- Details
- Category: Security News
For years, organizations have been threatened by DDoS attacks on several fronts, ranging from volumetric attacks to application-level and DNS strikes. Now come ransom-based attacks. Trey Guinn of CloudFlare discusses how to respond to each type of attack.
Ransom-based attacks are in the spotlight now, but Guinn - head of solution engineering at CloudFlare - has discovered an interesting disconnect.
"There are more attackers sending out ransom notes than are actually doing attacks," Guinn says. "We have seen many of these ransom notes go out, but it's clear in how [the attackers] receive payment that they have no way to determine who actually has paid the ransom. There is no expectation that there is ... going to be an attack."
The message to security leaders, then, is crystal clear, he says: "Never pay the ransom."
In a discussion about matching DDoS defenses to DDoS attacks, Guinn talks about:
Types of DDoS attacks most predominant today; How mitigation techniques must match the types of attacks; How to respond specifically to ransom-based attacks.Guinn leads the enterprise solution engineering group at CloudFlare, where he works with large customers to help them manage their network edge. His work focuses on TLS, DDoS mitigation, web application firewalls, HTTP and DNS.
He has worked in internet application delivery for over 15 years in small and large companies in several countries - from multinationals like KPMG to one room startups. Security is a continual focus of his career (as it should be for every engineer) with work ranging from network security to identity management.
- Details
- Category: Security News
Events , InfoSecurity Europe 2016
12 Sights: Infosec Europe 2016 Visual Highlights from Europe's Biggest Cybersecurity Event London's Olympia exhibition center hosted this year's conference.
London's Olympia exhibition center hosted this year's conference.The recent Infosecurity Europe 2016 conference in London drew attendees from more than 70 different countries. The free conference, which is Europe's largest cybersecurity event, spanned three days, and featured a variety of well-known information security luminaries delivering keynote presentations and participating in panel discussions.
See Also: Vulnerability Management with Analytics and Intelligence
Here are 12 visual highlights from the event:
 Opened as the National Agricultural Hall in 1886 - three years before the Eiffel Tower - the Olympia, located in London's Kensington district, features a wrought iron and glass shell.
Opened as the National Agricultural Hall in 1886 - three years before the Eiffel Tower - the Olympia, located in London's Kensington district, features a wrought iron and glass shell.
 The Olympia spans two levels, with the upper level hosting more than 100 exhibitors as well as the keynote presentations.
The Olympia spans two levels, with the upper level hosting more than 100 exhibitors as well as the keynote presentations.
 Mikko Hypponen, chief research officer of F-Secure, delivered an opening keynote presentation on top cybercrime trends.
Mikko Hypponen, chief research officer of F-Secure, delivered an opening keynote presentation on top cybercrime trends.
 Nearly 350 organizations - from security vendors and consultancies to governmental organizations and professional associations - exhibited at this year's conference.
Nearly 350 organizations - from security vendors and consultancies to governmental organizations and professional associations - exhibited at this year's conference.
 Hot topics at this year's conference ranged from ransomware, cybercrime, breach avoidance, supercomputers, the latest research, as well as discussions about why so many simple security problems just can't seem to get solved.
Hot topics at this year's conference ranged from ransomware, cybercrime, breach avoidance, supercomputers, the latest research, as well as discussions about why so many simple security problems just can't seem to get solved.
 The conference drew what organizers estimated to be more than 15,000 attendees, offering ample opportunities for not just free swag, but also networking.
The conference drew what organizers estimated to be more than 15,000 attendees, offering ample opportunities for not just free swag, but also networking.
 Vendors deployed the usual array of booth enticements to attract visitors, ranging from free lightsabers and notepads to the chance to win a drone or beat an opponent at a modified form of whack-a-mole (pictured).
Vendors deployed the usual array of booth enticements to attract visitors, ranging from free lightsabers and notepads to the chance to win a drone or beat an opponent at a modified form of whack-a-mole (pictured).
 With outside temperatures soaring in London, and the glass-roofed Olympia not offering state-of-the-art air conditioning, attendees snapped up cool freebies, ranging from beer at daily happy hours to ice cream and sorbet.
