- Details
- Category: Security News

A previously unknown cybercrime group has hacked into numerous organizations in the retail and hospitality sectors to steal an estimated 20 million payment cards, collectively worth an estimated $400 million via underground cybercrime forum sales, according to the cybersecurity firm FireEye.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
In a new report, FireEye says the group, which it's dubbed FIN6, steals credit card data and then sells it on darknet carder forums to buyers who use the payment card data to commit fraud.
While many other cybercrime groups take a similar approach, FIN6 excels in its unprecedented speed to market, says Richard Turner, FireEye's Europe, Middle East and Africa president. "As far as we can tell, this is the first group that has really put an effort into ensuring that they get the credentials to market as quickly and as efficiently as they can to maximize the premium price that those credentials will generate," he says. "They can deliver them to market quite quickly to enable people to commit their crimes more quickly."
The value of stolen card data on carder forums has long been tied to the freshness of that data. Maximum freshness comes with stolen card data that issuers don't yet know has been stolen. But as issuers spot card fraud and trace it back to particular e-commerce sites or physical locations, then identify likely breach periods, the freshness of that data naturally decays. As a result, sellers can no longer command premium prices for the data, because fewer card numbers will work for buyers.
As a result, there's a natural economic incentive for cybercrime groups to bring their cards to market as quickly as possible. "This is just a really good example of [how] our adversaries are not spotted youths in back rooms," Turner says. "They're well-skilled, well-resourced, intelligent people who have a mission to create and generate wealth by illegal means, and by defrauding companies. And they're just maturing, to say, 'How do I maximize my return on investment?' It makes a lot of sense. It's just such a shame that the effort isn't being put into more intellectual [and beneficial] efforts."
Top Targets: Hospitality, Retail
Turner says cybercrime groups typically target whatever is the weakest point in an organization's defenses. Their efforts typically involve targeted spear-phishing attacks, directly hacking into a targeted organization or gaining access via a connected network, for example, via a poorly secured supply chain partner, he says.
Whatever method is used, Turner says, the goal is to install point-of-sale malware and siphon off as many card details as possible. In the case of FIN6, the POS malware of choice appears to be Trinity, also known as FrameworkPOS.
In today's increasingly specialized cybercrime economy, while groups such as FIN6 steal card data, they don't use it themselves to commit fraud, but instead monetize the attacks by selling the card data to others (see Banks Reacting Faster to Card Breaches). As a result, a related breach might be well underway - or already over - by the time the fraud gets flagged.
The Lure of 'Reshipping Mule' Scams
The importance of bringing fresh card data to market quickly is tied to how fraudsters put that data to work. In the past, they often purchased stolen card data and attempted to use it to directly withdraw money; engaged money mules to withdraw money or buy and sell goods, and then wire the money to attacker-controlled bank accounts; or directly purchased high-value goods and tried to ship them overseas.
But the first two approaches involve a measure of physical risk - and trust - while the latter method has become less effective because many U.S.-based online retailers block shipments to certain geographies, including Russia and Ukraine, according to a new report from security researchers at Hewlett Packard Enterprise.
As a result, many fraudsters have been turning to so-called "reshipping mule scams," which are less risky as well as harder to block. Such scams involve a "stuffer" purchasing goods with the stolen card data, then shipping them to a neutral "drop" address - often, someone recruited via a "work at home" scam - after which the recipient sends the goods on to criminals, who then resell the items on the black market, or sometimes via legitimate sites, to turn a profit.
"Due to the intricacies of this kind of scam, it is exceedingly difficult to trace, stop and return shipments, which is why reshipping scams have become a common means for miscreants to turn stolen credit cards into cash," according to "Drops for Stuff: An Analysis of Reshipping Mule Scams," a research paper that was presented at the ACM Conference on Computer and Communications Security in October 2015. The paper is based on work undertaken by a team of researchers, including University of California at Santa Barbara information security researcher Shuang Hao.
