- Details
- Category: Security News
In planning for the aftermath of a data breach, many organizations focus on the obvious: the theft of personally identifiable information, including Social Security numbers; payment data and health information. In determining the cost of breaches, enterprises often concentrate on customer notification, credit monitoring and the possibility of legal judgments or regulatory penalties.
But a new study by the business advisory firm Deloitte & Touche - Beneath the Surface of a Cyberattack: A Deeper Look at Business Impact - contends these factors represent about 3.5 percent of the total breach costs.
"The costs that are commonly associated with cyberattacks and data breaches really end up being a small fraction of the overall impact," Emily Mossburg, principal in Deloitte's advisory cyber risk service, says in an interview with Information Security Media Group (click on player beneath image to listen). "Typically, based upon the model we put together, over 90 percent of the cost and the impact tend to be those things that are less tangible and often less discussed. What we really think this means is that it's not necessarily, 'OK, open eyes, this is costing more than you think.' It's more about you truly identifying the risk that are the most important to your organization."
In the interview, Mossburg discusses two scenarios Deloitte created that outline the multimillion dollar impact breaches have on two fictitious companies:
A health insurer with 50,000 employees and annual revenue of $60 billion that fell victim to a stolen laptop computer containing nearly 3 million patient records. A technology manufacturer with 60,000 workers and $40 billion in annual revenue that experienced a cyberattack from a nation-state.Mossburg contends these scenarios should help instruct organizations to understand the deep impact data breaches have on organizations.
Deloitte, in its report, itemizes 14 cyberattack impact factors, half of them with commonly known costs, the other half having hidden or less visible, but significantly higher costs.
 Source: Deloitte & Touche
Source: Deloitte & ToucheMossburg leads the resilient portion of Deloitte & Touche's cyber risk services portfolio, including the technical and organizational aspects of technology resilience, cyber incident response and post-incident crisis management for rapid recovery of operations, valuation and reputation. She has served a range of clients in the areas of technology risk management, data protection, data breach management and technology resilience, most recently focused on financial services and federal sectors.
- Details
- Category: Security News
Data Breach , Forensics , Governance
Did Russia - or Russian-Built Malware - Hack the DNC? Hack Attack Attribution: The Devil Is in the Details
Attributing attacks back to the responsible individual or group, and whoever might have sponsored them, is incredibly difficult. So is attempting to deduce a motive.
See Also: 2016 State of Threat Intelligence Study
That's my reaction to the June 20 headline on a Washington Post story: "Cyber researchers confirm Russian government hack of Democratic National Committee."
The story follows Dmitri Alperovich, CTO of cybersecurity firm CrowdStrike, announcing last week that his firm's investigation into a breach of the Democratic National Committee's systems had been perpetrated by two advanced persistent threat groups. The company refers to them as Fancy Bear, a.k.a. APT 28 in FireEye parlance, and Cozy Bear, a.k.a. APT 29. Both have been described as Russian APT groups by multiple security firms (see Report: Russia's 'Best' Hackers Access DNC's Trump Research).
"Our team considers them some of the best adversaries out of all the numerous nation-state, criminal and hacktivist/terrorist groups we encounter on a daily basis," Alperovich says in his blog post.
In the wake of the hack, the DNC said in a statement that no financial, donor or other sensitive personal information was stolen.
After obtaining samples of the malware recovered from the DNC systems, via CrowdStrike, Fidelis Cybersecurity has concurred with CrowdStrike's malware assessment. "Based on our comparative analysis we agree with CrowdStrike and believe that the Cozy Bear and Fancy Bear APT groups were involved in successful intrusions at the DNC," Fidelis says in a blog post. "The malware samples contain data and programing elements that are similar to malware that we have encountered in past incident response investigations and are linked to similar threat actors."
How security firms name two attack groups. (Source: Fidelis Cybersecurity)
APT 28, called GRU by German intelligence, is a state-sponsored Russian hacking group, according to Thomas Rid, a professor in the Department of War Studies at King's College London.
How Many Hackers Were Involved?
But these malware-based assessments have left some big questions unanswered. For starters, some security watchers have noted, if the individual or group behind the DNC hack was a group of elite Russian hackers, it's highly unlikely they would have left any tracks.
