Cybersecurity , Data Breach , Risk Management
12 Top Cloud Threats of 2016- Details
- Category: Security News

An experimental investment fund based on the digital currency ethereum has been hacked, with about $55 million worth of the currency stolen, according to news reports.
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
Founders of the $150 million fund, known as the Decentralized Autonomous Organization, have shut it down in the wake of the June 17 hack and are planning for its unwinding, the Wall Street Journal reports.
The attackers stole about 3.6 million ethereum coins, valued at about $55 million, and moved it to another account, the newspaper reports.
In a June 17 blog post, Vitalik Buterin, a co-founder of ethereum, acknowledges "an attack has been found and exploited in the DAO."
The attackers appeared to have exploited a loophole that essentially allowed a DAO stakeholder to create an identical fund and move money into it, the Wall Street Journal reports. But the code also imposes a waiting period that means the new fund can't move any money for 27 days. The DAO's founders are planning to "fork" the code and effectively void the hacker's transactions, according to Buterin's blog. "DAO token holders and ethereum users should sit tight and remain calm," he says. "Exchanges should feel safe in resuming trading."
The attack didn't target the ethereum network, but only the DAO fund, according to the Wall Street Journal report.
Currency flawed?
But Philip Daian, a researcher at Cornell University's Initiative for Crytocurrencies & Contracts, contends that ethereum itself seems to be flawed, based on the latest developments in the DAO hack, Cryptocoins News reports. "I would lay at least 50 percent of the blame for this exploit squarely at the feet of the design of the Solidity language [used for ethereum]," the professor writes in a blog. "This may bolster the case for certain types of corrective action.
A notice purportedly from the attacker and addressed "to DAO and the ethereum community" was posted on June 18 on PasteBin.
The DAO was set up in May as an experiment in using digital currencies and self-operating digital contracts to create a venture capital fund that could run itself, the Wall Street Journal reports. But it was criticized early on for being poorly constructed, the newspaper reports.
Hackers have targeted several other cryptocurrency-related services, says John Nye, senior penetration tester at the security consulting firm CynergisTek.
"This particular case seems to be very similar to the one that happened in early 2014 to the Mt.Gox bitcoin exchange," he says. "The biggest thing to know in this case is it is not a case of a flaw in the blockchain or other security measures that are used by cryptocurrencies but was caused by a flaw in the security of the Decentralized Autonomous Organization."
The various forms of digital currency are specifically designed to be run in a decentralized manner with anonymity as a core tenant, Nye notes. "This means that organizations like DAO that hope to hold onto large sums of these funds have to take steps far beyond what a typical financial institution may have to take," he says. "These extra steps are needed because they are a very lucrative target for criminals, since if they can bypass the security controls of the organization holding the currency they can transfer it anonymously and there is nothing that the victims can do. This is a big risk for organizations like DAO and Mt.Gox because there is no FDIC or insurance they can employ to guarantee the recovery of funds lost."
- Details
- Category: Security News
Endpoint Security , Network & Perimeter , Technology
Security Experts See Surge in Malware Using JavaScript to Evade Defenses
After channeling horror films and holding control of smart TVs for ransom, the latest ransomware innovation du jour involves attackers crypto-locking files using nothing more than JavaScript code (see Malware, Ransomware Thrive Despite Criminal Prosecutions).
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
The JavaScript ransomware, which its developers named RAA, was discovered by two security researchers. One is known as JAMESWT_MHT, who's a member of a group that calls itself the Malware Hunter Team, while the other is benkow. The researchers flagged the malicious code via Twitter, noting that it appears to be "100 percent" written in JavaScript.
Because JavaScript doesn't include any strong cryptographic capabilities, the malware uses the CryptoJS library to forcibly encrypt a number of types of files using AES-256 encryption, then deletes the originals, the researchers tells technology blog BleepingComputer. The malware also searches for all external and network-attached drives to which the PC has access and can encrypt those too, the researchers say.
RAA also includes a version of the Pony malware embedded inside of it, which RAA also installs on an infected PC, according to an analysis of the malware published by ReaQta, a cybersecurity firm that was formed in 2014 by former employees of the Milan, Italy-based nation-state spyware shop Hacking Team.
While Pony can be used to download additional pieces of malware, for the RAA infection, it's also configured to steal passwords. "This malware can collect browser passwords and other user information from an infected machine and is usually used by hackers to gather critical information on infected systems," researchers from security firm Trend Micro say in a blog post. While Pony often uses behavior associated with banking Trojans, such as stealing access credentials for online accounts, at least to date, RAA's version of Pony doesn't appear to have been doing this.
After the ransomware encrypts files and reboots, Pony then gets executed, while end users see a ransom note written in Russian, according to ReaQta (see Please Don't Pay Ransoms, FBI Urges). "The ransomware asks for 0.39 bitcoins [$300] and due to the language of the refund information file, it's clear that the targeted country is Russia," ReaQta says.
