Cybersecurity , Data Loss , Governance
Data Security Risk: A CISO's Perspective- Details
- Category: Security News
Cybersecurity , Risk Management
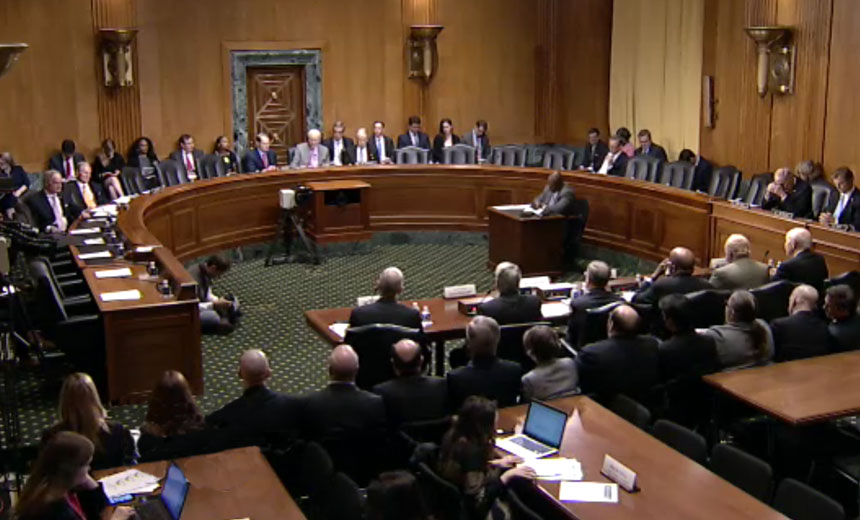
Obama Also Names MasterCard CEO to Group Working on Strategies Ex-NSA Director Keith Alexander, left, joins the Commission on Enhancing National Cybersecurity.
Ex-NSA Director Keith Alexander, left, joins the Commission on Enhancing National Cybersecurity.Keith Alexander, former National Security Agency director, and Patrick Gallagher, who once headed the National Institute of Standards and Technology, will join Ajay Banga, chief executive of MasterCard, on the new Commission on Enhancing National Cybersecurity.
See Also: Unlocking Software Innovation with Secure Data as a Service
The commission's members, appointed by President Obama, also include Tom Donilon, the former White House national security adviser, who was previously announced as chairman, and Samuel Palmisano, IBM's former leader, who is vice chairman.
Alexander, who also served as commander of the U.S. Cyber Command, is CEO of IronNet, a cybersecurity consultancy he founded in 2014. Gallagher left NIST in 2014 to become chancellor and chief executive of the University of Pittsburgh.
The commission, which holds its first meeting this week, has a Dec. 1 deadline to produce a report that will advise Obama and the next president on steps the government and private sector can take over the next 10 years to improve cybersecurity.
Other Commission Members
Other members of the commission named April 13 by President Obama include:
Annie Antón, professor and chair of the School of Interactive Computing at the Georgia Institute of Technology; Steven Chabinsky, general counsel and chief risk officer at security provider CrowdStrike and former deputy assistant director of the FBI's cyber division and chief of the FBI's cyber intelligence section; Peter Lee, corporate vice president at Microsoft Research; Herbert Lin, senior research scholar for cyber policy and security at the Center for International Security and Cooperation and a research fellow at the Hoover Institution, both at Stanford University; Heather Murren, private investor and member of the board of trustees of the Johns Hopkins University and the Johns Hopkins University Applied Physics Laboratory; Joe Sullivan, chief security officer at Uber and former CSO at Facebook and assistant U.S. attorney for computer hacking; and Maggie Wilderotter, former CEO and executive chairman at Frontier Communications.The Republican and Democratic leaders of the House and Senate were invited to recommend one commission member each, according to the executive order establishing the commission. The White House did not disclose which of the 12 commission members, if any, were suggested by lawmakers.
Cybersecurity National Action Plan
The commission is part of the administration's Cybersecurity National Action Plan, which Obama said would require the government and business to collaborate "for the next five years, 10 years, 20 years, so that we can make sure that we get the benefits of the internet and utilization, and not the dangers and threats.
"They're going to be thinking about everything from how do we keep the huge databases that exist in the federal government more secure, to how do we more effectively work with critical sectors of our economy, whether it's the financial sector or our critical infrastructure, like utilities, to make sure their systems are more secure," Obama said.
President Obama discusses the Cybersecurity National Action Plan on Feb. 9.The Department of Commerce's NIST will provide support to the commission. Commerce Secretary Penny Pritzker says involvement of public- and private-sector leaders would provide the perspectives of business, the tech sector, IT security, national security and law enforcement to address the nation's cybersecurity challenges.
