- Details
- Category: Security News
Cybersecurity , Data Breach , Risk Management
U.S. Election Meddling May Just Be Russian Payback How Can - or Should - the U.S. Respond?
The hacking and intrusions directed against U.S. political parties and government election authorities has caused deep concern in the U.S. The Washington Post reported on Sept. 5 that the U.S. intelligence and law enforcement agencies are investigating whether the intrusions are part of a broad covert campaign by Russia intended to undermine the U.S. elections in November.
See Also: A Smarter Approach to Third-Party Vendor Risk: A Case Study
The case against Russia is far from complete. While several private computer security firms have said the attacks against the Democratic Party organizations and Hillary Clinton's campaign have forensic clues that link to actors believed to be Russian, it's still a fuzzy picture. Other experts have cautioned that stronger evidence is needed (see Did Russia - or Russian-Built Malware - Hack the DNC?).
"If you know the pattern and digital footprint of an adversary, you can easily mimic the traits that they possess, so spoofing a breach to make it look like it's somebody else is extremely simple if you have a profile on the actor," says James Scott, a senior fellow at the Institute for Critical Infrastructure Technology.
The U.S. has confidently attributed cyber activity before, although with limited technical evidence. In mid-2014, the U.S. Department of Justice filed an indictment against five Chinese Army members, accusing them of stealing intellectual property from U.S. companies. Later that year, it also quickly blamed North Korea for the devastating attacks against Sony Pictures Entertainment that stole gigabytes of internal data and wrecked computers (see FBI Defends Sony Hack Attribution).
If Russia's alleged interference is a demonstration of power, it wouldn't be beyond its capabilities to do much worse than just reveal embarrassing Democratic Party emails. Scott recently co-authored a paper, Hacking Elections is Easy!, which contends that voting and e-voting machines have so many technical problems that it wouldn't take a large, orchestrated attack to affect an election outcome. In fact, targeting voting machines in just one county in a crucial swing state could be enough to tip a U.S. presidential election.
Angry Bear
Tensions between the U.S. and Russia have steadily increased since 2008, with Russia growing more irritated with what it believes is U.S. interference with its domestic affairs, says Greg Austin, professor in the Australian Centre for Cyber Security at the University of New South Wales in Canberra.
"There is definitely a war of sorts going on between the United States and Russia," Austin says. "We have reached a new level of low-intensity political skirmishes."
Among the historical bad feelings: The U.S. advocated for the inclusion of Ukraine in NATO in 2008, in part, by sending military and political leaders there for support. Russia pushed against it, and Ukraine later decided against joining. Then in 2014, Russia annexed Crimea, asserting its dominance over a former region of the Soviet Union.
The U.S. also has directly accused Russian President Vladimir Putin of amassing an ill-gotten fortune. In a January interview with the BBC, Adam Szubin, the U.S. Treasury's acting under secretary for terrorism and financial intelligence, said Putin's annual salary as president - around $110,000 - is not an accurate reflection of the his wealth. When asked if Putin was corrupt, Szubin said "In our view, yes."
Austin says that if Russia is behind the cyberattacks, the intrusions might be best classified as payback for a string of U.S. actions and policies that have caused offense.
U.S. Response
Nations have only started to tackle in the last decade the question of how to respond to cyberattacks. In 2008, the NATO Cooperative Cyber Defense Center of Excellence was set up in Tallinn, Estonia, to research, in part, how cyberattacks and cyber provocations should be handled under existing treaties dealing with warfare.
The U.S. is refining its cyberattack response tools. Soon after North Korea was pinned to the Sony attacks, President Barack Obama signed an executive order with a new round of sanctions against the nation (see Obama Imposes Sanctions on North Korea for Hack).
With the recent election-related hacks, it's difficult to tell what the motivation is. But influencing elections is something countries regularly attempt to do, notes Martin Libicki, an adjunct management scientist at the RAND Corporation. For example, Obama visited the U.K. earlier this year just ahead of the referendum to advocate that the nation stay in the European Union.
Tampering with elections is far more serious but more difficult to detect beforehand, Libicki says. But the line between tampering and influencing may be blurred in the cyber arena, making it difficult to establish a mutually respected boundary.
