Cybersecurity , Risk Management , Technology
Enhance Vulnerability Management with Analytics and Intelligence- Details
- Category: Security News
Anti-Malware , Data Breach , Fraud
Ransomware Repurposed to Target Business Accounts
A cybercrime gang has been using new malware to target business customers of banks in the United States and Canada and steal millions of dollars, primarily from business accounts, researchers at the IBM X-Force security group warn.
See Also: Rethinking Endpoint Security
So far, attackers have been focusing their attacks on business customers of 22 banks, credit unions and e-commerce sites in the United States, as well as two financial institutions in Canada, IBM's Limor Kessem, an executive security adviser, and Lior Keshet, a malware researcher, write in a blog post.
In just the first few days of April, the attackers successfully stole an estimated $4 million, IBM tells The Wall Street Journal.
IBM has not named which organizations' customers were targeted but says the organizations have been alerted to the malware campaign. After infecting a system, the malware can steal financial data and capture screenshots, then relay them to attackers, who will attempt to transfer money out of victims' accounts.
The attacks have been perpetrated using "a Trojan hybrid spawned from the Nymaim and Gozi ISFB malware," the IBM researchers say. They note that Nymaim - a Trojan downloader that can also function as ransomware - appears to be maintained and used by a single, closed group. Gozi, a.k.a. Vawtrak, is a banking Trojan that first appeared in 2012. The source code for Gozi was leaked twice - first in 2010 and again in 2015.
Threat-intelligence firm iSight Partners, in a research note, says it's not clear if a single group is behind Nymaim, noting: "Nymaim has been and continues to be operated by a limited number of actors." But it adds: "We consider it entirely plausible that Nymaim's operators produced a new version incorporating much of Gozi's credential theft capabilities."
Nymaim: Ransomware Roots
Over the past month, according to security firm ESET, Nymaim has predominantly been infecting victims in the United States, Germany and Poland. The malware, first spotted in September 2013, can be used to download additional attack code as well as to lock computers and demand a ransom, ESET notes.
Security researchers say Nymaim formerly was primarily distributed through the now defunct Blackhole exploit kit, a.k.a. DarkLeech, as well as by attackers tweaking search engine results - so-called Black Hat SEO - to make them return highly placed, legitimate-looking links for various keywords. In reality, however, those links led to sites that were infected with Blackhole, and which then launched drive-by attacks against known vulnerabilities in web browser plug-ins, in an attempt to seize control of endpoints.
In late 2013 alone, more than 2.5 million Nymaim infections were due to Blackhole, the anti-malware researcher known as Kafeine reported.
But the Nymaim gang had to adjust its malware-distribution tactics after Russian authorities busted members of the Blackhole cybercrime gang in October 2013 (see Russia: 7-Year Sentence for Blackhole Mastermind). By 2014, many computers infected by Nymaim were also infected with Gozi and Ursnif, the Miuref Trojan, as well as Pony, a downloader that enables attackers to push additional attack code onto infected PCs, security firm Proofpoint says in a recent blog post.
The GozNym Blend
Beginning in early 2016, some Pony infections were executing Nymaim before fetching Gozi - a.k.a. Gozi ISFB - as part of a multistage attack, IBM says, noting that many firms classified these as Gozi attacks, even though the Nymaim group - and malware - appeared to be responsible.
At that time, Proofpoint reported that Nymaim was primarily infecting PCs with the Ursnif banking Trojan, which is primarily designed to steal sensitive data. It said the primary distribution mechanism was "email to send document attachments or URLs leading to documents" which, when opened, would download macros and install Nymaim.
Early this year, the merged version of Gozi and Nymaim first appeared, combining "the best of both," IBM says. In particular, GozNym can evade antivirus software, as well as record keystrokes and take screenshots, for example, while users browse banking websites. As with other modern banking malware, GozNym can also use web injections, which enable attackers to alter the appearance of a user's online banking account to hide real-time transfers that attackers might be making.
