Data Breach , Data Breach Prevention and Response Summit , Events
Case Study: When Government Oversight Goes Wrong- Details
- Category: Security News
Fraud , ID Theft , Insider Fraud
Bank Fined $185 Million Over Rampant Misuse of Customers' Identities Photo: Mike Mozart (Flickr/CC)
Photo: Mike Mozart (Flickr/CC)For years, some Wells Fargo employees subscribed the bank's customers to products they didn't request, and that practice has now triggered $185 million in fines.
See Also: Detecting Insider Threats Through Machine Learning
The second-largest U.S. bank was accused by state and federal regulators of allowing its employees to access customers' personal information - and in some cases forging data - to subscribe them to products, such as credit cards, that both generated revenue for the bank as well as commissions for salespeople. Prosecutors say an astounding 2 million ghost deposit and credit card accounts were opened without customers' knowledge, or through misrepresentation.
This institutionalized campaign of fraud at Wells Fargo may represent one of the largest incidents of organized identity theft ever recorded.
On Sept. 8, Wells Fargo accepted related penalties imposed by the federal Consumer Financial Protection Bureau, the Office of the Comptroller of the Currency and the Los Angeles city attorney. It will pay a $100 million fine to the CFPB - the largest fine the agency has ever levied; $35 million to the OCC; $50 million to Los Angeles and $5 million in remediation to customers.
Wells Fargo says in a statement: "We regret and take responsibility for any instances where customers may have received a product that they did not request." Separately, the bank says it undertook a review and refunded $2.6 million to customers - with each refund averaging $25 - "for any fees associated with products customers received that they may not have requested." The bank said less than 1 percent of accounts were affected.
The enforcement actions against Wells Fargo will likely now cause regulators to look more closely at how banks incentivize sales associates and what governance structures are in place to prevent abuse, says Christopher Pierson, CISO and general counsel at invoicing and payments provider Viewpost. Pierson also sits on the Department of Homeland Security's Data Privacy and Integrity Advisory Committee and Cybersecurity Subcommittee.
"Many financial institutions have had overzealous sales persons overreach their authority or the wishes of the customers and in some cases commit blatant deceptive acts," Pierson says.
Product Pushing
Wells Fargo's retail banking revenues depend in part on cross selling, or trying to get existing customers to take up other fee-generating products.
The bank boasted that its customers held, on average, six different Wells Fargo products, but as part of its "Gr-eight" initiative, pushed for salespeople to increase that average to eight, according to a civil complaint filed by Los Angeles' city attorney in May 2015. But the complaint alleges that the goal was unattainable without salespeople resorting to abusive and fraudulent tactics.
"Managers constantly hound, berate, demean and threaten employees to meet these unreachable quotas," the complaint reads. "Managers often tell employees to do whatever it takes to reach their quotas."
The pressure was allegedly intense, with each Wells Fargo branch having to tally sales for district managers at 11 a.m., 1 p.m., 3 p.m. and 5 p.m. The complaint describes how associates pumped up their sales in an attempt to remain in managers' good graces. The tactics they used mirror how cybercriminals execute identity theft schemes, including borrowing identity details and opening fraudulent accounts in consumers' names.
The practices were allegedly so common that Wells Fargo employees had taken to nicknaming some of the related tactics. One, known as "pinning," involved bank employees enrolling customers - without their knowledge - into online banking and bill-paying products. Employees generated ATM cards for the dummy accounts and assigned PIN numbers - usually "0000" - to the cards, essentially impersonating customers, according to the complaint. For each of these new, bogus enrollments, an associate would receive compensation.
But subscribing people to new products often required more customer information than salespeople may have been able to access. Because customers were in the dark, bank employees allegedly sometimes just entered made-up data into Wells Fargo's internal system. To bypass computer prompts asking for customer contact information, for example, bankers allegedly often filled in fake email addresses, such as "
In some cases, Wells Fargo employees actually withdrew money from authorized accounts - a practice euphemized as "simulated funding" - to pad unauthorized, fee-generating deposit accounts that customers did not know existed. The bank took in at least $2 million in overdraft and monthly service fees, according to the complaint.
Those who didn't have enough money to pay the sneaky fees saw their credit reports get dinged. In another extraordinary consequence of this fraud, prosecutors say that the clandestine actions by Wells Fargo employees drove customers to purchase identity theft protection from Wells Fargo, not realizing that it was their bank that was fraudulently misusing their identities.
