- Details
- Category: Security News
Anti-Malware , Encryption , Technology
FBI to Ransomware Victims: Please Come Forward Bureau Says Reporting Crime Drives Intelligence, Disruption, Arrests
Have you been the target or victim of ransomware-wielding attackers? If so, your government needs you to come forward.
See Also: Disrupt Attack Campaigns with Network Traffic Security Analytics
So says the FBI in a new public service announcement aimed at both individuals and businesses. The FBI says the effort is designed to get "victims to report ransomware incidents to federal law enforcement to help us gain a more comprehensive view of the current threat and its impact on U.S. victims."
The bureau says that while anecdotal reports of crypto-locking attacks abound, it needs more precise information about attackers - ranging from the ransomware variant to the attacker's bitcoin address - to help it pursue, disrupt and potentially arrest suspects.
"While ransomware infection statistics are often highlighted in the media and by computer security companies, it has been challenging for the FBI to ascertain the true number of ransomware victims as many infections go unreported to law enforcement," the FBI's alert says.
Why Report?
The bureau has previously asked victims of everything from tech support scams to CEO fraud to come forward in efforts that parallel outreach by European law enforcement and security experts.
Security experts say that even if law enforcement agencies cannot act on every criminal report they receive, having victims come forward serves several essential purposes:
Intelligence: Reporting crime gives law enforcement agencies a more accurate picture of attackers' techniques so that they can attempt to track and ultimately disrupt them. Funding: Crime reports also help law enforcement agencies gauge the scale of the problem so they can devote sufficient resources as well as secure needed funding from legislators or other policymakers. Arrests: Amassing intelligence on cybercrime gangs helps investigators better correlate gangs' activities, thus potentially helping them unmask and pursue the individuals involved as their attacks generate more clues. The FBI has previously noted that "much of the infrastructure being used by cybercriminals is hosted overseas," and that it often works with international law enforcement agencies.FBI Seeks 9 Data Points
The FBI is asking anyone who's been the victim of a ransomware infection to file a report with the local FBI field office or via the website of the Internet Crime Complaint Center, or IC3. That's a joint partnership between the FBI, the National White Collar Crime Center and the Bureau of Justice Assistance, which was set up to receive and investigate internet-related crime complaints.
Here's the precise information being sought by the bureau:
Date of infection; Ransomware variant, as identified on the ransom page or by the encrypted file extension; Victim company information - industry type, business size; How the infection occurred - link in email, browsing the internet, etc.; Requested ransom amount Attacker's bitcoin wallet address - often listed on the ransom page; Ransom amount paid, if any; Overall losses associated with a ransomware infection, including the ransom amount; Victim impact statement.Please Don't Pay
In its public service request, the FBI again urges anyone who's suffered a ransomware infection to never pay ransoms because it helps criminals refine their attacks and snare even more victims.
"Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom," the FBI says. "Paying a ransom emboldens the adversary to target other victims for profit, and could provide incentive for other criminals to engage in similar illicit activities for financial gain."
The FBI also notes that business realities may, of course, influence some organizations to pay the ransom. "While the FBI does not support paying a ransom, it recognizes executives, when faced with inoperability issues, will evaluate all options to protect their shareholders, employees and customers."
Legal experts say there appears to be no way for U.S. law enforcement agencies to prosecute anyone who pays a ransom, even if the money ends up in the hands of an individual or organization on the U.S. Treasury Department's sanctions list, provided victims employ an intermediary. I've been told that some organizations are setting up such plans as well as stockpiling bitcoins in the event that they do fall victim to a related attack.
Anti-Ransomware Portal Offers Help
Some victims, however, can get the equivalent of a "get out of jail for free" card, thanks to ongoing efforts by security researchers to crack attackers' weak crypto or otherwise exploit code-level flaws in attack code.
 Photo: Mark Strozier (Flickr/CC)
Photo: Mark Strozier (Flickr/CC)One related effort, the public/private No More Ransomware portal, says that since launching in July, it's enabled 822 CoinVault and 941 Shade ransomware victims to decrypt their data for free.
