- Details
- Category: Security News
A roundup of the just-concluded ISMG Fraud and Breach Prevention in Toronto leads the latest edition of the ISMG Security Report.
In this episode, you'll hear:
Summit speakers, including BankInfoSecurity Executive Editor Tracy Kitten, discuss how the complexity of data and lack of transparency facilitates cyber risk, the need to combine fraud and IT security investigations and the challenge of getting IT and IT security technologists and corporate executives and board members to speak the same language; ISMG's Jeremy Kirk report on how the chief information security officer of a major publisher gets his security message across to its top executives and board members; ISMG's Varun Haran analyze the challenges CISOs face during their first 100 days on the job; and About DataBreachToday Executive Editor Mat Schwartz's blog that addresses how one U.S. federal government agency issues a security warning that apparently was caused by the actions of another government agency.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our Sept. 9 and Sept. 13 reports, which respectively analyze Republican candidate Donald Trump's understanding of cybersecurity and U.S. Sen. Elizabeth Warren's push to get Congress to investigate Wells Fargo for violating the privacy of bank. The next ISMG Security Report will be Tuesday, Sept. 20.
Theme music for the ISMG Security Report is by Ithaca Audio under the Creative Commons license.
- Details
- Category: Security News
Security spending has seen a steady rise in the Indian and Southeast Asian markets for the past several years with the increase in technology adoption and the cloud-first strategy being adopted by organizations. The rate of growth seems to be peaking this year as a result of a number of breach incidents and increased awareness, and spending growth should continue for the next five years, says Singapore-based Siddharth Deshpande, principal analyst at Gartner.
Organizations in the region are steadily shifting to a security strategy that's focused more on detection and response, he confirms (see: Gartner: Asia Security Spending Rising).
"Organizations have understood that the focus needs to be on measuring security in the terms of detection and response, and how good their organization is in that respect is the way forward," Deshpande says. "Gartner is now recommending to companies that they shift their security spending to have at least 60 percent of their security budget to be spent on detection and response, up from 10- to-15 percent today."
Many organizations are also looking at orchestration and automation of low-level functions so that they can focus on some of the more advanced capabilities in house, he adds. Meanwhile, regulators are moving away from prescriptive mandates and enforcements to more risk-based regulations and guidelines, he says.
The vendor landscape is also evolving as many new players enter the market, he notes. For instance, many cloud providers have started providing customer-facing security solutions, competing directly with the existing technology and service-provider segments. This changing landscape is also raising questions around the challenge of managing a heterogeneous environment of different types of technologies and vendors, he says.
The attacker landscape is changing as well. Until recently, highly skilled attackers or amateurs prevailed. But the commoditization of hacking has enabled a mid-market segment of attackers who are able to use commercially available technologies to opportunistically compromise organizations that have poor security practices. The current ransomware problem is a case in point, he says (see: Insights from Gartner India Security Summit 2016).
In this interview with Information Security Media Group (see player link below image), Deshpande highlights some of the key trends in the Asian security landscape in the last year and shares his insights on the implications. He discusses:
The overall developments in the security landscape in 2016; The impact of the newer generation of security vendors and technologies; How the shift from prevention to detection and response is progressing in the region.At Gartner, Deshpande advises technology providers and buyers on security-related topics. He also conducts research and is a frequent speaker at Gartner events and client events and workshops. His primary areas of focus are security market opportunity and growth projections, managed security services, cloud access security brokers, security sales and go-to-market strategies. Secondary areas of focus include SIEM, CIO strategic priorities, distributed denial-of-service attack mitigation and digital risk management.
- Details
- Category: Security News
Breach Notification , Breach Response , Data Breach
The Breach That Supposedly Isn't a Breach California Company's Bungled Response Risks the 'Streisand Effect'
Most companies don't ever want to be contacted by Troy Hunt, the Australian data breach researcher who created Have I Been Pwned, a popular service for figuring out if your data has been leaked. Hunt, an amiable guy, often brings bad news.
