- Details
- Category: Security News
Anti-Malware , Litigation , Technology
Intel Sets McAfee Free But Long-Gone Founder John McAfee Files Suit to Reclaim His Name Chris Young, general manager of Intel Security Group - pictured here at the 2016 RSA conference - will become CEO of McAfee. (Photo: Mathew Schwartz/ISMG)
Chris Young, general manager of Intel Security Group - pictured here at the 2016 RSA conference - will become CEO of McAfee. (Photo: Mathew Schwartz/ISMG)As the famous line attributed to Shakespeare goes: "What's in a name?"
See Also: Detecting Insider Threats Through Machine Learning
Chipmaker Intel (Nasdaq: INTC) announced Sept. 7 that it will be spinning out its Intel Security unit, which will once again be named McAfee, becoming what Intel bills as one of the world's biggest "pure-play cybersecurity companies."
Under the terms of the deal, McAfee will be valued at $4.2 billion. TPG - one of the world's largest private equity investment firms, which oversees $70 billion - will own a 51 percent stake in the newly formed, independent company, while Intel will retain a 49 percent stake and receive $3.1 billion in cash. Intel says it expects to close the deal in the second quarter of 2017.
The new company will be led by Chris Young, a former Cisco senior vice president who's now the general manager of Intel Security.
The terms of the deal represent a major decrease in the value of the information security business, which Intel purchased for $7.68 billion in 2011 as part of a bid to bake security into its chips. "In the past, energy-efficient performance and connectivity have defined computing requirements," Paul Otellini, Intel president and CEO, said at the time. "Looking forward, security will join those as a third pillar of what people demand from all computing experiences."
That plan, however, never came to fruition. Financial Times recently noted Intel's then-CEO David DeWalt, who helped lead the sale, left to form cybersecurity firm FireEye, while his replacement, Mike DeCesare, exited Intel in 2014 and is now the head of cybersecurity firm ForeScout.
The McAfee spinoff wasn't a surprise, as it followed Financial Times reporting in June that Intel was exploring the option. Arguably, Intel was never able to truly cash in on McAfee's potential. In 2010, Intel said McAfee had $2 billion in annual revenue and 6,100 employees. When announcing news of McAfee's spinoff, Intel said it had $1.1 billion in annual revenue for the first half of 2016 and 7,500 employees.
News of the deal follows Intel announcing in April that it would cut its workforce by 11 percent, laying off about 12,000 workers, as part of a bid to focus more on building chips for cloud computing. Industry watchers say Intel has been challenged by declining PC sales and its inability to capitalize on the smartphone revolution.
Name Game
Meanwhile, the right to use the McAfee name is under legal contention.
By way of background, Intel had rebranded parts of its McAfee unit as Intel Security beginning in January 2014, although it did continue to use the McAfee name for certain parts of the business.
The rebranding push appeared to be a reaction to the well-documented saga of company founder John McAfee having fled Belize after being wanted for questioning in connection with a murder investigation. The self-described "eccentric millionaire" was ultimately arrested in Guatemala for illegally entering the country and deported to Miami.
While John McAfee founded McAfee Associates in 1987 and sold his stake in the company in 1994 for about $100 million, he has not been a part of his namesake since. Meanwhile, McAfee Associates was renamed Network Associates in 1997 - formed by merging Helix Software, McAfee Associates, Network General and PGP Corporation - then changed its name back to McAfee in 2004.
McAfee vs. McAfee
The news of Intel partially rebranding McAfee as Intel Security in 2014 was celebrated by John McAfee. "I am now everlastingly grateful to Intel for freeing me from this terrible association with the worst software on the planet. These are not my words, but the words of millions of irate users," McAfee told the BBC at the time. "My elation at Intel's decision is beyond words."
His remarks followed a now-infamous - and not-safe-for-work - video released in 2013, featuring McAfee in a smoking jacket, attempting to uninstall the eponymous software.
In June, MGT Capital Investments (Nasdaq: MGT) and John McAfee announced that they planned to rename MGT as "John McAfee Global Technologies, Inc.," featuring John McAfee as its executive chairman and CEO.
On Sept. 2, however, MGT and John McAfee filed suit against Intel, in response to a legal warning they said that they received from the technology giant. The complaint references a June 3 letter from Intel's managing counsel, Kelly Smith, which allegedly reads: "As you surely are aware, Intel (under its Intel Security division) uses the McAfee trademark in connection with its portfolio of anti-virus and other security solutions and services," and adds that the company owns a number of trademarks related to the name.
