- Details
- Category: Security News
Evaluating ways to thwart massive distributed denial-of-service attacks leads the latest edition of the ISMG Security Report.
In the report, you hear (click on player to listen):
ISMG Security and Technology Managing Editor Jeremy Kirk assess long-shot approaches to foil massive DDoS attacks such as the one that last week targeted domain name system services provider Dyn, and limited access to popular internet sites; About how Chinese manufacturer Xiongmai Technologies plans to fix its products to prevent their use in DDoS attacks; DataBreachToday Executive Editor Mathew J. Schwartz explain how "conspiracy theories" will play out on Verizon Communications' planned acquisition of the internet company Yahoo, which continues to reel from a 2014 massive breach; and National Institute of Standards and Technology information risk guru Ron Ross describe the importance of changes in the wording of NIST's highly used security and privacy guidance.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Oct. 18 and Oct. 21 reports, which respectively analyze the financial services industry reaction to the latest state banking cybersecurity regulations and the likelihood of a hack to alter votes in this year's U.S. presidential election. The next ISMG Security Report will be posted on Friday, Oct. 28.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
Business Continuity/Disaster Recovery , Cybersecurity , Governance
Cyber Mandates for Big Banks Would Build on Earlier Guidance Regulators' Proposed Standards Would Ensure Institutions Are Taking Necessary Steps The Federal Reserve and two other regulators published proposed cybersecurity mandates.
The Federal Reserve and two other regulators published proposed cybersecurity mandates.Proposed federal cybersecurity standards for the nation's largest banks aim to mandate how banks must address risk management, business continuity and incident response (see Tough Federal Cybersecurity Standards for Big Banks Proposed).
See Also: Secure Access in a Hybrid IT World
But the proposed mandates shouldn't come as a big surprise because they're just an extension of what federal regulators have been suggesting for years in their guidance.
Enacting true mandates,, rather than guidance, however, shows that regulators want assurances that big banks are actually doing what's been recommended to mitigate risks associated with cyberattacks.
If the nation's leading banks have not already implemented most of the proposed requirements, including ensuring hands-on cybersecurity oversight from executive management and boards of directors, then shame on them.
Standards Won't Be Rushed
It could be a year or more before we see a final version of the proposed standards.
The Federal Deposit Insurance Corp., the Federal Reserve Board and the Office of the Comptroller of the Currency - the three Federal Financial Institution Examination Council agencies that published the proposal for new standards - are accepting comments until Jan. 17. After that, the comments will be reviewed by all five FFIEC agencies before new mandates are finalized and published. By then, the standards could be revised.
And keep in mind, the regulators are proposing that only institutions with $50 billion or more in assets be required to comply with the new standards.
The Proposal's Highlights
One of the more noteworthy proposed mandates is the call for holding boards and senior management more accountable for implementing cyber risk management frameworks. Regulators also propose that the nation's big banks take steps to ensure that board members have "adequate expertise" in cybersecurity.
In earlier guidance, regulators made it clear that boards and senior management need more cybersecurity involvement (see FFIEC Updates Cybersecurity Expectations for Boards).
The proposed mandates would ensure that banks are following through.
Regulators also want service providers used by banks and/or those linked to the financial infrastructure, such as payments processors, to be held to the same cybersecurity requirements that the banks they work with are.
So, third-party service providers working with the country's largest banks could have to adhere to the same federal mandates, once they're enacted.
Most of those providers are already examined by federal banking regulators, so imposing stricter requirements is not so much of a stretch. And banks will likely have to ensure in their contracts, as well as through ongoing due diligence, that their service providers are maintaining compliance with security mandates.
Banking regulators have expressed concern about the need to better mitigate third-party cyber risks for the past two years (see OCC Expands on Third-Party Cyber-Risks).
Resiliency Concerns
In an effort to ensure that the big banks aren't crippled by a significant cyberattack, such as a distributed denial-of-service attack, regulators propose mandating that banks take steps to ensure they can bounce back from a cyberattack within two hours of being targeted.
Cyber resiliency became a priority in the wake of the 2012-2013 DDoS attacks (see Hacktivist Speaks Out About DDoS), when many top-tier banks were caught off guard and, in some cases, had their online banking sites taken offline for hours, if not days.
Since then, however, leading banks have enhanced cyber threat information sharing efforts and updated their DDoS mitigation strategies to help them prepare.
Now regulators want to make sure the nation's largest banks remain vigilant by continually testing and upgrading their defenses and systems to ensure they're prepared for evolving attacks and threats (see DDoS Attack Blamed for Massive Outages).