Long-Running Practices
Wells Fargo allegedly violated a range of California regulations, including bans against the use of another person's data for illegal purposes and the accessing of personal information by unauthorized people.
Yet another one of the amazing aspects of this saga is that it seemed to persist for more than five years. The complaint notes that Wells Fargo had fired a handful of employees over the years for related offenses but adds that "those efforts have been, at most, cosmetic, and ultimately benefit Wells Fargo by providing them with plausible deniability."
Wells Fargo spokeswoman Mary Eshet says that 5,300 Wells Fargo employees have been fired due to practices described in the complaint. Those firings occurred between January 2011 through March 2016, suggesting that the bank failed early on to spot or squash these illegal practices.
Wells Fargo must now retain an independent consultant to review its sales practices, review training procedures and create a compliance plan, according to the consent order that the bank signed with the CFPB.
Executive Editor Tracy Kitten contributed to this report.
- Details
- Category: Security News
 Gregory Touhill, new federal CISO
Gregory Touhill, new federal CISOPresident Obama has named Gregory Touhill, a retired Air Force brigadier general, as the U.S. federal government's first chief information security officer.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
A Sept. 8 White House blog announced the appointment of Touhill, who now serves as deputy assistant secretary for cybersecurity and communications in the Department of Homeland Security. In his new role, Touhill will report to federal CIO Tony Scott, who's based in the White House Office of Management and Budget.
Grant Schneider, director for cybersecurity in the White House National Security Council, was named acting deputy CISO.
In February, Obama created the federal CISO post as part of a multifaceted initiative known as the Cybersecurity National Action Plan that's aimed at strengthening the nation's IT security (see Obama Creating Federal CISO Post ).
Scott and White House Cybersecurity Coordinator Michael Daniel, in the blog, say Touhill will leverage his considerable experience in managing a range of complex and diverse technical solutions with his strong knowledge of civilian and military best practices, capabilities and human capital training, development and retention strategies.
"Greg will lead a strong team within OMB who have been at the forefront of driving policy and implementation of leading cyber practices across federal agencies and is the team that conducts periodic CyberStat reviews with federal agencies to insure that implementation plans are effective and achieve the desired outcomes," Scott and Daniel write in the blog.
In CyberStat sessions, cybersecurity experts from OMB, the Department of Homeland Security and the national security staff help agency IT security leaders develop action plans to improve their information security posture.
Reaction to the Pick
Greg Garcia, who served as DHS assistant secretary for cybersecurity and communications in the George W. Bush administration, says Touhill is a strong pick for the job.
"As lead for the National Cyber and Communications Integration Center, he knows federal cybersecurity strengths and weaknesses in the context of both preparedness and incident response," Garcia says. "And he has been a participant and convener of numerous industry-government cyber exercises, where participants have gained a better sense of how a given cyberattack can impact critical operational processes, and how response protocols can be improved to mitigate damage."
Garcia characterizes Touhill as a common-sense manager. "Greg recognizes bureaucratic inefficiencies and isn't afraid to call them out," Garcia says. "He is both candid and personable with his stakeholders, which engenders trust."
Clock Ticking
Some cybersecurity and government policy experts wonder if Touhill will have enough time to accomplish anything significant in the final four months of the Obama administration (see Federal CISO Will Face Tough Challenges). The next president could choose a new federal CISO or do away with the job.
Martin Libicki, a national and cybersecurity scholar at the think tank The Rand Corp., says he was impressed with Touhill's knowledge in their one meeting, but questions how much he could do before inauguration day on Jan. 20. "The last few months are hardly time to get much done significantly - particularly if what he wants to get done is something that will run into opposition from someone else in the bureaucracy because snow-rolling someone at this stage is relatively simple at that point."
But Garcia notes: "Some flowers are planted to bloom in autumn; others are bulbs that wait until spring. Greg might be able to bridge the seasons by fertilizing agencies' alignment with the newly revised OMB Circular A-130 [which defines administration IT management policy]."
Among Touhill's past positions was a 2-year stint as CIO and director of C4 systems, the nation's military transportation combatant command. He also served for nearly 1½ years as CIO and director for communications and information for the air mobility command. He retired from the Air Force in 2005 after nearly 22 years of service.