While that's good news, as the FBI noted earlier this year in an intelligence memo, don't count on decryptors always being available, because they rely on attackers making coding errors.
"Since the most sophisticated ransomware variants are practically impossible to defeat without obtaining the actor's own private decryption keys, the FBI has focused on performing significant outreach to educate the public on ransomware and the importance of keeping backups and maintaining a level of operational security when using a computer," the FBI's memo states.
- Details
- Category: Security News
Application Security , Risk Management , Technology
Dropbox 'Hacks' Macs, Researcher Warns Dropbox Defends SQL Trick, Saying Desktop App Needs Broad Permissions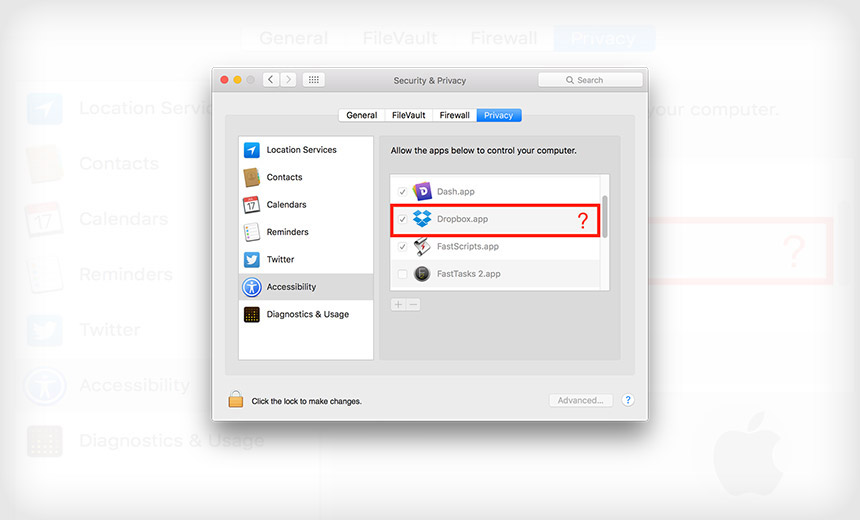 Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?
Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?A researcher's discovery of a sneaky trick used by Dropbox to gain wide-ranging access to Apple Mac OS X computers has infuriated some users, who allege the popular application is acting in a manner that's similar to malware. Dropbox officials have downplayed the finding, saying its Mac desktop app requires the modification to function correctly. But that hasn't stopped some users from vowing to never to use the file-sharing application again.
See Also: Disrupt Attack Campaigns with Network Traffic Security Analytics
The warning over the apparent liberties taken by Dropbox's software comes via Phil Stokes, a developer and freelance writer who authors the Applehelpwriter blog. Stokes, who digs deep into the workings of OS X, said he couldn't figure out why it seemed to be impossible to eliminate Dropbox from Apple's accessibility menu, which falls under the operating system's security and privacy options.
Although Dropbox asks for permission to be added to the accessibility menu, it arguably isn't honest about the its exact motivations. And once the program is in accessibility, it can't be easily removed - or at least, if it gets removed, it keeps reappearing, Stokes said. Of course, that's the kind of behavior that makes advanced users very, very nervous.
Beyond Accessibility
Here's the concern: An application inside the accessibility menu has total power over a computer. Apple introduced accessibility to allow people with disabilities, such as the blind, to still be able to use applications. Accessibility allows approved applications to perform actions on a user's behalf, such as clicking on menus and buttons and deleting files. Approved applications also get access to sensitive information, such as contacts and calendars.