Anatomy of a Reshipping Scam Operation
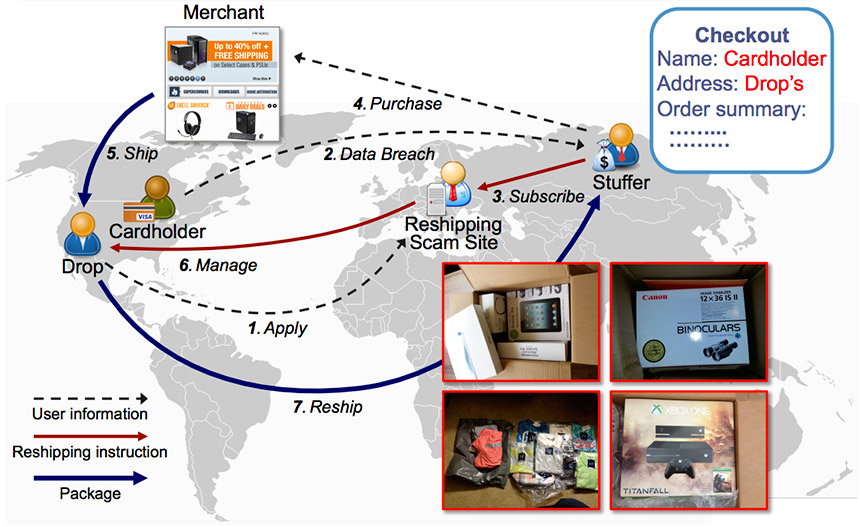 Source: "Drops for Stuff: An Analysis of Reshipping Mule Scams"
Source: "Drops for Stuff: An Analysis of Reshipping Mule Scams"The researchers estimate that a single reshipping site earns $7.3 million, on average, every year, and that the overall market earns $1.8 billion annually (see I Believe in Cybercrime Unicorns).
Some criminal groups are even offering "reshipping as a service," which they sell by either taking up to 50 percent of the profits, for high-value items, or charging a flat rate - typically $50 to $70 per package - for lower-value products, the researchers say.
All Roads Leads to Eastern Europe?
"Most drops are located in the United States, as most targeted retailers as well as stolen credit card data originate here," according to the Hewlett Packard Enterprise report. But the researchers also found one reshipping service targeting Germany-based online retailer Zalando.de.
The researchers found that of the reshipping scam sites they studied, 85 percent of all packages were shipped to either Moscow or its suburbs.
FireEye, in its report on FIN6, doesn't attribute the crimes perpetrated by the card data hacking specialists to a specific set of individuals or a region. But FireEye's Turner says the company suspects the group is operating from Eastern Europe.
- Details
- Category: Security News
Anti-Malware , Fraud , Technology
Malware Stole Payment Card Data, Drained Bank Accounts
Two of the hacker masterminds behind the notorious SpyEye malware have each received lengthy prison sentences after pleading guilty to related charges in U.S. federal court. But alleged Zeus creator and accomplice Evginy Bogachev remains at large.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
SpyEye was used by "a global syndicate of cybercriminals to infect over 50 million computers, causing close to $1 billion in financial harm to individuals and financial institutions around the globe," according to the U.S. Department of Justice. Security experts say SpyEye was the dominant malware toolkit cybercriminals used from 2009 to 2011.
"It is difficult to overstate the significance of this case, not only in terms of bringing two prolific computer hackers to justice, but also in disrupting and preventing immeasurable financial losses to individuals and the financial industry around the world," U.S. Attorney John Horn says in a statement.
The chief developer behind SpyEye, authorities say, was Russian national Aleksandr Andreevich Panin, a.k.a. Gribodemon, Harderman. The FBI arrested him in July 2013 - while on a layover at Hartsfield-Jackson Atlanta International Airport. In January 2014, he pleaded guilty to conspiracy to commit wire fraud and bank fraud charges. He was sentenced April 20 to serve nine years and six months in prison, followed by three years of probation.