With outside temperatures soaring in London, and the glass-roofed Olympia not offering state-of-the-art air conditioning, attendees snapped up cool freebies, ranging from beer at daily happy hours to ice cream and sorbet.
 More than 260 speakers presented this year in keynote presentations, panel discussions as well as smaller technology talks.
More than 260 speakers presented this year in keynote presentations, panel discussions as well as smaller technology talks.
 Keynote presentations occasionally turned personal, for example, when Hypponen revealed that he too had been pwned in the LinkedIn 2012 breach.
Keynote presentations occasionally turned personal, for example, when Hypponen revealed that he too had been pwned in the LinkedIn 2012 breach.
 Familiar symbology - as in this demonstration of an attack/defense training program offered by U.K. security firm Satisnet - featured heavily, if at times unsubtly, at the the conference.
Familiar symbology - as in this demonstration of an attack/defense training program offered by U.K. security firm Satisnet - featured heavily, if at times unsubtly, at the the conference.
 Only a handful of hoodie-wearing hackers, sadly forced to stand facelessly in the London rain, appeared at this year's event.
Only a handful of hoodie-wearing hackers, sadly forced to stand facelessly in the London rain, appeared at this year's event.
- Details
- Category: Security News
Encryption , Endpoint Security , Privacy
Apple Promises 'Differential Privacy' Security, Privacy Upgrades Follow FBI's Attempted Crypto Smackdown Apple CEO Tim Cook addresses WWDC 2016. (Source: Apple)
Apple CEO Tim Cook addresses WWDC 2016. (Source: Apple)Apple wants to sell you on "differential privacy."
See Also: How to Mitigate Credential Theft by Securing Active Directory
That's one of the security and privacy-related announcements made by Apple at its Worldwide Developer Conference this week.
Apple uses the annual event to preview forthcoming software and hardware for developers, and this year's event included a number of interesting-looking announcements, ranging from building Siri into Apple's desktop operating system and extending Apple Pay to websites, to an upgraded Home app to control your personal Internet of Things and better facial recognition for photos.
On the crypto front, with OS X 10.12 - code-named Sierra - that's due out next year, Apple's all-new Apple File System, a.k.a. APFS, will feature native encryption capabilities. AFPS will run on everything from Apple's watches and televisions to laptops and desktops, and allow developers to use single-key or multi-key encryption to protect data, even if devices' physical security gets compromised.
But amongst all of the announcements, one of the most puzzling is surely the promise of incorporating "differential privacy" into iOS 10, which Apple watchers expect to be released in September.
Promise: Privacy at Scale
Craig Federighi, Apple's senior vice president of software engineering, told the WWDC audience that on the iOS privacy front, Apple already attempts to do as many computations as possible on the device, and also uses end-to-end encryption for all iMessage and FaceTime messages.
Going forward, however, Apple says it wants to offer what amounts to privacy at scale, for example to spot patterns in how users are searching online, make better suggestions via the 'QuickType' keyboard or offer related links.
 Craig Federighi, Apple's senior vice president of software engineering, talks differential privacy at WWDC 2016.
Craig Federighi, Apple's senior vice president of software engineering, talks differential privacy at WWDC 2016.
"We believe you should have great features and great privacy," Federighi told the WWDC crowd. "Differential privacy is a research topic in the areas of statistics and data analytics that uses hashing, subsampling and noise injection to enable this kind of crowdsourced learning while keeping the information of each individual user completely private."
Differential privacy essentially means collecting two different sets of data - one that includes your personal information, and one that has it stripped out - and ensuring that the latter data set is good enough to work with, says Johns Hopkins University cryptography professor Matthew Green in a blog post (see Top 10 Data Breach Influencers). He adds that differential privacy can be improved if random noise gets added to the mix.
The Usual Secret Sauce
What's unclear so far, however, is how Apple will be implementing this system, and whether it will stand up to security researchers' scrutiny, although Apple says it's vetted its approach with Aaron Roth, a professor at the University of Pennsylvania computer science department, who's literally written a book on differential privacy.
