related hacking and leaks.
But Elizabeth Rosenberg, a former senior adviser to the U.S. Treasury who until 2013 helped develop and implement financial and energy sanctions, told The Wall Street Journal that imposing sanctions over the online attacks might be perceived as overkill.
"Imposing sanctions based on a hack alone is aggressive and disproportionate," she said. "It's a really aggressive response to a malicious cyber activity such as this one."
- Details
- Category: Security News
Authentication , Encryption , ID & Access Management
After Mega Data Breaches, Dropbox Strategy Has 'Grown Up Quite a Bit' Photo: Dropbox in 30 Minutes (Flickr/CC)
Photo: Dropbox in 30 Minutes (Flickr/CC)Dropbox has battened down its security hatches. There's good reason: The company was one of many this year that have faced nightmarish news that rumors of a password breach were, in fact, true. It's still unclear how Dropbox and companies including Yahoo, LinkedIn, MySpace and Twitter were hacked, or why the stolen data only circulated more widely several years after the intrusions. But the revelations have unnerved web services companies and spurred a new urgency around securing passwords.
See Also: Protect Your Microsoft Identity Infrastructure
Dropbox's intrusion was isolated to around mid-2012, an era that Rajan Kapoor, the company's senior manager for trust and security, says was a very immature time for cloud services. Since then, security has "grown up quite a bit," he says.
"The industry on the whole has learned a lot of lessons since 2012," Kapoor says. "Dropbox specifically has matured our security capabilities tremendously."
The password breach occurred around the same time as another security incident that became public. An attacker managed to compromise a Dropbox employee's credentials and stole a project document that contained user email addresses. Some users began receiving spam in German, English and Dutch advertising gambling websites.
Dropbox quickly shut down the spam and reset some user accounts after compromised credentials from other services had been successfully re-used. Although the circumstances aren't clear, it's possible that the compromised employee account was used to move laterally through Dropbox's system.
Kapoor says that the attackers eventually reached Dropbox's analytics tools. It's classic attack methodology: Use one compromised endpoint to move laterally through a victim's systems in search of sensitive information. The full scope of the breach did not become clear until four years later, when it was determined that credentials for 69 million accounts had been stolen, Dropbox said in August (see Dropbox's Big, Bad, Belated Breach Notification).
Locked Down Passwords
When the breach occurred, Dropbox was transitioning to stronger password security. Passwords can't be stored in plaintext, so they're processed with a one-way deterministic algorithm to produce a hash.
Analysis of the 2012 breach showed that some of Dropbox's passwords had been hashed with SHA-1, an algorithm that is considered insecure. Other passwords had been hashed with bcrypt, which is considered much more secure.
In an effort to restore confidence, Dropbox has taken the fairly unusual step of describing how it now secures passwords. It takes a layered onion approach that it hopes will mean that even if it experiences another breach, the information obtained will be useless. The steps were outlined in a Sept. 21 blog post.
Here's Dropbox's recipe: Plain-text passwords are first hashed with SHA-512. That result is then run through bcrypt with a per-user salt. Salt refers to unique values that are added to a cryptographic output that forces attackers to take more time. Plus, greater computing power is needed to guess what the hash represents. That value is then encrypted with AES256. The secret key used for the AES256 encryption - which Dropbox refers to as a "pepper" - is stored in a separate location.
If a password table was leaked, the information wouldn't be useful without the pepper, Kapoor says. As an additional defensive measure in the event of a breach, Dropbox could rotate the pepper and re-encrypt the hashes, which would block attackers from using the data they obtained, even if they were able to decrypt it, he says.
The company is already thinking about how to make this system more secure. It is considering storing the pepper in a hardware security module - a device designed to provide maximum security to data such as encryption keys. Plans are also already in the works to increase the strength of its bcrypt implementation.
Halting Lateral Movement
To prevent an intruder from laterally moving through its systems, Dropbox has also mandated its employees and engineers use two-factor authentication. "Just because you've authenticated once in one area, we do not infer that to mean you are authenticated to access anything else," Kapoor says.
Two-factor authentication has the potential to be irritating: Users are asked to fill in their normal login credentials plus a time-sensitive code. For engineers moving back and forth between different development and production systems, asking for that code every time is burdensome. But it's also essential.
"That can be pretty annoying for engineers," Kapoor says. "If they need to get into analytics four times in an hour and they've got to supply 2FA code each time, it's going to slow them down."
To reduce fiction around that process, Dropbox employees are assigned USB drives that generate the one-time passcodes. Once inserted into a computer, employees just need to tap a button to deliver the code.
