DDoS , Device ID , Risk Management
IoT Botnets: There Will Be Pwnage Default Usernames and Passwords Drive Hackable Device Smorgasbord Many IoT attacks target default credentials in the firmware that runs internet-connected devices, such as this Dahua Technology camera.
Many IoT attacks target default credentials in the firmware that runs internet-connected devices, such as this Dahua Technology camera.The internet of things is under attack, and the impetus for attackers is clear. Compromising thousands of legitimate devices gives cybercriminals tough-to-trace platforms for launching online attacks, ranging from distributing spam and malware to providing distributed denial-of-service attack services.
See Also: Eight Capabilities IT Pros Should Look for in a CASB
Some individual botnets today comprise 100,000 compromised devices or more, security experts warn. And this has enabled attackers to direct record-shattering amounts of bogus traffic against targets, unleashing DDoS mayhem.
More than a dozen types of common IoT-targeting malware are in use, according to the security firm Symantec. Furthermore, the recent release of source code used to build Mirai malware - which targets IoT devices sporting one of 62 different default passwords, according to the security researcher known as MalwareTech - presages what will surely be an increase in attacks.
Attacked in 60 Seconds
For one measure of the current IoT attack problem's severity, consider a Linux-based digital video recorder that was connected to the internet via a home cable modem by Johannes Ullrich, dean of research for the SANS Technology Institute, to act as a honeypot. The device allows remote logins via telnet, provided a user knows the password, which Ullrich left set to its default. It also used a normal Comcast IP address.
On average, the DVR was successfully exploited at least once every 30 minutes, Ullrich reports. But it also experienced intermittent denial of service conditions due to the volume of remote login attempts.
"The IP address is hit by telnet attempts pretty much every minute," Ullrich says in a blog post. "Instead of having to wait for a long time to see an attack, my problem was that the DVR was often overwhelmed by the attacks, and the telnet server stopped responding. I had to reboot it every few minutes."
Anatomy of an Attack
Many of the remote login attempts use a couple of commands to try and avoid logging into either a router or a well-known type of honeypot, Ullrich notes.
If the login is successful, then the attacker will often attempt to fingerprint the device and implant it with a malicious binary, Ullrich says. The binary file, once executed, starts scanning the internet for more vulnerable IoT devices, typically at a rate of more than 100 connections per second. The list of vulnerable devices is likely then routed back to a command server, so that those devices also can be attacked.
When it came to the DVR honeypot, however, "not all attacks were successful," Ullrich says. "The attacks used various passwords, and my honeypot only allowed logins for one of them. But a couple times an hour, someone used the correct password."
Phoning Home
Ullrich reports that a wave of brute-force telnet login attempts against IoT devices started in mid-September and is continuing.
Security experts say some of those login attempts are coming via Mirai malware. The security researcher known as Hacker Fantastic notes that Mirai-compromised devices will attempt to phone home via port 48101 TCP connections. Security researcher Kyle Lovett reports that as of Oct. 3, he had seen nearly 1 million unique devices creating port 48101 TCP connections. That suggests that the number of IoT devices compromised by Mirai attackers may have reached seven figures.
@hackerfantastic port 48101 has been showing increasingly growing numbers, a week ago around 450k, 2 days ago 850k and 950k today pic.twitter.com/LnOnkD1lnU
Default Problems
The success of these IoT attacks can be directly traced to many manufacturers opting to ship devices that have numerous services - including telnet - enabled by default. Many devices also sport default usernames and passwords, and these have been exhaustively cataloged by penetration testers and hackers and often circulated via "DVR password recovery software."
One commonly seen username plus password combination being tried by IoT attackers, for example, is "root" plus "xc3511," which is used to log into numerous types of DVRs, Ullrich says.