Security experts say that GozNym, like Nymaim, gets distributed both via malicious links - created on websites by exploit toolkits - as well as via malicious attachments to email messages. Once it infects a system, GozNym, like Nymaim, can be used to install additional code.
- Details
- Category: Security News
- Details
- Category: Security News
U.S. merchants of all sizes - not just smaller retailers - have seen significant increases in chargebacks in the wake of the Oct. 1, 2015, EMV fraud liability shift date, says Liz Garner, vice president of the Merchant Advisory Group, which represents large retailers.
In an in-depth interview with Information Security Media Group, Garner says chargebacks are running $10,000 to $15,000 per week for some smaller merchants to as much as $1 million a week for some of the largest merchants.
And those charges are largely unfair, she argues, because many merchants were not EMV-compliant by the liability shift date due to circumstances out of their control.
Most U.S. merchants had invested in and installed EMV-equipped point-of-sale terminals months before the October shift date, she contends. But because of software certification and installation backlogs, many U.S. retailers still are not ready to accept EMV transactions, and thus are being hit with the liability shift for fraud tied to the use of magnetic-stripe cards.
"Merchants aren't [EMV compliant] for lack of trying, but because of some of the challenges that the financial services industry faced in its ability to get some of these point-of-sale terminals certified - that's one of the pitfalls of inadequate timelines," Garner contends.
In the U.S., merchants had about four years to prepare for the shift to EMV according to the Visa roadmap, she says. In Canada, a nation with an economy one-tenth the size of the U.S., merchants had seven years to make the transition, she says. "So we are really dealing with a stack of cards against us."
Many merchants "are still waiting to get their terminals certified to accept EMV," she notes. "And while they wait on the payments industry to come around and do those certifications, they are being hit with very expensive chargebacks for counterfeit card fraud" (see EMV: Not Ready for Prime Time?).
During this interview (see audio player below photo), Garner also discusses:
The role the card brands and issuing banks should play in reducing chargebacks to merchants; Why more transparency about the specific fraud-related reasons for chargebacks is needed; and Why EMV transactions with PINS, rather than signatures, for autentication would significantly reduce fraud.Gartner is vice president at the Merchant Advisory Group, which represents 85 of the country's leading retailers. Previously, she served as director of commerce and entrepreneurship at the National Restaurant Association, representing the restaurant industry before Congress and regulatory agencies about issues impacting restaurant and food service profitability and entrepreneurship. Garner's areas of expertise include retail and mobile payments, data security, privacy, emerging technologies, taxes and finance.
- Details
- Category: Security News
Anti-Malware , Data Loss , Encryption
Attack Alert: JavaScript Spam Installs Ransomware Beware JavaScript Social Engineering Emails, Microsoft Warns
Warning: A recent spate of spam emails have been tricking users into installing several different JavaScript-based downloaders, which then install well-known ransomware that's designed to forcibly encrypt all files on a PC, Microsoft warns (see FBI Warning: Ransomware Is Surging).
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
"Be wary of emails with JavaScript attachments," says Alden Pornasdoro, who's part of Microsoft's malware protection group, in a blog post. "It is uncommon and quite suspicious for people to send legitimate applications in pure JavaScript file format - files with .js or .jse extension - via email. Do not click or open it."
Microsoft hasn't detailed how many users might have fallen victim to these social engineering attacks. But it warns that it's seen a surge in three different types of malicious downloaders written in JavaScript - Locky, Nemucod and Swabfex - being installed on PCs, and used to then download and install ransomware.
"Just like a typical email campaign, the JavaScript-toting spam finds its way [onto] your PC after a successful social engineering trick," Pornasdoro says. Said trickery often involves attackers picking interesting-sounding names, for example related to purported financial documents. First, however, users have to fall for the ruse by expanding a .zip or .rar file attached to the email, inside which is the malicious JavaScript, which they must then click to execute.