See Also: API vs. Proxy: Understanding How to Get the Best Protection from Your CASB
He works closely with some journalists, including me, to navigate the choppy waters that can come with notifying companies. It's not an easy game: You don't want to publish a story that wrongly identifies a company as being a victim of a breach. But at the same time, people should be notified as soon as possible if their data has gone walkabout.
The handling of a recent data breach - the details of which are still unfolding - by Oakland, Calif.-based web services company Regpack provides a look into how the discovery and disclosure of a breach can turn into a real train wreck.
Tweet Leak
In mid-July, Hunt came across a now-deleted tweet from a known trader of leaked data with a link to a 1.6GB file. The file contained more than 100,000 names, email and postal addresses, last four digits of payment card numbers, three-digit card verification values, expiration dates and amounts paid for services. The tweet claimed the data came from BlueSnap, a payment services provider founded in Israel.
But Hunt says a close analysis of the data showed that Regpack might be responsible. Regpack develops web-based registration forms that can be integrated into websites. The forms also accommodate credit card data, which Regpack passes on to BlueSnap for payment processing. It initially looked like BlueSnap was breached. But information in the leaked files, as well as full invoices available online, showed strong indications Regpack may be the source, according to Hunt.
In late August, I queried both companies, and neither said they were breached. Meanwhile, Hunt had reached out to verified subscribers of Have I Been Pwned whose email addresses appeared in the leaked file. Verified subscribers are those who have confirmed their email addresses and are good sources that Hunt uses to try to confirm the veracity of a breach. It's a sensitive query, but many people confirmed their details to Hunt, including CVV2s and elements of the last four digits of their payment cards. Clearly, this was a breach.
But the situation then stalled. I was reluctant to write a story without firm confirmation from either company, but Hunt was concerned that the victims were never going to be contacted. Hunt decided to go public on Sept. 13 with his research on his blog. The tree had been shaken and information trickled out. But rather than clarity, Regpack is making the situation more confusing, and it's not clear when the more than 100,000 victims may be notified.
Exposed, Not Compromised
Regpack has stopped answering my queries, but in a statement supplied to Hunt, the company acknowledges it was the source of the leaked information. Its explanation, though, is lacking - the company says the leak was the result of a developer's error.
Log files revealed that a Regpack employee had decrypted some of its payments data for analysis, a practice that likely clashes with PCI-DSS compliance, the hefty set of security requirements merchants are supposed to follow. The company maintains its servers are secure.
"We identified that a human error caused those decrypted files to be exposed to a public-facing server, and this was the source of the data loss," the statement says.
It also contends there wasn't a breach: "Neither Regpack nor BlueSnap had our systems breached." The phrasing is confusing, and what Regpack probably meant to say is that its systems were not subject to a cyberattack. Even if the cause was an internal error, it's still a breach.
"I think they're doing a lot of damage and missing language that could both inform people properly and mitigate damage to their organization," Hunt says. Regpack is essentially risking the "Streisand effect," the term for trying to obfuscate or hide an issue, inadvertently making it more prominent, he says. (The Streisand effect is named after singer Barbra Streisand, who in 2003 attempted to suppress photographs of her private residence, but only succeeded in attracting additional attention to the matter.)
Regpack has started notifying its customers, and I obtained one of the emails the company is sending out. Similar to its public statement, Regpack says it wasn't breached, arguing that a breach "is a situation where someone gains access to our servers and databases and steals information."
Hmmm. Isn't that what happened? The notification then tries even harder to advance Regpack's argument.
"A good analogy would be that the office containing your data is totally safe and impenetrable and is guarded 24/7 by multiple systems and security guards," writes Edgar Carrasco, vice president of business development. "Unfortunately, while leaving work, someone dropped a file out of their bag and someone passing by took it. Hence, the office (our servers), were not compromised but information was exposed."