The letter further asserts that "McAfee sold the MCAFEE trademark to McAfee Associates, LP [a predecessor company] ... [and] forfeited any right to use the McAfee name in connection with security solutions and services." In particular, it adds, any attempt to create a company named "John McAfee Global Technologies, Inc." would result in Intel "tak[ing] all necessary legal action to protect its trademark rights."
Intel declined to comment on the lawsuit.
Welcome to the Cyber Party
In their complaint, however, McAfee and MGT dispute that John McAfee ever signed away his right to use his name. "At no point in the agreement did McAfee assign the rights to his personal name, via assignment of trademark or otherwise, or agree to restrict his right to do business using his own name," according to their complaint.
"I want my name back in its original, untarnished, pristine condition," reads a Sept. 5 tweet from John McAfee, whose Twitter profile still lists him as a 2016 presidential candidate.
McAfee had announced his entry into the race in September 2015 as head of a newly created "cyber party" (see Guess Who's Running for President? John McAfee).
- Details
- Category: Security News
Anti-Malware , DDoS , DDoS Attacks
Available Now: DDoS on Demand, Bitcoin Tumblers, Attack Affiliates and More Criminals hope "tumbling" bitcoins will make them tougher to trace
Criminals hope "tumbling" bitcoins will make them tougher to traceThe cybercrime sector involves a rapidly growing services economy.
See Also: Eight Capabilities IT Pros Should Look for in a CASB
Police estimate that just 100 to 200 people may be powering the "cybercrime-as-a-service" ecosystem by developing the attack code and services that enable criminals who lack technical acumen to pay for their cybercrime will to be accomplished.
If you can think of a cybercrime service, chances are that it exists.
Security experts say various providers offer such services as installing malware onto PCs and then selling access to those devices; selling subscriptions to malware and ransomware toolkits that automate attacks, with developers taking a cut of all proceeds; and "mule" services that will arm gang members with fake debit cards so they can make as many ATM cash withdrawals as possible before banks catch on.
Some service providers offer bulletproof hosting services, promising to look the other way should the rented servers be used to launch malware attacks. Other services will offer to "clean" the bitcoins that attackers demand from victims, making them more difficult for authorities to trace.
Many cyber-extortion attacks today, meanwhile, involve criminals threatening to launch distributed denial-of-service attacks against organizations unless they pay attackers bitcoins. To carry through on those threats, attackers often rely on so-called booter or stresser services, which sell on-demand DDoS attacks. This week, police in Israel - at the request of the FBI - arrested two men who have been accused of running a stresser/booter service called vDos. The service earned an estimated $600,000 in profit over the past two years as a result of launching 150,000 on-demand disruptions.
Based on online advertisements, the cybercrime-for-hire business appears to be so lucrative and booming that hacker gangs can't keep their crews staffed.
Why Criminals Love Ransomware
That's especially true for ransomware attacks, which criminals love because - as a recent report from McAfee summarizes - "they're financially lucrative with little chance of arrest."
Some ransomware gangs have even set up "customer care centers" to field ransomware victims' inquiries, for example, instructing them in how to procure the bitcoins attackers demand in exchange for a decryption key for unlocking a forcibly encrypted PC or server.
At the end of last year, the number of new ransomware samples seen in the wild spiked. McAfee says that was driven, in part, by the emergence of open source ransomware code such as EDA2 and Hidden Tear, both of which were created for what their developers claimed were educational purposes. Both, however, quickly found their way into cybercriminals' arsenals.
Last month, for example, a strain of ransomware that's based on Hidden Tear and sports a Pokémon Go theme was discovered by MalwareHunterTeam member Michael Gillespie. Still, the developers of those open source options may be having the last laugh, since they've subsequently disclosed purposeful weaknesses in the code, designed to make related ransomware easy to decrypt.
Ransomware's Surge
Unfortunately, not all ransomware is built with flawed crypto; options abound. In the first half of this year, Trend Micro reported seeing 79 new ransomware families, compared to 29 new ransomware families in all of 2015.