Spam Leads to Locky, TeslaCrypt
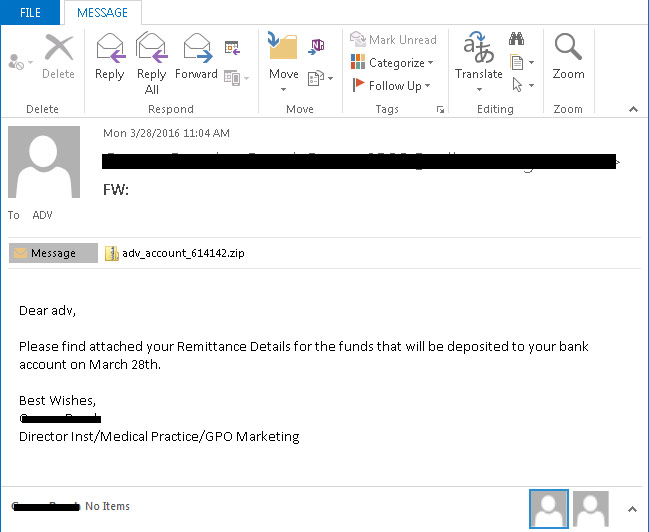 Pictured: Email associated with recent JavaScript-spam attacks that lead to ransomware infections. (Source: Microsoft.)
Pictured: Email associated with recent JavaScript-spam attacks that lead to ransomware infections. (Source: Microsoft.) With this particular JavaScript campaign, Microsoft says attackers have been using the downloaders to install two types of ransomware:
Tescrypt: Also known as TeslaCrypt and Bitman, this ransomware often gets dropped by such exploit kits as Angler, Fiesta, Nuclear, and Sweet Orange, some of which may now be responsible for the JavaScript spam attacks. Locky: This ransomware has been tied to many recent attacks, most notably against hospitals.Ransomware Gets Commoditized
But like banking Trojans, much of the ransomware being used by attackers today is functionally equivalent: It will forcibly encrypt sensitive files on a PC, then demand a ransom payment - in bitcoins - in exchange for a decryption key. Then it's up to organizations or end users to either wipe the infected system and restore a recent backup, or else to decide if they're going to pay the ransom (see Ransomware: Is It Ever OK to Pay?).
While anti-virus software should theoretically be able to block ransomware from being installed, by employing JavaScript, attackers have been evading many such defenses. "The JavaScript attachments are heavily obfuscated to avoid anti-virus software detections. It consists of a download and execute function paired with one or two URLs hosting the malware," Pornasdoro says.
As is typical with many types of malware or ransomware campaigns, attackers will then quickly discard the URLs and move to new ones, so that by the time security firms blacklist the URL - so that future, infected endpoints can't "phone home" to it - the URL is no longer in use.
Defending Against JavaScript Spam
To guard against these types of attacks, Microsoft recommends employing related defenses at the following levels:
Gateway: Ensure email gateways are scanning for malicious code and blocking it there. Endpoint: Use up-to-date and fully patched anti-malware and anti-spyware software. Macros: Disable macros in Office programs, and set Group Policy settings to disable macro loading. Training: Educate users to never click or open email attachments that carry files with .js or .jse.Bad Bet: Crypto Coding Failures
In some cases, for example earlier this month with Petya ransomware, or last year with a previous version of TeslaCrypt, ransomware developers make coding mistakes that allow researchers to crack their crypto and release a free decryption tool.
Attackers fumbling their ransomware crypto is a "lucky break" for anyone whose systems were infected, says Johannes Ullrich, CTO of the Internet Storm Center, in a recent SANS Institute newsletter. But there's never a guarantee that ransomware coders will screw up, and it's a sure bet that when they do, the next iteration of their ransomware will avoid making the same mistake.
"Remember that the real defense against crypto ransomware is offline backups - which also helps against a number of other disasters," Ullrich says.
- Details
- Category: Security News
Anti-Malware , Risk Management , Technology
Why It's Time to Remove QuickTime for Windows Apple Won't Patch, So Delete Software, US-CERT Advises
Apple's QuickTime media player and web browser plug-in should be immediately expunged from all Windows systems, security experts warn, in a reminder of the dangers of using outdated software - especially web browser plug-ins.