Honeypot Access Attempts
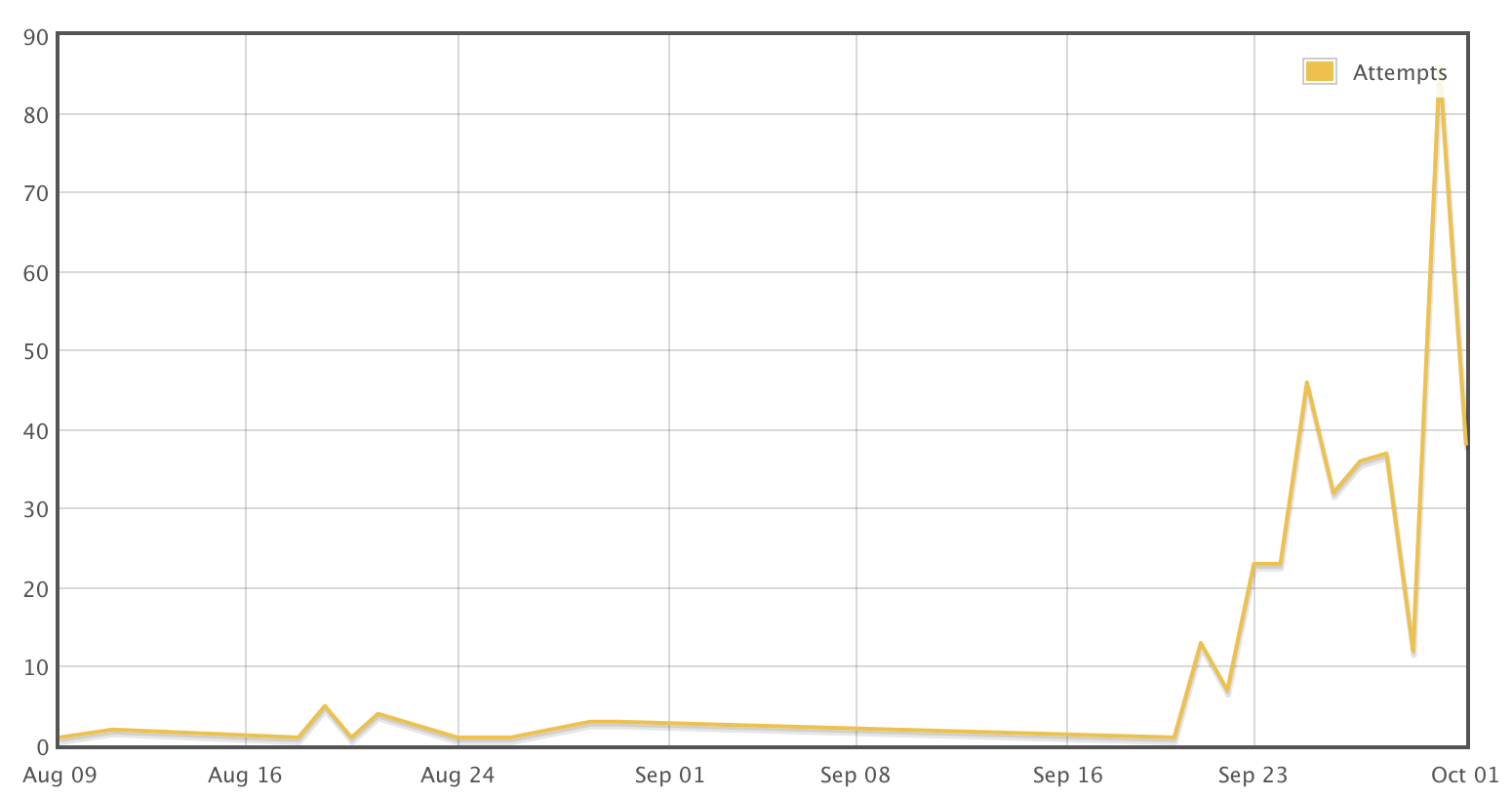 Attempts to use a common, default IoT password - "xc3511" - to remotely access an internet-connected digital video recorder set up by SANS Institute to act as a honeypot.
Attempts to use a common, default IoT password - "xc3511" - to remotely access an internet-connected digital video recorder set up by SANS Institute to act as a honeypot.
Another default password being targeted by attackers is "7ujMko0admin," Ullrich says. As multiple online forums have documented, numerous devices built by Dahua Technology have firmware for which the telnet password is the device's default username and password - both are "admin" - prepended by "7ujMko0." For attackers, compromising devices that have left the default credentials intact takes virtually no effort.
I've reached out to Dahua for comment on the recent wave of IoT attacks that appear to be compromising large numbers of its devices, but have yet to hear back.
Manufacturers' Culpability
A large part of the IoT problem can be traced to manufacturers shipping devices that are not secure by default. Too many IoT devices sport default usernames and passwords and services that are active by default. Both are grossly irresponsible practices. In addition, too few manufacturers support IoT devices - which consumers may leave internet-connected for a decade or more - by issuing firmware updates to fix known flaws throughout the life of the device. And too few have a reliable mechanism for ensuring that still-in-use devices somehow get and install these updates (see The Internet of Buggy Things).
The problem doesn't just involve consumer devices and behavior. I've been told by some manufacturers of carrier-grade and enterprise IT equipment that the system integrators who install their products at customer sites prefer to use equipment that has a default configuration - to make their lives easier. Too often, however, this equipment gets rolled out by less experienced personnel, who leave the defaults intact. As a result, the devices become sitting ducks and are used to attack the rest of us.
Welcome to the growing internet of hacked things.