"You want our activities in the acceptable pot and what we would like to see banned in the unacceptable pot," Libicki says. "Ultimately, this starts to argue for restrictions on what countries can do with the information that they get from cyber-espionage (e.g. no doxing)."
- Details
- Category: Security News
 Brazzersforums remained offline in the wake of the breach report.
Brazzersforums remained offline in the wake of the breach report.Yet another historical mega-breach has come to light, this time involving Montreal-based online porn site Brazzers, which reportedly suffered a 2012 data breach that allowed an attacker to steal nearly 800,000 user credentials.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
The breach is an operational security reminder to users to employ not just unique passwords for every site they use - so that attackers can't steal them from one site and use them at another - but to also consider employing unique usernames and email addresses, not least to safeguard the privacy of their online activities.
Brazzers, which describes itself as "the world's best pornsite," films and distributes its own adult videos.
The breached data, which came to light this week, includes about 790,000 unique email addresses as well as usernames and plaintext passwords, reports technology site Motherboard. The site said it obtained a copy of the stolen data from breach-information site Vigilante.pw and verified it with the help of Australian security researcher Troy Hunt, who runs the free Have I Been Pwned? breach-notification site.
According to the Vigilante.pw site, the data was originally dumped online in April 2013.
Brazzers has confirmed the breach and said it relates to how the company transferred passwords between its website and forum software.
"This matches an incident which occurred in 2012 with our 'Brazzersforum,' which was managed by a third party. The incident occurred because of a vulnerability in the said third-party software, the 'vBulletin' software, and not Brazzers itself," Matt Stevens, a spokesman for Brazzers, told Motherboard.
"That being said, users' accounts were shared between Brazzers and the 'Brazzersforum' which was created for user convenience," he said. "That resulted in a small portion of our user accounts being exposed, and we took corrective measures in the days following this incident to protect our users."
Exposed: Users' Fantasies
On Brazzersforum, users could discuss their favorite scenes from Brazzers films, as well as request new ones. Hunt says that's the real kicker with this breach, because it potentially exposed people's sexual fantasies.
Problem with a hack like that is it's a *forum*. Worse than just adult website creds, this is what people were talking / fantasising about.
That the breach involved the popular vBulletin software is also notable. In recent years, numerous sites have been breached after failing to keep their vBulletin updated. Hunt says that many sites choose to administer their own vBulletin forums, yet fail to install newly available patches in a timely manner, thus creating a "perfect storm of software with holes in it that people don't maintain" (see Epic Games Forums Breached Again).
Throwaway Credentials
For users, the Brazzers breach is a reminder to compartmentalize the personally identifying information that you share online, if you'd prefer that your related activities would never come to light publicly.
Vis-à-vis the Brazzers breach, there's no word on how many users reused their email addresses - not to mention passwords - on other sites. One user, "John," whose email was contained in the dumped data, and who was contacted by Motherboard, told the publication that security and the potential for his data to get stolen had been top of mind, so "I used throwaway login/pass for this very reason."
But if previous breaches are any indication, John was an outlier, and many users will have employed recognizable email addresses to register with the site. For example, the administrator of Vigilante.pw, who goes by "Keen," tells me that 1,446 ".mil" and 41 ".gov" email addresses are contained in the Brazzers data dump, as well as one ".uk.gov" email address, which are respectively official U.S. military, U.S. government and U.K. government email addresses. Brazzers didn't immediately respond to a request for comment about whether it was verifying users' email addresses when the site was breached.
Ashley Madison Lesson Redux
Last year's breach of infidelity-focused online dating site Ashley Madison also revealed that many users failed to think twice when it came to keeping their participation on the site a secret, for example, by employing single-use credit cards or at least some password security mojo. More than 100,000 of the site's users, for example, picked this easily guessable six-digit password: "123456" (see We're So Stupid About Passwords: Ashley Madison Edition).
At the same time, however, site participants were sharing more than just their contact information with the site. Impact Team, which was the group that claimed credit for breaching Ashley Madison and later dumping related data, reported that breached customer records included "profiles with all the customers' secret sexual fantasies and matching credit card transactions [and] real names and addresses," among other details.
