- Details
- Category: Security News
Breach Preparedness , Data Breach , Risk Management
Epic Systems vs. Tata: Key Security Questions Protecting Trade Secrets From Unauthorized Users
A whistleblower paved the way for electronic health records vendor Epic Systems' trade secret theft lawsuit against Indian IT consultancy Tata Consultancy Services, which resulted in the EHR vendor winning nearly $1 billion in damages, pending an appeal.
See Also: Data Center Security Study - The Results
The complex case raises a host of important security questions. But the most important is this: What potential indicators of compromise might have been missed by Epic's security team that could've helped the company detect and stop the apparent unauthorized downloading of thousands of sensitive documents much sooner - without the involvement of an external whistleblower?
In case you haven't heard about the legal battle between Verona, Wis.-based based Epic and Mumbai, India-based TCS, here's a brief synopsis:
At the center of the suit are allegations by Epic, one of the largest U.S. EHR vendors, that TCS consultants - who under a 2005 contract between the two companies were permitted limited access to and use of Epic's software - inappropriately downloaded thousands of confidential Epic documents to benefit "in the development or enhancement" of TCS's competing EHR software, Med Mantra.
Epic claims that a TCS consultant who was working for Epic's customer, Kaiser Hospital Foundation in Portland, Ore., "transferred" his credentials to at least two other TCS employees in India. With those credentials, Epic alleges the other TCS workers downloaded, via Epic' UserWeb web portal, "at least 6,477 documents accounting for 1,687 unique files."
In an amended January 2015 complaint that updates the original complaint Epic filed against TCS in October 2014, Epic said the documents downloaded by TCS personnel included, among other things, "confidential, proprietary and trade secret documents detailing over 20 years of development of Epic's proprietary software and database systems."
According to Epic's lawsuit, that includes programming rules and processes developed to produce optimal functionality of Epic's software, documents that decode the operation of its source code and information regarding Epic's system capabilities and functions.
Epic charges that through "illegally gained" access, TCS "brazenly" stole the trade secrets and confidential information, and that "the theft appears to have been masterminded in Mumbai, then carried out in both India and the U.S. through employees of a U.S. subsidiary of Tata Consultancy Services called Tata America International Corporation."
TCS's Response
TCS, in a statement issued after the April 15 jury decision, says it "did not misuse or derive any benefit from downloaded documents from Epic System's user-web portal. TCS plans to defend its position vigorously in appeals to higher courts."
The India-based consultancy adds that it "appreciates the trial judge's announcement from the bench that he is almost certain he will reduce the damages award." TCS says that it "did not misuse or benefit from any of the said information for development of its own hospital management system 'Med Mantra,' which was implemented for a large hospital chain in India in 2009."
'Informant' Tip-Off
Epic says it learned about the alleged inappropriate downloading of documents through an "informant" identified in Epic's amended complaint as a TCS employee who was responsible "for managing all aspects of TCS's contract with Kaiser to provide consulting services and reported directly to TCS executive management."
But why didn't Epic's own internal data security sleuths discover the alleged inappropriate access to intellectual property? That's just one of many questions this fascinating case raises. Others include:
How might have Epic prevented the credentials of an authorized user - with supposedly limited access - from being used to access and download information that Epic deemed sensitive, as well as irrelevant, to the user's role? What steps could Epic have taken to detect that the credentials of an authorized user in the U.S. were being inappropriately shared with unauthorized individuals in India? How might have Epic better secured its sensitive documents containing trade secrets? By encrypting the documents? By isolating the documents on a separate network or system? By implementing data loss prevention or other technology that might have stopped the information from flowing outside a perimeter?These days, the media spotlight is on data breaches that expose individuals' personal information, rather than those that expose intellectual property. Hopefully the Epic System case will call attention to the need to ramp up efforts to protect all information.