See Also: How to Mitigate Credential Theft by Securing Active Directory
Security vendor Trend Micro recently issued an "urgent security alert," warning that "everyone should follow Apple's guidance and uninstall QuickTime for Windows as soon as possible." The alert comes after the security firm found two zero-day flaws in QuickTime for Windows, which it says Apple won't patch.
Apple didn't immediately respond to a request for comment on that warning, or whether it plans to alert users directly.
The two flaws - designated ZDI-16-241 and ZDI-16-242 - could be abused by attackers to remotely execute code on vulnerable systems. Both were reported to Trend Micro's Zero Day Initiative by Steven Seeley at security firm Source Incite, based in Mexico City. Trend Micro alerted Apple on Nov. 11, 2015. So far, Trend Micro says, it hasn't seen any related attacks in the wild.
The alert follows security vendor Flexera Software warning that for the whole of 2015 - meaning before these two new flaws came to light - the riskiest application installed on U.S.-based Windows PCs was QuickTime. That's because the software has a high installation base, and more than half of all users are running an unpatched version that contains exploitable vulnerabilities.
The World's Riskiest Software
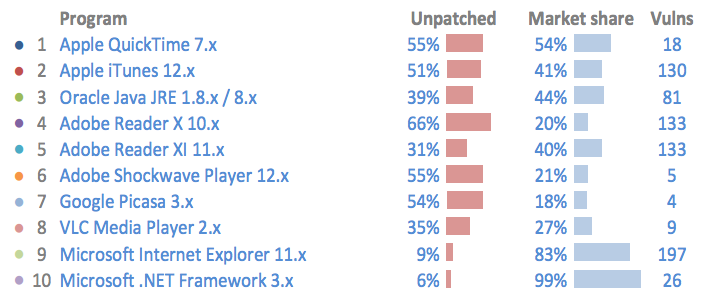 Software ranked by the severity and quantity of new vulnerabilities (vulns) discovered as well as the software's prevalence (market share), all in 2015. (Source: Flexera Software.)
Software ranked by the severity and quantity of new vulnerabilities (vulns) discovered as well as the software's prevalence (market share), all in 2015. (Source: Flexera Software.)Yet Apple's guidance still isn't to uninstall QuickTime. Instead it's more circumspect, offering removal instructions "if you no longer need QuickTime 7."
But the U.S. Computer Emergency Response Team doesn't mince words, warning that because Apple has ceased supporting QuickTime for Windows, the software is "vulnerable to exploitation," and that the only way to protect against that is to remove the software now. "Computer systems running unsupported software are exposed to elevated cybersecurity dangers, such as increased risks of malicious attacks or electronic data loss," US-CERT says. "Exploitation of QuickTime for Windows vulnerabilities could allow remote attackers to take control of affected systems."
That warning is a reminder that all nonessential software should be expunged from systems whenever possible. That's especially true for any web browser plug-ins, including outdated versions of Adobe Flash, Microsoft Silverlight and Oracle Java, which attackers often favor for compromising PCs and installing malware (see Cybercriminals Mourn Java Plug-In Death).
Too often, "outdated" seems to refer to any version of the plug-in software before it was updated yesterday. But that's the tradeoff users must make when using browser plug-ins. Indeed, security firm Kaspersky Lab says that in 2015, 62 percent of all online attacks targeted browsers, including plug-in flaws.
Removing Plug-In
One major security impetus for uninstalling QuickTime on Windows is that it will also remove the QuickTime browser plug-in, which is a potential attack target. "Uninstalling QuickTime 7 also removes the legacy QuickTime 7 web plug-in, if present," Apple says. "Websites increasingly use the HTML5 web standard for a better video-playback experience across a wide range of browsers and devices, without additional software or plug-ins."
Despite the US-CERT alert, however, Apple is still offering the latest QuickTime for Windows - version 7.7.9 - as a download. The download page, which was last updated March 9, carries no security-related warnings or deprecation alert.
