- Details
- Category: Security News

A recent federal court ruling against a bold motion by health plan Anthem Inc., which is fighting a consolidated class-action lawsuit in the wake of its massive data breach, spotlights some of the very complex questions that are at the center of many data breach cases.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
Because there are so many large data breaches these days, how can an individual who potentially suffers identity theft or tax fraud ever know for sure the root cause of those crimes? Was it the Anthem breach, or perhaps one of the countless other breaches that have occurred in recent years? Perhaps the ID theft was even caused by a breach that occurred on a consumer's own computer.
That last argument was at the center of a recent request by Anthem's attorneys "for access to computers of former customers who accuse the insurance giant of failing to protect their personal information in an enormous data breach last year," reports Courthouse News Service.
Just to refresh your memory, a hacker attack on Anthem exposed the data of nearly 80 million current and former health plan members, the insurer revealed early in 2015. About 100 lawsuits against the company have been consolidated into one jumbo federal class-action case that's playing out in California.
Consumer Scrutiny?
Anthem recently filed a motion seeking permission "to access plaintiffs' computers, smartphones and tablets to image and copy them to determine whether the data breach or embedded malware was responsible for the potential harm that could include identity theft and tax problems," the news report says.
But in his oral ruling rejecting Anthem's request, U.S. District Judge Nathaniel Cousins told Anthem it was "ironic that the defense was seeking discovery of the plaintiff's personal information when the core allegations of the plaintiffs is the defense failed to protect them from damage to their personal information," according to Courthouse News Service.
An attorney representing Anthem in the class action suit declined to comment to Information Security Media Group on the ruling.
But attorney Eve Cervantez of the law firm Altshuler Berzon LLP, one of the lawyers representing plaintiffs in the case, tells me: "This is an important ruling for plaintiffs in this and other breach cases."
The court's decision - and Anthem's failed attempt at examining plaintiffs' computers - highlight some of the intricacies woven through many data breach class-action cases.
Where's the Proof?
"It is not uncommon in data breach cases for the defendant to question whether it is the cause of any harm to the plaintiff," notes privacy attorney Adam Greene of law firm David Wright Tremaine.
For instance, "just because a laptop was stolen or a system was hacked, does not mean that it will result in identity theft or other compensable harm," he says.
"Courts often will not award damages based on speculation of potential identity theft. Rather, a court may require evidence of causation; evidence that a particular breach caused the identity theft that caused a particular patient harm," he says. "As we have more data breaches, it becomes more challenging to trace a particular incident of identity theft back to a particular breach incident."
Privacy attorney Kirk Nahra of the law firm Wiley Rein, offers a similar perspective. "Remember, so many of these class-action cases involving security breaches get dismissed early on because there is no allegation of actual damages, which is an element of a complaint in most situations," he notes.
Anthem's tactic of trying to put a spotlight on the weaknesses of plaintiffs' own security practices "isn't common - yet - because most cases haven't gotten to a point where this issue [of ID theft or fraud] is yet relevant," he says.
Blame Game?
So, was Anthem trying to play the "blame the victim" game in requesting to examine plaintiffs' computers for malware or other security problems that could be the root of potential ID theft and tax problems?
"Here, the question is causation of harm," Nahra says. "I don't think it is a 'blame the victim' strategy, but at the same time, it is a very broad approach that may have an impact on lots of individuals," he says. "Given how many security breaches there are, and the fact that many people's information may be subject to multiple breaches, the question of 'cause and effect' is a real one."
Whether the courts will allow this kind of strategy is an open question - and this is one of the first cases to address it, Nahra says. "But, at the same time, if these class actions get beyond the initial stages, we are going to have to have some way of connecting the dots, as we would in any other kind of case making this kind of claims.
"The connection between an action and a harm always needs to made, even in the simplest of tort claims," Nahra notes. "This is just a high tech version of this issue that could involve lots of people."
So, was it fair game for Anthem to raise the question of whether plaintiffs' own weak security practices were potentially to blame for increased risk of ID theft and other crimes? Or was the motion nothing more than a very desperate ploy? I invite you to share your views in the space below.