- Details
- Category: Security News
Anti-Malware , Data Loss , Encryption
Jigsaw Ransomware Adds Insult to Injury "Saw"-Themed Malware Deletes Encrypted Files While Users Watch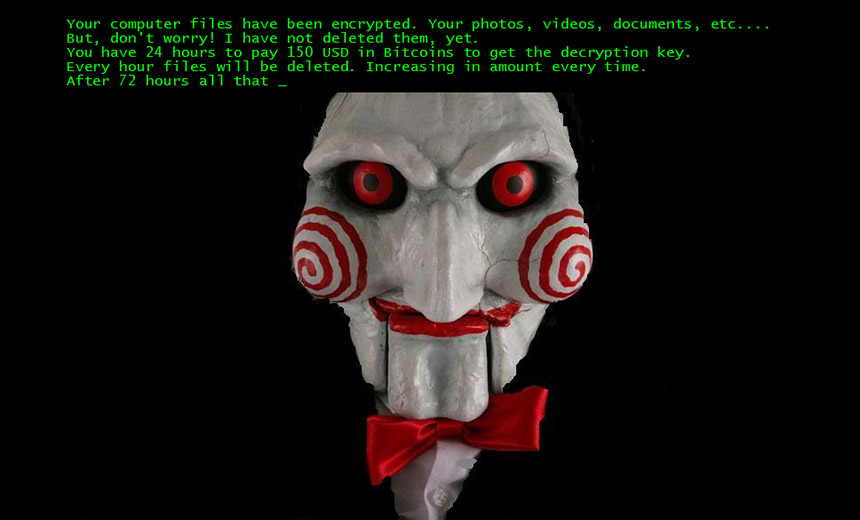 Jigsaw's ransom note. (Source: Trend Micro.)
Jigsaw's ransom note. (Source: Trend Micro.)What could be worse than a ransomware infection? How about getting infected by crypto-ransomware that taunts you by slowly deleting your encrypted files while increasing the ransom demand until you pay for the decryption key? And don't reboot your PC, or else the ransomware will delete 1,000 files at once as a reprisal.
See Also: How to Measure & Communicate Return on Cybersecurity Investments
That's the premise behind Jigsaw, a new strain of ransomware that not only tries to increase the pressure on victims to pay, but which also references the "torture porn" horror film series "Saw." In particular, the film's fictional serial killer, John Kramer, is nicknamed the Jigsaw Killer, and communicates with victims using a puppet called "Billy," which the Jigsaw ransomware author - or authors - also employ in their ransom note.
The ransomware also apes the red clock used in the movie to count down to deadlines imposed by the killer, to show victims how much time is left before more files get deleted, and the ransom demand increases. And after 72 hours, the ransomware deletes every encrypted file on the PC (see Ransomware: Is It Ever OK to Pay?).
This latest twist in ransomware appears to have been coded on March 23 and to have been used in live attacks by the end of the month, says Andy Settle, head of special investigations at Raytheon's cybersecurity business Forcepoint - formerly known as Websense - in a blog post. "This malicious program starts encrypting your files while adding, with no irony, the '.FUN' file extension," he says. "Using horror movie images and references to cause distress in the victim is a new low."
Other variants of the ransomware, meanwhile, copy and encrypt files using .KKK, .BTC, and .GWS extensions, before deleting the originals, Jasen Sumalapao, a malware analyst at Trend Micro, says in a blog post. He adds that the ransom note exists in both English-language and Portuguese-language versions, and that the lowest possible amount that victims can pay - before the demand starts increasing - ranges from $20 to $150 in bitcoins.
Jigsaw's Real-Time Shakedown
How the ransomware attack unfolds, as seen on an infected PC. (Source: Forcepoint.)No Free Lunch
Trend Micro says Jigsaw appears to be distributed via adware and "grayware" - a.k.a. "potentially unwanted applications" such as "free toolbars" - as well as via sites that host adult content. Many attacks likely begin with a "malware dropper" infection, which then downloads and installs a copy of Jigsaw being hosted on the free cloud storage service 1fichier.com. "This service has previously hosted other malware like the information stealer Fareit, as well as Coinstealer, which gathers bitcoins," Sumalapao says. "We already notified 1ficher about this incident and they already removed the said malicious URLs." Other versions of Jigsaw have also been seen at the waldorftrust.com website, he adds, noting that the ransomware has likely been bundled with applications that claim to be "cryptominer" software for using PCs to generate cryptocurrency. (Hint: they're often fake.)
Forcepoint says the Jigsaw variant that it studied was written in .NET code, which the developer attempted to obfuscate - "to prevent analysis" - and failed. As a result, security researchers have been able to recover the encryption key hardcoded into the malware, as well as 100 different bitcoin addresses to which ransoms can be paid. Settle says those addresses have now been shared with authorities (see Tougher to Use Bitcoin for Crime?).
Since the Jigsaw encryption key has been recovered, security researchers have also been able to publish instructions for removing Jigsaw infections. Of course, it's a sure bet that Jigsaw's developers will soon correct their coding errors in a new version, which is precisely what happened after the developers behind TeslaCrypt fumbled their crypto last year.
"Torture Ransomware" - Commodity Twist
Jigsaw continues the age-old practice of criminals - including online attackers - employing "psychological levers" in an attempt to trick or compel victims into parting with their money.