In addition, a supposed lone hacker - named "Guccifer 2.0" - claims to have breached the DNC and released not just an alleged DNC report on presumptive Republican presidential candidate Donald Trump, but also an Excel spreadsheet that appears to list donors. Trump has dismissed the hack attack report, claiming that the leak was intentionally done by the DNC.
On June 21, Guccifer 2.0 released an alleged DNC dossier that compiles criticism of presumptive Democratic presidential nominee Hillary Clinton.
#Guccifer2 Dossier on #HillaryClintonhttps://t.co/LGcRb1spRN pic.twitter.com/qweBMKR1Qg
Does Malware Equal Motive?
Aleks Gostev (a.k.a. "codelancer"), a chief security researcher at Kaspersky Lab, notes that while multiple security firms agree on the malware discovered on the DNC's systems, they couldn't prove who had used it. He added that unlike most other supposedly nation-state sponsored APT groups in the world, APT 28 and APT 29 unusually continued to use the same attacks and infrastructure after they'd been outed.
Typical behavior for most of current APT groups after public disclosure:1) Infrastructure cleanup and shutdown 2) Old tools never used again
Typical behavior for APT28/APT29 (attributed as most powerful intels): 1) Re-use of infrastructure 2) Sill using old tools
One obvious possibility, of course, is that Cozy Bear and Fancy Bear weren't the only hacking groups enjoying access to the DNC's network, and that the discovery of their malware simply doesn't tell the full story. But it's also a reminder that just because malware has been recovered, that doesn't make it clear who used it.
Does Attribution Matter?
The question of whether Russians or the Russian government hacked the DNC - and leaked related information - has revived the long-running debate over whether attribution matters, at least to anyone who's not part of a government agency.
Some security experts, vendors and firms that specialize in attribution argue that, indeed, attribution matters because it can help firms sharpen their information security defenses and repel the latest generation of attacks.
But others allege that attribution too often gets abused, especially by groups or governments that have a political or profit motive (see Ransomware Report: Is China Attribution Merely Hype?).
Jeffrey Carr, CEO at cybersecurity firm Taia Global, has accused firms that sell attribution services of too often having "confirmation bias" when it comes to ascribing attacks to particular nation states. For example, he says in a blog post that in a comprehensive report into APT 28 released in 2014 by FireEye, the authors "declared that they deliberately excluded evidence that didn't support their judgment that the Russian government was responsible for APT 28's activities," including targets that didn't appear to line up with typical nation-state APT group behavior.
"Had FireEye published a detailed picture of APT 28's activities including all of their known targets, other theories regarding this group could have emerged; for example, that the malware developers and the operators of that malware were not the same or even necessarily affiliated," Carr says.
This debate is a further reminder that organizations are perhaps best served by first ensuring they can block as many hack attacks as possible, for example, by complying with the Defense Department of Australia's "Top 4 Mitigation Strategies to Protect Your ICT System." Australia's Cyber Security Operations Center claims the four strategies will prevent 85 percent of all intrusions, no matter whether they're launched by a cybercrime group, advanced persistent teenagers or even attackers wielding APT malware, whoever they might be.
- Details
- Category: Security News
Fraud , ID Theft , Technology
Bill Aims to Help Reduce Identity Theft, Fraud Affecting Veterans Sen. Tammy Baldwin, D-Wis.
Sen. Tammy Baldwin, D-Wis.A bipartisan Senate bill proposes removing Social Security numbers of U.S. veterans from all Department of Veterans Affairs' information systems within the next five years in an effort to reduce identity theft and fraud.
See Also: Secure, Agile Mobile Banking: Keeping Pace with Last Best User Experience
The Veterans' Identity Theft Protection Act was introduced on June 16 by Sen. Tammy Baldwin, D-Wis., and is co-sponsored by Sen. Jerry Moran, R-Kansas.
"Our veterans should never be put at risk of identity theft with information that they have entrusted to the VA," Baldwin said in a statement. "That is why I am bringing this bipartisan solution forward to make certain that the VA stops using Social Security numbers to identify our veterans."
The bill would require the VA, the nation's largest healthcare provider, to discontinue the use of Social Security numbers with new claims for benefits within two years, and for all other veterans whose data is already in VA systems within five years. The VA, however, would still be permitted to use Social Security numbers if it needs to exchange information with another system outside of the agency that requires the use of those identifiers.
Other Efforts
The proposed bill isn't the first call for Social Security numbers to be eliminated as identifiers in various federal programs in an effort to reduce identity theft and fraud. But other proposals primarily have focused on dropping Social Security numbers from government-issued ID cards.