- Details
- Category: Security News
Encryption , Risk Management , Technology
4.5 Million Embedded Systems Reuse Crypto Keys, SEC Consult Warns SEC Consult says embedded systems that reuse cryptographic keys include the ToughSwitch from Ubiquiti Networks
SEC Consult says embedded systems that reuse cryptographic keys include the ToughSwitch from Ubiquiti NetworksInternet of Things alert: Many embedded systems contain hardcoded cryptographic credentials that attackers can use to seize control of the devices or crack encrypted website traffic. And the problem is only getting worse.
See Also: Managing Identity, Security and Device Compliance in an IT World
So says SEC Consult, a Vienna-based application security services and information security consultancy, in a new report that analyzes internet-connected embedded systems, referring to any type of system that uses software that's been embedded into hardware. It warns that many of those Internet of Things systems - including "Internet gateways, routers, modems, IP cameras, VoIP phones" and more - use private HTTPS and Secure Shell (SSH) keys that are not secret.
The report, from Stefan Viehböck, a senior security consultant at SEC Consult, builds on research that he released in November 2015, which involved analyzing cryptographic keys - public keys, private keys and certificates - contained in the firmware used to run more than 4,000 embedded devices from more than 70 vendors. In particular, he reviewed SSH host keys, which allow remote access to an SSH server, as well as X.509 certificates, which are used to facilitate HTTPS connections that encrypt web traffic.
Last year, SEC Consult warned it found that 580 unique, private HTTPS keys were being reused by 9 percent of all HTTPS hosts on the web and 6 percent of all SSH hosts on the web. The consultancy began working with the U.S. Computer Emergency Response Team in August 2015 to notify 50 affected vendors and ISPs. It hoped to trigger firmware upgrades from affected vendors as well as a concerted push to update vulnerable devices. Many such devices are customer premises equipment, referring to gear that gets installed on-site by ISPs or systems integrators.
But whereas the firm found 3.2 million devices using known private HTTPS keys nine months ago, recent scans have revealed that there are now 4.5 million such devices - an increase of 40 percent.
Clearly, the problem is getting worse, at least where HTTPS private certificates are concerned. The researchers haven't yet been able to run a new SSH host key test yet, although say they hope to do so soon.
Hundreds of certificates, SSH host keys +matching private keys found in embedded firmware: https://t.co/PCBGxFEfO1 pic.twitter.com/7LGRyvxubn
To help organizations identify related vulnerabilities, develop countermeasures - and no doubt pressure culpable vendors and ISPs - SEC Consult has released all 580 static keys via the code-sharing site GitHub. "Releasing the private keys is not something we take lightly as it allows global adversaries to exploit this vulnerability class on a large scale," Viehböck says. "However, we think that any determined attacker can repeat our research and get the private keys from publicly available firmware with ease.
Key Reuse: What's the Risk?
Reusing private keys poses numerous risks. Attackers that obtain a private HTTPS key used by a system could launch man-in-the-middle attacks against the device, including decrypting HTTPS traffic. Attackers who obtain a private SSH key for a system, meanwhile, could potentially authenticate to a remote device - gaining encrypted, admin-level access - and take it over, as well as potentially use it as a launching pad for hacking into other devices on the network.
In 2015, security experts began warning that tens of thousands of devices that run on ARM processors, including devices built by Ubiquiti, were being exploited by variants of MrBlack - a.k.a. Spike - botnet-building malware.
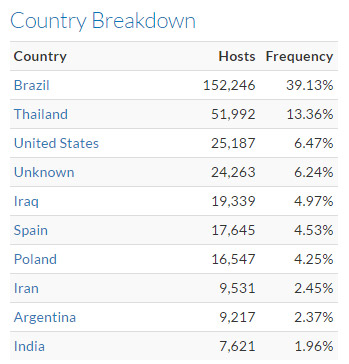 Ubiquity Networks devices that reuse crypto keys. Source: SEC Consult, using data from Censys.
Ubiquity Networks devices that reuse crypto keys. Source: SEC Consult, using data from Censys.In May, meanwhile, security firm Symantec released a report detailing how thousands of Ubiquiti AirOS routers running outdated firmware appeared to be getting hacked by malware that adds a backdoor to systems, giving attackers remote access.