But functionally speaking, as with banking Trojans, point-of-sale malware and now ransomware, there's often scant difference between different malicious code families. To up the ante, attackers have in some cases begun targeting not just individual PCs, but entire enterprises, including hospitals, looking for bigger one-off ransom payments.
Taking a page from the consumer-goods industry, meanwhile, some attackers are instead focusing on branding. "These days, the name of the crypto-ransomware game is to add 'unique' features or 'creative' ways to instill fear and put more pressure to users to pay up, despite the fact that, when it comes to their technical routines, there's not much difference among these malware," Trend Micro's Sumalapao says.
Enter "torture ransomware." And the fact that we've gotten to the point where ransomware developers are coding horror-movie variations demonstrates not just the relative ease of creating this type of malware, but the incredible profit potential.
Beat the Odds
As always, security experts' anti-ransomware advice remains the same, with or without attackers employing ransom notes featuring sadistic puppets named Billy:
Maintain up-to-date backups. Ensure backups are stored offline, so ransomware can't reach it via connected, network-based or cloud-based drives. Regularly test backups. Run anti-malware software to block known strains of ransomware. Keep all applications and operating systems up to date. Don't fear the ransomware.For more extensive advice, see security expert Bart Blaze's list of top-notch ransomware defenses for both individuals and organizations. In horror-movie terms: Prepare, so you don't have to pay.
- Details
- Category: Security News
Prosecutors have expanded a complex case, involving an alleged pump-and-dump stock scheme, hacking into U.S. banks and operating an unlicensed bitcoin exchange, to include money-laundering charges related to processing bitcoin ransoms paid by ransomware victims.
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
The alleged pump-and-dump stock scheme involved hacking into 12 U.S. banks to steal contact details for high-net-worth individuals, as well as using the bitcoin exchange Coin.mx to allegedly launder illegal profits, in part, via offshore shell companies.
On April 21, Preet Bharara, the U.S. Attorney for Manhattan, revised an indictment against Coin.mx operator Anthony Murgio and co-defendant Yuri Lebedev to include Anthony's father Michael as a defendant, also adding a charge of conspiracy to commit money laundering, according to court documents.
The revised indictment accuses all three of a conspiracy involving exchanging bitcoins obtained from ransomware victims for cash as well as failing to report related, suspicious transactions to authorities, in violation of U.S. anti-money laundering rules. All three are Florida residents (see Report: Spammers Tied To JPMorgan Chase Hack).
The charges against Anthony Murgio and Lebedev - first announced in July 2015 by the Manhattan U.S. Attorney's office - relate, in part, to their allegedly operating Coin.mx, which prosecutors say was an unlicensed money-transmitting business used to illegally move money out of the United States to overseas bank accounts (see Tougher to Use Bitcoin for Crime?).
The Latest Arrest
On April 21, the FBI arrested Michael J. Murgio, who appeared the same day in U.S. District Court in Florida, according to court documents. NBC News affiliate WPTV reports that Michael Murgio is a member of the Palm Beach County School Board. He's due to be arraigned in New York on April 26.
The elder Murgio's arrest followed a previous revision of the indictment, in March, which added Trevon Gross as a defendant. Gross formerly headed the New Jersey-based federal credit union Helping Other People Excel - "Hope FCU" - which primarily served individuals with low incomes, according to court documents. Prosecutors have accused Gross of accepting $150,000 in bribes from Anthony Murgio and his associates in exchange for allowing them "to take control of Hope FCU" by installing multiple co-conspirators on the board of directors and allowing them to operate the organization "as a captive bank for their unlawful bitcoin exchange until at least late 2014," according to court documents.
Authorities say related, questionable payment processing activities were discovered by the National Credit Union Administration, which forced the credit union to stop all such processing.
The NCUA says it placed Hope FCU into conservatorship in October 2015. "The agency made the decision to liquidate the credit union and discontinue operations after determining it was insolvent and had no prospect for restoring viable operations," NCUA says in a statement. An NCUA spokesman wasn't immediately able to comment on whether the alleged bitcoin money laundering or charges against Gross were directly related to Hope FCU's closure.
Gross, who's a minister, has pleaded not guilty to related charges, Bloomberg reports.
Bigger Case Included Alleged Bank Hacks
The Coin.mx and Hope FCU allegations are part of a much bigger case involving an alleged pump-and-dump stock scheme as well as a U.S. bank hacking spree (see Charges Announced in JPMorgan Chase Hack).