Ransomware is in vogue because related attacks are "very easy for criminals to monetize," says Rik Ferguson, vice president of security research for Trend Micro. "And it's something which is very easy for them to recruit in terms of networks, affiliates and distribution. And it's something which is morphing into another one of those crime-as-a-service offerings."
One affiliate program called Atom, for example, is based on Shark ransomware, which now "offers the soon-to-be cybercriminal customer an attractive 80 percent share of the profit for every successful payment from ransomware victims," Rommel Joven, an anti-virus analyst for cybersecurity software and hardware vendor Fortinet, says in a blog post.
Operational Security Concerns
Some attackers leverage these ransomware-as-a-service offerings - other examples include Ransom32 and Encryptor - not just because they eliminate the need to maintain their own attack infrastructure or code, but also because they can facilitate better operational security.
"You can use someone else's infrastructure, and so you're putting another layer between you and ... the defenders or law enforcement that might try to detect you," says Rick Holland, vice president of strategy for Digital Shadows.
Rick Holland, vice president of strategy for Digital Shadows, details why cybercriminals increasingly embrace software-as-a-service models.Operational security - a.k.a. OPSEC - refers to the practice of making one's activities more difficult to trace. For criminals, that might include using VPN service providers, the Tor anonymizing browser as well as bitcoins, which offer the promise of getting paid via tough-to-trace transactions.
Bitcoin Tumblers
Bitcoins, however, aren't truly anonymous, but rather pseudonymous, and researchers reportedly continue to find and develop new tools that allow law enforcement agencies to correlate information about suspects with bitcoin transactions, which all get logged, courtesy of the blockchain. What those actual capabilities are today, however, remains a closely held secret.
 Multiple sites will offer to launder bitcoins, supposedly making them more difficult for authorities to trace.
Multiple sites will offer to launder bitcoins, supposedly making them more difficult for authorities to trace.In response, some criminals have taken to seeking "clean coins" by means of a process called tumbling, which is the process of using a third-party service or technology to launder bitcoins. This "bitcoin mixing," as it's also known, involves breaking "the connection between a bitcoin address sending coins and the address(es) they are sent to," Will Gragido, head of threat intelligence for Digital Shadows, says in a blog post.
"Tumbling, it was discovered, could be as easy as confusing the trail of transactions between two wallets, making investigation and attribution almost impossible," he says. For example, an attacker could create one wallet, add bitcoins to it, then create a second wallet - via Tor - and move the funds into the new wallet.
For some attackers, however, the preferred option appears to be using third-party services to provide tumbling, which promise even greater degrees of obfuscation. One such service, Helix, promises users added privacy and security by swapping customers' bitcoins for "brand new ones that have never been to the darknet before."
As with all things cybercrime, where there's a criminal need, service providers seem all too ready to fulfill it.
- Details
- Category: Security News
Cybersecurity , Data Breach , Fraud
London Cops Busted Gang that Intercepted Shipments of Gold Adam Penny, 25, admitted to masterminding a hacking scheme designed to help steal gold bullion. (Source: Met Police)
Adam Penny, 25, admitted to masterminding a hacking scheme designed to help steal gold bullion. (Source: Met Police)A man who pleaded guilty to hacking into a gold bullion trading company's computers so his associates could intercept their gold shipments has been sentenced to serve five years and four months in jail. London's Metropolitan Police said they were able to launch the case thanks to the breached business having come forward.
See Also: Detecting Insider Threats Through Machine Learning
On Sept. 12, Adam Penny, 25, was sentenced at Kingston Crown Court in London. He'd been charged with conspiracy to steal, unauthorized access to a computer and blackmail. On April 1, he pleaded guilty to the first two charges, and not guilty to blackmail. But he was convicted of the blackmail charge in July.
Police say that Penny and three other individuals, who have also been sentenced, plotted to steal nearly £90,000 ($120,000) by physically intercepting shipments of gold to the customers of an unnamed metal-trading firm.
Penny was first arrested at his home in London in June 2015 as part of an investigation led by detectives from the Met's Cyber Crime Unit. The Met is responsible for policing greater London, with the exception of the city's financial district, which is the responsibility of City of London police.
At the time of Penny's arrest, investigators say, they seized six iPhones and two MacBooks - one secreted in a toilet cistern - from his house. They say that after conducting a digital forensic examination of the systems, they recovered "evidence of Penny's blackmail demands to the company and instructions for his interceptors."