"With a large dataset that consists of records of individuals, you might like to run a machine learning algorithm to derive statistical insights from the database as a whole, but you want to prevent some outside observer or attacker from learning anything specific about some [individual] in the data set," Roth tells Wired. "Differential privacy lets you gain insights from large datasets, but with a mathematical proof that no one can learn about a single individual."
Some other researchers say they are waiting to see full details relating to how Apple has implemented its system before pronouncing it effective or not. "Unfortunately Apple isn't known for being terribly open when it comes to sharing the secret sauce that drives their platform, so we'll just have to hope that at some point they decide to publish more," Johns Hopkins' Green says.
On the upside, however, Apple didn't have to do this, Green says, adding that any moves in this direction offer reason for cautious optimism. "It sure looks like Apple is honestly trying to do something to improve user privacy, and given the alternatives, maybe that's more important than anything else," he says.
Life After the Apple-FBI Crypto Fight
Of course, it's impossible to view Apple's differential privacy move without making reference to one of the potential catalysts: the Snowden revelations. Those began three years ago, and have revealed mass surveillance campaigns being conducted by U.S. and U.K. intelligence agencies, programs designed to crack or suborn Apple operating systems - both OS X and iOS - as well as attempts by intelligence agencies to exploit even minor weaknesses to track or spy on targets.
Earlier this year, meanwhile, the U.S. Justice Department attempted to force Apple to create a version of iOS that would allow the FBI to access the contents of an iPhone that had been issued to San Bernardino shooter Syed Rizwan Farook. Apple CEO Tim Cook vowed that Apple would fight the "dangerous" move, and the FBI ultimately backed off, although experts say related legal battles have only been temporarily deferred (see Silicon Valley: Crypto Debate Continues). In the interim, the world's largest technology company shows no signs of slowing down on its promise to deliver devices that provide greater levels of privacy and security for users.
- Details
- Category: Security News
Audit , Governance , Risk Assessments
Watchdog Urges Four Agencies to Improve Implementation of Access Controls GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.
GAO's Greg Wilshusen calls on U.S. agencies to toughen access controls.A government watchdog warned four federal agencies that they must be more diligent in implementing their cybersecurity programs. Otherwise, some of the government's most sensitive information is at risk of being disclosed to unauthorized individuals.
See Also: 2016 State of Threat Intelligence Study
Although NASA, the Nuclear Regulatory Commission, the Office of Personnel Management and the Department of Veterans Affairs developed risk assessments for their high-risk systems, they have all been inconsistent in their implementation of access controls, according to report released June 21 by the Government Accountability Office, the investigative arm of Congress.
GAO also says the four agencies have weaknesses in patching software vulnerabilities and planning for contingencies because they didn't fully implement key parts of their information security programs.
Gregory Wilshusen discusses the findings of the GAO audit of four federal agencies."Until the selected agencies address weaknesses in access and other controls, including fully implementing elements of their information security programs, the sensitive data maintained on selected systems will be at increased risk of unauthorized access, modification and disclosure, and the systems at risk of disruption," Gregory Wilshusen, GAO director of information security issues, says in the report.
Audit Sought by Congressional Overseers
GAO surveyed 18 federal agencies that store and process high-impact information, which the National Institute of Standards and Technology defines as having a severe or catastrophic adverse effect on operations, assets and individuals if compromised.
The leaders of the Senate Homeland Security and Government Affairs Committee, which provides government IT security oversight, requested GAO study how federal agencies protect high-impact data. The request came after the breach of Office of Personnel Management computers that exposed the personal information of at least 21.5 million individuals, many of them holding security clearances (see Nominee Explains OPM's Recovery from Massive Breach).
During the fiscal year that ended Sept. 30, 2014, 11 of the 18 agencies GAO surveyed reported 2,267 incidents affecting their high-impact systems, with nearly 500 of the incidents involving the installation of malware. Of the federal government's 9,714 information systems in the 24 agencies covered by the Chief Financial Officers Act, 912 of them - or 9 percent - are deemed high impact.
The audit also revealed that the attacks delivered through email were deemed the most serious and frequent.
