- Details
- Category: Security News
Cybersecurity , Risk Management
Researcher Finds Trump Organization Runs IIS 6.0, Windows Server 2003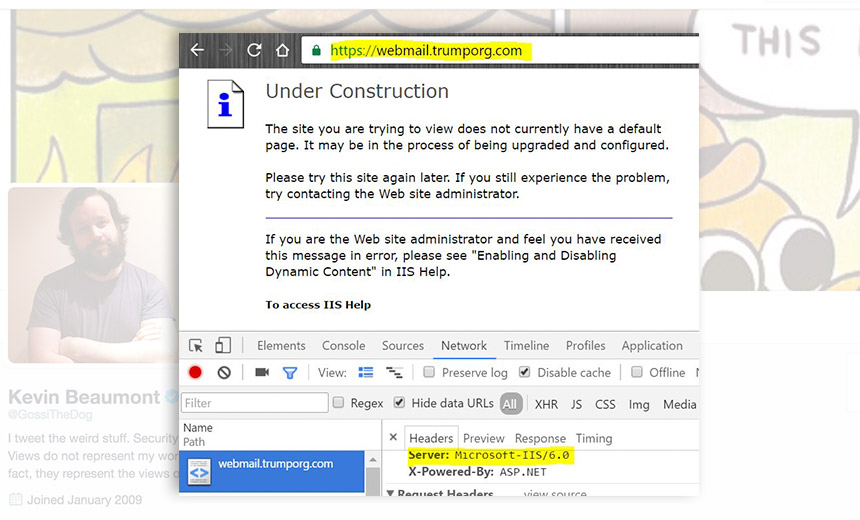 Researcher Kevin Beaumont says webmail.trumporg.com ran Microsoft's Internet Information Services 6.0, a web server that was part of Windows Server 2003.
Researcher Kevin Beaumont says webmail.trumporg.com ran Microsoft's Internet Information Services 6.0, a web server that was part of Windows Server 2003.A U.K.-based researcher using public data found that U.S. presidential candidate Donald Trump's business organization runs email servers using decade-old Microsoft software, posing dangerous security risks. In a presidential election where hackers and cybersecurity have played a large role, it's surprising that the findings didn't come to light sooner.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
Kevin Beaumont, who lives in Liverpool, investigated websites falling under the umbrella of the Trump Organization, which manages the Republican presidential candidate's real estate, golf and hotel businesses.
Beaumont tweeted a screenshot on Oct. 18 that showed webmail.trumporg.com ran Microsoft's Internet Information Services 6.0, a web server that was part of Windows Server 2003. Microsoft stopped developing security fixes for Windows Server 2003 in July 2015.
It appeared that Trump's email systems were accessible from the web, but did not use multifactor authentication, such as one-time passcodes, Beaumont found. The services also don't have a mobile device management feature.
That's a particularly bad oversight, considering the woes of the Democratic Party. It's believed that hackers acting on behalf of Russia obtained critical party correspondence in part by capturing usernames and passwords. Requiring an additional time-sensitive passcode offers greater security if login credentials have been stolen (see DNC Breach More Severe Than First Believed).
But We Have a Firewall
The Trump Organization couldn't immediately be reached for comment. But Beaumont tweeted a statement released by the organization, which downplayed the findings and offered a questionable explanation of why there isn't a problem.
"The Trump Organization deploys best in class firewall and anti-vulnerability technology with constant 24/7 monitoring," it says. "Our infrastructure is vast and leverages multiple platforms which are consistently monitored and upgraded using current cyber security best practices."
Security experts generally recommend moving to current, supported versions of software. Microsoft gives long lead times for when it plans to retire a product, so companies can budget and prepare to migrate to new platforms. Still, some organizations delay those moves, which weakens their defenses against hackers.
Patching as soon as possible is also recommended. But for unsupported software, there are no fixes. In those cases, firewalls or other security software may be ineffective at stopping an intrusion.
In regard to the Trump Organization's statement, Beaumont writes: "That's a bit like saying it's okay to install WordPress and leave it unpatched forever because there's a firewall."
Trump corp have issued a statement saying it doesn't matter if they run Exchange on Win 2003 internet because they have a firewall. pic.twitter.com/F6FmjFE6nN
FBI Contacted
After Beaumont began trickling his findings on Twitter, Trump supporters took him to task and apparently contacted law enforcement. "The FBI and Secret Service had a bunch of complaints from angry people who didn't understand what they were reporting," Beaumont writes.
In subsequent tweets, Beaumont clarified how he obtained the information. He didn't probe the servers other than visiting their domain names and using a feature in the Chrome browser that shows the version of software that runs on the site and also viewing Domain Name System records, which are public.