"Any router that runs older versions of the firmware and has its HTTP/HTTPS interface exposed to the internet could be infected," Symantec said. "Ubiquiti released a patch for this vulnerability almost a year ago. However, as is often the case on these devices, many routers may still have old firmware installed."
Default credentials may also be to blame. "While investigating this threat, we identified attempts to log into our honeypot routers over Secure Shell (SSH) using the default Ubiquiti credentials (username: ubnt and password: ubnt)," Symantec says. "Data from our honeypots shows that these credentials are among the top five that attackers use to try and break into routers."
Pwn All the Things
Viehböck notes that numerous users of Ubiquiti Networks' equipment still appear to be struggling to eliminate malware from their devices (see Router Hacks: Who's Responsible?).
"Ubiquiti has even started to include functionality to remove malware in their firmware updates and released a standalone tool called 'CureMalware' that promises removal of the botnets Skynet, PimPamPum and ExploitIM," he says. "The tool comes with the helpful instructions," including the malware-imposed expletive-derived username and password that users must enter to regain control of their devices from the worm detailed by Symantec.
On the upside, Viehböck says, whereas he counted 1.1 million public-facing, internet-connected Ubiquiti devices in November 2015, that number has since dropped to 410,000. "The bad news is that the major drop is likely caused by various botnets that exploit weak credentials as well as critical vulnerabilities, including an innocently titled "arbitrary file upload" vulnerability [that enables] straightforward remote code execution." A related attack module is freely available as well via the free, open source penetration testing toolkit Metasploit. Viehböck surmises that ongoing attacks against the devices have led users to safeguard them with firewalls, which is why they're not showing up in his internet scans anymore.
"What a mess," Viehböck says, "and Ubiquiti still has remote management on the WAN port enabled by default."
Ubiquiti did not immediately reply to Information Security Media Group's request for comment.
SEC Consult says that Ubiquiti is not the only vendor or ISP at fault. It claims its research also discovered numerous vulnerable devices being shipped via other vendors and ISPs, including 500,000 devices from CenturyLink in the U.S; more than 1 million from Mexico's TELEMEX; 170,000 from Telefónica in Spain, 100,000 from China Telecom, 55,000 from Chile's VTR Globalcom, 45,000 from Chunghwa Telecom in Taiwan and more than 26,000 from Telstra in Australia.
How Vendors Must Respond
Viehböck says the solution to the key reuse problem is no secret. "Vendors should make sure that each device uses random, unique cryptographic keys," he says. "These can be computed in the factory or on first boot. In the case of [customer premises equipment] devices, both the ISP and the vendor have to work together to provide fixed firmware for affected devices."
One reason so many devices reuse keys is that many systems integrators and ISPs prefer devices that can be easily accessed remotely, both to initially configure the device as well as provide ongoing troubleshooting. But security experts have long warned that devices that ship with default configurations - including on-by-default remote access - too often get deployed with those defaults intact.
Viehböck recommends that if an ISP or systems integrator requires remote access to a device, it should not allow remote access to the device's wide-area-network port, but instead use a VLAN with "strict" access control lists.
For enterprise end users, whenever possible, "change the SSH host keys and X.509 certificates to device-specific ones," Viehböck says. For vulnerable devices where this isn't possible, or for "a regular home user" who will likely lack the required technical knowledge - and fortitude - to undertake the required steps, the only other recourse may be to throw away the device and buy a new one.
Many enterprises and home users, however, don't junk outdated - and thus potentially exploitable - devices. Last month, for example, security researchers counted at least 15,000 Cisco PIX devices still in use, despite Cisco ceasing support in 2013 and having recommended since 2008 that users upgrade to its Adaptive Security Appliance devices range. As a result, at least some of those devices appear to have been hacked by cybercrime gangs as well as intelligence agencies to access corporate networks (see NSA Pwned Cisco VPNs for 11 Years).
- Details
- Category: Security News
- Details
- Category: Security News
Data Breach , Data Breach Prevention and Response Summit , Events
Cryptocurrency Exchanges, Regulation and Ransomware: How Recent Breaches Will Impact the Future of BitcoinMore Articles …
Page 3496 of 3546

 After any significant breach, many parties - ranging from customers, clients, business partners and government agencies - will demand clarity about how a breach occurred and what data was stolen.