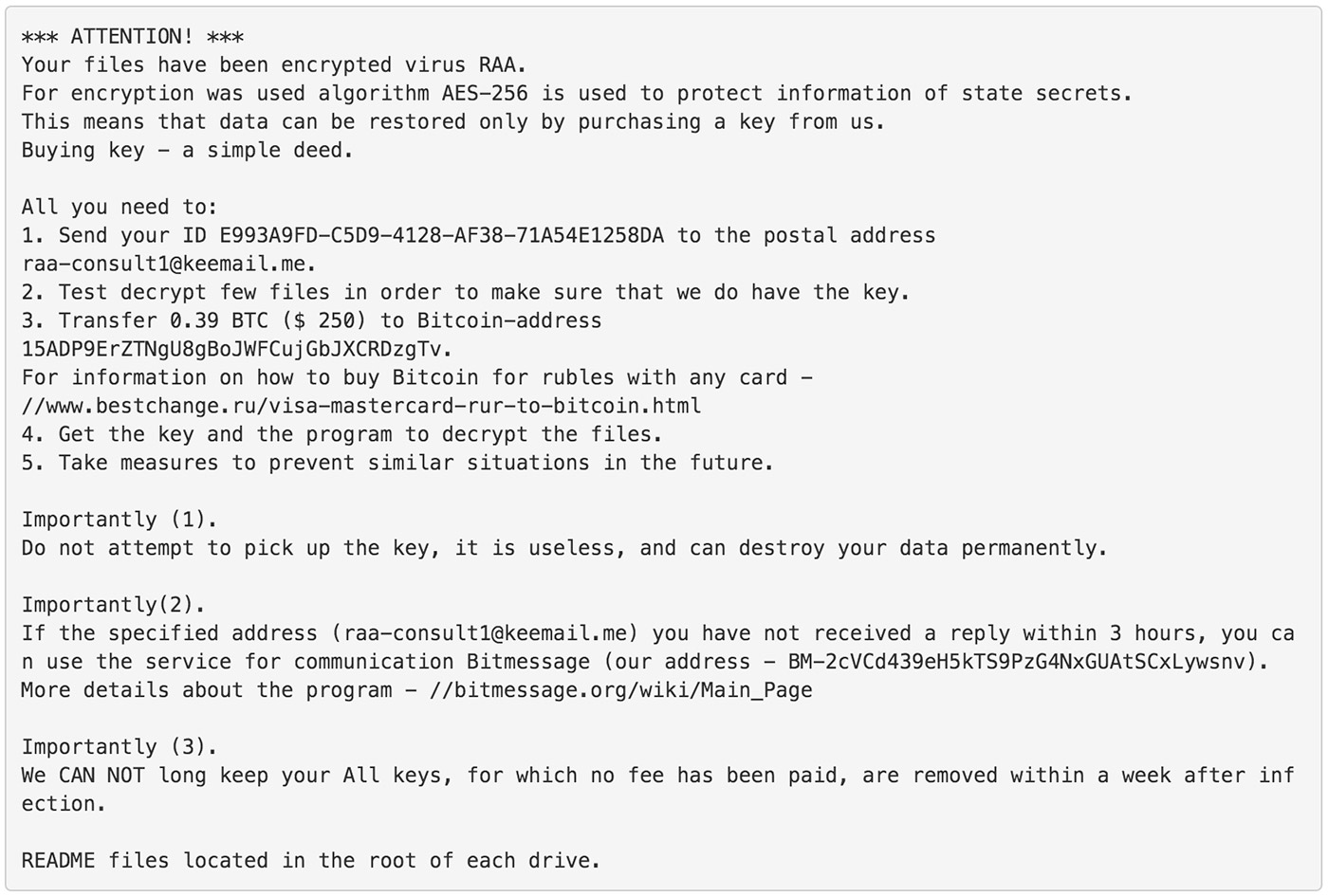 Ransom demand issued by RAA, which is 100% built from JavaScript. Ransom note translation (from Russian) source: BleepingComputer.
Ransom demand issued by RAA, which is 100% built from JavaScript. Ransom note translation (from Russian) source: BleepingComputer.
But as Trend Micro notes: "It's only a matter of time until it's distributed more widely and localized for other languages."
SANS Sounds Warning
The arrival of the JavaScript ransomware comes as the SANS Institute warns that it's seen an overall uptick in exploit kits using JavaScript to infect systems with malware.
"If the JavaScript arrives in an inbound email, and one of your Windows-based users clicks it, it doesn't execute in the browser; it executes inside of the Windows shell," says Rob VandenBrink, who's an Internet Storm Center handler for SANS, as well as a senior consulting engineer at drug and diagnostic discovery company Compugen. To entice users to click on these files, he says many attackers will name files attached to spam messages using double extensions - such as "corporate layoffs.doc.js" - to make the file appear to be an Office document or PDF file.