- Details
- Category: Security News
 FDIC headquarters
FDIC headquartersA House committee is seeking information about security breaches at the Federal Deposit Insurance Corp. in the wake of a former employee departing the agency with a mobile storage device containing sensitive data on more than 44,000 individuals.
See Also: Unlocking Software Innovation with Secure Data as a Service
Rep. Lamar Smith, the Texas Republican who chairs the House Science, Space and Technology Committee, characterizes the breach as "troubling" in an April 8 letter he wrote to FDIC Chairman Martin Gruenberg. "Sensitive information that is housed for any length of time without proper measures in place to mitigate cybersecurity risks is susceptible to a breach," Smith wrote. "Even more troubling, the potential for a breach is especially heightened when sensitive information for over 44,000 individuals is stored without proper security measures."
Smith confirms an FDIC worker in the process of leaving a job at the agency copied personal information of 44,000 individuals onto a personal portable storage device.
According to a memo from Gruenberg obtained by the Washington Post, which first reported the breach, the employee left the FDIC on Feb. 26, taking the storage device from the premises "inadvertently and without malicious intent." Using technology to track downloads to removable devices, the FDIC detected the breach on Feb. 29 and the employee returned the device the next day.
FDIC Eliminating Portable Storage Device Use
FDIC spokeswoman Barbara Hagenbaugh told the Post the agency has eliminated the use of portable storage devices for most employees and plans to do that for others. The former employee signed an affidavit indicating the breached information was not used in any way, Hagenbaugh told the newspaper. The affected data included names, addresses and Social Security numbers. The trade publication American Banker reports the exposed customer information came from closed banks.
Smith says the committee wants to ensure that the FDIC is taking appropriate action to mitigate the risks posed by the incident as well as other cybersecurity risks. The committee seeks documentation regarding the incident as well as detailed descriptions of all major security breaches involving FDIC information since Jan. 1, 2009.
Smith's committee is investigating the breach because it has jurisdiction over the National Institute of Standards and Technology, which develops cybersecurity standards for government agencies.
- Details
- Category: Security News
 OMB Director Shaun Donovan
OMB Director Shaun DonovanThe Obama administration proposes to spend $3.1 billion next year to seed a fund designed to improve cybersecurity by modernizing federal information systems.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
The funding is part of a White House legislative proposal that would establish a board of government IT security experts - headed by the federal CIO - to identify the highest-priority IT modernization projects.
"Ultimately, retiring or modernizing vulnerable and inefficient legacy IT systems will not only make us more secure, it will also save money," Federal CIO Tony Scott says in a White House blog.
Scott's boss, Shaun Donovan director of the Office of Management and Budget, says federal civilian agencies spend nearly three-fourths of their IT budgets maintaining legacy IT systems. "These systems may pose security risks, such as the inability to utilize current security best practices, including data encryption and multifactor authentication," Donovan wrote in an April 8 letter to Vice President Joseph Biden, as president of the Senate, and House Speaker Paul Ryan.
Vulnerabilities, Risks Remain Unresolved
"These systems may also pose operational risks, such as rising costs and inability to meet mission requirements," Donavan said. "Absent immediate action, the cost to operate and maintain legacy systems will continue to grow, while security vulnerabilities and other risks will remain unresolved."
Former CIA CISO Robert Bigman says implementing more modern systems would enable federal agencies "to take advantage of more contemporary IT and security capabilities" not available until recently. As an example, he cites segmenting sensitive applications in the cloud. "Buying this as a service can also include - for a few more dollars - better configuration security, better auditing, better identification and authentication and better encryption," says Bigman, president of the IT security consultancy 2BSecure. "These services were not readily available even three years ago."
Many government stakeholders use mobile devices and cloud computing, says Tom Patterson, chief trust officer at integrator Unisys, which works with the federal government on a number of IT security programs. "That new environment is very difficult to address from a security perspective if you have old equipment," he says. "Having servers sit inside of a room, and putting walls around them, doesn't compute in today's modern environment. You need a different approach, a fresh approach to security. The good news is that if you use modern, advanced technologies instead of trying to drag forward your old concepts into the new world, you can save money and lower your risks at the same time."