The proposed federal cybersecurity standards will put more pressure on the nation's top banks to make certain that their cybersecurity strategies are as complete and effective as possible. And if banks have been paying attention to earlier guidance, compliance shouldn't be challenging.
- Details
- Category: Security News
Application Security , Endpoint Security , Risk Management
Weak Drivers Key to Compromising macOS Researcher Patrick Wardle Finds Ways to Get Inside the All-Important Kernel
When he's not surfing Hawaiian waves, Patrick Wardle spends considerable time figuring out new ways to hack Apple's operating system, macOS. Although Apple has maintained for more than a decade its security superiority over Windows, it's only truly hardened the OS in the last few years.
See Also: Managing Identity, Security and Device Compliance in an IT World
Wardle, who is director of research with Synack, says the days of finding a single software flaw in say, Safari, that yields full control over a Mac are long over. From isolating apps in sandboxes to code signing to the sealing of critical OS areas using System Integrity Protection, or SIP, hackers now face imposing obstacles.
His latest research, presented last weekend at the Ruxcon security conference, has focused on Apple's I/O kit, the company's platform for writing software drivers - the code for working with a computer's software and hardware.
"It's just tough to write secure drivers, and a lot of the code is very, very, very complicated," Wardle says. "From a bug hunter's view, it's a very good place to look."
Many bugs have been found in I/O kit drivers, Wardle says. Some of those drivers have authority to interact with macOS's kernel, the core, most sensitive part of the operating system. That's the place where hackers want to be, especially because Apple curtailed the power of root access with SIP.
"Nowadays on modern Mac operating systems, you pretty much need a kernel vulnerability in order to really own or infect the box in a good way from the malware's point of view," Wardle says.
Apple highly restricts what apps can get access to the kernel. Most applications don't need access to the kernel. But security applications do because it's a crucial area that needs monitoring.
In order to get kernel access, developers must apply for a kernel-signing certificate, and Apple closely vets those applicants. It even took Wardle, who frequently corresponds with Apple security's team, awhile to obtain one.
Cracking Kernels
Wardle actually started investigating how to get access to the kernel almost three years ago. As part of this research, he took a look at Little Snitch, a network monitoring tool made by Objective Development Software, a German company.
He found a way to exploit Little Snitch in order to get kernel access. But there was a problem: An obscure bug on Apple's side prevented the exploit. In a type of perverse reporting process, Wardle reported that bug to Apple, which took almost two and a half years to fix it. But once it was fixed, his Little Snitch attack worked. He reported the Little Snitch flaw, a buffer overflow, to Objective Development Software, which fixed it within three weeks.
For a successful attack to be executed remotely, Wardle says he would need another flaw in an application such as Safari to get on the system. Then, the Little Snitch driver could be loaded and the exploit launched.
It doesn't matter whether the user on the system at the time has root access or is a guest user, he says. "You can escalate from that all the way to the kernel because there's an installed kernel driver that has a bug," he says.
Because Little Snitch's kernel driver is signed, there's no protesting from AV products or other Apple security features, such as SIP, about the attack. While patching its bug, Little Snitch also fixed a behavior that allowed any code to talk to its kernel driver. Now Wardle says the application only allows its own components to talk to the driver.
"So even if there is other buggy code, it kind of shuts down that attack surface," Wardle says.
What can users take away from the findings? Be aware that some applications, particularly security ones, may have kernel-level access, so it's good to be judicious when considering whether to install one. And for driver developers: Be very careful, because a mistake could be very bad for users.
