Cybersecurity , Data Breach , Risk Management
Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry- Details
- Category: Security News
Breach Preparedness , Cybersecurity , Data Breach
OCR Outlines Steps to Avoid Falling Victim to Rising Threats
Federal regulators have issued new guidance urging healthcare organizations and business associates to bolster their cyberattack defenses. The advice comes after several high-profile attacks, including one targeting MedStar Health that forced the 10-hospital system to temporarily shutter many of its systems to minimize the spread of malware.
See Also: Proactive Malware Hunting
The Department of Health and Human Services' Office for Civil Rights' alert warns about the dangers posed by ransomware, nation-state attacks and emerging attacks targeting smartphones. It urges organizations to implement a series of key measures to defend against those threats.
"Recent cyberattacks on major healthcare entities have been eye-opening for some healthcare professionals and have changed many views on security for the healthcare sector," says a March 30 update from the Department of Health and Human Services' Office for Civil Rights. The latest update is part of a cyber awareness initiative that OCR launched in January. The first update focused on ransomware and tech support scams (see OCR: Cyber-Awareness Effort: Will it Have an Impact?).
In the latest alert, OCR notes, "In the past, security compliance personnel and their leadership at healthcare entities may have been more focused on issues like security breaches that involve workforce members losing unencrypted laptops or other mobile devices containing patient's protected health information. While lost or stolen devices still represent a large portion of health industry breaches, healthcare sector organizations must consider new cyber threats, as well."
Cyberattacks involving hackers targeting the databases and network systems of healthcare sector organizations "are becoming more common and sophisticated, and may be different from the privacy breaches many entities have seen previously," OCR notes.
Hospital Attacks
The latest OCR guidance was issued as MedStar Health struggled to recover from a malware attack that shut down its IT systems. As of April 3, MedStar said in a statement that it had brought its virtual private network back online, enabling physicians to remotely access MedStar clinical systems.
Although the Washington Post reported last week that the malware attack involved a request for a ransom, MedStar hasn't confirmed that account, and it has not responded to repeated inquiries from Information Security Media Group.
The attack on MedStar followed ransomware attacks that targeted Methodist Hospital in Kentucky, two California hospitals and Ottawa Hospital in Canada (see Hospital Ransomware Attacks Surge; So Now What?). Plus, Hollywood Presbyterian Medical Center in California grabbed headlines in February when it announced it paid extortionists a $17,000 bitcoin ransom to unlock its data.
In addition to those attacks, Mercy Iowa City on March 25 reported a malware attack potentially exposing information on almost 16,000 individuals. That incident was recently added to the OCR "wall of shame" website of health data breaches as affecting 500 or more individuals.
In a statement, Mercy Iowa City says that it learned of the attack on Jan. 29, when law enforcement advised it that a computer virus had potentially infected some of its systems on Jan. 26, 2016. The organization's investigation determined that some of its computers were infected by a virus designed to capture personal data. However, to date, Mercy Iowa City says it has no evidence that patient information has been used improperly.
The organization is working with law enforcement in its investigation. A Mercy Iowa City spokeswoman declined to discuss details of the attack or type of malware involved, but tells ISMG that ransomware was not part of the incident.
Disruptions to Care
OCR's new guidance notes the various ways that "cyber threats and attacks can disrupt healthcare entities' information systems and cause delays in patient care." For example, certain attacks can slow down the process of providing patients their daily medication or meals; printing patients' labels, ID badges or discharge papers; and accessing patient medical records, the alert notes. "Some attacks can affect life-saving medical devices."
In fact, security experts, as well as government agencies, including the Department of Homeland Security and Food and Drug Administration, have been warning healthcare entities for the past several years about the potential cybersecurity risks to medical devices and other healthcare equipment connected to the internet (see Security Flaws in Legacy Medical Supply Systems Spotlighted).
Ransomware Attacks
As for the recent string of ransomware attacks on hospitals, OCR notes that "hackers and ransomware tools are becoming more sophisticated." But to fend against these attacks, which involve attackers locking up databases and files with encryption, OCR suggests healthcare entities take a number of steps that are recommended by the U.S. Computer Emergency Readiness Team, including:
Performing regular backups of all critical information, keeping data on a separate device and keeping backups stored offline; Maintaining up-to-date anti-virus software and keeping operating system and software up to date with the latest patches; Not clicking on unsolicited web links in emails, and using caution when opening email attachments.OCR also notes that the FBI discourages healthcare entities and business associates from paying the ransom, "as this does not guarantee files will be released."