Intercepting Postal Deliveries
In court, prosecutors detailed a criminal campaign that involved Penny hacking into the systems of a firm that sells bullion - referring to any bulk quantity of a precious metal - to steal details of customers and impending gold shipments. Penny then shared that information with his associates so they could attempt to physically intercept the deliveries.
"Penny hacked into the computers of the company and got others to intercept the gold packages for him," Detective Constable Matt Burke, who's part of the Met's Cyber Crime Unit, says in a statement. "When even this wasn't enough for his lavish lifestyle, he blackmailed the company for £50,000 ($66,000). At the time of his arrest, Penny was living in a luxury apartment in the Canary Wharf area, despite having no paid employment that we could identify."
A LinkedIn profile registered in Penny's name lists Penny as being a dealer in precious metals as well as the founder and managing director of a company called GB & Coins Limited, founded in November 2014. "The business is totally focused on delivering exceptional service to private investors looking to buy gold and silver coins or bars. At U.K.'s cheapest prices," the profile states.
Penny's previous job, according to the LinkedIn profile, was delivering newspapers for three years for a corner shop.
In 2011, Penny - then age 19 - had faced one charge of fraud and two charges of money laundering after he allegedly defrauded gold bullion buyers on eBay, local newspaper Western Morning News reported. In particular, three separate buyers had reported losing between £4,400 ($5,800) and £6,850 ($9,100) each. Penny denied the allegations, and the Crown Prosecution Service said that it lacked sufficient evidence to pursue the case, leading to it being dismissed.
Gang of Four
In the case of the gold-interception scheme, three others have also been convicted of conspiracy to steal and were sentenced Sept. 12:
Joshua Wilkins, 25, who was sentenced to 22 months' imprisonment; Nour Mansouri, 24, who was sentenced to 200 hours community service and ordered to pay £1,000 ($1,325) in costs; Daniel William Rabbitte, 25, who was sentenced to 18 months' imprisonment, which has been suspended for two years, meaning that if he doesn't commit any further offenses for two years, he'll stay out of jail."The defendants stole, or attempted to steal, six packages with an estimated value of over £88,000 ($117,000)," according to the Met. "The stolen gold was then sold to an unsuspecting jeweler in London."
 Also sentenced (from left): Joshua Wilkins, Nour Mansouri and Daniel William Rabbitte. (Source: Met Police)
Also sentenced (from left): Joshua Wilkins, Nour Mansouri and Daniel William Rabbitte. (Source: Met Police)
Prosecutors told the court that Penny provided relevant customer details and shipment-tracking numbers to Wilkins, Mansouri and Rabbitte, who would then go to the designated address and wait for the delivery. In one case, the defendants traveled to Newcastle - 300 miles north of London - where they attempted to take receipt of a delivery but failed "because the postman knew the victim and refused to hand over the parcel," according to the Met police.
Victim Came Forward
Police said they were able to launch the case after the business that was targeted alerted authorities (see Cybercrime Victims: Please Come Forward).
"This case highlights the importance of robust cybersecurity systems for businesses and particularly those with an online presence," Sanjiv Gohil, a detective inspector with the Met's Cyber Crime Unit, says in a statement. "In this case, the breach was reported to the police and we were able to investigate and bring Penny to justice, without further compromise to the company and their customers."
- Details
- Category: Security News
 The vDOS site user interface
The vDOS site user interfaceTwo men have been arrested by Israeli police, at the request of the U.S. Federal Bureau of Investigation, in connection with an investigation into the vDos site, which provided distributed denial-of-service attacks on demand.
See Also: A Smarter Approach to Third-Party Vendor Risk: A Case Study
Itay Huri, a.k.a. "P1st" and "M30w," and Yarden Bidani, a.k.a. "AppleJ4ck," both age 18, were arrested Sept. 8, according to a local press report. Police told Israeli financial website The Marker that the arrests were made at the request of the FBI, and that both men were questioned Sept 9 and released under house arrest for 10 days after they posted the equivalent of about $10,000 in bail. Both men have been prohibited for 30 days from connecting to the internet or using any type of telecommunications device and from leaving the country or communicating with each other, police said. They also are required to report to police for questioning on demand. Both men's passports have also been confiscated.
Police did not specify the charges against the men, The Marker notes. But both were named by security blogger Brian Krebs in a Sept. 8 blog on the vDos service. Based on leaked documents, he estimated that vDos had earned more than $600,000 in profits over the past two years, courtesy of launching 150,000 DDoS disruptions.