- Details
- Category: Security News
Anti-Malware , DDoS , Technology
Can't Stop the Mirai Malware So Save Yourself, and Maybe the Rest of Us Too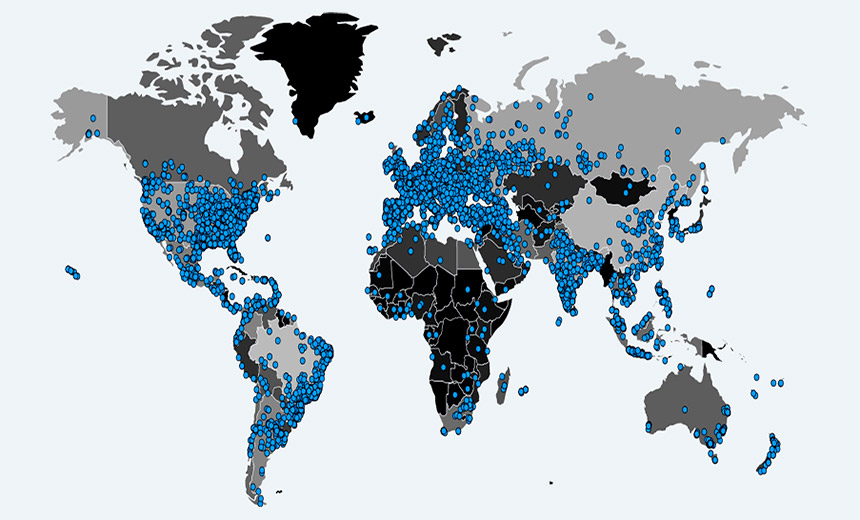 Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source: MalwareTech
Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source: MalwareTechInternet of things security takeaway: Save yourself. And by doing so, maybe help save the rest of us too.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
That's the obvious takeaway from the rise of low-tech, high-impact Mirai malware, which was built to exploit the default usernames and passwords used by dozens of different manufacturers' IoT devices. It's also been tied to the record-setting distributed denial-of-service attacks against domain name server provider Dyn on Oct. 21, which resulted in widespread internet outages, preventing users from reaching such leading websites as Amazon, PayPal, Spotify and Twitter.
Just as some vaccines provide a "herd effect" - indirectly protecting people at risk of a disease by ensuring there's a large population that's immunized against it - the more individuals and organizations that proactively secure their IoT devices, the better off we'll all be.
Unfortunately, it's going to be a long time - read: never - before we see the equivalent of IoT herd immunity against information security threats.
"Mirai is a huge disaster for the internet of things," Hangzhou Xiongmai Technologies spokesman Cooper Wang tells Information Security Media Group. Xiongmai is the manufacturer of some of the many different types of IoT components and circuit boards targeted by Mirai. The manufacturer promised to recall some of that technology, or at least release more secure firmware.
Meanwhile, the U.S. Department of Homeland Security says it's "working with law enforcement, the private sector and the research community to develop ways to mitigate against [Mirai] and other related malware." It plans to develop and release "a set of strategic principles for securing the internet of things ... in the coming weeks."
Both of those moves, however, require manufacturers of low-cost devices as well as the users - including millions of consumers - who rely on them to up their security game. And that's a long shot.
Far From Sophisticated
Compounding the problem: Mirai-type attacks are not complex.
"I'm not quite sure when people are going to realize that the Internet and the web are running on protocols that were never intended to be secure, and as such it's almost inevitable that these guys will find a way of attacking," University of Surrey computer science professor Alan Woodward tells me.
"It's not sophisticated, it's not clever, it's just waiting to happen," he adds.
Mirai Botnet: Unique IP Addresses Seen
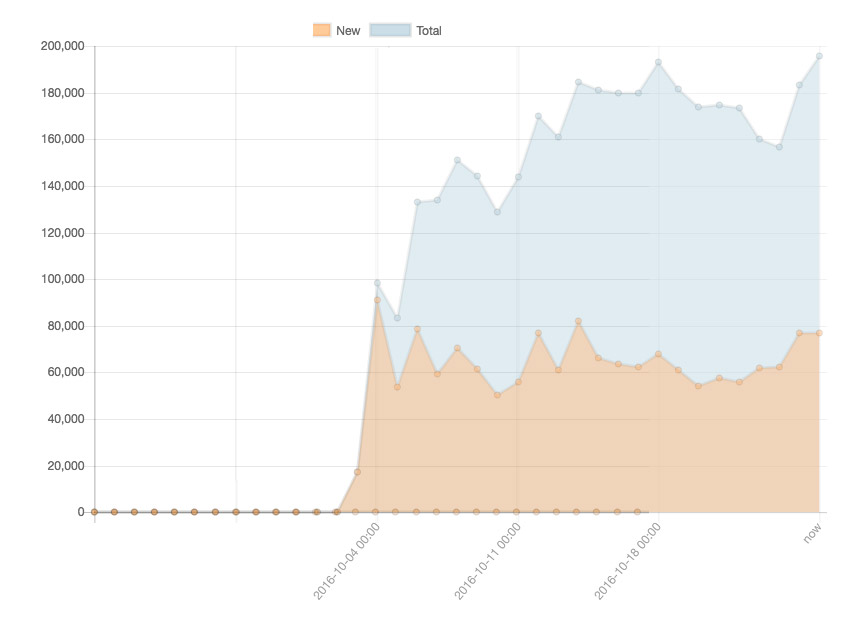 Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source: MalwareTech.
Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source: MalwareTech.Bet on Teenagers
Who's to blame? From an attack standpoint, there's abundant, albeit anecdotal, evidence that an individual or outfit calling itself Poodlecorp originally developed Mirai and used it to disrupt online gaming. Historically speaking, that's the M.O. of stresser/booter service providers, sometimes run by non-advanced but highly persistent teenagers.
"Mirai was once [controlled] by PoodleCorp and they even stated they would attack on the 21st [of October], specifically EA's Battlefield 1 launch day," Bryant Townsend, CEO of DDoS defense firm BackConnect, tells me. "Since their tweet about this, the Mirai source code was publicly released, which now makes it difficult to attribute the attack to any individual or organization."
October 21st #PoodleCorp will be putting @Battlefield in the oven
The Oct. 21 attacks did appear to disrupt some players of Electronic Arts' game, at least ones who were using the PlayStation Network.
Rise of the Exploiters
The ability to consistently marshal attacks of the size that targeted Dyn has implications. "What we do know is that an individual or organization has achieved hegemony over the botnet, as it would not be possible to launch an attack of this size unless they were in complete control over all of the infected IoT devices," Townsend says. "There is also the possibility of attackers using multiple botnets in addition to Mirai to increase the attack size, but we haven't seen anything to indicate this yet."
Already, rival online gangs are vying for vulnerable IoT devices, developing malware that removes rivals' botnet software from such devices. "There is a never-ending underground war for vulnerable IoT devices to be used for DDoS attacks," Townsend says. "Topple the current leader of this war, and the others will soon be fighting to claim their throne."
Design Philosophy: Battle IoT Breaches
Blocking IoT attacks isn't conceptually complex, and as the security researcher known as "SwiftOnSecurity" notes, we've solved these types of problems before.
"Assume breach" is a systems monitoring and information architecture approach, NOT a statement of the status of all electronic devices.
Xiongmai, for example, has promised to stop enabling telnet by default in its IoT components, as well as to prompt users to change default usernames and passwords, both of which have been exploited by Mirai. It's also advising users to firewall the devices and block all unnecessary ports.
Minneapolis-based IT consultant Rich Farris did just that when he found himself having to deal with internet-connected security cameras that had been infected with malware and used to launch DDoS attacks, despite his having changed their default usernames and passwords (see How an IT Pro Kicked Hackers Off Surveillance Cameras). With his customer not wanting to throw the cameras away and buy new ones, he put them behind a firewall, blocking all ports except the ones required for audio, video and to access the web-based admin panel. He then reinstalled a clean copy of the firmware.
That's one hands-on but relatively non-complex way that vulnerable IoT devices can be safeguarded, making them unavailable for malware-wielding attackers' exploitation. But realistically, how many other such IoT-using consumers or even some administrators will also be able save themselves, and by extension the rest of us?
- Details
- Category: Security News
 StarHub's headquarters
StarHub's headquartersThe massive attack against U.S.-based domain name server provider Dyn isn't the only such disruption launched by internet of things devices that's been seen in recent days.
See Also: Avoid Theft of Your Privileged Credentials
Just after Dyn was targeted with distributed denial-of-service attacks that disrupted its DNS services, blocking access to major websites for many internet users, Singaporean ISP StarHub suffered two similar DNS attacks.
StarHub has blamed the attacks on malware-infected IoT devices owned by its customers.
"We are now able to confirm that we had experienced intentional and likely malicious distributed denial-of-service attacks on our domain name servers," StarHub says in a Facebook post to customers. "These two recent attacks that we experienced were unprecedented in scale, nature and complexity."
DNS services resolve domain names into internet protocol addresses, which is how machines and systems reach websites.
"This is the first time that Singapore has experienced such an attack on its telco infrastructure," Singapore's Cyber Security Agency and Infocomm Media Development Authority said in a joint statement, reports Singapore's The Straits Times.
IoT Devices Blamed
Speaking at an Oct. 26 press conference, StarHub CTO Mock Pak Lum said the company traced the attacks to infected devices - such as webcams and routers - owned by subscribers and advised consumers to only purchase the devices from reliable vendors, The Strait Times reports. He added StarHub would "soon" dispatch technicians to help customers clean any malware-infected devices (see Mirai Aftermath: China's Xiongmai Details Webcam Recall).