- Details
- Category: Security News
After recent reports that Dropbox and Last.fm suffered historical mega-breaches that have only now come to light, now news of yet another such data breach arrives.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
Russian web portal Rambler - likened by some to being a Russian version of Yahoo - was reportedly hacked in February 2012, resulting in the theft of data relating to nearly 100 million users.
Moscow-based Rambler offers various online services, including email and search, and also sells online advertising. It's a subsidiary of Prof-Media Management, which is the largest diversified media holding company in Russia. Rambler disputes some aspects of LeakedSource's data breach report.
The allegedly four-year-old breach was flagged Sept. 6, when paid breach-notification service LeakedSource announced that it had obtained stolen information relating to 98.2 million Rambler users, including their email address - containing their username - as well as their password and ICQ chat number (see LeakedSource: 'Assume Every Website Has Been Hacked').
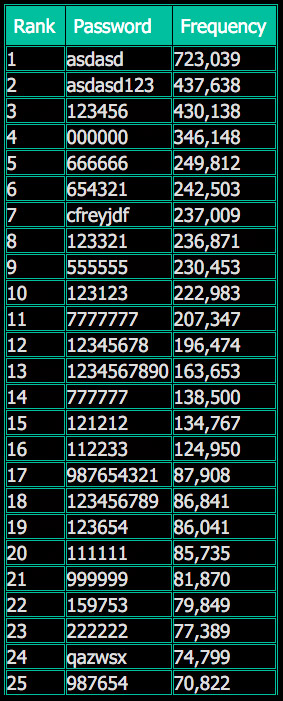 Top top 25 password choices of Rambler users. Source: LeakedSource
Top top 25 password choices of Rambler users. Source: LeakedSourceLeakedSource claims that the website was storing passwords without any encryption or hashing.
If true, that would constitute a very basic security failure, because it meant that anyone - insider or outsider - who was able to gain access to the password repository would have been able to immediately steal and use any user's credentials without having to first try and crack them.
Based on a list of top Rambler passwords published by LeakedSource, the site also appears to not have been requiring users to pick long and strong passwords (see We're So Stupid About Passwords: Ashley Madison Edition).
LeakedSource said that it verified three of the email addresses and passwords contained in the dump with the help of Russian journalist Maria Nefedova, who writes for Russian hacker magazine Xakep.ru. She reportedly reached out to the email address owners, provided the first half of their password, and asked them to supply the final four to six digits.
But Rambler disputes some aspects of LeakedSource's account. "We know about that database. It was leaked March 2014 and contained about 4 million accounts," Rambler spokeswoman Sofya Ivanova tells me. "Right after the accident we forced our users to change their passwords. Some passwords still might be matched because lots of them [are] as simple as 123456."
Ivanova adds: "Nowadays [a] situation like that [would be] impossible. We do not store passwords in plain text, all data is encrypted, we have added a mobile phone verification option and constantly remind our users about the necessity of changing passwords. We also have forbidden [them] to use the previously used passwords for the same account."
Can't Stop the Old Mega-Breaches
The Rambler breach alert follows LeakedSource on Sept. 1 announcing that it obtained user credentials that were stolen from music service Last.fm four years ago. LeakedSource claims that the service was hacked in March 2012 and that information on 43.6 million users - including usernames, email addresses and passwords - was stolen. LeakedSource said it had been able to crack 96 percent of the passwords contained in the dump, which were hashed using MD5.
LeakedSource says it obtained the Rambler data via "
The Last.fm breach warning followed reports on Aug. 27 that a mid-2012 Dropbox breach was much worse than originally believed (see Dropbox's Big, Bad, Belated Breach Notification).
Other historical mega-breaches that have only come to light this year have involved the likes of dating site Fling, hacked in 2011; has-been social network MySpace, hacked at an unknown time; microblogging site Tumblr, which was hacked in 2013; and LinkedIn, breached in 2012.
LinkedIn knew that it had been breached after 6.5 million LinkedIn users' password hashes appeared on a password-cracking forum in 2012. But the social network didn't force all users to reset their passwords. Fast-forward to May 2016, and it's apparent that LinkedIn failed to exercise proper caution, after a cache of 167 million accounts appeared for sale on a dark web forum.
LeakedSource said it was given copies of the dumped data from Rambler and LinkedIn for free.
This story has been updated to clarify that LeakedSource received the leaked LinkedIn and Rambler data for free.