Beaumont's findings are especially ironic given the almost outsized role cybersecurity has played in the election, from the concerns around Hillary Clinton's use of a private email server while serving as secretary of state to suspected Russian meddling in the election.
Trump extensively criticized Clinton's use of a private email server, which she says she regrets. But while the FBI found Clinton and her staff were careless in handling classified information, the agency did not recommend criminal charges. It's unclear if the email server was compromised by hackers.
On Oct. 7, the U.S. formally accused Russia of coordinating the compromise of political figures' email accounts, leading to emails being posted on websites including DCLeaks.com and Wikileaks. The activity could only have been coordinated by senior Russian officials, the Department Of Homeland Security and Office of the Director of National Intelligence asserted. Russia has repeatedly denied involvement (see US Government Accuses Russia of Election Hacking).
- Details
- Category: Security News
×Close
Request to Republish Content
- Details
- Category: Security News
Since the Federal Financial Institutions Examination Council released its Cybersecurity Assessment Tool in July 2015, banking institutions have raised numerous questions about how they should use the tool to address risk and whether it should be included as part of IT examinations with federal banking regulators (see Banks to FFIEC: Cyber Tool is Flawed).
In response, the FFIEC has released a "frequently asked questions" guide to help clarify how the council expects the tool to be used, experts from one of FFIEC's five regulatory agencies explain in this in-depth interview with Information Security Media Group.
Tim Segerson, deputy director of the Office of Examination and Insurance at the National Credit Union Administration, acknowledges the tool, which sheds light on regulators' expectations, won't answer every question that banking institutions have about the tool. All of the FFIEC agencies, including the NCUA, the Federal Deposit Insurance Corp., the Federal Reserve Board, the Office of the Comptroller of the Currency and the Consumer Financial Protection Bureau, reached a consensus on what was most important to include, he explains.
One key point the FAQ reiterates is that use of the Cybersecurity Assessment Tool is not mandatory, nor is its use a required part of the IT examination process, says Wayne Trout, supervisor of critical infrastructure and cybersecurity within the NCUA's Office of Examination and Insurance.
"On the examination process right now, for institutions that have ... actually gone through and completed the assessment tool, examiners are engaging in conversation with those institutions' managers and determining what the institution rated themselves in the inherent risk profile, as well as [how] the institution rates themselves in the maturity portion of the tool," Trout says.
For instance, by talking with credit unions about how they rate themselves in certain categories, Trout says it became clear to NCUA examiners that some institutions had trouble interpreting portions of the tool, such as those related to the use of cybersecurity controls that might be outsourced to a third party.
During this interview (see audio link below image), Segerson and Trout also discuss:
Why the Cybersecurity Assessment Tool has not yet been automated; How the Cybersecurity Assessment Tool aligns with the NIST Cybersecurity Framework; and How the tool could evolve.At the NCUA, Segerson oversees the operations of the Office of Examination and Insurance and assists the director with implementation of policies related to examinations, supervision and insurance, and guaranty-fund risk management.
Trout, supervisor of critical infrastructure and cybersecurity within the Office of Examination and Insurance, served as an NCUA representatives to the FFIEC Cybersecurity Critical Infrastructure Working Group to assist in developing portions of the Cybersecurity Assessment Tool.
- Details
- Category: Security News
 Czech police released a video of the suspect's arrest.
Czech police released a video of the suspect's arrest.Russian hackers may think twice before traveling outside the country for a vacation in light of the arrest of alleged 2012 LinkedIn hacker "Yevgeniy N." by Czech police at a hotel in Prague earlier this month.
See Also: Avoid Theft of Your Privileged Credentials
Police in the Czech Republic, acting on a red notice issued by Interpol, say they arrested the Russian national 12 hours after receiving information about his whereabouts from the FBI. Red notices are international requests for cooperation - alerts between Interpol's 190 member countries seeking the location and arrest of wanted individuals, potentially for extradition.
Police identified the suspect as "Yevgeniy N.," according to Reuters, saying he's a Russian citizen born in 1987.
LinkedIn issued a statement confirming that the arrest was in relation to the massive data breach that it suffered in 2012, the full severity of which it didn't uncover until four years later.
"Following the 2012 breach of LinkedIn member information, we have remained actively involved with the FBI's case to pursue those responsible," LinkedIn says in its statement. "We are thankful for the hard work and dedication of the FBI in its efforts to locate and capture the parties believed to be responsible for this criminal activity."
Czech police arrest alleged Russian hacker in relation to 2012 LinkedIn breach investigation.After the suspect was arrested at a Prague restaurant - where he was dining with his girlfriend - Czech police say he collapsed and required medical assistance and was briefly hospitalized before being returned to custody.