Privacy and security expert Kate Borten, founder of consulting firm The Marblehead Group, says that the FBI's advice about not paying a ransom is well grounded, but likely unrealistic for some organizations struggling desperately to unlock their data in the wake of a ransomware attack. "While I understand the reasons behind the FBI's message, I suspect CEs and BAs who find themselves in this position are likely to pay the ransom rather than play chicken with the bad guys."
Privacy attorney David Holtzman, vice president of compliance at the security consulting firm CynergisTek, notes: "It is most important to note that the cyberattacks - whether they be ransomware, infiltration of malware or keyloggers - that permit exfiltration of data have a common denominator of an email phishing attempt that activates when a link included in the message is selected by the recipient." He says healthcare entities must "recognize that the best ways to battle this is through monitoring what is going on in your information system along with user education on how to recognize and avoid opening up emails from sources that are not recognized."
Nation-State Attacks
OCR also warns that it's not only ransomware attacks that healthcare entities and business associates need to be worried about. For example, healthcare entities may be the target of hackers in China, Russia and several countries in Eastern Europe, OCR notes. "The motivation for this type of attack varies from collecting protected health information for sale and collecting data for intelligence-building and potential espionage, to stealing intellectual property from medical technology companies."
To mitigate the risk of nation-state attacks, OCR advises covered entities and business associates to refer to advice from the FBI that includes:
Recognizing internal and external security threats to the entity's sensitive data and implementing a plan for safeguarding it; Confining access to an entity's sensitive data to a need-to-know basis; Providing training to employees about its data security plan and how to avoid email attacks involving phishing; Avoiding storing private information on any device that connects to the internet.Smartphone Attacks
OCR also warns healthcare organizations to be on the lookout for emerging attacks targeting smartphones. "Patients, staff and third-parties of covered entities are using smartphones to interact with new healthcare applications and medical devices. Although smartphones have beneficial features, entities must ensure these devices have appropriate safeguards against cyberattacks," the guidance says.
OCR notes that the U.S. CERT advises organizations to mitigate the risks of a cyberattack on smartphones by implementing such security practices as:
Enabling the password feature on mobile phone, as well as enabling encryption, remote wipe capabilities and antivirus software; Checking what permissions mobile applications require. If the permission seems beyond what the application should require, do not install the application; Setting Bluetooth-enabled devices to non-discoverable; Avoiding using unknown Wi-Fi networks and using public Wi-Fi hotspots; Deleting all information stored in a device prior to discarding it.While the OCR updates include important information, OCR should consider other ways to draw more attention to the advice, Holtzman contends.
"OCR is missing an opportunity to provide meaningful assistance and updates to the healthcare sector with a monthly 'newsletter' on cybersecurity," he says. "The threats posed by cybercriminals evolve too quickly to justify this response from the front-line agency responsible for safeguarding American's health information privacy. A more effective approach would be to pass along the weekly bulletins and alerts provided by the US-CERT."
- Details
- Category: Security News
- Details
- Category: Security News
Today's distributed enterprise faces two key challenges: Provide top-notch cybersecurity and ensure a seamless user experience. Paul Martini, CEO and co-founder of iboss Cybersecurity, discusses a new strategy designed to meet both goals.
The problem is that employees work everywhere today - at home, on the road, in different geographic regions, on multiple devices - and yet that data protection and user experience both need to be on par with what one would find in a corporate office.
"You want the user not only to have the same consistent experience while they surf the web, use email or use cloud applications," Martini says. "But you also want them to be just as secure."
Organizations historically have tried different approaches to ensuring security and a consistent user experience. But iboss, with its "elastic container," believes it has found a unique new strategy.
In an interview about securing the distributed workforce, Martini discusses:
The challenge of providing both security and seamless user experience; The iboss 'elastic container' approach to security; How to overcome the challenges of complexity and legacy systems.As CEO and co-founder of iboss Cybersecurity, Paul Martini pioneered the award-winning iboss Secure Web Gateway (SWG) and has furthered iboss' position as a leading security innovator with the introduction of FireSphere and iboss Cloud.
- Details
- Category: Security News

The number of information security analysts in the United States grew by 8 percent in the first three months of 2016, reaching a record 78,300, according to Information Security Media Group's analysis of U.S. government employment data.