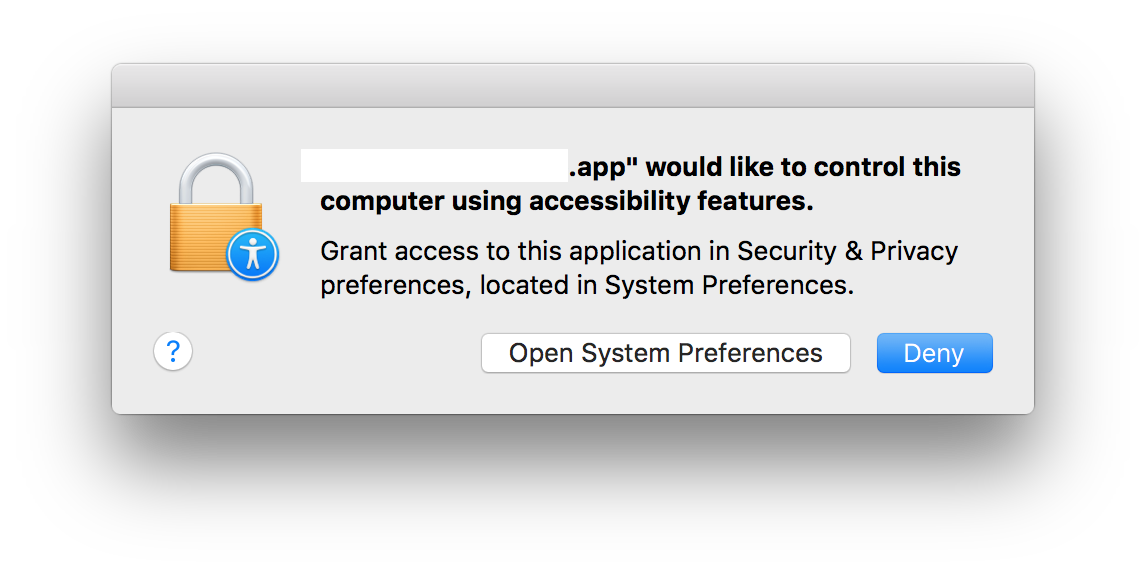 The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes)
The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes)Stokes couldn't figure why Dropbox kept appearing after he revoked its accessibility privileges, and he said the security implications of his inability to remove the application are serious.
"If Dropbox itself has a bug in it, it's possible that an attacker could take control of your computer by hijacking flaws in Dropbox's code," Stokes writes. "Of course, that is entirely theoretical, but all security risks are - until someone exploits them."
Permission Confusion
How Dropbox gets into accessibility isn't straightforward. Apple has a standard dialog box that appears when an application wants to get added to the system preferences menu. It advises that an app "would like to control this computer using accessibility features" and that access can be granted through the "security & privacy preferences."
Instead, Dropbox displays a custom-worded dialog box that asks for a user's system password. It advises that the system password is necessary "for Dropbox to work properly." But the mystery wasn't completely solved. Stokes said in his blog post that gaining access to the system password still shouldn't be enough to allow Dropbox to place itself in accessibility.
By late August, however, Stokes had found the answer. Dropbox uses the system password to then drop three binary files onto the computer. One of those binaries tampers with a SQL database called TCC, which is built into Mac OS X to track which applications are in accessibility.
"We finally hit gold, and the exact proof I was looking for that Dropbox was using a SQL attack on the TCC database to circumvent Apple's authorization policy," Stokes wrote in a second blog post.
Dropbox's slight modification to the database means that even if a user removes the Dropbox app from the accessibility menu, it will keep reappearing - a magic trick that many people would consider to be a hack.
Phil Stokes demonstrates how Dropbox overrides OS X user preferences in the security & privacy accessibility pane.Cue Backlash
After Stokes' findings reached Hacker News, Dropbox faced an immediate and strong backlash, particularly from users who are naturally prone to be suspicious over what permissions applications want.
"The only way to regain my trust at this point is providing an official explanation of what's going on with technical details," wrote a user who goes by the nickname Bicubic. "Now that I got the impression that Dropbox is doing something outside of that envelope, even if that impression is wrong, my money is going to go elsewhere, probably to a competitor."
Dropbox's Ben Newhouse, who lists his position at the company as "minister of magic," and works on the company's desktop client team, quickly weighed in on Hacker News.