Busted in Bangkok
One of his accomplices, 27-year-old Algerian national Hamza Bendelladj, a.k.a. Bx1, was apprehended by the FBI at an airport in Bangkok in January 2013 while he was in transit from Malaysia to Algeria and extradited to the United States in May 2013. On June 26, 2015, he pleaded guilty to all 23 counts of a federal indictment first filed in 2011 against both him and Panin, who at that time had yet to be named. The charges included various counts of wire and bank fraud as well as computer fraud.
On April 20, Bendelladj was sentenced to serve 15 years in prison, followed by three years of probation.
Bendelladj pleaded guilty to sending more than 1 million emails that contained SpyEye and other malware to potential victims. He also admitted developing and selling various malicious botnet add-ons such as "spreaders," designed to sneak malware onto systems, which he used to disseminate SpyEye and Zeus, web injections to alter the appearance of online banking pages to hide malicious activities and automated transfer systems to drain funds from accounts, prosecutors say.
Authorities say Bendelladj stole personal identifying information from nearly 500,000 individuals, stole hundreds of thousands of payment card and bank account numbers, caused millions of dollars in losses to both individuals and global financial institutions and ran the VCC.sc website, which sold stolen payment card information to other cybercriminals.
Modern Banking Trojan
SpyEye's developers had at least 150 customers, who paid $1,000 to $8,500 for the malware, which Panin advertised and sold via invitation-only cybercrime forums, according to the Justice Department.
SpyEye and its infrastructure were targeted and disrupted as part of an international effort, involving the FBI and 26 other law enforcement agencies, as well as private industry assistance from Microsoft, Trend Micro and others, authorities say. SpyEye incorporated numerous features that are now standard in banking malware, including web injections customized for many different banks, keystroke loggers and card-data grabbing capabilities, as well as the ability to control infected endpoints - and exfiltrate data - via botnet command-and-control servers.
In recent years, however, many cybercrime gangs have begun adopting exploit kits - such as the now-defunct Blackhole exploit kit developed by Dmitry "Paunch" Fedotov - that can be used to infect PCs with a range of malicious code, including multiple types of banking Trojans as well as click-fraud software and ransomware. The exploit kit also has the ability to turn "zombie" endpoints into distributed denial-of-service attack launching points.
Arrest Led to Darkode Bust
Authorities say Bendelladj's arrest helped a task force composed of 20 countries' law enforcement agencies shutter the Darkode.com cybercrime forum in July 2015 (see How Do We Catch Cybercrime Kingpins?).
Panin was SpyEye's primary developer and distributor, authorities say, noting that he developed the malware to be the successor to the Zeus banking Trojan after allegedly receiving the Zeus source code and sales rights from Evginy Bogachev - a.k.a. Slavik, lucky12345 - and adding many aspects of the Zeus code base into new versions of SpyEye. Authorities allege Panin was in charge of marketing SpyEye and operated from Russia.
Panin's arrest prevented him from releasing a new strain malware - "SpyEye 2.0" - that had been in development, the Justice Department says. The investigation also led to the arrest by authorities in the United Kingdom and Bulgaria of four of Panin's SpyEye clients and associates (see Europol Targets Ukrainian Botnet Gang).
At Large: Alleged Zeus Creator
Bogachev, however, remains at large. He's currently at the top of the FBI's Cyber Most Wanted list, and has been blamed for creating both Zeus and GameOver Zeus.
The U.S. Department of State's Transnational Organized Crime Rewards Program has offered a reward of up to $3 million for information leading to his arrest or conviction (see FBI Hacker Hunt Goes 'Wild West').
- Details
- Category: Security News

Although skimming attacks remain the No. 1 ATM fraud concern in the United States, so-called "black box" attacks loom as a growing threat.
See Also: How to Measure & Communicate Return on Cybersecurity Investments
Black box attacks against ATMs already are on the rise in Europe, according to two new alerts from ATM manufacturer NCR Corp.
In a black box attack, criminals cut holes into the fascia or top of the ATM to gain access to its internal infrastructure. From there, the ATM's cash dispenser is disconnected and attached to an external electronic device - the so-called black box. The box sends commands to the dispenser to push out cash, bypassing the need for a card or transaction authorization.