See Also: 2015 Data Center Security Study - The Results
At the same time, the size of the information technology workforce - including occupations with IT security responsibilities such as network and computer administrators and computer systems analysts - inched ahead by 1.7 percent in the first quarter to nearly 5 million, also a record.
U.S. Information Security Analysts Workforce
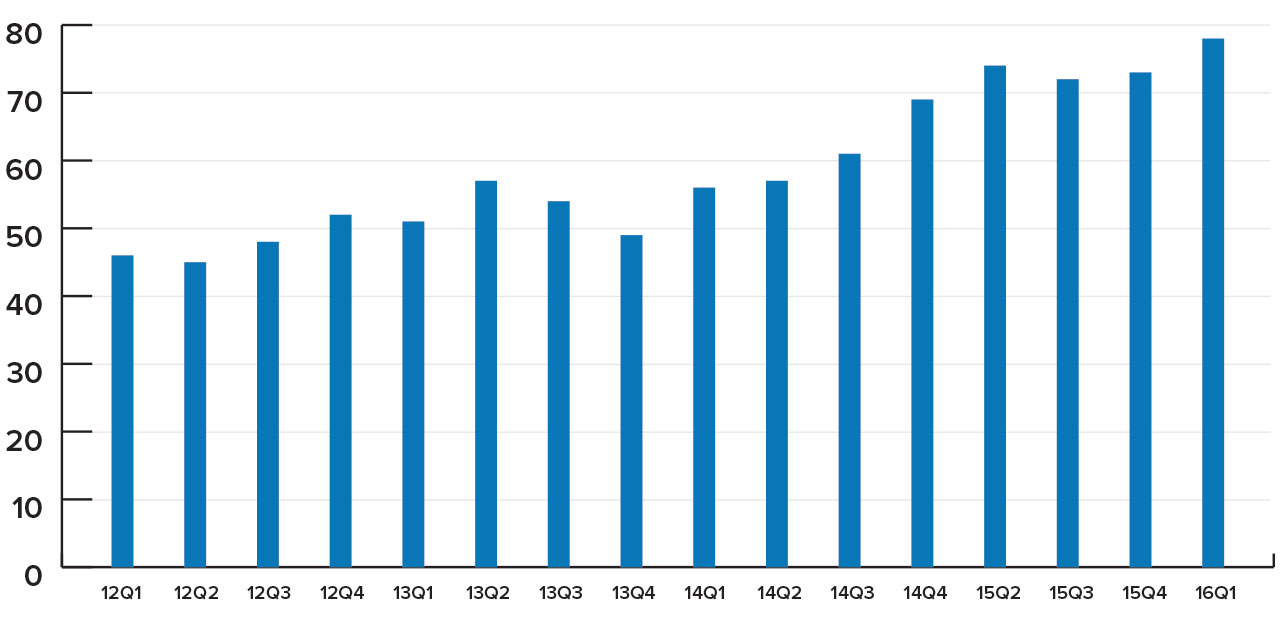 ISMG analysis of Bureau of Labor Statistics data
ISMG analysis of Bureau of Labor Statistics dataOver the past four quarters, the size of the information security analyst workforce increased by nearly 14 percent. During the same period, the IT workforce rose by 2.2 percent.
IT Workforce
Here is the size of the IT workforce during the first quarter of 2016 for each of the computer-related occupations the BLS tracks:
Source: ISMG analysis of Bureau of Labor Statistics dataCatastrophic Conditions
Despite the increase in the IT security workforce, organizations continue to struggle to identify qualified personnel to hire. "We're coming up on catastrophic conditions, if we're not already there, in the labor market in terms of the gap between companies unable to find or breed (internally) or have sufficient talent available to them to do what they want to do," says David Foote, co-founder of the IT employment research firm Foote Partners.
By some estimates, a shortfall of more than 200,000 IT security specialists exists in the United States.
Finding qualified cybersecurity personnel is especially acute in the federal government. The government has authorized the Department of Homeland Security to hire 1,000 cybersecurity specialists (see 4 Barriers to Hiring DHS InfoSec Experts). But that will be a challenge. At a Senate hearing last month, Homeland Security Secretary Jeh Johnson said the government cannot match the salaries offered by private companies for employees with IT security skills. "We need more cyber talent without a doubt in DHS, in the federal government, and we are not where we should be right now," Johnson told the Senate Homeland Security and Governmental Affairs Committee.