- Details
- Category: Security News
Anti-Malware , Encryption , Risk Management
Numerous Cisco Devices Still Vulnerable to EXTRABACON Cisco Patched Equation Group Exploit, But Uptake Lags, Rapid7 Warns Cisco ASA 5540 Adaptive Security Appliance. Photo: Dave Habben (Flickr/CC)
Cisco ASA 5540 Adaptive Security Appliance. Photo: Dave Habben (Flickr/CC)Tens of thousands of Cisco Adaptive Security Appliances remain vulnerable to a powerful exploit that many security experts believe was created by the U.S. National Security Agency, according to scans conducted by security firm Rapid7 (see Cisco Patches ASA Devices Against EXTRABACON).
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
The zero-day exploit, called EXTRABACON, dates from 2013 and appears to have been developed by an organization called the Equation Group, which is widely believed to be associated with the NSA's Tailored Access Operations team (see NSA Pwned Cisco VPNs for 11 Years).
The exploit was released as part of an Aug. 13 attack-tool dump from a group calling itself the Shadow Brokers. The attack exploits a vulnerability in Cisco ASA firmware code that could allow a hacker to remotely gain full control of the device. Cisco ASA network security appliances provide anti-virus, firewall, intrusion prevention and virtual private network capabilities, and the flaw could be used to decrypt any traffic encrypted by the VPN.
Security experts say the vulnerability isn't easy to exploit, but does enable an attacker to bypass Cisco ASA device authentication, and thus could be attractive not just to intelligence agencies, but also cybercrime groups, including botnet builders.
Not all Cisco ASA devices can be exploited using the flaw. "The requirements for the ExtraBacon exploit are that you have SNMP read access to the firewall, as well as access to either telnet or SSH," according to security researcher XORcat, who confirmed that Cisco ASA devices running up to firmware 8.4(4) were at risk. Subsequently, however, Hungarian security firm SilentSignal said that it had been able to modify the exploit to work on any ASA device, including version 9.2(4).
We successfully ported EXTRABACON to ASA 9.2(4) #ShadowBrokers #Cisco pic.twitter.com/UPG6yq9Km2
Cisco says there are more than 1 million ASA devices deployed around the world.
Counting Vulnerable ASA Devices
Security researchers at Rapid7 decided to see how many unpatched Cisco ASA devices they could find. Rapid7's Derek Abdine and Bob Rudis say in a blog post that the company's in-house internet scanning project, dubbed Project Sonar, recently counted more than 50,000 Cisco ASA devices that were configured to act as SSL VPNs (see Scans Confirm: The Internet is a Dump).
But they wanted to know how many might be vulnerable to the vulnerabilities revealed by EXTRABACON, which generally require SNMP and telnet/SSH access to a vulnerable device to be enabled, before the exploit can be deployed.
Related efforts, however, were constrained in part by legal concerns. "Actually testing for SNMP and telnet/SSH access would have let us identify truly vulnerable systems," they say, but laws in the United States and elsewhere prohibit anyone from making "credentialed scan attempts" on devices they don't own. Instead, the researchers used hping to query device uptime. Specifically, the researchers counted how many machines had been rebooted since Cisco began releasing patched ASA firmware on Aug. 15, and since SilentSignal released its Aug. 25 blog post warning that they'd been able to update the Equation Group attack to exploit all current ASA devices.
Of the 50,000 Cisco ASA devices configured to be SSL VPNs that were identified by Rapid7, about 12,000 prevented them from capturing timestamps via hping. That left 38,476 systems, and of those, only 10,097 had been rebooted since Aug. 26, suggesting that they might have been patched.
In other words, the scans found at least 28,000 unpatched ASA devices.
Examples of presumed-vulnerable organizations include an unnamed large Japanese telecommunications provider with 55 devices, a large U.S. multinational technology company with 23 devices and a large U.S. healthcare provide with 20 devices.
"This bird's eye view of how organizations have reacted to the initial and updated EXTRABACON exploit releases shows that some appear to have assessed the issue as serious enough to react quickly while others have moved a bit more cautiously," the researchers say. "It's important to stress, once again, that attackers need to have far more than external SSL access to exploit these systems. However, also note that the vulnerability is very real and impacts a wide array of Cisco devices beyond these SSL VPNs."