Most Serious, Frequently Identified Cyber Threat Vectors
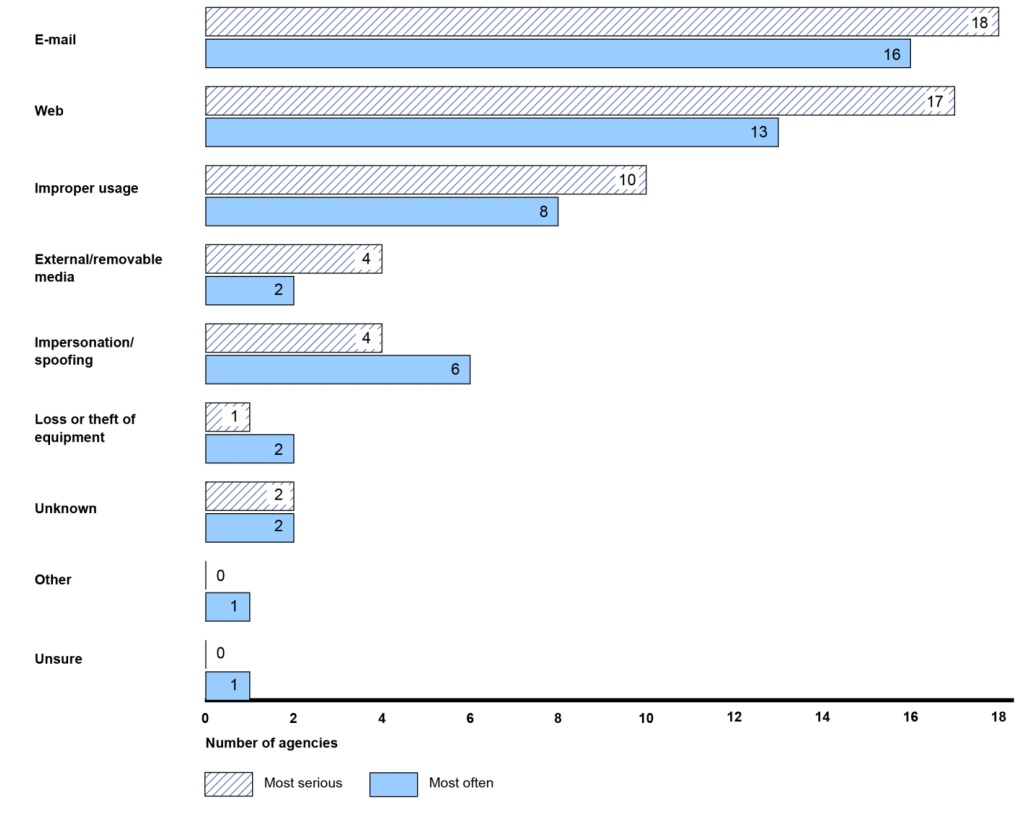 Source: GAO
Source: GAOGAO also recommended that the Office of Management and Budget, the White House organization that oversees federal agencies IT security, complete its plans and practices for securing federal systems, known as the Cybersecurity Implementation Plan (see Federal Cybersecurity Strategy Revised).
The auditors called on NASA, NRC, OPM and VA to fully implement key elements of their information security programs. The agencies generally concurred with GAO's recommendations, with the exception of OPM.
Pushback from OPM
OPM did not concur with the recommendation regarding evaluating security control assessments. David Vargas, OPM's associate CIO, says GAO failed to provide enough information to fully respond to the recommendation. But GAO contends it briefed OPM staff on its technical findings nearly two months before OPM was required to respond to a draft of the audit.
GAO also recommended that OPM provide and track specialized training for all individuals, including contractors, who have significant security responsibilities. Vargas says OPM concurs with the intent of that recommendation, but disagrees on the approach GAO suggests. He says the OPM system audited by GAO was owned and operated by a contractor, which he considers a crucial point.
"It is more appropriate and efficient for OPM to monitor IT training requirements for contractors without access to OPM's network through contractor audits and oversight, as opposed to directly providing and tracking those individuals' training," Vargas says in his response to the GAO recommendation. "OPM's IT security office currently conducts annual site visits on a sample of contractors each year and is working to improve the site assessment process to better align it to verify compliance with all the standard IT contract clauses, including those regarding contractor employee training."