Who's to blame for the chasm? "The skills gap at most companies is a self-inflicted wound," Foote contends. He argues that employers should have had the forethought years ago to convert existing personnel to cybersecurity specialists. "In many companies, [there] are a number of systems and network people that are doing a lot of the heavy lifting in security. Why not cross-train those people to assume a higher level job in security rather than just bury them in firewalls and all of that stuff? They just didn't do it."
Foote sees other ways to close the skills gap: automate security processes, work with academia to provide real-world experience to students studying IT security and participate in vendor partnerships that provide IT security solutions.
Defining InfoSec Occupations
As IT security becomes more important to the enterprise, a growing number of occupations incorporate IT security skills.
BLS defines information security analysts as those who plan, implement, upgrade or monitor security measures for the protection of computer networks and information. They may ensure appropriate security controls are in place that will safeguard digital files and vital electronic infrastructure and respond to computer security breaches and viruses. Job titles could include computer security specialists, network security specialists and internet security specialist.
Foote questions the methodology BLS uses to identify occupations, contending the government agency misses many jobs in the IT workplace. "They have a taxonomy that completely ignores a lot of the jobs in IT," he says. "They have different titles, and they can't track that information."
But defining what occupations require IT security skills isn't simple. "People working in the field don't agree on titles or skills sets required for a position," Purdue University Computer Science Professor Eugene Spafford says. "Imposing an occupation classification may or may not be useful. Many employers don't know what it is that they want."
Why Report BLS Numbers?
Historically, the BLS numbers have reflected IT and information security employment trends, especially after they're annualized, which we've done for this report.
That's attained by adding four quarters worth of survey data and dividing the result by four. For example, to arrive at the 78,300 figure for the information security analyst workforce, we took the reported numbers for the last three quarters of 2015 and the first quarter of 2015 then divided by four.
If deficiencies exists in the way BLS tracks IT and information security employment, why do we report it? They're the only official numbers available. We'll explain how BLS determines its classifications and the employment numbers it collects and allow you to decide what they mean.
BLS recognizes that shortcomings exist in the way it defines IT and IT security occupations. The bureau says it's revising its Standard Occupation Classification and might add new information security occupation descriptions. Later this spring, BLS is expected to publish new SOCs that would take effect in 2018. The last update of the SOC occurred in 2010, with the first employment surveys based on it occurring in 2011.
Culling Employment Data
For this report, the workforce numbers come from the government's Current Population Survey of American households, the same survey BLS uses to determine the monthly unemployment rate. Survey takers interviewing households ask respondents characteristics about their jobs and then determine their appropriate occupation category.
BLS each quarter furnishes, upon request, a breakdown of 535 job categories, including the ones labeled information security analysts, database administrators and network and computer systems administrators. Because the survey size for some individual occupation categories, such as information security analysts, is too small to be statistically reliable, BLS neither officially publishes this data, nor claims it's reliable. BLS Economist Karen Kosanovich explains that occupations, such as information security analysts, with a base of less than 75,000 for quarterly averages, don't meet the bureau's publication standards.
- Details
- Category: Security News
Anti-Money Laundering (AML) , Compliance , Cybersecurity
If You Hide It, They Will Hack What the 'Panama Papers' Tell Us
When it comes to articulating lessons to be learned from the so-called "Panama Papers" leak, the top takeaway would seem to be a no-brainer. To riff on the famous Kevin Costner fantasy-baseball flick "Field of Dreams" line: "If you hide it, they will hack."
See Also: Proactive Malware Hunting
In other words, don't hide - or help hide - money in illegal, offshore shell companies, and don't let your friends and family do so either. Otherwise, you may face some difficult questions. Indeed, as everyone from the government of Pakistan and the now-former prime minister of Iceland to British Prime Minister David Cameron and Russian President Vladimir Putin have discovered, transparency is a bitch.
Of course telling many politicians or owners of mega-corporations - as well as other, more garden-variety insanely rich types - to not dodge taxes is a bit like telling governments to avoid land wars in Asia. But in what might seem like a rare occurrence, these shadowy dealings have been brought into the light, thanks to the leak of data from Panama-based law firm Mossack Fonseca, which has reportedly helped numerous individuals and organizations create offshore shell companies.
Cue Cyber-Class Warfare
If you cast the Panama Papers leak in terms of class warfare, this isn't the first time that a faceless few have acted for what they perceive to be the good of the proletariat, in a bout of hacker - or insider - vigilantism.