Regardless, vulnerability remediation expert Wolfgang Kandek, CTO at the security firm Qualys, advocates removing all software as soon as it loses support. But if that's not possible, then he recommends trying to reduce or eliminate network access for devices that continue to run the outdated software, in particular by blocking the ability to browse websites or check email. He also recommends installing Microsoft's Enhanced Mitigation Experience Toolkit, which is designed to prevent software vulnerabilities in Windows from being exploited (see 5 Secrets to Security Success).
What Windows XP Use Tells Us
Unfortunately, too many users fail to heed the "if it's outdated, delete it" advice.
According to market researcher Net Applications, for example, Windows XP still accounts for 11 percent of all operating systems in use, despite Microsoft dropping related support two years ago. Similarly, Flexera Sofware reported that at the end of 2015, the outdated - and frequently targeted - Adobe Flash Player version 19 continued to be present on 73 percent of all U.S. systems (see 2016 Resolution: Ditch Flash).
More Articles …
Page 3415 of 3546

 Vulnerability management, defined as the cyclical practice of identifying, classifying, remediating and mitigating vulnerabilities, has been a basic element of the security posture in many global organizations. As the technology evolves by use of cloud, social and internet of things in organizations, the vulnerability management function grows more complex and critical.
Attend this session to hear directly from Sameer Shelke, Cofounder and CTO of Aujas, a global information risk management company on:
The threat landscape and how it forces vulnerability management programs to evolve;
How analytics and intelligence can be added to your vulnerability management program;
A case study of one large, multinational organization that has experienced this evolution and growth
Adding "analytics" and "intelligence" aspects to the vulnerability management function help to ensure that it keeps up with the challenging threat and risk landscape. For example:
Analytics: The vulnerability management program produces a large volume of data related to vulnerabilities, assets, trends, mitigation measures, gaps, compensating controls, etc. Converting the raw data to information using organization context and then to insights based on the risk landscape can provide real value for risk management decisions and actions.
As an example, analytical information on the vulnerability root cause, its link to vulnerability trends and assets can help effective mitigation. Similarly, vulnerability remediation analytics can help identify weakness in the process for improvements.
Intelligence: Typically, the vulnerability management process starts with vulnerability identification, which depends on vulnerability scanning. That's the start in the find-and-fix process. A critical miss in the process can be any weakness in the "find" step, either due to tool functionality or zero day vulnerabilities.
Adding vulnerability intelligence to the management process from authoritative sources and mapping them to the organization assets and their specific configurations would remove critical gaps in the find process.
You might also be interested in …
Vulnerability management, defined as the cyclical practice of identifying, classifying, remediating and mitigating vulnerabilities, has been a basic element of the security posture in many global organizations. As the technology evolves by use of cloud, social and internet of things in organizations, the vulnerability management function grows more complex and critical.
Attend this session to hear directly from Sameer Shelke, Cofounder and CTO of Aujas, a global information risk management company on:
The threat landscape and how it forces vulnerability management programs to evolve;
How analytics and intelligence can be added to your vulnerability management program;
A case study of one large, multinational organization that has experienced this evolution and growth
Adding "analytics" and "intelligence" aspects to the vulnerability management function help to ensure that it keeps up with the challenging threat and risk landscape. For example:
Analytics: The vulnerability management program produces a large volume of data related to vulnerabilities, assets, trends, mitigation measures, gaps, compensating controls, etc. Converting the raw data to information using organization context and then to insights based on the risk landscape can provide real value for risk management decisions and actions.
As an example, analytical information on the vulnerability root cause, its link to vulnerability trends and assets can help effective mitigation. Similarly, vulnerability remediation analytics can help identify weakness in the process for improvements.
Intelligence: Typically, the vulnerability management process starts with vulnerability identification, which depends on vulnerability scanning. That's the start in the find-and-fix process. A critical miss in the process can be any weakness in the "find" step, either due to tool functionality or zero day vulnerabilities.
Adding vulnerability intelligence to the management process from authoritative sources and mapping them to the organization assets and their specific configurations would remove critical gaps in the find process.
You might also be interested in …