For instance, the Government Accountability Office had repeatedly over several years recommended that Social Security numbers be eliminated from Medicare beneficiary ID cards before President Obama signed a bill in 2015 that provides $320 million in funding to remove those numbers from the IDs within four years (see SSNs to Disappear from Medicare Cards).
The VA is in the process of removing Social Security numbers from veterans' healthcare ID cards. Instead, new cards display an Electronic Data Interchange Personnel Identifier as their member ID on the front of the card. That Department of Defense internal identification number for veterans is also embedded in the card's magnetic stripe and barcode (see VA Issuing New ID Cards to Fight Fraud).
Also, in June 2011, the DoD completed efforts to replace almost 10 million military identification cards that had Social Security numbers printed on them with cards that stored the numbers in bar codes. DoD is also working to remove the numbers from the barcodes and magnetic stripes on the cards.
The VA on its website says it has "significantly reduced the unnecessary collection and use of SSNs as the department's primary identifier." Social Security numbers were either removed completely or truncated to the last four digits on most VA correspondence, and the identifier no longer appear on any VA prescription labels, bottles, or mailing labels, the agency says.
Those efforts by the VA, however, don't necessarily address the kinds of problems that prompted Baldwin to craft the proposed legislation. In her statement, Baldwin says the bill aims to prevent the type of mishap that occurred in early 2015 when Social Security numbers of hundreds of Wisconsin veterans were accidentally emailed by a VA employee to an unauthorized person. "This unintended disclosure of personal information put veterans and their families at risk for fraud and identity theft," she said.
The VA did not immediately respond to an Information Security Media Group's request for comment.
Good Idea, But is it Doable?
Mac McMillan, a former information security leader at the DoD who is currently CEO of security consultancy CynergisTek, says phasing out all use of Social Security numbers at the VA "eliminates at least one avenue where it can be compromised. But we need to understand that the SSN is still used for many, many different purposes."
Nevertheless, the legislation could prove troublesome to implement, McMillan says.
"If they come up with the replacement process for identification, it will be relatively easy for new veterans, but I think purging the system of all references to SSN for us older veterans may not be so simple," he says. "I would imagine it will be fairly costly endeavor. It's not going to be as simple as search and replace I'm sure."
A spokesperson for Baldwin tells ISMG: "We don't have an estimate of the cost because the VA refused to provide feedback; we've been asking since March."
In potentially replacing Social Security numbers for identifying veterans in VA IT systems, McMillan says, "any unique identifier will do, but I'd like to see one tied to other information about the veteran for authentication purposes and ... at least one additional factor used to access it."
The consultant also says it will prove challenging for the VA to carry out the bill's provision permitting it to use Social Security numbers if it needs to exchange information with another system outside of the VA that requires the use of those identifiers.
"If those other systems rely on the SSN ... for their identification purposes, removing it from one could break processes in the other," he says. "This is not a trivial matter and one of the big reasons I think this will not be easily or cheaply done."
The Baldwin spokesperson says the bill has been referred to the Senate Veterans Affairs Committee.
- Details
- Category: Security News
DDoS , Events , InfoSecurity Europe 2016
Cybercrime Services Plus Social Engineering Equals Payday, Akamai WarnsWhile police continue to arrest distributed denial-of-service attack extortion suspects, such attacks have nevertheless continued.
See Also: Unlocking Software Innovation with Secure Data as a Service
One such arrest occurred in December 2015, when police in Bosnia and Herzegovina collared two individuals suspected of being involved in the high-profile extortion group DDoS for Bitcoin (see Europol Announces DD4BC Arrests). Many security experts suspect that DD4BC members also launched attacks using the "Armada Collective" moniker.
But other criminals have been moving in to exploit related shakedown opportunities, using attacks and tactics that may have no outwardly different appearance (see Akamai: Beware of Copycat Extortionists).
"Since [the arrests], there's also been a wave of copycats, who send letters that are either very similar or exactly the same as what 'DD4' and Armada were sending," says Martin McKeay, a senior security advocate at Akamai. "But most of these copycats either don't have the capabilities of the attacks, which were at most 50 gigabits, or they just don't have any capability, and they hope that people cave in and pay them some money and they walk away having done nothing other than sending a threatening email."