Police say they expect the suspect to soon face extradition proceedings initiated by the United States, with which the Czech Republic has an extradition treaty. The U.S. has two months to file related paperwork.
But the Russian government is already demanding the suspect's return.
"The embassy has been taking all necessary efforts to protect the interests of this Russian citizen," Russian Embassy spokesman Andrey Kolmakov told Russian news service TASS. "We are in contact with his attorney. Russia repudiates Washington's policy of imposing its extraterritorial jurisdiction on all countries. We insist that the detainee is handed over to Russia."
Endangered: Hacker Holidays
The arrest is no doubt already sending shock waves throughout the cybercrime community. Indeed, Nicholas Weaver, a researcher who focuses on computer security at the International Computer Science Institute in Berkeley, Calif., warns that the arrest highlights cybercriminals' rapidly disappearing vacation options.
"As a Russian hacker, your only vacation spot left is Sochi," he says via Twitter, referring to Russia's largest seaside resort city.
Breach Coda
The arrest also serves as a potential breach coda for LinkedIn, which has been criticized for failing to force all users to reset their passwords after 6.5 million password hashes showed up on a password-cracking forum in 2012 (see LinkedIn's Password Fail). Earlier this year, however, it came to light that attackers actually stole details on 165 million users' accounts, in what now ranks as one of the largest breaches in history.
The severity of the breach was further compounded by LinkedIn in 2012 using the SHA-1 hashing algorithm. Passwords shouldn't be stored in plain text, so algorithms are used to convert a password into a hash, or a cryptographic representation, which, in theory, cannot be reverse-engineered. But even four years ago, security experts were warning that SHA-1 was weak, inappropriate for hashing passwords and could be easily cracked. Following the breach, however, LinkedIn hired a CISO and overhauled its password and other security practices.
Cybercrime Travel Secrets
To date, Russia has extradited no cybercrime suspects to other countries. In fact, so long as cybercriminals operating from parts of the former Soviet Union follow a few rules, such as not stealing money from Russian banks, they have little chance of being locked up.
Faced with that reality, the U.S. Justice Department has resorted, in part, to a tactic it calls "informal extradition," but which others might call kidnapping. It involves federal agents intercepting a suspect abroad, flying them to U.S. territory, charging them and then bringing them before a judge.
For example, Russian hacker Roman Seleznev was grabbed by U.S. Secret Service in 2014 while he was vacationing in the Maldives. While that country has no extradition threat with the United States, it apparently sanctioned the moves. Seleznev was convicted in August of defrauding 3,700 financial institutions in the United States of at least $169 million.
Similarly, Russian hacker Vladimir Drinkman was arrested while in Amsterdam in 2012, at the U.S. Justice Department's request. He pleaded guilty last year in connection with a hacking scheme that resulted in the theft of more than 160 million payment card numbers.
The FBI's Modus Operandi
Those arrests highlight the FBI's long-standing modus operandi. As FBI supervisory special agent Elvis Chan noted in a panel in March at the Information Security Media Group's Fraud and Breach Prevention Summit in San Francisco, criminals might get away with their crimes in the short term, or hide out in jurisdictions that U.S. prosecutors can't reach. But he said the FBI's memory - and reach - is long.
"We are relentless; we are going to turn over every stone to make sure that we get the job done," Chan said.
- Details
- Category: Security News
 Julian Assange pictured in 2013 in Ecuador's embassy in London with Ecuadorian politician Ricardo Armando Patiño Aroca. Photo: Xavier Granja Cedeño (Flickr/CC)
Julian Assange pictured in 2013 in Ecuador's embassy in London with Ecuadorian politician Ricardo Armando Patiño Aroca. Photo: Xavier Granja Cedeño (Flickr/CC)What does the world's self-proclaimed leaker in chief do when his internet connection gets severed? Maybe he can put his feet up, read a few thrillers and take up knitting?
See Also: Managing Identity, Security and Device Compliance in an IT World
That seems the perilous prospect now facing Julian Assange, the Australian founder of WikiLeaks, which bills itself as an international non-profit journalistic organization focused on publishing secret information.
WikiLeaks announced Oct. 17 that Assange's internet connection had been cut Oct. 15, after the organization published what appeared to be transcripts of three speeches delivered by Democratic presidential candidate Hillary Clinton to financial services firm Goldman Sachs. The speeches were delivered after Clinton retired from her role as Secretary of State in 2013 and before she began her presidential campaign in 2015, and appeared to have been stolen from Clinton campaign chairman John Podesta's email account, CNN reports.