Love them or loathe them, you could say the same about:
Chelsea Manning: The former Private Manning leaked a classified U.S. Army video of an Apache helicopter crew in Baghdad firing on and killing 11 adults - including two Reuters reporters - and seriously injuring others, including two children. Also leaked an archive of 251,287 sensitive U.S. State Department cables. Edward Snowden: Leaked National Security Agency documents that detailed secret - and likely illegal - mass surveillance programs in the United States, United Kingdom and other countries. Impact Team: Hacked into pro-infidelity dating service Ashley Madison, then leaked details of more than 30 million customers, including evidence that now-former CEO Noel Biderman had multiple extramarital affairs, despite claims to the contrary (see Top 10 Data Breach Influencers). PhineasFisher: A person or group operating under that name hacked the Italian surveillance software maker Hacking Team, and dumped 400 GB of corporate data. Those records show that the company sold its surveillance software to dozens of governments, including the United States and Spain, as well as Russia, Bahrain and Sudan. PhineasFisher had previously claimed credit for hacking and leaking data from former FinFisher surveillance software vendor Gamma Group.Who would ever have predicted someone might try to steal and leak those organizations' information?
The same goes, of course, for Mossack Fonseca, since it helps individuals create shell companies. And there are good and legal uses for shell companies. But according to a review of the records over the past year spearheaded by the International Consortium of Investigative Journalists, the firm helped sell "financial secrecy to politicians, fraudsters and drug traffickers as well as billionaires, celebrities and sports stars."
With scandals in Russia, China, UK, Iceland, Ukraine, and more, perhaps a new rule: if you're in charge of a country, keep your money in it.
Setting aside allegations of enabling illegal activities, one of the Mossack Fonseca's primary errors - yes, besides getting caught out - was failing to safeguard its stored information. Because there seems to be no other, more charitable explanation for how an attacker - potentially an insider, although his or her identity remains unknown - managed to leak 2.6 terabytes of data to journalists over the course of more than a year.
Cue a rare case of wealth and accountability colliding.
Of course, not all of the world's shell companies have been created by Mossack Fonseca. And it's a sure bet that more have been - or will be - targeted by people who wish to expose the activities of these firms, as well as their customers, to say nothing of any other high-profile organization engaged in illegal or distasteful activities.
The revolution may not be televised. But it will be leaked.
More Articles …
Page 3409 of 3546

 Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities." Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
How to implement remote ID verification;
How to provide better patient and provider electronic authentication;
How to get simplified workflow inside healthcare facilities;
How to secure end-to-end communications between patients and providers;
How superior identity management naturally leads to improved HIPAA and HITECH compliance.
You might also be interested in …
Healthcare is in the middle of a major evolution toward digital, personalized medicine and the empowered patient. Ongoing regulatory and monetary incentive programs are driving healthcare providers to increase their EHR and E-Prescribing adoption. Additionally, the U.S. Office of the National Coordinator for Health Information Technology (ONC) is focused on strengthening identity-proofing and authentication of all participants in the healthcare system: providers, staff, business associates, and patients. With many organizations including HIMSS, AHIMA and CHIME calling for a nationwide unique patient identifier with support from the National Strategy for Trusted Identities in Cyberspace's (NSTIC), Identity Ecosystem Steering Group, a trusted digital identity will likely soon be on your IT agenda.
This massive push toward digital medicine brings about numerous security and interoperability challenges, including a shift in thinking from "supposedly known users" to "secure and trusted identities." Knowing who is accessing PHI at any point in time is beyond critical to ensure security. How can the healthcare community move closer to making this leap to digital medicine without sacrificing security and confidentiality?
This exclusive webinar, sponsored by VASCO, will talk about ways your healthcare organization can create a secure bridge between the verified identity in the physical world and the online identity in the cyberspace on a state or national level. Co-hosts Michael Magrath, Director of Business Development at VASCO and a nationally recognized leader in the healthcare identity management field, and Andrew Showstead, Director of Technical Consultancy at VASCO, will discuss how your organization can deploy a unique, reusable and trusted digital patient credential that provides interoperability and links multiple players via a trust framework.
In this exclusive webinar, Magrath and Showstead will also discuss:
How to implement remote ID verification;
How to provide better patient and provider electronic authentication;
How to get simplified workflow inside healthcare facilities;
How to secure end-to-end communications between patients and providers;
How superior identity management naturally leads to improved HIPAA and HITECH compliance.
You might also be interested in …