T.J. Horan, vice president of fraud solutions for FICO's Card Alert Service, says black box attacks, such as those now plaguing Europe, will eventually emerge as a serious threat in the United States as well. Meanwhile, new research from FICO confirms that ATM skimming is still a much larger problem in the United States than in other parts of the world.
"We just released data that indicated ATM skimming increased 546 percent from 2014 to 2015," he says. "That is the largest year-over-year increase we've seen in the 20-plus years of the FICO Card Alert Service."
FICO's research, which is based on the analysis of thousands of U.S. ATMs, shows that off-premises retail ATMs were most often targeted, with 10 times as many of those terminals being plagued by skimming attacks in 2015 than in 2014.
"Criminals are targeting non-bank ATMs, which are more vulnerable," Horan says. "In 2015, non-bank ATMs accounted for 60 percent of all compromises, up from 39 percent in 2014."
Horan says black box attacks are likely to spread to the U.S. because they "are consistent with the trend toward an increase in compromises at non-bank-owned ATMs. Criminals are targeting weaker links in the system, including sometimes hacking into machines and not just simply installing skimming devices. These types of attacks are more common at non-bank locations and show the blurring of lines between skimming and certain forms of cybercrime."
Shirley Inscoe, a financial fraud analyst at consultancy Aite, offers a similar assessment: "Skimming continues to be a huge concern in the U.S., but it would not be surprising for these black box attacks to migrate here from Europe. Based on how the scam works, it would work here just as well."
And Al Pascual, head of fraud and security at Javelin Strategy & Research, says the recent rise in black box attacks in Europe should serve as a warning for U.S. ATM deployers.
"Skimming in the U.S. will only get worse at unattended terminals, including ATMs, until they have largely been upgraded to accept EMV cards," he says. "Even then we will not be out of the woods, as the black box warnings out of Europe should be a warning ... that once we close one door on fraud, fraudsters will open another. A metal box that spits out cash will always be an attractive target for criminals, and both information and physical security will continue to evolve to protect ATMs until cash is a thing of the past."
Black Box Resurgence
Black box attacks, first identified in 2012, have made a resurgence in Europe in recent months, says Owen Wild, global director of security solutions for NCR. "They seemed to slow down as they were replaced by the malware attacks," he says. "But over the past quarter, we have seen a rise in the occurrence of the black box attack. Further, we have seen it appear in new regions. ... As we have seen with every other form of ATM crime, no region should expect that they are immune. Crime expands, and now expands as quickly as ever."
Off-premises, retail ATMs have historically been the most vulnerable to black box attacks, according to NCR's alerts, because attackers have to physically manipulate the ATM. But bank branch ATMs are proving to be just as vulnerable, NCR notes.
An April 14 alert from NCR notes black box attacks waged against through-the-wall NCR Personas ATMs, which are typically located at bank branches, were on the rise in Italy. And in an April 18 alert, NCR notes that black box attacks waged against the NCR SelfServ ATM line, which is designed for off-premises and branch/lobby deployment, were on the rise in Germany.
Back in March 2015, NCR reported a rise in black box attacks in India (see Alert: Indian ATMs Face New Attacks).
In its most recent alerts, NCR points out that ensuring ATM software and hardware are up to date is critical for mitigating risks associated with black box attacks. "Fleet modernization is an important part of staying secure," the alerts note. "Modern architectures containing modern technologies are critical in the defense against criminals."
Planning a Defense
Graham Mott, who heads up the LINK Scheme, the U.K.'s central ATM network, says black box attacks "require a great deal of technical knowledge and significant investment in resources." But they can be blocked through a range of measures, including physical defenses, he says. "Therefore, while they can result in large losses, if successful, a layered approach to security should prevent them from occurring."
Closely monitoring and regularly inspecting ATMs is the best way to detect a black box or skimming attack, says Aite's Inscoe. "Machines that are not closely monitored or inspected frequently are at the highest risk," she says. "It is so easy for criminals to attach skimming devices, and in many cases, cameras to catch the PIN when it is keyed. Methods of matching the color and material on the ATM surround or camouflaging the device on a gas pump or other machine have made detection of skimming devices more difficult. This is extremely lucrative for the fraudsters, so attacks will continue to rise."