WikiLeaks blamed "a state party" for Assange's sudden internet outage. "We have activated the appropriate contingency plans," it added, without elaborating on what that cloak-and-dagger statement was supposed to mean.
Julian Assange's internet link has been intentionally severed by a state party. We have activated the appropriate contingency plans.
Timeout for Political Inference
On Oct. 18, however, the government of Ecuador, which earlier granted Assange asylum in its London embassy, announced that it was the state party in question, and emphasized that WikiLeaks' leaks have been entirely the organization's own doing.
"Ecuador has exercised its sovereign right to temporarily restrict access to some of its private communications network within its embassy in the United Kingdom," according to an official communiqué issued by the Ecuadorian government. "This temporary restriction does not prevent the WikiLeaks organization from carrying out its journalistic activities."
The statement adds: "The Government of Ecuador respects the principle of non-intervention in the internal affairs of other states. It does not interfere in external electoral processes, nor does it favor any particular candidate."
Despite the temporary restriction, Ecuador says that it will continue to offer asylum to Assange and "safeguard his life and physical integrity until he reaches a safe place."
Official Communiqué | Ecuador respects the principle of non-intervention in the internal affairs of other states https://t.co/4F7R5Iktsd pic.twitter.com/5FtbLViMEo
— Foreign Affairs Ec (@MFAEcuador) October 18, 2016The move follows WikiLeaks having been accused by some security experts of acting as a propaganda arm for the Russian government. The organization was explicitly cited by the U.S. Department Of Homeland Security and Office of the Director of National Intelligence earlier this month when it blamed the Russian government for attempting "to interfere with the U.S. election process" via "the recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona" (see U.S. Government Accuses Russia of Election Hacking).
WikiLeaks, meanwhile, alleges that Ecuador severed Assange's internet access under pressure from the U.S. government, saying Secretary of State John Kerry made a related request while in Colombia last month with Ecuadorean President Rafael Correa, during a show of unity over the country's peace deal with leftist rebels, The Associated Press reports.
The State Department, however, has denied those allegations. "While our concerns about WikiLeaks are longstanding, any suggestion that Secretary Kerry or the State Department were involved in shutting down WikiLeaks is false," U.S. State Department spokesman John Kirby tells The Associated Press. It adds that deputy spokesman Mark Toner reports that Kerry neither mentioned the issue nor met with Correa during his Colombian visit.
A History of Leaks
Founded in 2006, WikiLeaks earned plaudits from many quarters in 2010 when it published a chilling, classified U.S. Army video of an Apache helicopter crew in Baghdad, leaked by Chelsea Manning. The video shows the gunship firing on and killing 11 adults - including two Reuters reporters - and seriously injuring others, including two children. Later that year, meanwhile, as part of "Cablegate," the organization leaked an archive of 251,287 sensitive U.S. State Department cables.
In June 2012, facing questioning by Swedish prosecutors over a sexual-assault allegation - which he denies - Assange entered the Ecuadorian embassy in London and requested asylum, which the Ecuadorian government granted two months later. He's been in the embassy ever since, and WikiLeaks has continued to leak documents.
More recently, however, the group has come under fire for appearing to take sides in the U.S. presidential election, with Assange regularly voicing antipathy for Clinton - as he has in the past - and WikiLeaks releasing stolen Democratic National Committee emails.
Those moves prompted allegations that WikiLeaks has been acting on behalf of Russian intelligence, as encapsulated in a front-page feature in The New York Times titled: "How Russia Often Benefits When Julian Assange Reveals the West's Secrets."
WikiLeaks, however, dismissed that report and similar allegations as "conspiracy theory," including allegations that it avoids criticizing the Russian government. "WikiLeaks has published more than 650,000 documents about Russia & president Putin, most of which is critical," it said.
Privacy Backlash
But the value of some of the group's leaks has regularly been called into question, such as a recently leaked email exchange between Clinton's campaign chairman, Podesta, and Center for American Progress president Neera Tanden. In the alleged exchange, both criticize attorney and activist Lawrence Lessig, a Harvard University professor who was also briefly a candidate for the Democratic presidential nomination.
Following the leak and airing of Podesta and Tanden's alleged criticism of him, Lessig issued a classy response. "I'm a big believer in leaks for the public interest. That's why I support Snowden, and why I believe the President should pardon him. But I can't for the life of me see the public good in a leak like this - at least one that reveals no crime or violation of any important public policy," he said.
"We all deserve privacy," Lessig added. "The burdens of public service are insane enough without the perpetual threat that every thought shared with a friend becomes Twitter fodder."
This piece has been updated to detail the WikiLeaks allegations against Secretary of State John Kerry.
More Articles …
Page 3517 of 3545