The GAO study reveals how cyber threats affects the 18 agencies with high-impact systems. It shows that threats from nations and malicious insiders were the most serious. Threats posed by nations, unknown malicious outsiders and hackers/hacktivists occurred most often, as indicated, for example, by alerts or notifications.
Most Serious, Frequently Identified Adversarial Cyber Threat Sources
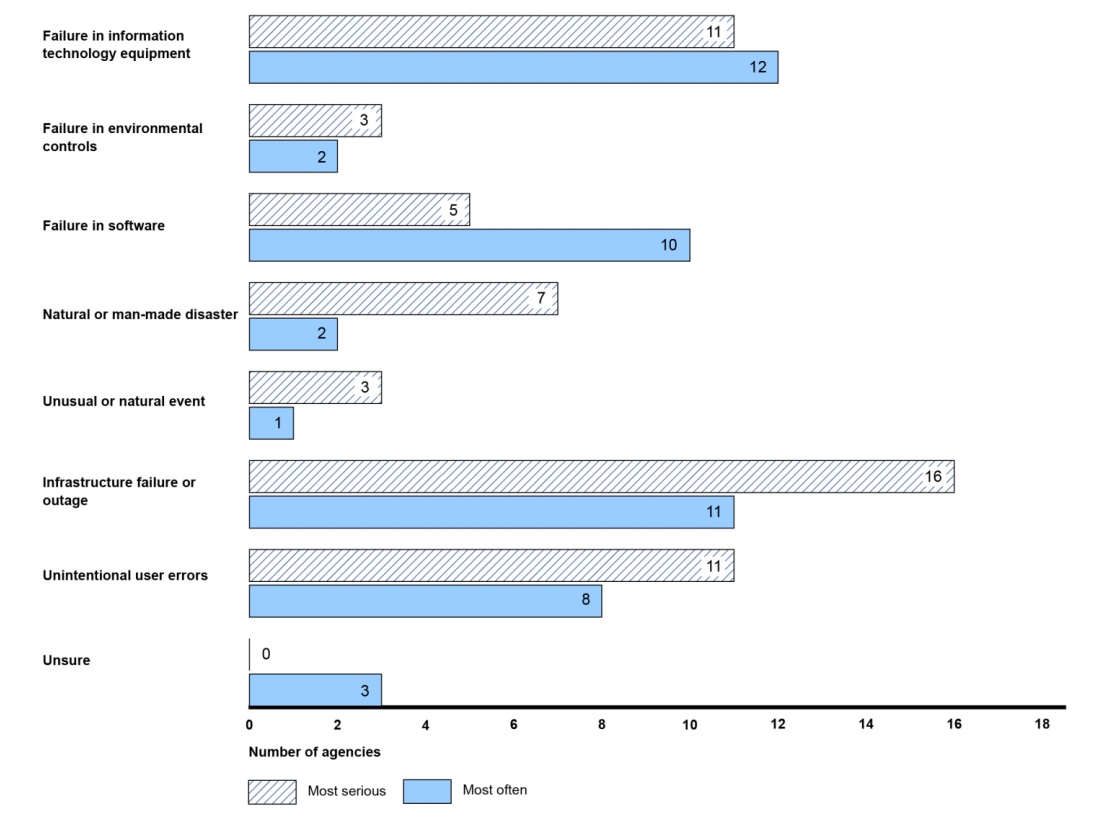 Source: GAO
Source: GAOThe agencies also reported that phishing and spear phishing proved to be the most serious and most frequently identified method of waging cyberattacks.