The vDos site advertised various plans costing $30 to $200 per month. But the site and service have been offline since Sept. 9.
All of the email domains associated with vDos administrators used a domain that had been registered to someone named Itay Huri, using a phone number tied to Israel, Krebs reported. The service was configured to send requests for tech support via text messages - using an SMS service called Nexmo.com - to six mobile phone numbers, one of which matches with a phone number used by Huri on a domain registration, and another that's tied to an Israeli citizen named Yarden Bidani, according to the blogger. Krebs added that support emails were being routed to the email addresses itay@huri[dot]biz,
On March 7, 2015, the Twitter account @AppleJ4ck_vDos, which lists "Yarden Bidani" as the account holder's name, and "vdos-s.com" as his site, claimed that parts of the Pentagon website had been disrupted.
Based on the leaked data, other potential victims of vDos included gaming site GoodGame.co.uk, anti-DDoS firm Zare.com and the Model United Nations club for the U.K.'s Imperial College in London, the Register reports.
Customer Secrets Spilled
DDoS defense provider CloudFlare is hosting a text file containing a list of attacks carried out by vDos from April to July, including the vDos username that commissioned the attack, the target IP address, as well as details relating to the attack type, date and time. The information was gleaned after an anonymous security researcher reportedly exploited a vulnerability in the vDos site in July and stole copies of the databases and configuration files underpinning the site. Krebs said he was given a copy of those files and noted that many trouble tickets logged by the site related to users complaining that DDoS attacks that they commissioned against targets in Israel were not happening - suggesting that the site's administrator's prohibited attacks against Israeli targets.
"Chances are that many of vDos's customers may have imagined that their details would have been kept private, and that there would have been little risk of their identities being discovered," says security expert Graham Cluley in a blog post. "That belief was clearly misguided."
Claims of Legitimacy
DDoS-on-demand services are often marketed as being stresser/booter services that can supposedly help administrators test their sites' resilience against DDoS disruption attempts. And vDos appeared to be no different, running a blog post on Aug. 4, for example, titled "5 ways to prevent DDoS attacks."
On June 21, vDos published a tweet marketing its services a preventive tool. "#Booters give your #network the ounce of prevention it needs against #DDoS by simulating Layer 4 and Layer 7 tests," it stated.
Likewise, Huri and Bidan appeared to be positioning themselves as DDoS security experts. In August, they released a technical paper on amplified DDoS attack techniques - how to maximize disruptive power using minimal resources - for an Israeli technology site called Digital Whisper. The paper was bylined with Huri's name as well as a researcher using the email address "
Distributed Cybercrime Economy
Despite any claims to legitimacy, stresser and booter services have long been favored by anyone who holds a grudge - criminals, hacktivists, unscrupulous competitors, rival political parties - as a way to disrupt any individuals or organizations to which they're opposed.
DDoS defense firm Incapsula estimates that DDoS-for-hire services accounted for 93 percent of all DDoS attacks seen between January and March of this year. That was a marked increase from April to June 2015, when Incapsula tied 64 percent of all DDoS attacks to such stresser or booter services.
Using such services enables criminals to obtain DDoS attack capabilities without having to maintain related infrastructure themselves. Indeed, cybercrime gangs such as Armada Collective and DD4BC have used such disruptions, or the threat of such disruptions, to extort victims into giving them bitcoins (see Stresser/Booter Services Fuel DDoS Extortion).
Advertisements for vDos have also often been featured on the Hack Forums site - described as "a wretched hive of scum and villainy" by Robert McArdle, threat research lead for Europe, the Middle East and Africa at security vendor Trend Micro.
McArdle has said that Hack Forums often attracts cybercrime wannabes - a.k.a. script-kiddies - who lack technical knowledge but want to know how to bolster their skills, noting that so often, "today's idiot is tomorrow's supervillain."
- Details
- Category: Security News

SentinelOne, one of a batch of vendors using machine learning to conquer malware, says it will not integrate its malware detection engine into VirusTotal service. CEO and co-founder Tomer Weingarten claims the investment wouldn't provide a worthwhile return right now, although the company is open to working with Google, which runs VirusTotal.