Carrasco's notice also contains a suggested email that Regpack customers should send to their customers whose personal data was exposed. Notably, it neglects to spell out all the data elements that were exposed.
"They're still missing really vital elements of the incident in their communication," Hunt says.
One Victim's Tale
One of the victims whose data was exposed is Thomas Bacon, an Austin, Texas-based web designer and developer. He used a Regpack-powered website to register his son for summer camp. Bacon contacted the summer camp to let them know of the breach. He claims that the camp wasn't happy because Regpack initially downplayed the impact of the leak. The camp, however, has now received the email notice from Carrasco.
Bacon, who has an interest in computer security, has already taken action. "I've cancelled my card," he says in a phone interview.
Although the leak doesn't contain full card numbers, Hunt argues that the last four digits are still critical information that could be used by attackers. Companies often ask consumers for the last four digits of their card as part of oral authentication questions over the phone. Another problem is that Regpack should not have been storing the CVV2 numbers, a practice prohibited by PCI-DSS.
"That may get them in a lot of trouble," Hunt says.
Notification could be messy. Regpack will have to let its website customers know which of their clients are affected by the breach, meaning it will have to carefully parse 1.6GB of data to make sure no one is left out. At least 899 services that used Regpack are affected by the breach, Hunt contends.
"The sites that use Regpack really haven't done anything wrong," Hunt says. "Regpack has clearly done multiple things wrong. When you're dealing with payments, the trust in the brand is really paramount. This is inevitably why they're being really cautious in their communications. They don't want to erode trust."
But it may already be gone.
The Regpack data has been in Have I Been Pwned since Sept. 13, so it's easy to figure out if you're affected. If so, it's probably wise to cancel your card.
- Details
- Category: Security News
Cybersecurity , Network & Perimeter , Technology
While NSA Hacks, US-CERT Frets "Sophisticated Hackers and Advanced Threat Actors" Target Networking Gear Photo: Jon 'ShakataGaNai' Davis (Creative Commons)
Photo: Jon 'ShakataGaNai' Davis (Creative Commons)In the wake of the leak of firewall attack tools from the Equation Group, by a group calling itself the Shadow Brokers, the U.S. Computer Emergency Readiness Team has issued a warning to all organizations, telling them that they must do more to lock down their networking equipment.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
"For several years now, vulnerable network devices have been the attack-vector of choice and one of the most effective techniques for sophisticated hackers and advanced threat actors," it reads.
But many security experts have tied the Equation Group exploits to the National Security Agency's in-house hacking squad.
Security expert Bruce Schneier, CTO of IBM's Resilient, says in a blog post that the leaked attack tools show that "the agency is hoarding information about security vulnerabilities in the products you use, because it wants to use it to hack others' computers." He adds that "those vulnerabilities aren't being reported, and aren't getting fixed, making your computers and networks unsafe."
In other words, the "sophisticated attacker" alert from US-CERT, which is part of the Department of Homeland Security, was triggered by attack capabilities that apparently trace to the same government's signals intelligence agency, some of which include custom-built exploits for networking equipment developed and sold by U.S. manufacturers.
Does this feel like a family affair, or what?
We'll Always Have Puns
The Shadow Brokers dump includes Equation Group attacks sporting names such as PIXPOCKET, which exploits vulnerabilities in Cisco PIX devices, and which Cisco stopped supporting a few years ago. Other attacks include EGREGIOUSBLUNDER, targeting Fortinet devices; ESCALATEPLOWMAN, targeting WatchGuard devices; and ELIGIBLEBOMBSHELL, targeting Topsec devices.
Meanwhile, an attack called EXTRABACON can be used to hack into any Cisco ASA device unless it's been recently patched using Cisco's related updates.