Modernization Challenges
Some federal agencies already are attempting to launch IT modernization projects. The Department of Veterans Affairs, for instance, is seeking to nearly double its cybersecurity budget in the fiscal year that begins Oct. 1 to $370 million, in part, to carry out an inspector general's recommendation to replace or upgrade legacy systems, VA CIO LaVerne Council says (see OIG: VA Must Address InfoSec Weaknesses).
Bent Arronte, VA deputy assistant inspector general, in testimony before Congress last month contended "the diversity in applications adversely affected facilities and management's ability to consistently remediate IT security deficiencies agencywide."
But despite OMB's recommendation to increase Department of Labor IT modernization funding, Congress cut the department's modernization budget by $4.1 million in fiscal 2014 and $15.4 million in fiscal 2015. "This lack of funding has directly impacted the ability of DoL to improve its IT security posture, including but not limited to the identity access management project," Labor Department Assistant Inspector General Elliot Lewis wrote in a memo last summer (see 3 InfoSec Woes Plaguing Federal Agencies).
Senator Expresses Concern
Agencies' use of legacy systems that provide less security is a problem recognized by Sen. Tom Carper, the Delaware Democrat who is ranking member of the Senate Homeland Security and Governmental Affairs Committee, the panel that provides federal government IT security oversight. Carper called on the administration to improve the acquisition process to make it easier for federal agencies to acquire the latest information systems that can be more easily secured.
"Flaws in the federal acquisition process can limit the tools agency network defenders can obtain," Carper wrote last week to Donovan, the OMB director. "Because the techniques our adversaries use against us online are always evolving, deploying innovative products and services is critical to staying ahead of the threats we face online. Financial institutions, power companies, retailers and other private critical infrastructure owners are able to quickly reap the benefits of the many new and innovative cyber defense products put on the market each year. Yet it is not clear that federal agencies are similarly able to rapidly acquire new and innovative cybersecurity solutions."
Agencies Repay Modernization Investments
Federal CIO Scott says the $3.1 billion in the Information Technology Modernization Fund would be seed money to fund $12 billion in modernization projects over 10 years, noting that agencies would eventually repay money they receive to modernize their IT so the program would be self-sustaining. The agencies could make the required reimbursement from any appropriation available for IT activities, according to a summary of the proposed legislation.
"By establishing a central fund that agencies must apply to and compete for, the legislative proposal will provide strong incentives for agencies to develop comprehensive, high-quality modernization plans," Scott says. "Additionally, stable funding allows for long-term thinking and shorter development times, rather than costly one-off fixes."
The board to oversee the funding initiative would be chaired by the administrator of OMB's Office of Electronic Government, also known as the federal CIO, with another permanent member being a senior official from the General Services Administration, the federal agency that oversees the acquisition of IT wares and services. Other members of the Information Technology Modernization Board would include representatives from the National Institute of Standards and Technology and Department of Homeland Security as well as three other federal employees - appointed by the OMB director - who primarily have expertise in IT development, financial management, cybersecurity and privacy and/or acquisition.
"By collecting modernization proposals from many agencies, the board can identify opportunities to replace multiple legacy systems with a smaller number of common platforms - something that is difficult for agencies, acting on their own with limited insight into other agencies' operations, to do," Scott says. "As a result, the ITMF will facilitate a transition to common platforms and re-engineered business practices across government. This will both reduce risks and save money."
- Details
- Category: Security News
Anti-Malware , Risk Management , Technology
Exploit Kits Are Targeting Zero-Day Flaw in Flash
Security experts are once again warning all Adobe Flash users to either update or uninstall the browser plug-in software to protect themselves against active exploits. The attack campaigns, which began March 31, have been exploiting a zero-day flaw in the Windows version of the software to install ransomware. Recent versions of Flash for Mac OS X, Linux and Google ChromeOS are also at risk.