"As the owners and operators of much of the infrastructure and digital networks that represent the backbone of the 21st century economy, the private sector is our indispensable partner in protecting the networks that are so essential to commerce, public safety and national security," Pritzker says.
- Details
- Category: Security News
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
More Articles …
Page 3413 of 3546

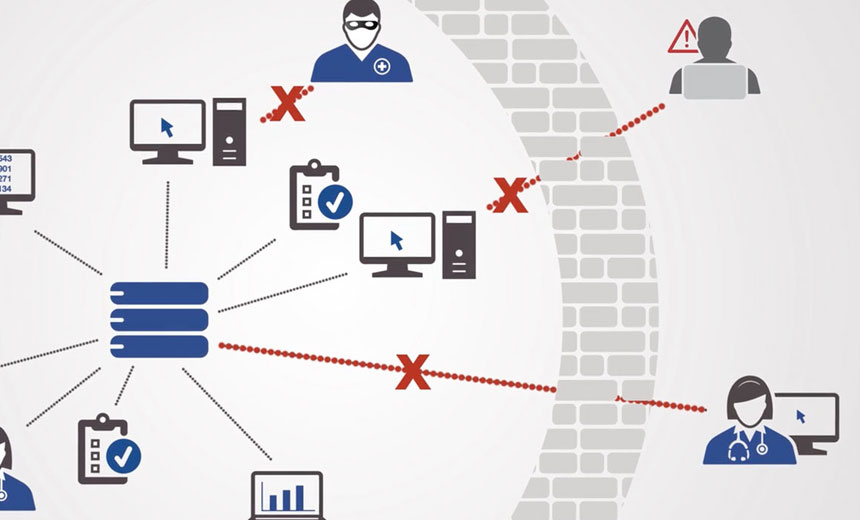
 Protecting sensitive information is especially difficult for corporations that have data stores scattered in physical, virtual and cloud-based repositories across the globe. Not only do these multinational organizations need to protect their data from countless threat actors, they must contend with exploding data growth and constantly changing, oftentimes contradictory privacy regulations in the countries where they do business.
This session will cover key topics for data and security professional in 2016, including:
CISO Perspective on Data Security Risk
The Intersection of Data Security Risk and Data Management
Create a 360-degree view of your data security risks
Deliver on-demand intelligence for prioritization, audit and governance
Never-ending threats, exploding data growth and privacy regulations challenge IT and security responsible for thousands of data stores scattered across the globe. Therefore, a data security framework is mandatory to protect your data across international regions. But in order to construct this framework, you need visibility into all your data and its attendant risk.
This webinar, hosted Bill Burns, CISO at Informatica, and featuring Josh Alpern, vice president, strategic business development, data security at Informatica and David Loshin president of consultancy Knowledge Integrity, will teach you how to gain visibility, control and understanding of your sensitive data and the financial impact of keeping it safe.
Register for this webinar and learn the why and how of devising an effective global data risk and security framework.
This informative session will also highlight how you can:
Understand data proliferation (AKA the "data monster")
Create a 360-degree view of your data risks
Deliver on-demand intelligence for audit and governance programs
Eliminate costly and error-prone manual efforts in securing your data
You might also be interested in …
Protecting sensitive information is especially difficult for corporations that have data stores scattered in physical, virtual and cloud-based repositories across the globe. Not only do these multinational organizations need to protect their data from countless threat actors, they must contend with exploding data growth and constantly changing, oftentimes contradictory privacy regulations in the countries where they do business.
This session will cover key topics for data and security professional in 2016, including:
CISO Perspective on Data Security Risk
The Intersection of Data Security Risk and Data Management
Create a 360-degree view of your data security risks
Deliver on-demand intelligence for prioritization, audit and governance
Never-ending threats, exploding data growth and privacy regulations challenge IT and security responsible for thousands of data stores scattered across the globe. Therefore, a data security framework is mandatory to protect your data across international regions. But in order to construct this framework, you need visibility into all your data and its attendant risk.
This webinar, hosted Bill Burns, CISO at Informatica, and featuring Josh Alpern, vice president, strategic business development, data security at Informatica and David Loshin president of consultancy Knowledge Integrity, will teach you how to gain visibility, control and understanding of your sensitive data and the financial impact of keeping it safe.
Register for this webinar and learn the why and how of devising an effective global data risk and security framework.
This informative session will also highlight how you can:
Understand data proliferation (AKA the "data monster")
Create a 360-degree view of your data risks
Deliver on-demand intelligence for audit and governance programs
Eliminate costly and error-prone manual efforts in securing your data
You might also be interested in …