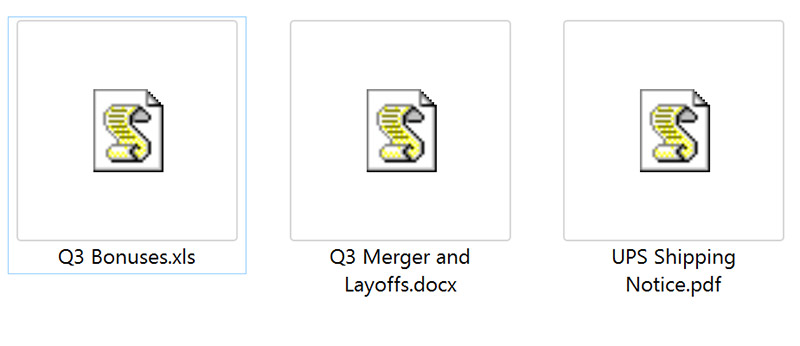 Spot the malicious JavaScript attachments. (Hint: All.) Source: SANS Institute.
Spot the malicious JavaScript attachments. (Hint: All.) Source: SANS Institute.
Blocking JavaScript Malware
Security experts say enterprise administrators can apply some relatively easy defenses against malware - including ransomware - that's been written in JavaScript. VandenBrink suggests these three steps:
Block JavaScript attachments: "Out of the gate we should strip out attachments of type .JS in emails at the spam gateway - there's no good reason to be emailing JavaScript files in and out of the organization, in almost all cases," he says. Re-associate JavaScript files: In Windows, associate JavaScript files on all systems with an application that won't execute the file, such as Notepad. This protects against any business partners "who might be whitelisted in the spam filter" or insiders - because "internal mail doesn't typically go through the spam filter" - who might unwittingly receive or transmit malicious JavaScript files. Use Group Policy: IT administrators can also force-block JavaScript from executing in the Windows shell on every PC inside an organization using Windows Group Policy, VandenBrink adds.While forcibly blocking some types of technology, such as scripts, can have unintended effects, VandenBrink says that in most cases, no user needs to be running JavaScript at the Windows shell level.
- Details
- Category: Security News
- Details
- Category: Security News
In this edition of the ISMG Security Report, DataBreachToday Executive Editor Mathew J. Schwartz analyzes the new ransomware threat posed by JavaScript.
You'll also hear (click on player beneath image to listen):
A report on what the founders of an investment fund based on the digital currency ethereum are doing after an apparent hack; A discussion by HealthcareInfoSecurity Executive Editor Marianne Kolbasuk McGee on how enterprises can address the security and privacy threats posed by virtual reality technology; A report by Jeremy Kirk, ISMG managing editor for security and technology, on an FBI warning on a new type of business email compromise scam; and Insights on why a blood test could be a form of user authentication.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Please check out our June 14 and June 17 reports, which respectively analyze Symantec's purchase of Blue Coat and how the Watergate break-in of Democratic Party headquarters might have played out if today's information technology had been available in 1972. The next ISMG Security Report will be posted Friday, June 25.
Theme music for the ISMG Security Report is by Ithaca Audio under a Creative Commons license.
- Details
- Category: Security News
As the PCI Security Standards Council celebrates its 10th anniversary, Troy Leach, the council's chief technology offer, offers his assessment of how its PCI Data Security Standard might evolve in the next 10 years.
The types of security controls the PCI-DSS will need to include 10 years from now will hinge on the amount of static payment data used to conduct transactions, he says in an interview with Information Security Media Group (see audio player below photo).
"If we reflect to 10 years ago, I couldn't have imagined that we would have so many payments being run through phones and watches ..." Leach says. "The ecosystem in which payments operates today is different than it was 10 years ago. What we need to be cognizant of is an ability to create dynamic data that changes how those transactions occur, how they work with security. And so as long as there are static data that we need to protect, the relevancy of DSS, or parts of the DSS, to control and protect that information will remain. The question is: What does a payment account number look like in 10 years?"
Evolution of the Standard
Leach says that if payments continue to evolve, relying more heavily on dynamic rather than static data, then the PCI-DSS will have to evolve as well.
"If it is dynamic information, then we have to focus our attention on how that dynamic information is created, how authentication to that transaction occurs, and other relevant aspects of a payment transaction, rather than the ... amount of controls that are required in the diverse types of technology environments we operate in today," he says.
PCI-DSS was created so organizations could re-evaluate how they were actually using and managing cardholder information, Leach says. "If we reflect back to that time, people were not aware of the risks associated with storing cardholder information or using it for loyalty programs or customer management programs. So much of the DSS effort in the beginning was actually to educate about the removal of unnecessary storage of information that was associated with many breaches at the time."
In a dynamic payments environment, however, concerns about stored payment data go away, Leach says.
During this interview, Leach also discusses:
The PCI Council's accomplishments over the past 10 years; How EMV and the PCI-DSS will complement each other; Hot topics to be addressed during this fall's round of PCI Council community meetings, which kick off Sept. 20 in Las Vegas.In his role at the PCI Council, Leach partners with council representatives, PCI participating organizations and industry leaders to develop comprehensive standards and strategies to secure payment card data and the supporting infrastructure. He is a congressional subject-matter expert on payment security and is the current chairman of the council's standards committee.
In the weeks ahead, ISMG will offer a series of interviews and updates about the global outlook for the evolving role of PCI-DSS.
More Articles …
Page 3448 of 3546







