- Details
- Category: Security News
Republican presidential candidate Donald Trump laying out his cybersecurity agenda leads the latest version of the ISMG Security Report.
Also in the Security Report (click player above to listen), you'll hear:
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Sept. 27 and Sept. 30 reports, which respectively analyze the massive Yahoo breach that exposed the weaknesses in the way enterprises employ hashed passwords and why cybercrime is on the rise. The next ISMG Security Report will be posted on Friday, Oct. 7.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
How can issuers and acquirers help smaller merchants improve payment card security? One way is to dramatically ramp up their efforts to educate the retailers about PCI compliance, says Michel Christodoulides, Barclaycard's vice president of payment security.
"Small merchants probably suffer most, in many ways, from the payment security breaches," Christodoulides says in an interview with Information Security Media Group conducted at the PCI Security Standards Council's North American Community meeting last month in Las Vegas. "Small merchants are experts in whatever their business is. ... But we shouldn't expect our small merchants to be experts in cybersecurity, information security and the technical language that takes place behind the scenes."
In July, the PCI Council released a compliance resource for small merchants (see Can Banks Help Small Merchants with PCI?).
As an acquirer, Barclaycard, part of the retail and business banking division at London-based Barclays, is now pushing that guidance out to its customers and encouraging other banks to do the same, Christodoulides says. "What we are doing is enabling the small merchant to take advantage of industrywide expertise that's contained within the [PCI Council's Small Merchant] Task Force," he says.
The goal is to help small merchants ensure that they are adequately mitigating their risk of being breached, he adds.
"Let's not be too complacent about this," Christodoulides says. "The criminal is not concerned about which part of the world you're in. The criminal is looking for the easy pickings. And if we can enable our small merchants to make the right decisions by using the guidance that has been published, then that will protect and contribute toward protecting the small merchants."
During this interview (see audio player below photo), Christodoulides also discusses:
The role of the PCI Council's Small Merchant Task Force; How Barclaycard is promoting the new small merchant guidance to is merchant customers; and Why small merchants outside the U.S. need to be more educated about emerging payments risks.Christodoulides represents Barclaycard as a member of the PCI Security Standards Council's board of advisers. He is co-chair of the council's Small Merchant Task Force and is a PCI internal security assessor. At Barclaycard, he focuses on mitigating risks that threaten payment card security.
- Details
- Category: Security News
With passage of the Cybersecurity Information Sharing Act in 2015, Congress authorized the Department of Homeland Security to develop a system in which the federal government and businesses can share cyber threat information (see Obama Signs Cyber Threat Information Sharing Bill ).
Commerce Secretary Penny Pritzker thinks DHS shouldn't have a monopoly on government and businesses sharing cyber threat information. In a recent speech at the U.S. Chamber of Commerce, Pritzker suggests that regulatory agencies should implement cyber threat information sharing programs with the businesses they regulate, not only to enhance their IT security, but to build a collaborative environment between the two, often adversarial sides.
"Pick any cyber breach - Target, Sony, Yahoo; when under attack, these companies do not think about how government can help them," Pritzker said in a speech delivered last week at the U.S. Chamber of Commerce Cybersecurity Summit. "What they see are the downsides of engagement - potential liability, the risk of punitive action and the investigations that may result from even basic interactions. ... We cannot blame executives for worrying that what starts today as an honest conversation about a cyberattack could end tomorrow in a punish-the-victim regulatory enforcement action."
In this audio report (click on player above to listen), you'll hear:
Pritzker explain the reasoning behind getting regulators and regulated companies to collaborate on cybersecurity information sharing; Experts express concerns about how too close of a relationship between the two sides could jeopardize the protections regulations provide the public; and Lawyers representing businesses before regulatory agencies address why such cooperation could enhance cybersecurity among regulated companies.Pritzker became Commerce secretary on June 26, 2013, and had 27 years of private sector entrepreneurial experience before joining the Obama administration. Previously, Pritzker founded and served as advisory board chairman of Skills for America's Future, a national initiative that works directly with employers to develop training mechanisms to prepare workers with in-demand skills.
- Details
- Category: Security News
DDoS , Device ID , Risk Management
IoT Botnets: There Will Be Pwnage Default Usernames and Passwords Drive Hackable Device Smorgasbord Many IoT attacks target default credentials in the firmware that runs internet-connected devices, such as this Dahua Technology camera.