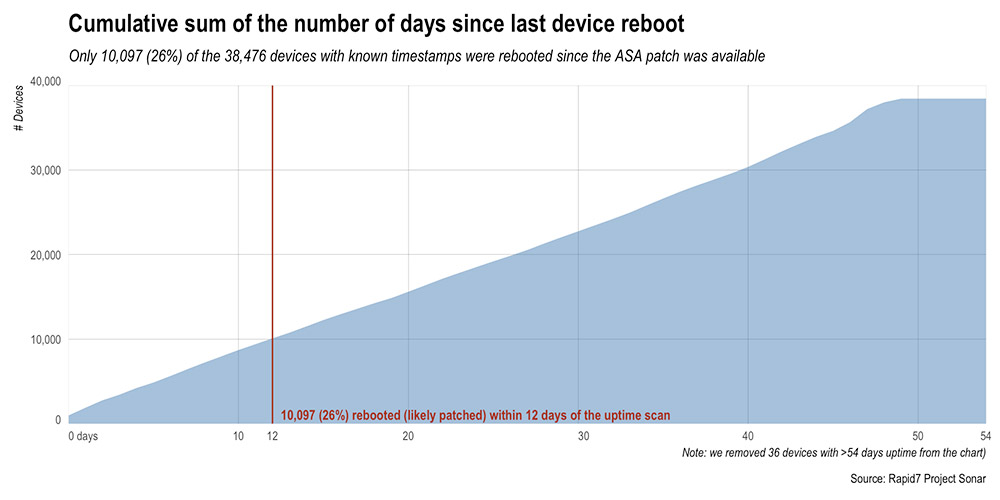 The number of detected Cisco ASA devices that have been rebooted - and thus theoretically patched - following EXTRABACON-related warnings. Source: Rapid7
The number of detected Cisco ASA devices that have been rebooted - and thus theoretically patched - following EXTRABACON-related warnings. Source: Rapid7
Patch Sooner, Not Later
The Rapid7 researchers say their study is a reminder to enterprise IT departments to ensure that they have an up-to-date inventory of deployed devices and firmware versions, that they patch Cisco ASA devices sooner than later, and until then ensure such devices aren't sitting ducks (see How to Cope With Intelligence Agency Exploits).
"EXTRABACON is a pretty critical vulnerability in a core network security infrastructure device and Cisco patches are generally quick and safe to deploy, so it would be prudent for most organizations to deploy the patch as soon as they can obtain and test it," the researchers say.
It's unlikely, however, that all vulnerable Cisco ASA devices will see patches get installed. Indeed, unpatched devices and operating systems never seem to die, instead just gradually fading away while never quite reaching extinction.
In June, for example, security researcher Billy Rios told me that more than 200,000 internet-connected systems remained vulnerable to the OpenSSL vulnerability known as Heartbleed. That was a decrease from an April 2014 high of 1.5 million vulnerable devices, which fell to 250,000 vulnerable devices in January 2015. But more than two years after Heartbleed was found, it remained far from extinct.
- Details
- Category: Security News
Two men allegedly tied to the hacking group "Crackas With Attitude" have been arrested as part of an investigation into hacks against U.S. government systems as well as senior government officials, including CIA Director John Brennan's personal AOL email account.
See Also: Disrupt Attack Campaigns with Network Traffic Security Analytics
Andrew Otto Boggs, a.k.a. "Incursio," 22, and Justin Gray Liverman, a.k.a. "D3f4ult," 24, were both arrested Sept. 8 in North Carolina as part of a joint operation involving the FBI and the U.S. Secret Service, according to the Justice Department.
The men have been charged with conspiring to violate numerous federal laws, including falsely impersonating an officer or employee of the United States, aggravated identity theft, computer-related fraud, providing false information or perpetuating hoaxes as well as making harassing telephone calls.
The FBI alleges that the Crackas with Attitude group included not just Boggs and Liverman, but also three individuals based in the United Kingdom - Cracka, 17; Derp, 17; and Cubed, 15 - who legally cannot be named because of their ages. They were arrested in January and February (see UK Police Arrest Suspect Over CIA Director's Email Hack).
Boggs and Liverman are due to first appear in federal court next week.