The intention, he writes, has been to ensure that Dropbox functions properly across operating system updates. Apple's controls for granting permissions "aren't as granular as we would like," he writes. He also maintains that the company doesn't store a computer's system password.
But Stokes has noted that Dropbox really, really wants a user's system password, and it will pester users every time the Dropbox desktop app is launched - or the computer is restarted - until a user parts with it.
In response, Stokes noted that Dropbox appeared to work perfectly well, even if he declined to share his system password, thus calling into question Dropbox's contention that it must know a user's system password.
Dropbox declined to make Newhouse available to me for an interview.
But the company has issued a formal press statement attempting to further downplay the controversy.
Dropbox to Users: No Spoofing
"Reports of Dropbox spoofing interfaces, or capturing system passwords, are absolutely false," it says. "We realize we can do a better job communicating how these permissions are used, and we're working on improving this."
The explanation fell flat with some users, however, who say they've uninstalled Dropbox.
"I understand the desire to make your features 'just work,' but circumventing the user's privacy controls to do that is never acceptable," wrote a Hacker News commentator who goes by the name Brentdax. "Especially accessibility, which is basically a general warrant to snoop on everything the user does. You wouldn't be on my system anymore if my work didn't require Dropbox. You're going to lose a lot of trust over this, and it won't even be half of what you deserve."
The Dropbox hack's days, however, appear to be numbered. Stokes says he notified Apple last year about the issue but never heard back from the company. But he's noticed that the upcoming 10.12 version of OS X, code-named Sierra and due for release Sept. 20, blocks the trick.
- Details
- Category: Security News
Application Security , Cybersecurity , Risk Management
Researchers' Hack Turned on Wipers, Opened Doors and Applied Brakes Photo: Maurizio Pesce (Flickr/CC)
Photo: Maurizio Pesce (Flickr/CC)Electric car manufacturer Tesla has updated its firmware after researchers in China demonstrated how they could remotely turn on the windshield wipers, open the trunk and apply the brakes in brand-new Model S sedans.
See Also: Protecting Your Assets Across Applications, Services and Tiers
The researchers, from Tencent's Keen Security Lab, released a video and blog post on Sept. 19 after Tesla had been privately informed of the software. An over-the-air software update was delivered 10 days after Keen notified Tesla. The car maker maintained that the risk to customers was very low.
"We commend the research team behind today's demonstration and plan to reward them under our bug bounty program, which was set up to encourage this type of research," the company says in a statement.
The automotive industry has been under increasing pressure to ensure its software is free of vulnerabilities that could jeopardize safety. Cybersecurity experts have warned for years that the increasing complexity of vehicle computers, combined with network connectivity, poses vast new risks.
A dramatic public demonstration of a vehicle hack last year advanced those concerns. Chris Valasek and Charlie Miller remotely triggered a 2014 Jeep Cherokee's brakes on a California highway. While the demo was criticized for its possible risks to the public, it illustrated that worries about vehicle hacking were already far beyond theoretical (see Creating Cybersecurity Rating Systems for Cars).
That hack was enabled by software vulnerabilities in UConnect, which is a telematics unit used for navigation and entertainment. As a result of the research, Fiat Chrysler recalled 1.4 million vehicles.
To strengthen security, Fiat Chrysler and Tesla launched bug bounty programs this year that reward independent researchers for responsibly reporting security flaws. Vehicle manufacturers have also established the Automotive Information Sharing and Analysis Center (Auto-ISAC) to share information on vehicle-related threats (see Car Hacking Spurs Automakers to Share Threat Information).
Wipers Are On
Keen Research Lab's video shows the effects of the researchers' attacks against two Tesla Model S sedans in a rainy parking lot.
Their blog post says the software problems, uncovered over several months, granted access to the Controller Area Network bus (CANbus), a critical unit that brokers signals from a variety of electronic systems.
The demonstration, while light on technical detail, shows how they were able to open the sunroof, turn on a turn signal, move the driver's seat back and lower the back left window on a white Model S P85 Tesla.