Many IoT attacks target default credentials in the firmware that runs internet-connected devices, such as this Dahua Technology camera.The internet of things is under attack, and the impetus for attackers is clear. Compromising thousands of legitimate devices gives cybercriminals tough-to-trace platforms for launching online attacks, ranging from distributing spam and malware to providing distributed denial-of-service attack services.
See Also: Eight Capabilities IT Pros Should Look for in a CASB
Some individual botnets today comprise 100,000 compromised devices or more, security experts warn. And this has enabled attackers to direct record-shattering amounts of bogus traffic against targets, unleashing DDoS mayhem.
More than a dozen types of common IoT-targeting malware are in use, according to the security firm Symantec. Furthermore, the recent release of source code used to build Mirai malware - which targets IoT devices sporting one of 62 different default passwords, according to the security researcher known as MalwareTech - presages what will surely be an increase in attacks.
Attacked in 60 Seconds
For one measure of the current IoT attack problem's severity, consider a Linux-based digital video recorder that was connected to the internet via a home cable modem by Johannes Ullrich, dean of research for the SANS Technology Institute, to act as a honeypot. The device allows remote logins via telnet, provided a user knows the password, which Ullrich left set to its default. It also used a normal Comcast IP address.
On average, the DVR was successfully exploited at least once every 30 minutes, Ullrich reports. But it also experienced intermittent denial of service conditions due to the volume of remote login attempts.
"The IP address is hit by telnet attempts pretty much every minute," Ullrich says in a blog post. "Instead of having to wait for a long time to see an attack, my problem was that the DVR was often overwhelmed by the attacks, and the telnet server stopped responding. I had to reboot it every few minutes."
Anatomy of an Attack
Many of the remote login attempts use a couple of commands to try and avoid logging into either a router or a well-known type of honeypot, Ullrich notes.
If the login is successful, then the attacker will often attempt to fingerprint the device and implant it with a malicious binary, Ullrich says. The binary file, once executed, starts scanning the internet for more vulnerable IoT devices, typically at a rate of more than 100 connections per second. The list of vulnerable devices is likely then routed back to a command server, so that those devices also can be attacked.
When it came to the DVR honeypot, however, "not all attacks were successful," Ullrich says. "The attacks used various passwords, and my honeypot only allowed logins for one of them. But a couple times an hour, someone used the correct password."
Phoning Home
Ullrich reports that a wave of brute-force telnet login attempts against IoT devices started in mid-September and is continuing.
Security experts say some of those login attempts are coming via Mirai malware. The security researcher known as Hacker Fantastic notes that Mirai-compromised devices will attempt to phone home via port 48101 TCP connections. Security researcher Kyle Lovett reports that as of Oct. 3, he had seen nearly 1 million unique devices creating port 48101 TCP connections. That suggests that the number of IoT devices compromised by Mirai attackers may have reached seven figures.
@hackerfantastic port 48101 has been showing increasingly growing numbers, a week ago around 450k, 2 days ago 850k and 950k today pic.twitter.com/LnOnkD1lnU
Default Problems
The success of these IoT attacks can be directly traced to many manufacturers opting to ship devices that have numerous services - including telnet - enabled by default. Many devices also sport default usernames and passwords, and these have been exhaustively cataloged by penetration testers and hackers and often circulated via "DVR password recovery software."
One commonly seen username plus password combination being tried by IoT attackers, for example, is "root" plus "xc3511," which is used to log into numerous types of DVRs, Ullrich says.