In the U.S., the Federal Trade Commission acts to ensure that any given organization is not negligent or reckless with consumers' private information. But upon what information does the FTC act? In Canada, the FTC's counterpart is the Competition Bureau; and, like the FTC, it is responsible for stopping deceptive marketing practices in Canada. What's more, the FTC and the Competition Bureau have an "agreement," to share information about breaches and companies that they feel are not adequately protecting consumer data.
Actions taken by the FTC will affect Canadian businesses.
This session will focus on a specific case where the FTC relied on highly suspect information obtained by, for all intents and purposes, a "faux" breach of a cancer-screening service, to launch an investigation that resulted in a protracted legal fight that ultimately led to the collapse of the allegedly breached organization, LabMD. Michael Daugherty, founder, president and CEO of LabMD and the author of the book "The Devil Inside the Beltway," will share his story of what to expect when the government launches an investigation. He'll then join in a discussion with Randy Sabett, vice chairman of the Privacy and Data Protection Practice Group at law firm Cooley LLP, about how laws in various international jurisdictions are impacting companies just like LabMD.
You might also be interested in …
After any significant breach, many parties - ranging from customers, clients, business partners and government agencies - will demand clarity about how a breach occurred and what data was stolen.
In the U.S., the Federal Trade Commission acts to ensure that any given organization is not negligent or reckless with consumers' private information. But upon what information does the FTC act? In Canada, the FTC's counterpart is the Competition Bureau; and, like the FTC, it is responsible for stopping deceptive marketing practices in Canada. What's more, the FTC and the Competition Bureau have an "agreement," to share information about breaches and companies that they feel are not adequately protecting consumer data.
Actions taken by the FTC will affect Canadian businesses.
This session will focus on a specific case where the FTC relied on highly suspect information obtained by, for all intents and purposes, a "faux" breach of a cancer-screening service, to launch an investigation that resulted in a protracted legal fight that ultimately led to the collapse of the allegedly breached organization, LabMD. Michael Daugherty, founder, president and CEO of LabMD and the author of the book "The Devil Inside the Beltway," will share his story of what to expect when the government launches an investigation. He'll then join in a discussion with Randy Sabett, vice chairman of the Privacy and Data Protection Practice Group at law firm Cooley LLP, about how laws in various international jurisdictions are impacting companies just like LabMD.
You might also be interested in …







 Although developed to support the infamous Bitcoin, the blockchain mechanism is proving to have a multitude of use-cases, from IoT micropayments to capital-market trading, retail banking and even voting.
The blockchain, in effect, is a distributed ledger, shared with hundreds of thousands of automated auditors that verify the authenticity of every transaction, drastically reducing, if not completely eliminating, fraudulent entries. But as recent events have proven, the proverbial weak link in the chain is not the blockchain, but, rather, the cryptocurrency exchanges that manage user accounts.
How will recent breaches of those exchanges impact the future of blockchain technology, from a legal and regulatory standpoint? And now that cybercriminals are increasingly requesting that their victims pay in cryptocurrency for ransomware attacks and other cyberschemes, will Bitcoin and other cryptocurrencies' reputations be damaged?
Many current transaction mechanisms are vulnerable to fraud. This session will walk through the potential impact of broader blockchain deployment, and the implications recent events are likely to have on blockchain's future.
Although developed to support the infamous Bitcoin, the blockchain mechanism is proving to have a multitude of use-cases, from IoT micropayments to capital-market trading, retail banking and even voting.
The blockchain, in effect, is a distributed ledger, shared with hundreds of thousands of automated auditors that verify the authenticity of every transaction, drastically reducing, if not completely eliminating, fraudulent entries. But as recent events have proven, the proverbial weak link in the chain is not the blockchain, but, rather, the cryptocurrency exchanges that manage user accounts.
How will recent breaches of those exchanges impact the future of blockchain technology, from a legal and regulatory standpoint? And now that cybercriminals are increasingly requesting that their victims pay in cryptocurrency for ransomware attacks and other cyberschemes, will Bitcoin and other cryptocurrencies' reputations be damaged?
Many current transaction mechanisms are vulnerable to fraud. This session will walk through the potential impact of broader blockchain deployment, and the implications recent events are likely to have on blockchain's future.