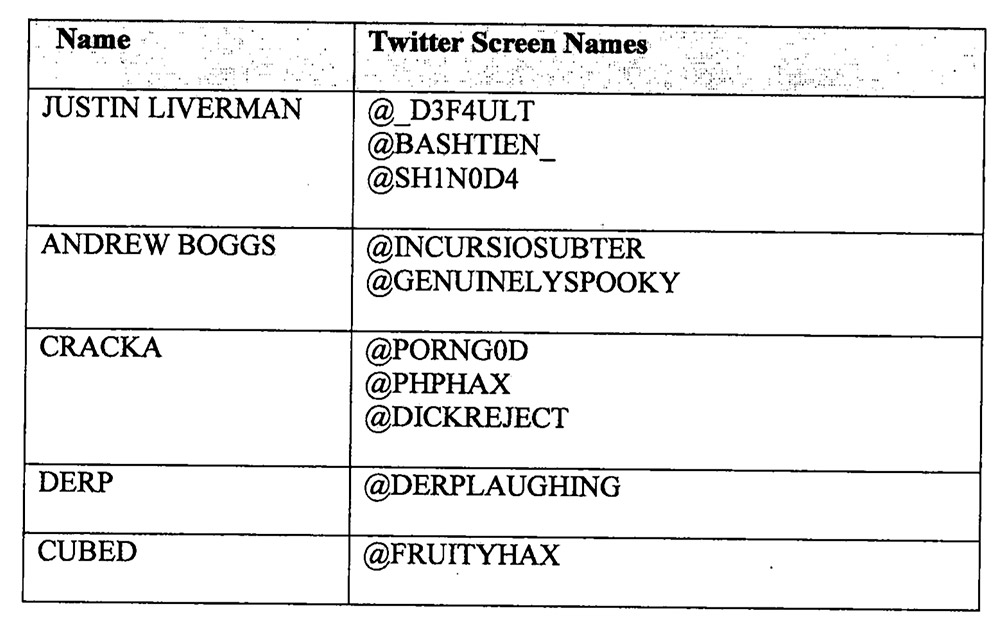 The FBI's affidavit details Crackas With Attitude suspects and Twitter handles.
The FBI's affidavit details Crackas With Attitude suspects and Twitter handles.
According to charging documents filed in federal court Sept. 2 and unsealed Sept. 8, Cracka - using the Twitter screen name @Porng0d - first began exchanging Twitter direct messages with the Twitter account @GenuinelySpooky, controlled by Boggs, around July 17, 2015. "In one of these DMs, Cracka related he had obtained the Social Security number of a senior U.S. government official and 'jacked [their] comcast email so I can listen to [their] voicemail, look at [their] answered calls and missed calls and control whats on [their] tv. Nvm, I don't regret it, [expletive] the gov'" (all sic), according to an FBI affidavit included with the charging documents.
Boggs allegedly asked Cracka later that day if he wanted "to join TeamInncuous," adding: "We'll only be hitting governments and security firms. I'm waiting on our logo to be finished before we commence attacks on governments :)." Cracka allegedly responded, "Sure, I'd love to join :P."
By way of motivation, Boggs later claimed that he'd been "looking for evidence of aliens since Gary," an apparent reference to Gary McKinnon, a Scottish man who allegedly hacked into computers operated by NASA in search of proof of extraterrestrial life, according to the affidavit.
Cracka responded that he was in, and that he had "just released emails of them admitting to torture."
Socially Engineering Victims
The affidavit reveals how the Crackas With Attitude group allegedly executed their attacks.
On Oct. 12, 2015, for example, "victim 1's spouse" - Kathy Brennan, wife of CIA Director John Brennan - received an email from Verizon saying that her online password had been changed, according to the complaint. "Records obtained from Verizon included October 11, 2015, voice recordings from multiple calls by Cracka who impersonated [both] a Verizon employee and Victim 1 [John Brennan] to gain unauthorized access to Victim 1's Verizon ISP account," according to the FBI's affidavit.
Shortly thereafter, Cracka claimed credit online for stealing the contents of Brennan's personal AOL email account - AOL is owned by Verizon - and routing them to WikiLeaks, which released them on Oct. 21, 2015. At the time, Cracka said the leaks were retaliation for U.S. foreign policy, and multiple posts to Cracka-controlled Twitter accounts voiced support for Palestine.