Honeypot Access Attempts
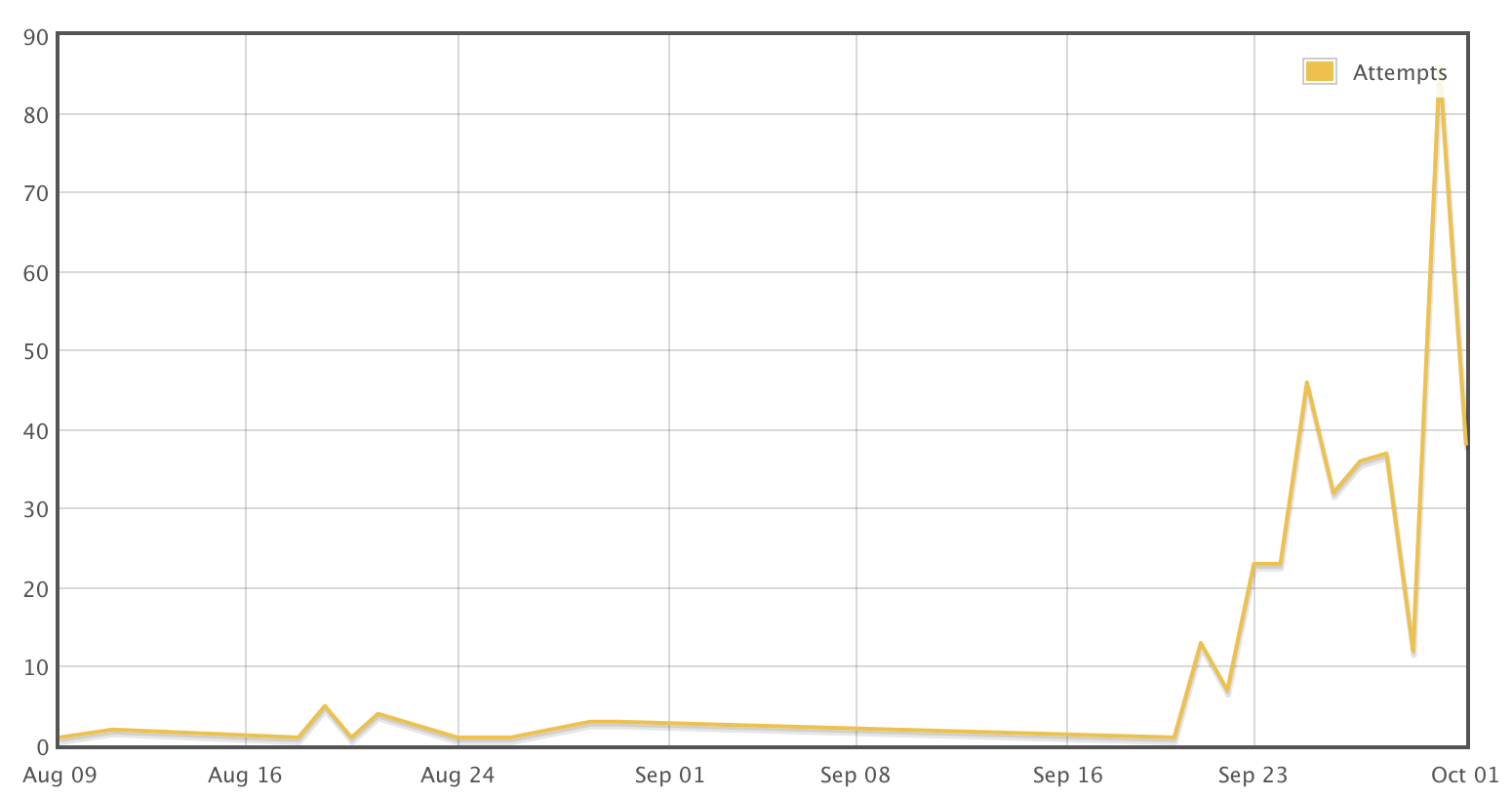 Attempts to use a common, default IoT password - "xc3511" - to remotely access an internet-connected digital video recorder set up by SANS Institute to act as a honeypot.
Attempts to use a common, default IoT password - "xc3511" - to remotely access an internet-connected digital video recorder set up by SANS Institute to act as a honeypot.
Another default password being targeted by attackers is "7ujMko0admin," Ullrich says. As multiple online forums have documented, numerous devices built by Dahua Technology have firmware for which the telnet password is the device's default username and password - both are "admin" - prepended by "7ujMko0." For attackers, compromising devices that have left the default credentials intact takes virtually no effort.
I've reached out to Dahua for comment on the recent wave of IoT attacks that appear to be compromising large numbers of its devices, but have yet to hear back.
Manufacturers' Culpability
A large part of the IoT problem can be traced to manufacturers shipping devices that are not secure by default. Too many IoT devices sport default usernames and passwords and services that are active by default. Both are grossly irresponsible practices. In addition, too few manufacturers support IoT devices - which consumers may leave internet-connected for a decade or more - by issuing firmware updates to fix known flaws throughout the life of the device. And too few have a reliable mechanism for ensuring that still-in-use devices somehow get and install these updates (see The Internet of Buggy Things).
The problem doesn't just involve consumer devices and behavior. I've been told by some manufacturers of carrier-grade and enterprise IT equipment that the system integrators who install their products at customer sites prefer to use equipment that has a default configuration - to make their lives easier. Too often, however, this equipment gets rolled out by less experienced personnel, who leave the defaults intact. As a result, the devices become sitting ducks and are used to attack the rest of us.
Welcome to the growing internet of hacked things.