Most Serious, Frequently Identified Cyberattack Methods
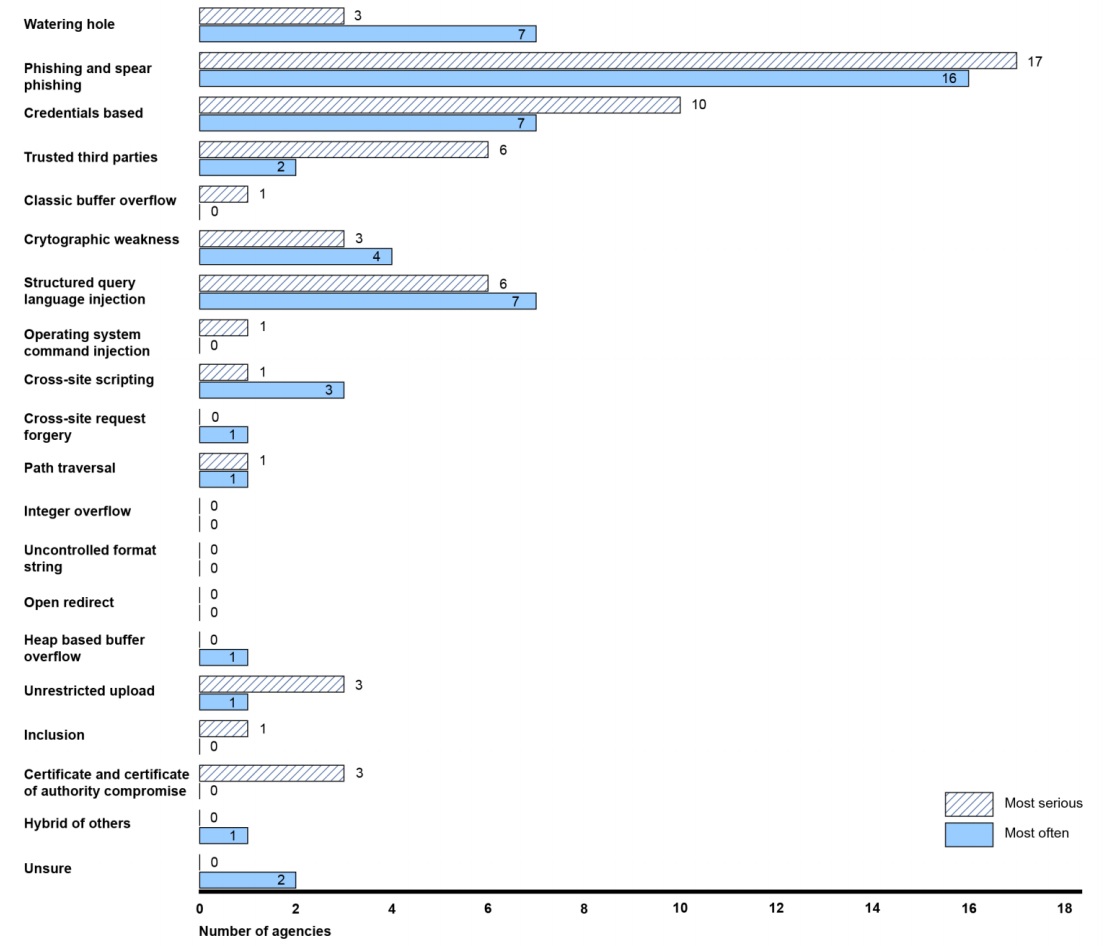 Source: GAO
Source: GAOThe 18 agencies with high-impact systems reported that they considered infrastructure failure or outage, failure in IT equipment and unintentional user errors to be the most serious non-adversarial threat sources that affect their high-impact systems.
- Details
- Category: Security News
Breach Preparedness , Data Breach , Fraud
Scrutiny Follows SWIFT-Focused Hack Attacks
The Office of the Inspector General has begun auditing the Federal Reserve's effectiveness when it comes to ensuring that U.S. banks have robust information security policies, procedures and practices in place, including the ability to quickly detect and respond to data breaches.
See Also: Unlocking Software Innovation with Secure Data as a Service
The "Audit of the Board's Oversight of Cybersecurity Threats to Financial Institutions" was announced June 20 as part of the latest OIG work plan.
"The growing sophistication and volume of cybersecurity threats presents a serious risk to all financial institutions," the OIG's work plan says. "We are focusing our review on how the Federal Reserve System's examination process has evolved and whether it is providing adequate oversight of financial institutions' information security controls and cybersecurity threats."
The Fed has already developed guidance for banks "to define expectations for information security and data breach management," the OIG reports. Now the watchdog agency will review how - and if - banks are complying with that guidance.