See Also: Avoid 75% of all Data Breaches by Keeping Privileged Credentials Secure
Security companies use VirusTotal to get a heads-up on new malware samples via a threat feed. Malware can also be uploaded to get a quick idea of how more than 50 vendors might be detecting a new sample. A subscription package also lets companies see why a vendor decided if something was malware, via its so-called "ratings" feature.
In a controversial move, VirusTotal said it would block vendors that have not integrated their anti-virus engines into the scanning service to access the ratings feature. The change came after long-established security vendors alleged that startups were leaning on those ratings to keep their own products up to speed.
Weingarten, meanwhile, claims the way the scanning service is configured doesn't accommodate how SentinelOne actually works.
"The infrastructure needs to change, and once it happens and once we can actually work with that, I would say 'why not?'" Weingarten says. "The investment we need to make in order to kind of try and work with them is not something ... we're willing to afford right now."
By contrast, CrowdStrike and Invincea recently said both would allow their technology to be integrated into VirusTotal. Another much talked-about startup, Cylance, didn't respond to a query about whether it plans to make a similar move (see CrowdStrike, Invincea Integrate With VirusTotal).
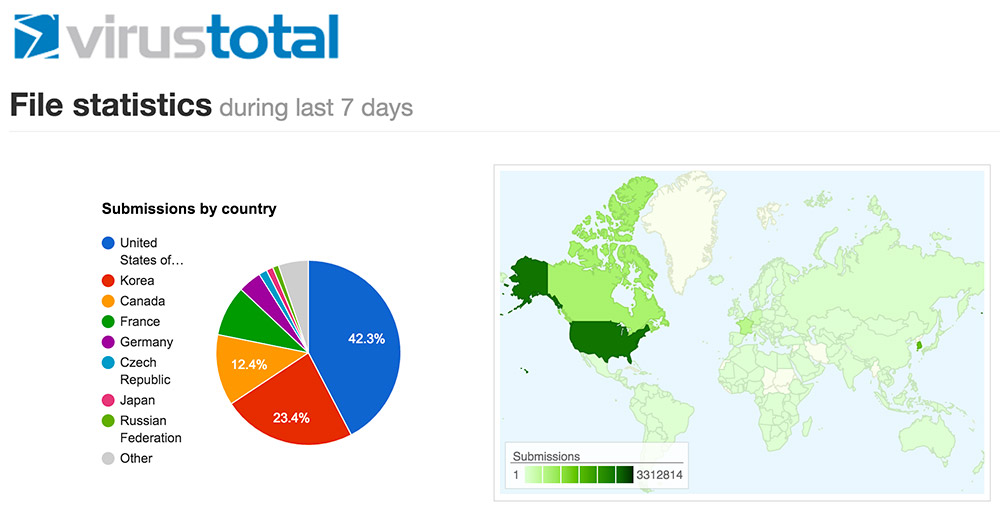 VirusTotal allows anyone to submit a file or URL for scanning, to see if it appears to be malicious.
VirusTotal allows anyone to submit a file or URL for scanning, to see if it appears to be malicious.
Debate: Static vs. Dynamic
SentinelOne's product has several components. Its Dynamic Behavioral Engine uses machine learning - which can also be referred to as statistical analysis - to determine whether something is likely malicious.
The Dynamic Behavioral Engine monitors all processes and applications from the operating system's kernel, including a computer's memory, network connections, input/output traffic, system calls and API calls. It then uses algorithms to classify every kind of behavior by processes to determine if those processes might be malicious. The decision by those algorithms is made on an endpoint, so the computer could be offline and the detection capabilities wouldn't be affected.
SentinelOne's Windows and Mac products are a bit different. As a backstop on Macs, the product also uses data from the cloud, flagging suspicious binaries before they run based on factors that have been seen in the past. Weingarten says, however, that no signatures are used in that process.
Startup security vendors have waged aggressive marketing campaigns criticizing older companies for relying too heavily on signatures - descriptions of known malware files - for deciding whether a file should be immediately quarantined. Signatures are faulty in the sense they're created after something has already attacked a computer. Malware authors often re-compress the same attack code to make it look different while leaving it functionally intact and enabling it to evade vendors' lists of known malware signatures.
But old-guard companies such as Symantec and Trend Micro have for years also employed behavioral analysis techniques to identify malware. It's part of why those companies have been irritated by some of the newer startups' marketing techniques and have suspected unfair play when it comes to utilizing VirusTotal's data. Trend Micro made some of its most pointed accusations just after VirusTotal announced its changes.