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
Adobe has released updated versions of Flash that fix the targeted flaw, which has been designated as CVE-2016-1019. "Adobe is aware of reports that CVE-2016-1019 is being actively exploited on systems running Windows 10 and earlier with Flash Player version 20.0.0.306 and earlier," Adobe says in a security alert.
The flaw is a "type confusion" vulnerability in ActionScript, which is an object-oriented programming language designed for Flash. Type confusion refers to code failing to verify what type of object - meaning a series of coding statements - gets passed to it, which attackers can sometimes exploit to run their own arbitrary code and take control of a system.
But Adobe's latest Flash update includes fixes for 24 flaws in total, many of which are "critical vulnerabilities" that "could potentially allow an attacker to take control of the affected system," it says. The latest - fully patched - version of the Flash Player Desktop Runtime is now 21.0.0.213. Adobe recommends all users upgrade immediately.
Magnitude Exploit Kit Targets Flaw
Adobe says the in-the-wild attacks against CVE-2016-1019 were first spotted by researchers at cloud security firm Proofpoint. In a blog post for Proofpoint, the malware researcher known as Kafeine reports that the firm on April 2 found that the "Magnitude exploit kit was successfully exploiting Adobe Flash version 20.0.0.306" via drive-by attacks. With Flash version 21 now being current, the researchers suspected that the exploit kit was targeting some older Flash flaw. But after sharing the findings with other security researchers, FireEye discovered that the flaw was in fact new, after which the researchers alerted Adobe, Kafeine says.
Magnitude Exploit Kit Traffic
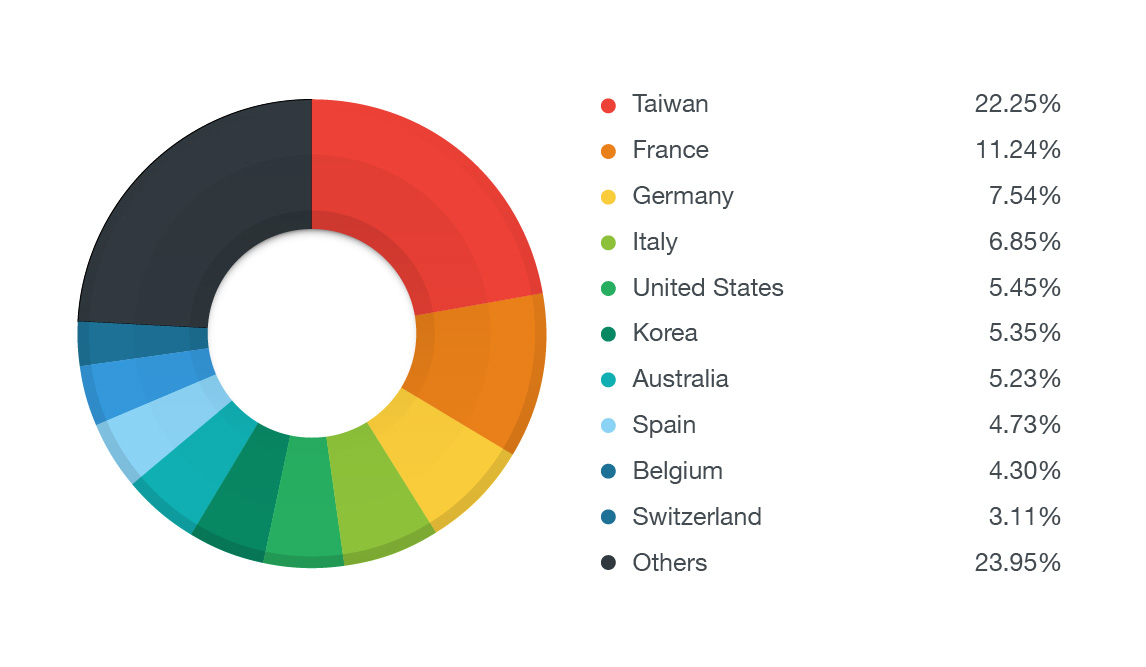 A global view of Magnitude traffic, from March 31 to April 6. Source: Trend Micro.