The façade is easy to maintain, McKeay says, because attackers can inexpensively rent so-called stresser or booter services to temporarily disrupt targets, as a taster, while threatening to make the disruptions a long-term affair (see How Do We Catch Cybercrime Kingpins?).
From a victim's standpoint, however, experts warn that giving any money to attackers can lead to criminals coming back and demanding more (see Cyber Extortion: Fighting DDoS Attacks).
In this interview with Information Security Media Group conducted at the Infosec Europe conference in London, McKeay describes:
The latest DDoS extortion tactics; How stresser/booter services are becoming increasingly commoditized; Best practices for defending against DDoS attacks.McKeay is a member of Akamai's security intelligence team. Previously, he was a senior consultant at both Verizon Business and TrustWave, a product evangelist at StillSecure and a PCI quality security assessor and incident responder. He's a frequent speaker at information security conferences, having delivered presentations at AusCERT, BSides San Francisco, Hong Kong InfoSecurity Summit and RSA.
- Details
- Category: Security News

The U.S. Securities and Exchange Commission has obtained an emergency court order to freeze the assets of a British citizen who it has accused of hacking into brokerage accounts in the United States and abroad to manipulate and fraudulently profit from stock price fluctuations that he engineered.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
On June 22, the SEC filed a complaint in the U.S. District Court in the Southern District of New York, alleging that Idris Dayo Mustapha "hacked into numerous accounts of U.S. customers of broker-dealers in and outside the U.S." He's been accused of violating federal security laws' anti-fraud provisions. The SEC says it's seeking permanent injunctions; return of allegedly ill-gotten gains, with interest; as well as financial penalties.
Mustapha's scheme earned him profits of at least $68,000, according to the SEC's complaint, and led to at least $289,000 in losses for the owners of the brokerage accounts into which he allegedly hacked.
Judge Alison J. Nathan granted the SEC's request to freeze approximately $100,000 in Mustapha's assets and ordered him to not destroy evidence. The SEC, in its complaint, says it's still gathering evidence related to how Mustapha allegedly hacked into victims' accounts.
The SEC, which enforces U.S. securities laws and oversees the nation's stock and options exchanges, cannot file criminal charges, but it can file complaints and refer cases to federal or state prosecutors.
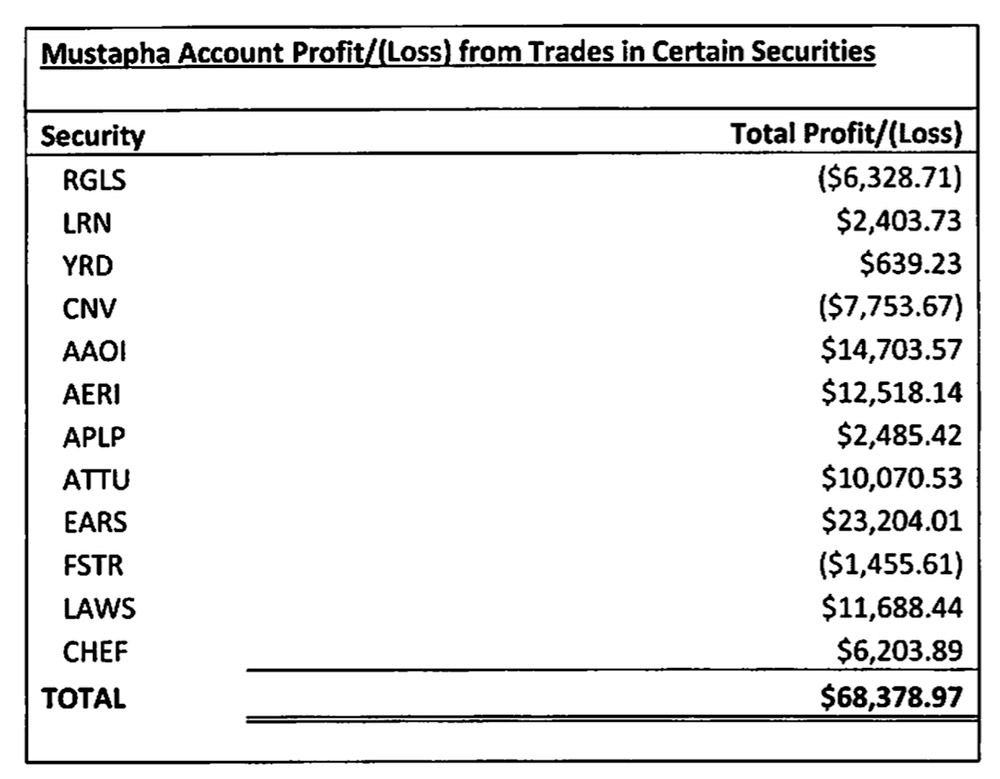 Profits and losses via Mustapha's alleged short-selling scheme of the listed stock symbols. (Source: SEC complaint against Idris Dayo Mustapha.)