The Manhattan U.S. Attorney's office unsealed a related, 11-count indictment in July 2015 against three men that they accused of having earned $2.8 million via an illegal pump-and-dump stock scheme that involved blasting out millions of spam emails per day to artificially "pump" up the price of penny stocks they owned, before then "dumping" the stocks and making a profit. The scheme was reportedly tied to hack attacks against such financial services heavyweights as JPMorgan Chase, Fidelity Investments and E*Trade Financial that occurred from 2012 to mid-2015.
Authorities in November 2015 indicted three men - Israeli nationals Gery Shalon and Ziv Orenstein, as well as U.S. citizen Joshua Samuel Aaron - as part of an alleged scheme involving hacking into 12 U.S. banks, manipulating securities markets, and using offshore shell companies to hide funds. Prosecutors have accused Shalon of masterminding the operation, and both he and Orenstein have been arrested, while Aaron remains at large.
From April 2013 until July 2015, Shalon helped direct - if not control - Murgio's Coin.mx bitcoin exchange, federal prosecutors claim.
- Details
- Category: Security News

Visa's new plan to help merchants speed checkout times for EMV chip payments sounds good, in theory. But in reality, it isn't likely to have much immediate impact on either speeding EMV adoption or enhancing the user experience.
See Also: The Inconvenient Truth About API Security
A majority of U.S. merchants are still trying to get their EMV terminals certified as compliant with chip card standards so they can be put to use (see EMV: Chargebacks Hitting Merchants of All Sizes). Without EMV terminals turned on at the point-of-sale, an add-on feature or upgrade aimed at speeding the EMV transaction process is, well, useless.
What Visa and other card brands should be focused on, for now, is ensuring that all U.S. merchants are able to accept EMV chip payments as soon as possible. To do that, they need to devise ways to help processors and third-party POS vendors streamline their EMV certification processes. After that, working on improving transaction times would be appropriate.
Visa's Quick Chip Announcement
On April 19, Visa announced the launch of Quick Chip for EMV, a POS software upgrade that purports to speed an EMV chip transaction to 2 seconds or less, substantially faster than current speeds.
Visa says it developed the software for Quick Chip to improve the merchant and customer experience. Merchants and consumers alike have complained about the slow process of conducting EMV chip payments - which require chip cards to be inserted into POS terminals and left there until transactions are processed.
Quick Chip is designed to speed the payment process by enabling consumers to insert their chip cards into the reader and immediately remove them, similar to the time it takes to swipe a magnetic stripe card. In this way, Quick Chip makes contact EMV payments similar to contactless, tap-and-go EMV payments, which are widely used in other parts of the world, says Visa spokeswoman Sandra Chu.
"In 2011, when Visa first announced the roadmap to bring more secure chip technology to the U.S., we also encouraged the industry to adopt contactless chip technology, which would provide a faster chip experience just as it has in countries like the U.K. and Australia, where about 70 percent of transactions are made using contactless cards," she says. "Visa also communicated recommendations to not only streamline the implementation process but also optimize speed of transactions. Now that the migration has progressed, there seems to be more industry willingness to try to find ways to make chip transactions even more convenient for merchants and consumers."
Quick Chip does not require additional testing or certification and can be implemented without any changes to EMV chip cards, Chu adds.
MasterCard recently came out with a similar solution called M/Chip Fast, which brings "some of the principles successfully implemented for contactless cards and mobile wallets around the world to point-of-sale terminals," MasterCard says.
MasterCard did not respond to my request for clarification about how its software upgrade is being distributed.
Faster Payment, New Risks?
It's not a given that all EMV-compliant merchants on the Visa network will automatically be offered access to Quick Chip.
Visa is distributing Quick Chip software through payment processors, POS vendors and other technology partners. Given what we've seen with the challenges most of these providers have had in simply getting POS devices certified for EMV payments, I find it hard to believe they will have a streamlined process to get Quick Chip out to merchants that are capable of using it and want it (see EMV: Not Ready for Prime Time?).
"Some merchants are having significant problems with chip cards processing very slowly," says Shirley Inscoe, an analyst at consultancy Aite. "Consumers tend to want to remove the cards after a bit, then the slow transaction has to begin all over again. But the distribution mechanism for this upgrade is indeed a concern."
And despite Visa's promises that Quick Chip won't require additional EMV certification or security checks, some payments experts are skeptical.