- Details
- Category: Security News
Conducting penetration testing on "Internet of Things" devices is similar to testing any other Internet-connected product: Hammer away at it to see if its security can be broken, and then determine what that might allow attackers to do.
All IoT-related hardware and software demands security testing, says Charles Henderson, IBM's global head of security testing and threats, in an interview with Information Security Media Group. But one big challenge with IoT devices is that they're not a technology, but a collection of technologies, and small problems in each of those technologies can add up to big risks.
"Very often, some of the most damaging vulnerabilities that we see in IoT are vulnerabilities that actually present across multiple technologies," Henderson says. "Effectively, it's not the mobile application alone, it's the way the mobile application integrates with the API, with the web platform, and with the sensor device that it connects to. It's a chain of problems, rather than an individual problem in a specific technology."
That's why manufacturers need to test not just the point technologies, applications or services associated with their devices, but everything together, Henderson says. Developers must think about how attackers might attempt to exploit a device, and why, and then write code designed to lock devices down against such attacks, he stresses.
Cook Up Device "Abuse Cases"
For developers, helping to create secure devices involves not just thinking about how to deliver specific types of functionality, but also to "think like an attacker," he says. "Think not just of use cases, but think of abuse cases. Think how your product can be misused to circumvent security safeguards."
In this in-depth interview (see audio player below photo), Henderson also discusses:
The value of using humans - not just automated tools - to look for vulnerabilities; How devices most often fail - on the security front - and what can be done to prevent that; The importance of having developers do informal threat modeling against the applications, devices or services they build or use.Before joining IBM as global head of security testing and threats, Henderson served as vice president of managed security testing at Trustwave, as well as head of its penetration testing services group and director of application security services. He's also worked as a security consultant specializing in penetration testing.
- Details
- Category: Security News
Only 23 percent of surveyed organizations can respond effectively to a cybersecurity incident. This is among the findings of Solutionary's fourth annual Global Threat Intelligence Report.
Among other key findings from this new report, produced by Solutionary in conjunction with Lockheed Martin, Wapack Labs, Recorded Future and the Center for Internet Security:
Spear phishing attacks accounted for about 17 percent of incident response activities last year; Almost 21 percent of vulnerabilities detected were more than three years years old; The retail sector experienced the most attacks - roughly 2.7 times the number of attacks as organizations in finance.The lack of preparedness is a growing concern, says Rob Krause, Director of Security & Strategy Research for Solutionary's engineering research team.
"There is a very small amount of organizations that are actually trying to mature their incident response programs," Kraus says. "And this is from organizations just outright saying 'We're not prepared.'"
Kraus describes the approach as using the "phone a friend" option when organizations are under attack. "They don't have the security budget ... but a lot of it is related to expertise. And it's not because there's a lack of expertise out there. It's more because: It's the budget. Incident responders are not a cheap resource."
Ultimately, it comes down to business resiliency, Kraus says, and here is where organizations can learn from their adversaries.
"When malware authors are out there creating malware to do its mission, the first mission of the malware is to do what? It's to survive," Kraus says. "Organizations need to think the same way."
In an interview about Solutionary's latest Global Threat Intelligence report, Kraus discusses:
What's unique about this year's report; Top attack vectors and targets; Where organizations continually fail in being resilient.Kraus is the director of research for the Solutionary engineering research team. He is a Certified Information Systems Security Professional (CISSP), specializing in vulnerability research, malware analysis, threat intelligence, Web application security assessments, external and internal penetration testing, and social engineering. He previously was a manager within Solutionary's security consulting services group.
Solutionary, an NTT Group security company, is the next generation managed security services provider (MSSP). Comprehensive Solutionary security monitoring and security device management services protect traditional and virtual IT infrastructures, cloud environments and mobile data.
More Articles …
Page 3416 of 3546