Profits and losses via Mustapha's alleged short-selling scheme of the listed stock symbols. (Source: SEC complaint against Idris Dayo Mustapha.)
Where is Mustapha?
Authorities do not appear to know Mustapha's whereabouts; the government says it plans to issue a summons for him to appear in court via the email address used to register his brokerage account, as well as by delivering a letter to his brokerage firm, which it hopes will communicate the summons to him.
Between February and May, according to the complaint, Mustapha hacked into accounts owned by five customers of an unnamed U.S. brokerage firm, as well as four customers of two unnamed foreign brokerage firms.
The SEC says in its court filings that the allegations against Mustapha are the result of an "expedited investigation" and that it's continuing to analyze other profits in Mustapha's U.S. brokerage account to see if they tie to fraudulent activity.
The agency says the alleged fraud could be even more wide-reaching. "Mustapha used sophisticated and deceptive means to orchestrate the account intrusions and unauthorized trading, which constitute securities fraud," the SEC says in its complaint. "The commission has been able to link Mustapha to the account intrusions specifically identified in the complaint, but there is a substantial risk that he may be continuing his scheme through other brokerage accounts that the commission has not yet identified."
Anatomy of a Short-Selling Scheme
Mustapha is accused of hacking into one of the victim's accounts to increase the price of the stock of Lawson Products, trading as "LAWS," and then begin selling short the stock in his own brokerage account, according to the SEC's complaint. Short selling, or shorting, refers to selling shares that an individual doesn't own - but has been loaned by a brokerage - on the belief that the value of the stock will fall. After selling these shares and having the amount credited to their account, the trader later "closes" by buying the shares. If the price has fallen, they make a profit, while if it's risen, they must pay the difference.
"[One] way in which an investor can make a profit through a short sale is to engage in a fraudulent scheme intended to depress the stock price and then purchase the stock at the depressed price. That is what Mustapha did here," the SEC's complaint says.
Mark Albers, an SEC forensic accountant, details in a declaration to the court how a related series of May 17 trades, which occurred during the following U.S. Eastern times, unfolded:
1:33:26 p.m. to 1:34:49 p.m.: Victim account - without accountholder's authorization - purchased LAWS shares at prices that began at $18.99 per share, increasing to up to $19.49 per share, and accounted for about 12,779 shares of the approximately 13,779 LAWS shares traded at that time. 1:34:46 p.m. to 1:34:47 p.m.: Mustapha's brokerage account sold short at least 4,200 shares of LAWS stock at $19.49 per share. 1:39:10 p.m. to 1:40:00 p.m. The victim account sold 8,000 shares of LAWS at prices that decreased from $19.05 to $18.71. 1:41:20 p.m. to 1:41:24 p.m.: The Mustapha account purchased LAWS stock for about $18.75 per share.As a result of the trades - which accounted for 78 percent of all LAWS shares traded that day - Albers says Mustapha's account profited $11,688 from the short selling, while the victim's account lost $48,218.