Exploits Leaked by Shadow Brokers
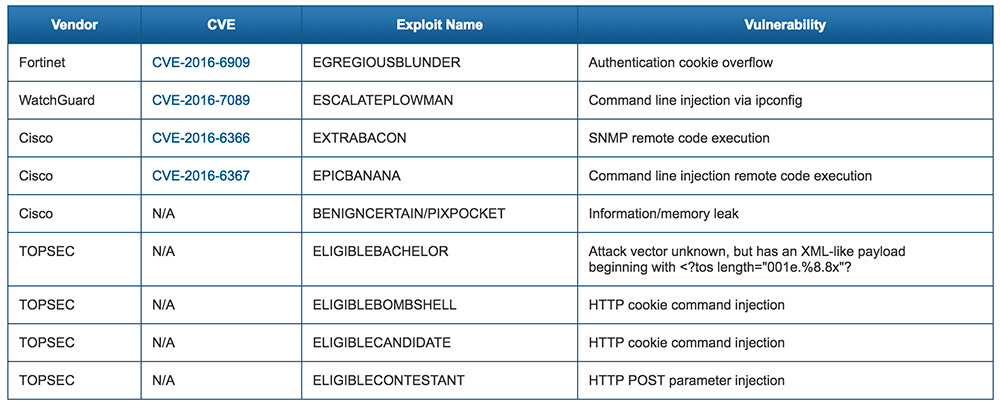 Source: US-CERT6 Network Admin Essentials
Source: US-CERT6 Network Admin Essentials
Whatever the identity of the Equation Group, security experts have long told me that any nation-state that can muster a hacking team will do so. China, France, Israel, Russia and the United Kingdom often feature on hacking experts' lists of "the best of the best."
Thus US-CERT's recommendations, while released in the shadow of the Equation Group tool dump, count as a "must do" for any organization that manages its own networking equipment.
Here's a brief overview:
Segregate networks and functions: Network segregation can "contain malicious occurrences" and block attackers from gaining access to other parts of the network. Limit unnecessary lateral communications: Restricting and filtering communications, including using vLANs with access control lists, helps battle backdoors. Harden network devices: Use secure configurations, restrict physical access to devices, employ strong passwords and encryption, disable all unnecessary services and never allow unencrypted remote access to admin protocols, for starters. Secure access to infrastructure devices: Use multifactor authentication, maintain privileged access controls and keep admin credentials locked down. Perform out-of-band management: Separate user traffic from network management traffic, locking down all admin-level access to devices. Validate integrity of hardware and software: Know your supply chain, validate all equipment and firmware and keep a close eye on network configurations for unauthorized changes.Still Falling For SYNful Knock
What US-CERT is recommending, however, is what organizations should already have been doing. But it's clear that many haven't been paying sufficient attention to the security of their networking equipment.
In the same alert, for example, US-CERT calls out an attack known as SYNful Knock - so named by U.S. cybersecurity firm FireEye - that came to light in September 2015, which can be used to change a router's operating system to give attackers persistent access to the device. "The initial infection vector does not leverage a zero-day vulnerability," US-CERT says. "Attackers either use the default credentials to log into the device or obtain weak credentials from other insecure devices or communications."
Who needs potentially sophisticated, NSA-built exploits to hack, if network administrators have rolled out equipment with default passwords or otherwise failed to secure other parts of the network?
- Details
- Category: Security News
Anti-Fraud , Fraud , Risk Management
'Daily Validation Reports' Will Provide Out-of-Band View of Messages
To help financial institutions better spot attempted fraud, the SWIFT interbank messaging network plans to begin offering voluntary "daily validation reports" to customers in December.
See Also: How to Mitigate Credential Theft by Securing Active Directory
The move is designed to provide an "out of band" view of an institution's messages to help anti-fraud teams better spot unauthorized attempts to move money via SWIFT, the organization says in a statement.