- Details
- Category: Security News
Anti-Malware , DDoS , Risk Management
Free Source Code Hacks IoT Devices to Build DDoS Army But Code Release Offers No Free Lunch for Cybercrime Script Kiddies Mirai malware targets default accounts and passwords in IoT devices
Mirai malware targets default accounts and passwords in IoT devicesBad news: A hacker has released source code for malware that can be used to automatically find and hack internet of things devices that use default accounts and passwords, then use them to launch distributed denial-of-service attacks. Numerous Linux-based routers, security cameras and digital recorders, among other devices, are at risk and have been compromised in this manner to unleash record-breaking attacks (see Hacked IoT Devices Unleash Record DDoS Mayhem).
See Also: 2016 Annual Worldwide Infrastructure Security Update
Good news: Using the attack code isn't as simple as clicking "compile," meaning that unskilled "script kiddies" may find themselves hard-pressed to create an army of hacked IoT devices ready to do their DDoS bidding.
More bad news: It's a virtual certainty that the leaked code will be widely used, as well as eventually refined and turned into point-and-click attack tools for less technically sophisticated DDoS attackers.
Those are just a few of the takeaways following malware developer "Anna-senpai" releasing for free the supposed source code for Mirai malware, which has been tied to massive DDoS attacks launched via hacked IoT devices.
The source code dump was announced by Anna-senpai Sept. 30 in a post to Hack Forums, a social network devoted to hacking that security experts say attracts numerous hacker wannabes - a.k.a. script-kiddies - who lack technical knowledge but want to know how to bolster their skills. Many cybercrime-as-a-service purveyors advertise their wares on the site.
"Just so it's clear, I'm not providing any kind of 1 on 1 help tutorials," Anna-senpai said, noting that configuring the related scripts should take someone who knows what they're doing less than one hour.
Some security experts say the Mirai botnet appears to be the one that deep-sixed the website of information security journalist Brian Krebs, who ironically was also the first to report on the subsequent source code release. The malware targets Linux systems' SSH or telnet accounts, according to an analysis of the Mirai botnet published by the group of security researchers who are part of the "Malware Must Die" team.
The security researcher known as "Hacker Fantastic," via Twitter, rates the Mirai code "5/10, easy on the eyes, well commented, not an innovative malware but would read again. A++" and says it's designed to disrupt sites via UDP, TCP, DNS, GRE and HTTP attacks.
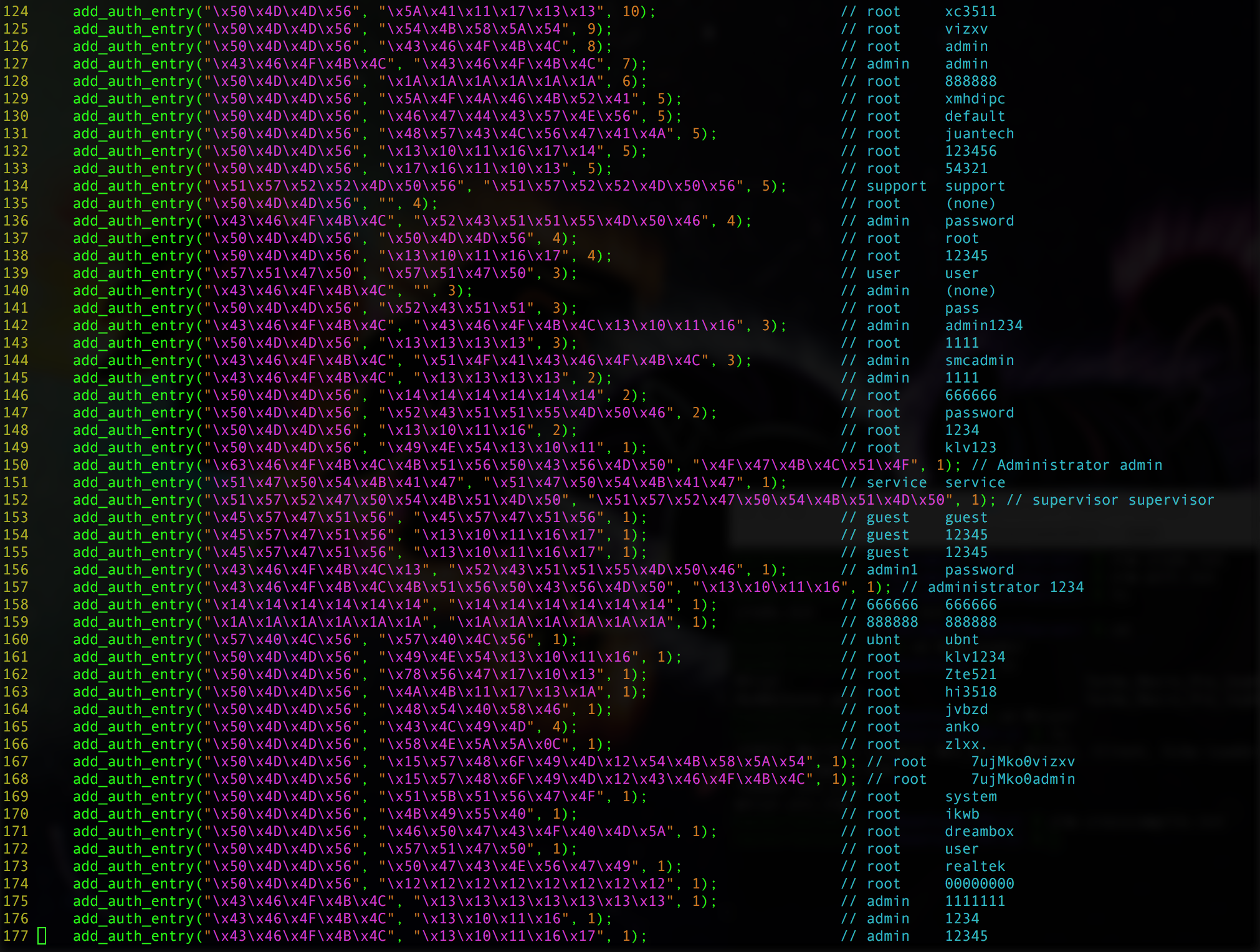 Hacker Fantastic says Mirai targets default credentials in IoT devices.
Hacker Fantastic says Mirai targets default credentials in IoT devices.