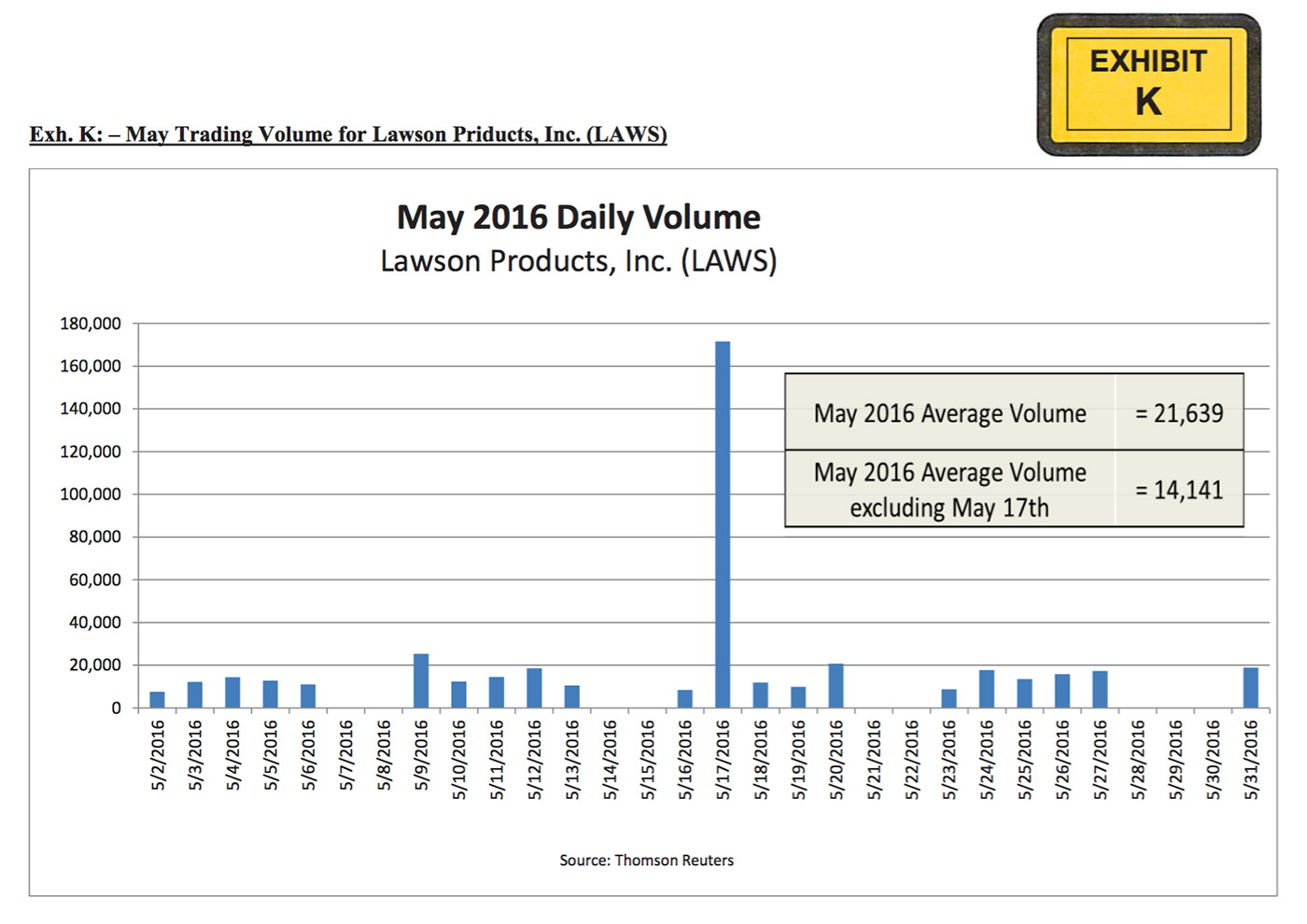 Daily trading volume for LAWS stock. (Source: SEC complaint against Idris Dayo Mustapha.)
Daily trading volume for LAWS stock. (Source: SEC complaint against Idris Dayo Mustapha.)
"Mustapha accessed the [victim's] account ... on May 17, 2016, with an IP address that was an 'anonymizer,' or an anonymous proxy tool, to mask his true originating IP address," according to the SEC's complaint. The complaint doesn't detail how the SEC traced the anonymizer to Mustafa, but it suggests that the agency may have subpoenaed or otherwise obtained related records from the unnamed anonymous proxy service.
The same computer MAC address was used to access both Mustapha's brokerage account as well as many of the victim accounts, Albers says.
$9 Million Put at Risk
The nine victims of Mustapha's alleged trades that the SEC has identified to date collectively lost at least $289,400 as a result of unauthorized trades, which also put $9 million of the account holders' capital at risk, Albers says.
Between March 11 and May 13, 11 transfers - totaling $109,000 - were made from a brokerage account registered in Mustapha's full name to a U.S. bank account registered in his full name, Albers adds, noting that they appeared to be fraudulently obtained profits. Subsequently, $12,000 was transferred, and in late May, an attempt to also transfer $25,000 was made.
The SEC's related investigation is ongoing.
More Articles …
Page 3449 of 3546