A global view of Magnitude traffic, from March 31 to April 6. Source: Trend Micro.
Magnitude may not have the name-brand recognition of some of the most prevalent ransomware kits, such as TeslaCrypt and CryptoWall, but it's still a threat. Formerly known as Popads, Magnitude is crimeware that "in recent months ... seems to be used by only one actor," Kafeine says. He adds that the attacker had been using Magnitude to distribute CryptoWall until mid-March, then switched to distributing Teslacrypt, and since the end of March has instead been distributing Cerber, which security firm Malwarebytes describes as new but relatively advanced ransomware that's sold in part via underground Russian forums (see Why Russian Cybercrime Markets Are Thriving). As is typical with ransomware, Cerber will forcibly encrypt most files on a system, then demand bitcoins in exchange for a decryption key.
Cerber Ransom Demand
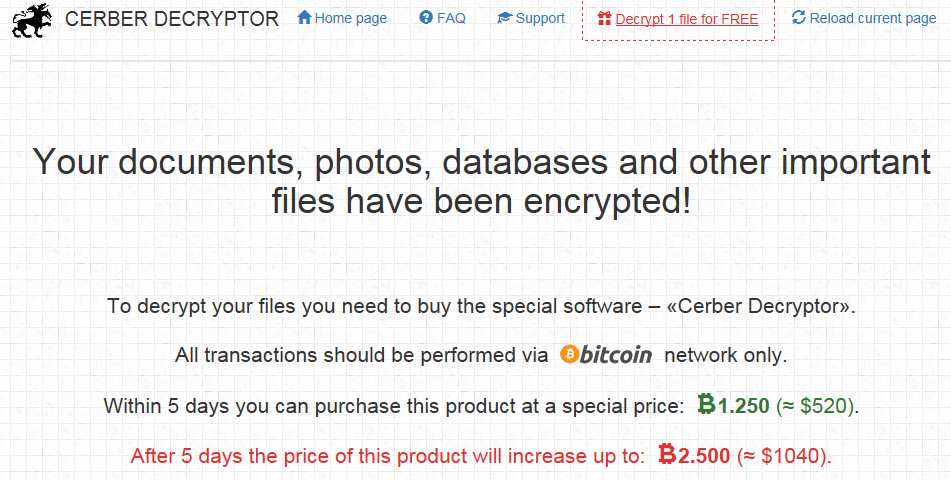 The ransom note displayed by a system that's been infected with Cerber ransomware. Source: Malwarebytes.
The ransom note displayed by a system that's been infected with Cerber ransomware. Source: Malwarebytes.
Kafeine says attackers also attempted to exploit the type-confusion vulnerabilities in Flash version 21, but failed due to a coding error. While ransomware that targeted the flaw can still cause newer - unpatched - versions of Flash to crash, it won't result in arbitrary code execution.
Nuclear Packs Related Exploit
Magnitude isn't the only exploit kit that's been attacking the Flash flaw. Researchers at FireEye and anti-malware firm ESET also discovered that on March 31, an updated version of the Nuclear Pack exploit kit began targeting the flaw and attempting to infect systems with Locky ransomware. That ransomware uses macros, hidden in document files, to disguise related malware. It has been tied to a large number of recent incidents, especially in the healthcare sector, including Methodist Hospital in Kentucky (see Hospital Ransomware Attacks Surge; So Now What?).
Malwarebytes security researcher Jérôme Segura says in a blog post that Flash remains attackers' top choice for launching drive-by attacks, because it can be used to automatically infect large numbers of PCs - and with no user interaction required. Drive-by attacks occur via "compromised sites" as well as via malvertising, he says.
Recommended Action
One option for defending against Flash attacks is to delete the plug-in, and some security experts recommend taking that approach whenever possible.