Thankfully, getting the code to work requires some technical knowledge. "The Mirai source code appears to be legitimate, but has been modified to mess with scriptkiddies who just compile and run," the security researcher known as Malwaretech says via Twitter.
Anna-senpai claims to now be giving up the DDoS thug life. "When I first go in DDoS industry, I wasn't planning on staying in it long. I made my money, there's lots of eyes looking at IOT now, so it's time to GTFO," Anna-senpai's post reads. "So today, I have an amazing release for you. With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb [sic] DDoS, ISPs been slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping."
Stresser/Booter Options Abound
DDoS attacks and related tools have long been sold via cybercrime sites by groups such as Lizard Squad, often labeled as stresser/booter services.
But Mirai is just one type of malware designed to compromise IoT devices. "We're thinking this is the tip of the iceberg," Dale Drew, head of security at Level 3 Communications, told The Wall Street Journal.
Level 3 operates one of the world's biggest backbones, thus giving it insight into network traffic. It says a notable number of recent DDoS attacks appear to be getting launched via compromised devices - especially security cameras and digital video recorders - built by Chinese manufacturer Dahua Technology. The company's technology is often re-branded and sold by other companies; its website lists dozens of technology partners in the United States alone.
Dahua Technology didn't immediately respond to my request for comment on those reports. But a spokeswoman told The Wall Street Journal that it's reviewing Level 3's research, noted that older devices running outdated software could be easy prey and recommended users set a password on the devices as well as upgrade the firmware.
If all it took to create biggest recorded DDoS attack in history was a telnet scanner and 36 weak credentials the net has a huge IoT problem
Socialism for IoT-Built Botnets
In August, Level 3 reported that it had detected that 1 million IoT devices built by Dahua Technology had been infected with malware called Bashlite - a.k.a. Lizkebab, Torlis, Gafgyt - which is also used to generate DDoS attacks. Together with cybersecurity firm Flashpoint, Level 3 said it was tracking more than 200 related command-and-control servers, which are used to send and receive instructions to hacked devices. Some C&C servers, it added, launched up to 100 attacker per day.
Today, any would-be attackers can tap Bashlite malware. "The source code for this malware was leaked in early 2015 and has been spun off into more than a dozen variants," according to a blog post from Level 3's threat research labs.
No doubt the same will now happen with Mirai source code.
If there's one upside, however small, it's that at least one solo hacker no longer controls thousands of compromised devices, MalwareTech says via Twitter. "Nice thing about the [Mirai] code being public is it mean less devices for any single person to control .... kinda like socialism for botnets."
More Articles …
Page 3508 of 3545