A second attack was directed against a red Model S 75D. Senior researcher Sen Nie asks Keen Security Lab Director Samuel Lv to figure out where the nearest charging station is. Lv sits in the red Tesla for a bit and comes back, saying a charge point is about six miles away. Ling Liu, a Keen researcher, then says, "It is ready."
Lv returns to the vehicle to find that the large, 17-inch touchscreen tablet mounted on the dashboard is unresponsive, and the driver's instrument cluster is also frozen. Both displayed the logo for Keen Security Lab. In a low-speed driving demo, they turn on the windshield wipers, open the trunk, manipulate a right-side mirror and trigger the brakes remotely from 12 miles away.
Tesla's statement indicated the software problems are linked to the touchscreen tablet's web browser.
"The issue demonstrated is only triggered when the web browser is used, and also required the car to be physically near to and connected to a malicious Wi-Fi hotspot," the company says. "Our realistic estimate is that the risk to our customers was very low, but this did not stop us from responding quickly."
Mystery Vulnerabilities
Craig Young, a cybersecurity researcher with Tripwire, says a Wi-Fi attack could only be conducted at a maximum distance of around 900 feet. "I suspect that the attack may have actually been possible by another user on the same cell tower or with a cell site stimulator," Young says. "In this case, I hope that the researchers do release further details to help understand the automotive attack surface better."
Nonetheless, the exercise shows how security holes in an application can be used to gain kinetic control over a vehicle. "Ideally these systems should be completely isolated from one another," Young says.
The up-to-date software is v7.1 2.36.31, and drivers are advised to ensure the patches have been applied.
- Details
- Category: Security News
CISO , Education , Governance
Testimony Given to Presidential Commission on Enhancing National Cybersecurity Commerce Secretary Penny Pritzker (Photo: Department of Commerce)
Commerce Secretary Penny Pritzker (Photo: Department of Commerce)A group of cybersecurity policymakers recommends a series of steps the U.S. federal government and the private sector should take to ensure that the nation will have enough cybersecurity specialists in the coming decade.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
Among those steps are providing student debt forgiveness for those studying cybersecurity, creating internships and mentorship programs as well as moving to centralized recruiting and training for the federal government.
In testimony given Sept. 19 before the presidential Commission on Enhancing National Cybersecurity, witness after witness stated the need for government-backed initiatives to enhance the IT security workforce in government and the private sector.
"This shortage is reflected at every level, from basic entry-level network managers to senior researchers," says Neal Ziring, technical director for capabilities at the National Security Agency. "The technologies of cyberspace will continue to grow and change, and attackers will continue to develop new tradecraft. Without a solid workforce, we will not be able to maintain or improve security in the long term. ... The shortage will continue indefinitely unless we take action to alleviate it."
200,000 Shortfall in Cybersecurity Specialists
The situation is acute in the federal government.
Commerce Secretary Penny Pritzker, in her prepared remarks, points out that the nation faces a shortfall of 200,000 cybersecurity specialists. That gap hits government particularly hard. "Since arriving at Commerce, I have faced a chronic shortage both in quantity and quality of cybersecurity personnel," she says. "Yet I do not have the authority, flexibility or resources to do enough about it. ... The federal government's challenges are compounded by a smaller talent pool, uncompetitive salaries and a cumbersome hiring process."
But even when qualified personnel are identified, getting them on board remains a challenge. "As many of you know, Washington is not Silicon Valley; hiring takes months, not minutes," Pritzker laments. "In all honesty, I feel like Sisyphus here. I meet biweekly with my CIO and often find out that by the time we bring someone new on board, someone else has been lured away by private sector perks or poached by an agency that offers hiring bonuses or higher pay."
Gregory Wilshusen, director of information security issues at the Government Accountability Office, says he doesn't expect the situation in the federal government to improve soon. "Ensuring that the government has a sufficient number of cybersecurity professionals with the right skills and that its overall workforce is aware of information security responsibilities remains an ongoing challenge," Wilshusen says in written testimony.