New @federalreserve #infosec evaluation (p. 3), other updates to our Fed & @CFPB Work Plan: https://t.co/uyM9wJZzya pic.twitter.com/Uqv6dYb7Y9
The audit is due to be completed in the fourth quarter of this year. The upcoming OIG report may be the first-ever public assessment of the Federal Reserve's effectiveness at ensuring that U.S. banks have sufficient cybersecurity controls in place, Reuters reports. Previous audits were limited to the cybersecurity practices of the Federal Reserve system itself.
Fed Breach Report
The OIG notes that part of its mission is to "focus on those programs and operations in which potential deficiencies pose the highest risk to the [Fed Reserve] Board and the CFPB."
On a related note, the OIG's information security questions follow a recent report from Reuters, noting that from 2011 to 2015, the Fed detected more than 50 data breaches involving its networks. That information was based on a Freedom of Information Act request filed by the news agency, which relates only to the Washington-based Board of Governors, which is a federal agency that is subject to public records laws, unlike the Fed's 12 privately owned regional branches.
When it comes to that breach report, "I'm not at all surprised," Avivah Litan, an analyst with Gartner Research, tells Information Security Media Group. "The Feds have all kinds of breach attempts on a daily basis. The question is, did any [successfully] exfiltrate sensitive information or money? My guess is that some were indeed successful but that's just an educated guess, based on what I have seen elsewhere."
Audit Follows SWIFT-Enabled Fraud
The OIG's probe also follows the February theft of $81 million from the central bank of Bangladesh's New York Federal Reserve account via the messaging service provided by Brussels-based SWIFT. Formally known as the Society for Worldwide Interbank Financial Telecommunication, SWIFT is a cooperative owned by 3,000 banks that bills itself as "the world's leading provider of secure financial messaging services." Today, 11,000 banks globally use SWIFT daily to process 25 million communications that collectively account for billions of dollars' worth of transfers.
The security of SWIFT's messaging system has been called into question after investigators reported discovering coordinated malware attacks against multiple banks. Based on a technical analysis of the malware used in those attacks, some security experts say they have a high degree of confidence that a group sponsored by the government of North Korea was behind the hacks.
While the attack campaign might have begun as early as 2013, the campaign only came to light after Bangladesh Bank disclosed its hack attack and related losses in March. At the time, it blamed the New York Fed and SWIFT for processing and routing the fraudulent transactions, although the Fed and SWIFT dismissed those accusations.
Last month, in a joint statement, the three organizations stopped their respective finger-pointing and pledged to work together. Subsequently, SWIFT also began issuing increasingly strong warnings to users, and urging them to ensure that all systems that touch the SWIFT network have strong security controls (see Banks With Bad Cybersecurity Could Face SWIFT Justice).
Congress Queries Fed
In the wake of the Bangladesh Bank hack, multiple nations began probing the security of SWIFT, as well as their own banking systems (see Banks, Regulators React to SWIFT Hack). In April, the U.K. central bank - the Bank of England - reportedly ordered all of the country's banks to detail how they were reacting to the SWIFT hack.
U.S. legislators have been asking the Fed if it plans to follow the Bank of England's lead, and whether U.S. banks could survive a similar attack. Last month, the House Committee on Science, Space and Technology launched a probe of the attacks, and asked the Fed specifically what it was doing to oversee banks' cybersecurity practices as well as SWIFT itself (see Fraudulent SWIFT Transfers: Congress Queries New York Fed).
Oversight of SWIFT is the responsibility of the 11 countries that are in the G10 - Belgium, Canada, France, Germany, Italy, Japan, the Netherlands, Sweden, Switzerland, the United Kingdom and the United States, with the National Bank of Belgium taking the lead role.
Other members of Congress have also been questioning the Fed's cybersecurity oversight, as well as the preparedness of U.S. banks to defend against related attacks. In March, for example, Rep. Carolyn B. Maloney, D-N.Y., requested further details on the Bangladesh Bank heist from the Fed, and the Fed responded in April.
Last month, Sen. Tom Carper, D-Del., the ranking Democrat on the Senate Homeland Security and Governmental Affairs Committee, likewise asked the New York Fed how it was responding to the bank heists.
Executive Editor Tracy Kitten also contributed to this story.
More Articles …
Page 3447 of 3546