No Problem for CrowdStrike
Explaining why SentinelOne is currently opting to not integrate with VirusTotal, Weingarten says that VirusTotal would need to be able to accommodate executable code for his product to work effectively with it. He suspects that some newer security vendors do not have their entire anti-virus engine integrated with VirusTotal, but rather a command-line static analysis engine, which would meet the service's new requirements.
CrowdStrike, though, doesn't appear to have the same problem, or else has worked around it. The company explained in an Aug. 25 blog post how its Falcon Host scanner has been integrated. Although it's not present just yet on VirusTotal, Falcon Host will give a "confidence score" related to whether something is malware or not. The score is calculated after analyzing thousands of aspects of a file or executable.
"If we detect a file, we return a confidence score - there is no coarse yes/no decision as with traditional, signature-based AV," wrote Sven Krasser, CrowdStrike's chief scientist. "Presently, the score ranges from 60 to 100. The higher the score, the more certain we are that the file is indeed malware."
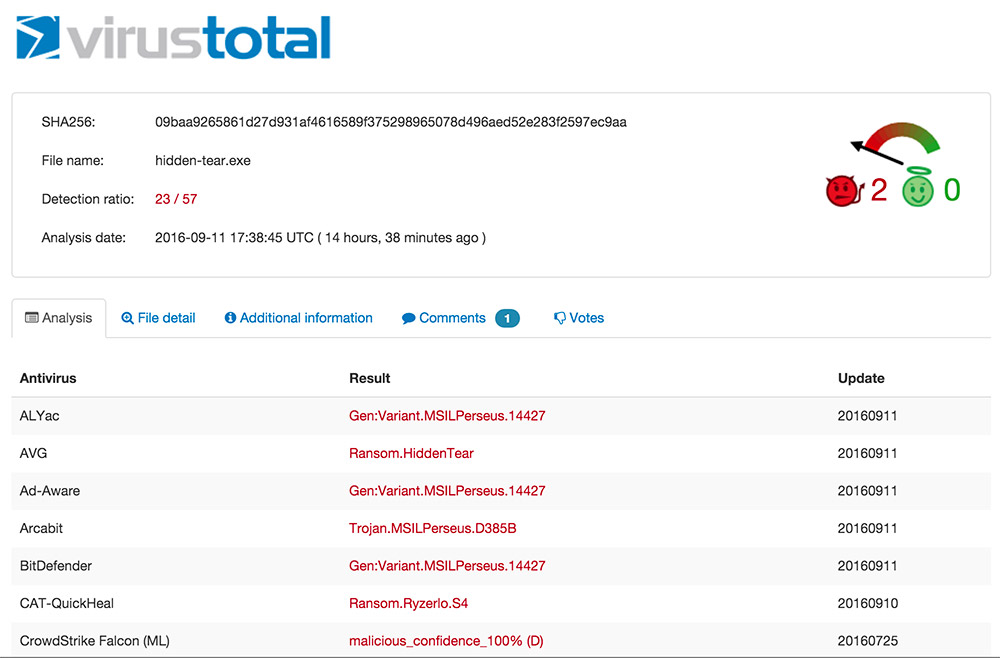 VirusTotal says its service "checks suspicious samples with several anti-virus solutions and helps anti-virus labs by forwarding them the malware they fail to detect," but should not be used to compare anti-virus products, which often include complementary defenses that it doesn't take into account.
VirusTotal says its service "checks suspicious samples with several anti-virus solutions and helps anti-virus labs by forwarding them the malware they fail to detect," but should not be used to compare anti-virus products, which often include complementary defenses that it doesn't take into account.
Machine Learning
Weingarten says that despite SentinelOne's decision, it's still on friendly terms with VirusTotal. SentinelOne also still pays for a subscription to the malware feed.
Not having access to the ratings doesn't matter since the company didn't depend on that information, he says. VirusTotal's malware feed goes to SentinelOne's machine learning clusters, which analyzes malware, malicious documents, suspicious scripts and exploit code. The company then updates its algorithms on endpoints once or twice a month via a slim, 100K file.
"We profile hundreds of thousands of files and attack code samples on a daily basis," Weingarten says.
More Articles …
Page 3498 of 3546