Continuing Struggle
Studies over the years show the struggle in building an IT security staff. For example, a GAO survey earlier this year of federal agencies' CISOs reveals their difficulties in recruiting, hiring and retaining security personnel. Wilshusen says the problem of maintaining a sufficient security staff makes it more challenging for agencies to effectively carry out their responsibilities.
In building the federal government's cybersecurity workforce, Pritzker suggests the commission consider recommending a centralized system to recruit, train and place federal cybersecurity personnel as well as creating specialized pay scales to compete with the private sector.
"We need to rethink recruitment with bold ideas like debt forgiveness for graduates of certified programs, tuition-free community college in return for federal service and cybersecurity apprenticeships within civilian agencies," the Commerce secretary says.
NSA's Ziring offers similar suggestions for building the IT security workforce, including supporting students pursuing cybersecurity degrees and certificates directly through scholarships and indirectly through internship programs and industry incentives. Ziring cites as an example the National Science Foundation Cybercorps Scholarship for Service Program, which he contends has been successful in drawing talented undergraduate and graduate students into cybersecurity and then placing them in government positions at the start of their careers.
Teaching the Teachers About Cybersecurity
All sectors - not just the government - face challenges in boosting their cybersecurity staffs. A major roadblock is the dearth of qualified educators to train cybersecurity specialists.
"High schools and universities are being challenged to introduce cybersecurity to the nation's next generation in order to create a substantial pipeline of inspired cyber students," says Rick Geritz, CEO of the online learning platform LifeJourney. "The reality is that high schools and teachers lack cybersecurity skills and training."
Geritz suggests in his testimony that mentoring by cybersecurity specialists can play a role in addressing the shortage of qualified educators.
"Evidence informs us that mentoring is critical - to both students and teachers - to imparting up-to-date knowledge about the field, the marketplace needs and career opportunities," Geritz says. Mentoring programs "must be designed to facilitate the spirit of collaboration among all participants committed to the universal goal - to optimize the national - and ultimately the planetary - human capital base."
In his testimony, Geritz cites studies that show significant mentoring relationships help drive individuals into specific careers.
Geritz also recommends offering cybersecurity training for all teachers, irrespective of their background or current assignments. Such training, he says, would enable more educators to inspire students to become part of America's digital economy. He also suggests a "day of cyber," which would expose all students to cybersecurity skills so they'd understand the career opportunities in the field.
Seeking Well-Rounded CIOs
Karen Evans, a former federal CIO who heads the U.S. Cyber Challenge, a program of competitions and encampments aimed to attract young people to cybersecurity workforce, testified about the skills federal agencies' CIOs are lacking.
"Many CIOs argue they don't 'have a seat at the table,'" Evans says. "I would argue that a seat at the table is earned by having the skills and abilities to contribute to the agency's mission - including protecting the agency from threats."
Federal law assigns responsibility for agencies' IT security to their CIOs. Evans points out that CIOs serve as strategic advisers to the heads of federal agencies regarding the use and management of information while managing the risk associated with use of technology to provide the mission services.
Evans says the commission in its findings should urge rigorous enforcement of federal rules that CIOs possess the technical and policy skills needed to serve their agencies.
"The skills set needed by the CIOs includes more than just understanding policy," she says. "CIOs who have technical skills and understanding combined with the good communications and interpersonal skills will be successful."
Commission Mandate
President Obama, in an executive order issued in February, created the Commission on Enhancing National Cybersecurity, requiring it to submit a final report by Dec. 1 with recommendations for how the government and private sector can strengthen cybersecurity over the next decade while protecting privacy, ensuring public safety and economic and national security (see Cybersecurity Commission Includes Former Heads of NSA, NIST).
Exploring ways to strengthen the cybersecurity workforce is only one component of the commission's charter. In developing its recommendations, the commission will identify and study advances in technology, management and IT service delivery that should be developed, widely adopted or further tested throughout the government and private sector.
- Details
- Category: Security News
×Close
Request to Republish Content
More Articles …
Page 3502 of 3546