StarHub says the attacks against it involved a "sudden and huge increase in traffic load" on Oct. 22, the same day that the seventh annual StarHub TVB Awards aired. The awards involve viewers as well as a panel of judges voting for their favorite actors, actresses and television programs on Hong Kong's TVB station. Winners this year included actress Nancy Wu for "A Fist Within Four Walls" and actor Wayne Lai for "Short End of the Stick," among others.
StarHub said it was targeted by a second wave of attacks on Oct. 24.
"On both occasions, we mitigated the attacks by filtering unwanted traffic and increasing our DNS capacity, and restored service within two hours," StarHub says. "No impact was observed on the rest of our services, and the security of our customers' information was not compromised. We kept customers informed on these matters via our hotline and social media."
We're aware that some broadband customers are facing difficulties accessing the internet. For more information visit https://t.co/GpRC2eFWXF
Home Broadband Disrupted
StarHub says that home broadband users were affected, but not enterprise, mobile or home voice customers. So far, the ISP says it does not know who launched the attacks or what their motivation might have been. "We continue to stay vigilant against possible follow-up DDoS attempts. In addition, we are working closely with the authorities to determine intent and source of these two DDoS attacks," StarHub says.
Singapore's Cyber Security Agency and IMDA have warned other ISPs and telecommunications providers to beware of similar attacks and have also called on IoT device owners to keep their devices secure. "Given the increasing connectedness of digital systems, there is no fool-proof solution. It takes a collective effort from companies and society to bolster our cyber resilience," they said.
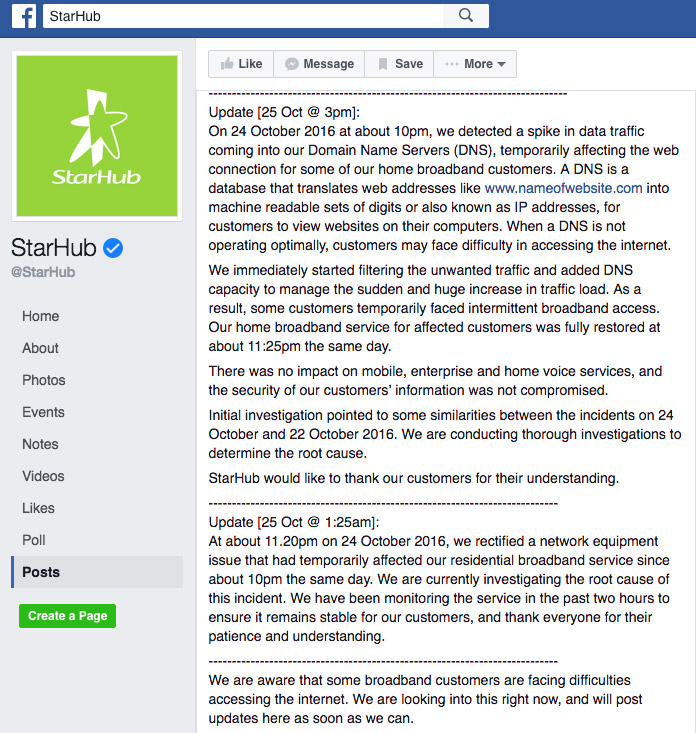 StarHub's communication to customers via Facebook.
StarHub's communication to customers via Facebook.A StarHub spokesman tells Information Security Media Group that the ISP has begun scheduling home visits for customers whose devices it's identified as being involved in the attacks. "During the home visits, our technical service officers 'HubTroopers' will conduct an onsite investigation before helping the customers secure any unsecured internet connected devices," he says. "These may include installing anti-malware software, changing default passwords, updating device software, fixing device misconfiguration and/or replacing devices."
The spokesman adds that StarHub is also encouraging all customers "to review the security settings of their internet-connected devices and disconnect any suspect device."
No Word on Malware Used
StarHub declined to comment on a request for more information about the attacks, including the type of malware that was used and whether the infected devices included any IoT devices - such as routers - supplied by the ISP to its customers.
So it's not clear if the ISP was targeted by IoT devices infected by Mirai malware, or a different type of malware, such as Bashlite - a.k.a. Lizkebab, Torlis, Gafgyt. According to telco Level 3 Communications and security intelligence firm Flashpoint, there are more than 200 separate command-and-control servers for Bashlite. Since July, the largest of those botnets was controlling 120,000 infected devices, the firms reported last month.
Dyn, meanwhile, says that its ongoing investigation into the DDoS attacks against it has found that the attack was launched by "up to 100,000" IoT devices, and that "a significant volume of attack traffic originated from Mirai-based botnets.
This story has been updated with comment from StarHub.
More Articles …
Page 3521 of 3545