But Dropbox users haven't embraced two-factor authentication as much as the company would like. Kapoor says a single digit percentage uses two-factor authentication, a figure that it would like to see increase. In August, Dropbox broadened its support for two-factor authentication, announcing compatibility with hardware security keys using the open FIDO Universal 2nd Factor (U2F) standard.
- Details
- Category: Security News
Attackers have healthcare entities in their crosshairs, and their favorite targets are easily-compromised credentials. Tracy Hulver of Synchronoss Technologies offers new ideas for how security leaders can reduce risk and protect sensitive data by better securing identities.
In some ways, healthcare is no different than any other sector, says Hulver, Director of Identity Strategy at Synchronoss. "Everyone is in danger; all the data has a threat against it," Hulver says. "But in other ways healthcare is different because people's privacy is at the heart of healthcare information, so not only is there a financial component and motivator ... but also there's a strong privacy element as well. If there's anything that I want to keep private as a citizen or as an individual, healthcare information is at the top of that [list]."
In an interview on how to strengthen identity management in healthcare, Hulver discusses:
Common characteristics of healthcare breaches; Why healthcare entities have been slow to embrace multifactor authentication; How to gain business support for new ID management solutions.Hulver is director of identity strategy for Synchronoss with responsibility for helping to guide the direction of Synchronoss Universal ID and helping Synchronoss customers reduce the risks of identity fraud through better protection of online credentials. Prior to joining Synchronoss, Hulver was Chief Identity Strategist for Verizon where he helped oversee the company's identity strategy and roadmap.
A well-known industry leader in the areas of cyber-attacks and security intelligence, Hulver is a member of the Computer Security Institute, the National Cyber Security Alliance, the Armed Forces Communications and Electronics Association, the Information Systems Security Association, the Cloud Security Alliance and the Open Identity Exchange. He also served on the Department of Homeland Security's National Cyber Security task force.
- Details
- Category: Security News
CISO , Cybersecurity , Governance
Cybersecurity Employment at Record Levels, But Still Doesn't Meet Demand Competitors at a U.S. Cyber Challenge competition. (Photo: Eric Chabrow)
Competitors at a U.S. Cyber Challenge competition. (Photo: Eric Chabrow)Although an analysis of the latest government statistics confirms continued growth in the information security workforce, the supply of security expertise isn't meeting the demand.
See Also: Managing Identity, Security and Device Compliance in an IT World
Information Security Media Group's analysis of the latest quarterly employment numbers from the U.S. Bureau of Labor Statistics shows the size of the information security analysts workforce has soared by 68 percent since the BLS began producing these jobs reports in 2011.
In the third quarter, the number of workers in the United States who consider themselves information security analysts stood at an annualized 88,000, up from 80,500 in the second quarter and 72,800 a year earlier.
Information Security Analysts Workforce
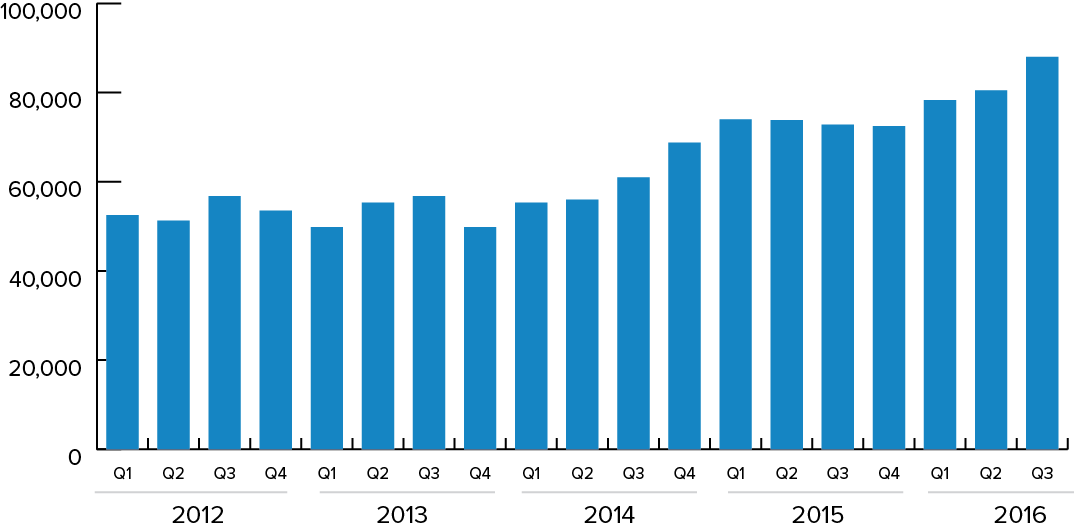 ISMG analysis of U.S. Bureau of Labor Statistics data
ISMG analysis of U.S. Bureau of Labor Statistics dataNumerous efforts are underway to help boost the security workforce. For example, in the past decade, scores of colleges and universities have introduced information security degree programs. Also, many companies have identified workers, often with programming and other computer expertise, and provided them the training to become information security professionals. Among the best known programs are competitions, such as those sponsored by the U.S. Cyber Challenge, which introduces students and young workers to cybersecurity and allows them to participate in contests that tests their security skills.