"A key step in the modus operandi in recent wire fraud cases at customer firms involves the attackers concealing their fraudulent messaging activity on customers' local systems," says Stephen Gilderdale, who heads SWIFT's customer security program, in a statement. "Daily validation reports will provide a reliable and independent source of information, providing such institutions with an activity lens to help them quickly detect fraud - whether perpetrated by external attackers or by malicious insiders."
Formally known as the Society for Worldwide Interbank Financial Telecommunication, SWIFT is a member-owned, Brussels-based collective. About 11,000 institutions in more than 200 countries use SWIFT's interbank messaging software and network.
The pending anti-fraud feature follows the February theft of $81 million from the central bank of Bangladesh's account at the Federal Reserve Bank of New York via fraudulent SWIFT messages. As part of the Bangladesh theft, attackers employed malware that prevented details of the transactions from being printed out on the bank's printer, thus delaying the bank's discovery of the fraud.
Research conducted by British defense and security firm BAE Systems found that as part of the attack, hackers gained access to a Bangladesh Bank PC that connected to the SWIFT network. BAE Systems security researchers Sergei Shevchenko and Adrian Nish reported that attackers then injected fraudulent money-moving messages into the SWIFT network and replaced the bank's PDF reader with a Trojanized version that removed traces of the fraudulent messages.
SWIFT has warned customers that the Bangladesh Bank hack was part of a wider attack campaign that has targeted multiple banks, including Vietnam's Tien Phong Bank in late 2015. Some security researchers say that the malware used in the attacks ties to the attack code used against Sony Pictures Entertainment in 2014, and that the attack campaign appears to have been carried out at the behest of North Korea.
Following the Bangladesh Bank hack, and facing criticism that SWIFT should be doing more to help customers stay secure, SWIFT CEO Gottfried Leibbrandt in May announced the launch of a new customer security program. In July, SWIFT also announced that it had assembled an internal intelligence team and tapped BAE Systems and cybersecurity firm Fox-IT to serve as a digital forensics investigation team for assisting any customers whose systems get hacked. SWIFT has not publicly disclosed pricing for that service.
Daily Out-of-Band Validation
SWIFT says the new daily validation reports are part of a new "transaction pattern detection stream" launched as part of the customer security program. The reports, it says, will comprise two parts:
Activity reports: Financial institutions can see "aggregate daily activity across currencies, countries and counterparties" and review it for unusual patterns. Risk Reports: These will flag "large or unusual payment flows and new combinations of payment parties" to help anti-fraud teams more quickly identify "unusual senders, destinations and patterns."Smaller financial firms should especially benefit from the new reports, SWIFT says. "Smaller institutions, in particular, are currently dependent on the accuracy of the data on their own systems, but in the event of a security breach, their locally stored payment and reconciliation data may be altered or unavailable," Gilderdale says.
Of course, savvy attackers could also target the PCs receiving these daily validation reports in an attempt to suppress them.
Voluntary Program
Signing up for the daily validation reports will be voluntary, and SWIFT has yet to finalize pricing, spokeswoman Natasha de Teran tells The Wall Street Journal. "Our focus is to improve security, not to derive profit," she said.
The introduction of the reports is good news for banks and shows SWIFT reacting to the Bangladesh Bank hack. It follows SWIFT launching an awareness campaign relating to its relationship management application, which it describes as a filter that customers can use "to select and limit the correspondents from whom they wish to receive messages, as well as to restrict the type of messages that they receive." SWIFT portrays it as a first line of defense against fraudulent messages.
But if previous cybercrime campaigns are any measure, then attackers will have also been continuing to refine their efforts - and with a head start.
Independent financial fraud consultant William Murray - who says that banks, not SWIFT, are responsible for ensuring the authenticity of SWIFT messages they send or receive - warns that whoever hacked Bangladesh Bank likely remains active. "The more we learn, the more resourceful these attacks appear to be," Murray said. "[Attackers] are now well funded and we must expect them to be active until we hear of arrests."
More Articles …
Page 3500 of 3546