One of the alleged attackers - who demonstrated control of the Twitter account @phphax that sported the username "cracka" - told the New York Post that in Brennan's AOL account, he found a contact list containing 2,611 email and instant message addresses, including some for top U.S. national security and intelligence officials. He added that 40 emails had file attachments that also contained sensitive information, including Brennan's application for a top-secret security clearance.
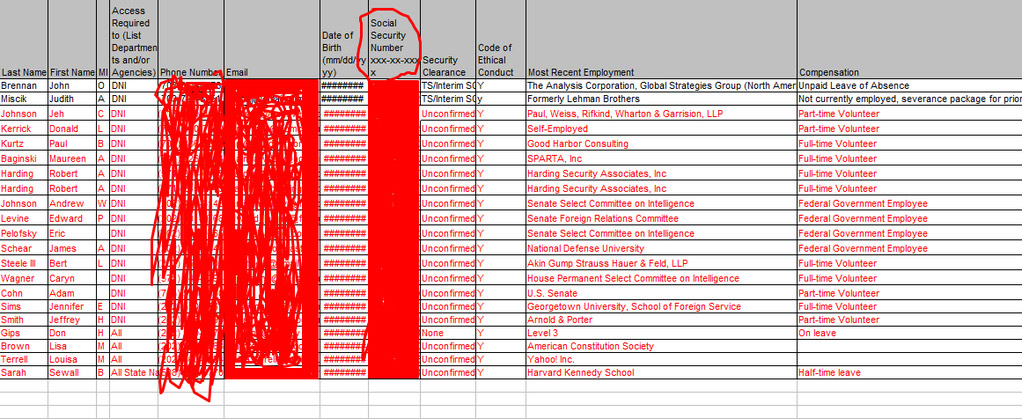
A spreadsheet of information compiled by "Cracka" and posted to Twitter, containing excerpts of the allegedly stolen data.
'Hello, I'm DHS Secretary Johnson'
Cracka also said he'd accessed the online Comcast account for Homeland Security Secretary Jeh Johnson, "victim 2" in the affidavit, listened to his voicemails and subsequently published what he said were personal details about Johnson and his family.
On Nov. 4, according to the affidavit, Cracka used Secretary Johnson's credentials to access the Law Enforcement Enterprise Portal - or LEEP - which the bureau describes as "a secure, internet-based information sharing system available to agencies around the world that are involved in law enforcement, first response, criminal justice, anti-terrorism, intelligence and related matters" (see Hackers Claim FBI Information-Sharing Portal Breached).
Cracka used the portal to also gain access to the Justice Department's Joint Automated Booking System and search for information relating to Jeremy Hammond, a U.S. hacker currently serving a 10-year sentence for hacking into global intelligence firm Stratfor, according to the affidavit. At the time, the hacker group tweeted screenshots of Hammond's alleged JABS records.
The group also allegedly stole and leaked personal information relating to Director of National Intelligence James Clapper, White House Deputy National Security Advisor Avril Haines, and others (see Dox Files: DHS Probes Information Dump).
Poor Opsec
According to the affidavit, Boggs and Liverman failed to practice good operational security. For example, it says members of the group began recommending - via unencrypted Twitter direct messages - the encrypted chat programs Cryptocat and Wickr to each other.
The FBI said it traced the IP address used to register the @GenuinelySpooky Twitter account, which was also used to access it repeatedly from Oct. 2, 2015, to Nov. 11, 2015, to a Charter Communications ISP account registered to Bogg's father, with whom he lived.
The affidavit also reveals that federal agents executed a search warrant against Liverman that found evidence of the group's activities on one of his hard drives, including instant messaging conversations - using the Jabber chat client - that included the transfer of stolen information obtained from victims, including ISP records; a list of more than 80 Miami-area police officers that were leaked via Twitter on Jan. 21; as well as Bandicam screen-recorder videos of Crackas With Attitude chat sessions. Investigators said they also found a list containing information about 20,000 FBI employees and 9,000 DHS employees on the hard drive, which had been leaked online by the hacker group.
More Articles …
Page 3495 of 3546