For anyone who still uses Flash, meanwhile, the prevailing wisdom is to let it auto-update whenever possible. Flash Player 11.2.x or later for Windows, as well as Flash Player 11.3.x or later for OS X, can be set to "allow Adobe to install updates," which will result in automatic updates. All Google Chrome users already see automatic updates across all platforms, as do Microsoft Edge and Internet Explorer for Windows 10 users, as well as Windows 8.1 users running Internet Explorer 11.
For anyone who sticks with Flash, researcher Paul Duckin at security firm Sophos also recommends setting the plug-in to not be allowed to execute whenever it chooses. "If you do need to keep it, make sure you keep it up to date, and use your browser's click-to-play feature (also known as ask to activate) so that Flash content doesn't run without you realizing, especially on sites you've never visited before," he says in a blog post.
- Details
- Category: Security News

The continuing success of attackers stealing billions of dollars from organizations is a sad commentary on the state of corporate security practices as well as our collective lack of cybersecurity smarts (see The Evolving Hacker Mantra: Simplicity).
See Also: 2015 Data Center Security Study - The Results
How else can you react to a recent FBI alert warning that there's been an alarming increase in business email compromise scams? Also known as masquerading schemes, man in the email attacks or CEO fraud, these scams involve criminals trying to trick firms into wire transferring corporate funds into attacker-controlled accounts by impersonating a CEO or other executive (see Business Email Fraud: Who's Liable?).
The combination of easy and lucrative attacks means that - surprise - more and more criminals are lining up to execute these types of scams.
Indeed, the FBI's alert cites $2.3 billion in related, reported losses from October 2013 through February 2016. In the same time frame, law enforcement agencies globally counted 17,642 victims across all 50 U.S. states as well as 79 other countries (see 13 Scenes from an Irish Cybercrime Conference). And since January 2015, the FBI says, the reported number of victims has nearly tripled.
"The schemers go to great lengths to spoof company email or use social engineering to assume the identity of the CEO, a company attorney or trusted vendor," according to the FBI's alert. "They research employees who manage money and use language specific to the company they are targeting, then they request a wire fraud transfer using dollar amounts that lend legitimacy."
Scam: Trick the Money Movers
Various versions of the scam target companies large and small, the FBI says, as well as across industries and sectors, from the largest not-for-profits to the smallest enterprises. But firms that work with foreign business partners or suppliers, or which "regularly perform wire transfer payments," are especially frequent targets, the bureau says.
Will the FBI's alert help stop these attacks? Based on the number of cybersecurity alerts that the bureau has already issued - and our collective failure to stop cyberattacks - don't hold your breath (see Biz Email Fraud Could Hit $1 Billion).
That's despite the fact that as far as "cybersecurity attacks" go, these business email compromises are about as low-tech as you can get. And the lure of an easy payday keeps these attacks coming. Wireless networking technology provider Ubiquiti, for example, fell for one such scheme, and lost $46.7 million as a result.
Ready, Set, Plan Ahead
Thankfully, low-tech attacks frequently have low-tech solutions. Indeed, one related defense that I heard multiple information security professionals suggest at this year's RSA Conference in San Francisco is deceptively simple: Think ahead. In particular, many firms have now created security policies that spell out exactly how wire transfers will be handled. That involves using multiple stages of sign-offs - to help spot any social engineering attacks that might have tricked an employee - as well as preapproved communications channels specifying how such transfers will be commissioned, triple-checked and ultimately approved.
In some cases, attackers will attempt to infiltrate systems and move the money themselves, without trying to trick an insider. That appears to be what happened with the recently disclosed attack against Bangladesh Bank, in which attackers obtained the bank's payment-transfer codes and successfully moved nearly $100 million out of its account at the Federal Reserve Bank of New York.
But with criminals reportedly making oodles of money via much simpler business email compromise scams, in many cases they don't need to bother with these types of more sophisticated attacks (see I Believe in Cybercrime Unicorns). And until businesses put processes and training in place to help prevent employees from falling for these attacks, why would most attackers bother with anything more complicated than simple trickery?
More Articles …
Page 3411 of 3546