"We're concerned about one-off efforts by any single network or industry player that could have the impact of further confusing things at the POS," says Mark Horwedel, CEO of the Merchant Advisory Group, which represents 85 of the largest U.S. merchants. "There is obviously a speed problem with EMV, and this technology may provide some relief. But early comments from some of our more EMV-savvy members suggests it may have some negative consequences for fraud mitigation, and likely will require even more certification on the heels of what is already a too costly and too cumbersome situation."
If only some, but not all, EMV-compliant POS terminals are upgraded to offer Quick Chip or M/Chip Fast, consumers could become even more confused about the chip card transaction experience.
And we can expect to see more challenges on the back end for processors, who soon could be faced with trying to integrate software updates from each of the card brands. Wouldn't a single, interoperable solution make more sense?
It's too bad that the issue of transaction speed was not adequately addressed before the first EMV terminal went into service in the U.S. But for now, let's focus on finishing the EMV rollout, and then worry about speeding the transaction times.
- Details
- Category: Security News

A massive collection of documents from Qatar National Bank, based in Doha, was leaked and posted online to the whistleblower site Cryptome on April 26. The leaked data, which totals 1.4 GBs, apparently includes internal corporate files and sensitive financial data for QNB's customers.
See Also: How to Mitigate Credential Theft by Securing Active Directory
Cryptome reports that the leak comprises 15,460 files, containing details, including passwords, PINs and payment card data, for hundreds of thousands of the bank customers' accounts. Multiple experts have also examined the data, and likewise report that it appears to be legitimate. But Cryptome offered no insights into how the data was obtained, for example, if it was via an external hack attack, or an inside job.
2/2 QNB hack: 15.4K docs, 1.4GB, most tiny, dozens big. Zip (431MB): https://t.co/R4jiU8iXEy (RU?) /@aljazeera______ pic.twitter.com/KXjI2ELvzi
QNB did not respond to Information Security Media Group's email request for more information. But the bank released a statement April 26 that references "social media speculation in regard to an alleged data breach," saying that "it is QNB Group policy not to comment on reports circulated via social media."
QNB, however, did comment on those reports by saying that "there is no financial impact on our clients or the bank" and that it is "further investigating this matter in coordination with all concerned parties."
Authenticity of Data
ISMG was not immediately able to verify the authenticity of the information contained in the data dump. But multiple apparent customers who were directly contacted by ISMG, using the information contained in the data dump, confirmed that the leaked information about them was accurate.
Multiple sources who have reviewed the data dump have also confirmed to ISMG that the data appears to be genuine. One researcher, speaking on condition of anonymity, also confirmed that he had successfully used leaked customer internet banking credentials from the data dump to begin logging in to the customer's account, purely for research purposes. But he said the bank's systems then sent a one-time password to the customer's registered mobile number, which would serve as a defense against any criminals who might now attempt to use the leaked data to commit fraud.
Security engineer Omar Benbouazza, an organizer of the RootedCON conference, likewise believes that leaked data is legitimate. He's analyzed the leaked documents and found that the IP addresses listed, as well as information relating to these IP addresses, plus administrator information, appeared to belong to QNB and relate to QNB's mobile banking service, hosted at apps.qnb.com and apps.qnb.com.qa.
Confirmed. QNB was breached #qnb #databreach pic.twitter.com/YTqXCztwAW
Information expert Nitin Bhatnagar, who heads business development for cybersecurity firm SISA Information Security, also says the leaked data appears to be genuine. Based on his analysis of the leaked data, the dump contains nearly 1 million payment card numbers, along with expiration dates, credit limits, cardholder details and other account information, all stored in clear text. Also present in the dump are banking documents, including sensitive information on the bank's retail business and banking application, plus administrator-level account access details, he says.
The leak contains PII, which could have serious repercussions for customers, Bhatnagar says. A sample customer profile, for example, includes a national identification number, social media profile links, card numbers, expiry dates, logins, passwords and password-reset questions, among other data - all stored in clear text.
Intelligence Agency Reports?
Although analysis of the leaked data remains ongoing, there are reports that it contains additional, unusual information. U.K.-based digital media news site IBTimes, for example, reports that in addition to consumer data, the leaked information also includes documents with information on Qatar's Al-Thani royal family as well as the broadcaster Al Jazeera, which is partly funded by the same family.
In addition, some leaked folders are marked "Spy" and contain what appear to be intelligence dossiers on individuals, according to IBTimes. Some files contained in the dump are labeled as "MI6" - in apparent reference to the British intelligence agency - with others naming Qatar's state security bureau, known as the Mukhabarat, as well as French and Polish intelligence agencies, IBTimes reports.
More Articles …
Page 3417 of 3546