"The cyber challenges around the country - and world - are a positive influence on building the workforce," says Elise Yacobellis, manager of the Global Information Security Workforce Survey published by (ISC)2, an international, not-for-profit organization that provides IT security education and certification. "They're exposing IT security as a separate profession that could be sought out versus just the IT field. It helps them understand at a hands-on level what they'll possibly be doing if they were to move into this career. And, it also helps them understand if they like it, they have the aptitude for it and this is something they want to pursue."
None of these programs are flooding the job market with IT security specialists, although they're apparently beginning to help add personnel to the cybersecurity employment rolls.
Demand Outstrips Supply
But despite the pickup in the pace of the growth of information security analysts, the supply of IT security expertise isn't meeting the demand. A 2015 study by Frost & Sullivan for (ISC)2 projects a shortfall in worldwide IT security specialist of 1.5 million by 2019.
"Growth is very shallow and is at risk from the perspective that we clearly don't have a good number of deeply experienced professionals in this field," says Danny Miller, systems CISO at Texas A&M University. "I know of companies that have lots of openings, but no qualified personnel to fill them."
Still, IT security expertise can be found in other computer fields, especially database administrators, network and computer systems administrators, computer systems analysts and computer network architects.
And those occupations also are experiencing growth. Computer occupations have seen a steady climb, with more than 5 million people working or seeking work in a variety of information technology jobs, according to the ISMG analysis. That's a jump of 22 percent - or 4.6 percent annualized - since the BLS implemented its new way to calculate employment at the beginning of decade, according to the ISMG analysis.
Computer Occupations Workforce
Third quarter, 2016
| Occupations | Size |
|---|---|
| Computer and information systems managers | 619,000 |
| Computer and information research scientists | 24,000 |
| Computer systems analysts | 528,000 |
| Computer programmers | 483,500 |
| Software developers, applications and systems software | 1,477,800 |
| Web developers | 222,800 |
| Computer support specialists | 556,800 |
| Database administrators | 98,000 |
| Computer occupations, all other | 604,500 |
| Total | 5,041,500 |
Defining InfoSec Occupations
BLS defines information security analysts as those who plan, implement, upgrade or monitor security measures for the protection of computer networks and information. They may ensure appropriate security controls are in place that will safeguard digital files and vital electronic infrastructure and respond to computer security breaches and viruses. Job titles could include computer security specialists, network security specialists and internet security specialist.
Historically, the BLS numbers have reflected IT and information security employment trends. Because of the sample size of the survey, it's not statistically reliable for the information security analysts category. However, on recommendation of BLS economists, ISMG annualizes the survey results, which make them more reliable. That's attained by adding the latest four quarters worth of survey data and dividing the result by four. For example, to arrive at the 88,000 figure for the information security analyst workforce, ISMG took the reported numbers for the last quarter of 2015 and the first three quarters of 2016 then divided by four.
BLS recognizes that shortcomings exist in the way it defines IT and IT security occupations. The bureau says it's revising its Standard Occupation Classification and might add new information security occupation descriptions. BLS says it expects to publish shortly new SOCs that would take effect in 2018. The last update of the SOC occurred in 2010, with the first employment surveys based on it occurring in 2011.
Culling Employment Data
For this report, the workforce numbers come from the government's Current Population Survey of American households, the same survey BLS uses to determine the monthly unemployment rate. Survey takers interviewing households ask respondents characteristics about their jobs and then determine their appropriate occupation category.
BLS each quarter furnishes, upon request, a breakdown of 535 job categories, including the ones labeled information security analysts, database administrators and network and computer systems administrators. Because the survey size for some individual occupation categories, such as information security analysts, is too small to be statistically reliable, BLS neither officially publishes this data, nor claims it's reliable.
More Articles …
Page 3511 of 3545
